3 hours ago
#Netflix remains one of the world’s most influential #entertainment brands, even in a hyper-competitive #streaming market. Platforms like Disney+, Prime Video, Apple TV+, YouTube, and regional OTT players are constantly fighting for viewer attention, yet Netflix continues to hold a dominant global presence.
The reason?
A sharp, evolving, and highly data-driven #marketing #strategy .
In this #article , I’ll break down Netflix’s current marketing strategy (2025) with a approach covering everything from #content strategy to #technology , partnerships, social media, and #growth tactics.
https://pratsdigital.in/ne...
The reason?
A sharp, evolving, and highly data-driven #marketing #strategy .
In this #article , I’ll break down Netflix’s current marketing strategy (2025) with a approach covering everything from #content strategy to #technology , partnerships, social media, and #growth tactics.
https://pratsdigital.in/ne...
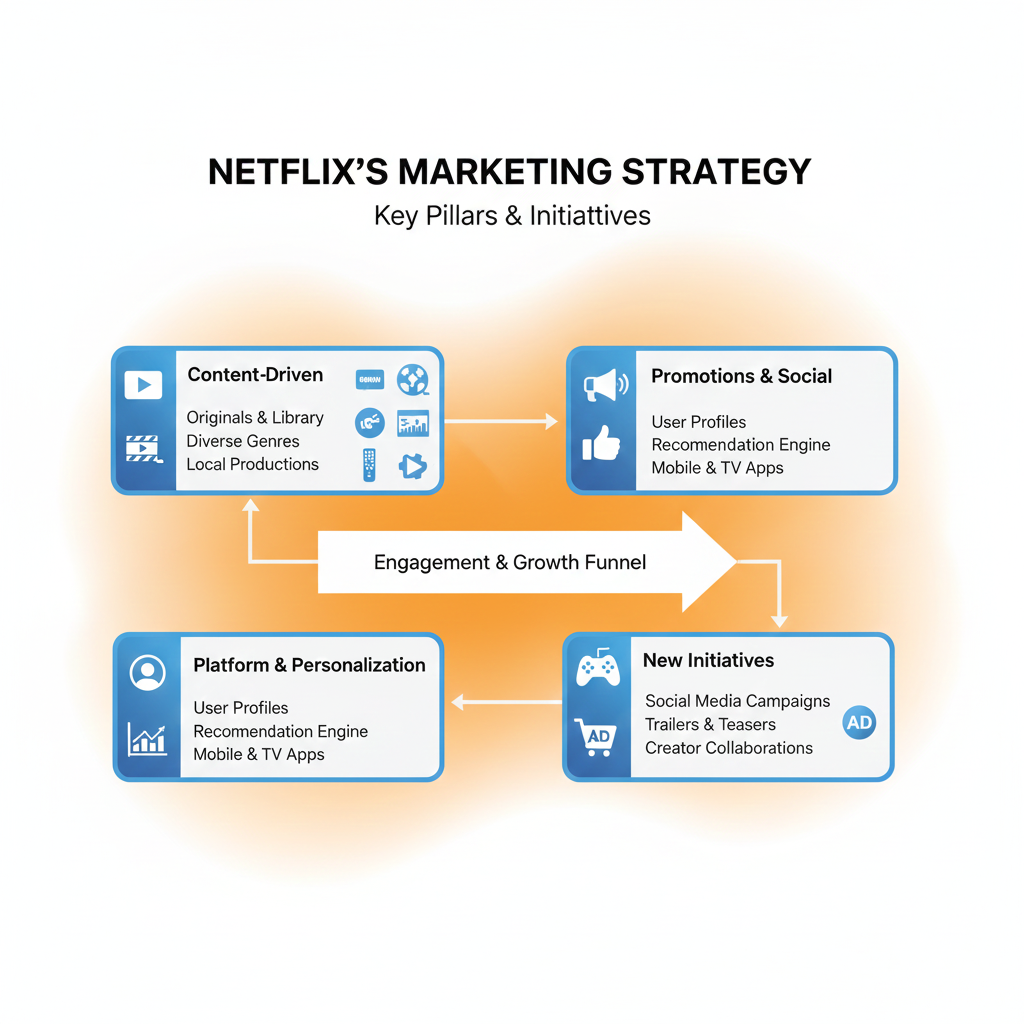
Netflix’s Current Marketing Strategy (2025): A Complete Breakdown - PratsDigital
Netflix’s current marketing strategy explained: data-driven personalization, global content, ad-tier expansion, partnerships, and social media innovations.
https://pratsdigital.in/netflix-current-marketing-strategy/
2 months ago
Expert Crypto Sniper Bot Development Services
Koinkart is the premier partner for Crypto Sniper bot development, focused on smart and reliable strategies. We design bots that follow proven signals and reduce noise so trades are more accurate and less stressful.
Check out the features here:
Focus on robust wallet encryption and secure API handling.
Multi-strategy engine
Built-in backtesting and live-paper trading options.
24/7 monitoring and incident alerts to keep bots live.
Ready to simplify trading and gain insights? Start with a free demo and setup guidance at Koinkart.org.
📲 Get Demo or Quote Now!
🌐 Website: https://www.koinkart.org/b...
📞 WhatsApp: +91 93842 63771
Koinkart is the premier partner for Crypto Sniper bot development, focused on smart and reliable strategies. We design bots that follow proven signals and reduce noise so trades are more accurate and less stressful.
Check out the features here:
Focus on robust wallet encryption and secure API handling.
Multi-strategy engine
Built-in backtesting and live-paper trading options.
24/7 monitoring and incident alerts to keep bots live.
Ready to simplify trading and gain insights? Start with a free demo and setup guidance at Koinkart.org.
📲 Get Demo or Quote Now!
🌐 Website: https://www.koinkart.org/b...
📞 WhatsApp: +91 93842 63771
3 months ago
From Strong Idea to Trusted Meme Coin - Beleaf Technologies
A successful meme coin blends creativity, strategy, and flawless execution. We provide everything you need to turn your concept into a trusted digital asset with lasting impact.
Our Services Include:
Innovative concept and tokenomics planning
Blockchain choice and smart contract creation
Secure wallet integration and liquidity setup
Distinctive branding, logo, and website design
Exchange listing assistance and community growth support
We make your meme coin unique, secure, and ready to capture attention.
Get a Free Consultation !
Visit Us >>>> https://www.beleaftechnolo...
Let’s Talk >>>> WhatsApp: +91 7904323274
Telegram: BeleafSoftTech
Email: businessbeleaftechnologies.com
A successful meme coin blends creativity, strategy, and flawless execution. We provide everything you need to turn your concept into a trusted digital asset with lasting impact.
Our Services Include:
Innovative concept and tokenomics planning
Blockchain choice and smart contract creation
Secure wallet integration and liquidity setup
Distinctive branding, logo, and website design
Exchange listing assistance and community growth support
We make your meme coin unique, secure, and ready to capture attention.
Get a Free Consultation !
Visit Us >>>> https://www.beleaftechnolo...
Let’s Talk >>>> WhatsApp: +91 7904323274
Telegram: BeleafSoftTech
Email: businessbeleaftechnologies.com
4 months ago
Focus on Cyber Warfare and Fraud-
What roles do global alliances (e.g., NATO, QUAD, ASEAN) play in cyber defense?
Global alliances play increasingly vital and multifaceted roles in cyber defense, recognizing that cyber threats transcend national borders and require collective action.
They provide frameworks for cooperation, information sharing, capacity building, and, in some cases, collective response.
Here's a breakdown of how different alliances contribute:
NATO (North Atlantic Treaty Organization):
NATO is arguably the most advanced military alliance in terms of its cyber defense integration, primarily because its core mission is collective defense.
Collective Defense (Article 5): A cornerstone of NATO's cyber defense strategy is the understanding that a cyberattack could potentially trigger Article 5 (an attack against one Ally is an attack against all). While the threshold for this is intentionally ambiguous and assessed on a case-by-case basis (based on the effects of the attack), it signifies a strong commitment to mutual defense in cyberspace.
Cyberspace as a Domain of Operations: NATO officially recognized cyberspace as a domain of operations (alongside land, sea, and air) in 2016. This allows NATO military commanders to better integrate cyber capabilities into missions and operations.
Information Sharing and Threat Intelligence: NATO facilitates the real-time sharing of information about cyber threats, malware, and best practices among Allies through dedicated platforms and expert networks.
Rapid Reaction Teams (RRTs): NATO maintains cyber rapid reaction teams that can be deployed to help Allies address cyber challenges, providing technical assistance and coordinating responses to incidents.
Capacity Building and Training: NATO works to enhance the individual cyber defenses of its member states through training programs, exercises (like Cyber Coalition), and setting common targets for national cyber defense capabilities.
Norms and International Law: NATO consistently reaffirms that international law, including the UN Charter, applies in cyberspace, contributing to the development of responsible state behavior norms.
Public-Private Partnerships: NATO strengthens its relationship with industry and academia through initiatives like the NATO Industry Cyber Partnership to leverage external expertise and resources.
QUAD (Quadrilateral Security Dialogue - Australia, India, Japan, United States):
The QUAD, while not a military alliance in the traditional sense, has significantly increased its focus on cybersecurity cooperation, particularly given the shared concerns about threats in the Indo-Pacific.
Critical Infrastructure Protection: A key priority for the QUAD is to strengthen the resilience of critical infrastructure across member states and the broader Indo-Pacific region against cyber disruptions. This involves sharing approaches to policy development and threat information.
Supply Chain Risk Management: Collaboration on securing digital supply chains, recognizing that vulnerabilities in one component can impact all users.
Software Security Standards: Efforts to align and ensure the implementation of baseline software security standards, potentially leveraging the collective purchasing power of their governments to drive secure-by-design principles in the software ecosystem.
Information Sharing: Promoting rapid and timely sharing of threat information between governments and with industry partners.
Capacity Building: Collaborating on capacity-building programs in the Indo-Pacific region to help partner nations enhance their cybersecurity capabilities.
Workforce Development: Working together to enhance the collective cybersecurity workforce and pool of talented cyber professionals among member states.
Responsible Cyber Habits: Launching public campaigns like the "Quad Cyber Challenge" to improve cybersecurity awareness and habits among Internet users.
ASEAN (Association of Southeast Asian Nations):
ASEAN's approach to cyber defense is focused on regional cooperation, capacity building, and harmonizing policies among its diverse member states.
Regional Cybersecurity Cooperation Strategy: ASEAN has a strategy (e.g., 2021-2025) focused on advancing cyber readiness, strengthening regional cyber policies, enhancing trust in cyberspace, and capacity building.
ASEAN CERT Network: Facilitating coordination and information sharing between national-level Computer Emergency Response Teams (CERTs) of member states. An ASEAN CERT is being established to enable timely exchange of threat information.
Cybercrime Operations Desk: Collaborating with INTERPOL to promote information sharing on cybercrime threats and better integrated operations for the region.
Capacity Building and Training: Numerous initiatives (often supported by dialogue partners like Singapore, Japan, and the U.S.) to build technical, policy, and strategic cyber capacity among member states through training programs, workshops, and joint exercises. Examples include the ASEAN Cyber Capacity Programme (ACCP) and the ASEAN–Japan Cybersecurity Capacity Building Centre (AJCCBC).
Cyber Defense Network (ACDN): A defense-focused network aiming to link the cyber defense centers of all member states, assist in developing new centers, and identify information-sharing gaps.
Norms and Responsible Behavior: Encouraging member states to subscribe to voluntary, non-binding norms of responsible State behavior in cyberspace.
Malware Information Sharing Platform (MISP): Launched to allow member states to share timely cybersecurity threat information.
Common Roles Across Alliances:
Despite their differences in scope and structure, these alliances share several common roles in cyber defense:
Information and Threat Intelligence Sharing: This is foundational. By sharing insights into TTPs, vulnerabilities, and ongoing campaigns, members can collectively improve their defenses and develop more effective countermeasures.
Capacity Building: Many alliances invest in programs to uplift the cybersecurity capabilities of their members, especially those with fewer resources. This includes training, exercises, and sharing best practices.
Norm Development: Alliances contribute to the ongoing global dialogue about responsible state behavior in cyberspace, advocating for the application of international law and promoting peaceful conduct.
Policy Coordination: They provide platforms for members to discuss, coordinate, and harmonize national cybersecurity policies and regulatory frameworks, leading to more cohesive responses to transboundary threats.
Collective Response and Deterrence: For military alliances like NATO, this involves explicit commitments to collective defense. For others, it involves coordinated public attribution or diplomatic pressure, aiming to deter malicious actors.
Joint Exercises and Drills: Simulating cyberattacks and responses helps members test their readiness, identify weaknesses, and improve coordination in real-world scenarios.
In summary, global alliances are indispensable in the cyber domain. They recognize that no single nation can effectively combat sophisticated, borderless cyber threats alone, fostering a collaborative environment to enhance collective resilience, deter aggression, and shape the future of cybersecurity governance.
What roles do global alliances (e.g., NATO, QUAD, ASEAN) play in cyber defense?
Global alliances play increasingly vital and multifaceted roles in cyber defense, recognizing that cyber threats transcend national borders and require collective action.
They provide frameworks for cooperation, information sharing, capacity building, and, in some cases, collective response.
Here's a breakdown of how different alliances contribute:
NATO (North Atlantic Treaty Organization):
NATO is arguably the most advanced military alliance in terms of its cyber defense integration, primarily because its core mission is collective defense.
Collective Defense (Article 5): A cornerstone of NATO's cyber defense strategy is the understanding that a cyberattack could potentially trigger Article 5 (an attack against one Ally is an attack against all). While the threshold for this is intentionally ambiguous and assessed on a case-by-case basis (based on the effects of the attack), it signifies a strong commitment to mutual defense in cyberspace.
Cyberspace as a Domain of Operations: NATO officially recognized cyberspace as a domain of operations (alongside land, sea, and air) in 2016. This allows NATO military commanders to better integrate cyber capabilities into missions and operations.
Information Sharing and Threat Intelligence: NATO facilitates the real-time sharing of information about cyber threats, malware, and best practices among Allies through dedicated platforms and expert networks.
Rapid Reaction Teams (RRTs): NATO maintains cyber rapid reaction teams that can be deployed to help Allies address cyber challenges, providing technical assistance and coordinating responses to incidents.
Capacity Building and Training: NATO works to enhance the individual cyber defenses of its member states through training programs, exercises (like Cyber Coalition), and setting common targets for national cyber defense capabilities.
Norms and International Law: NATO consistently reaffirms that international law, including the UN Charter, applies in cyberspace, contributing to the development of responsible state behavior norms.
Public-Private Partnerships: NATO strengthens its relationship with industry and academia through initiatives like the NATO Industry Cyber Partnership to leverage external expertise and resources.
QUAD (Quadrilateral Security Dialogue - Australia, India, Japan, United States):
The QUAD, while not a military alliance in the traditional sense, has significantly increased its focus on cybersecurity cooperation, particularly given the shared concerns about threats in the Indo-Pacific.
Critical Infrastructure Protection: A key priority for the QUAD is to strengthen the resilience of critical infrastructure across member states and the broader Indo-Pacific region against cyber disruptions. This involves sharing approaches to policy development and threat information.
Supply Chain Risk Management: Collaboration on securing digital supply chains, recognizing that vulnerabilities in one component can impact all users.
Software Security Standards: Efforts to align and ensure the implementation of baseline software security standards, potentially leveraging the collective purchasing power of their governments to drive secure-by-design principles in the software ecosystem.
Information Sharing: Promoting rapid and timely sharing of threat information between governments and with industry partners.
Capacity Building: Collaborating on capacity-building programs in the Indo-Pacific region to help partner nations enhance their cybersecurity capabilities.
Workforce Development: Working together to enhance the collective cybersecurity workforce and pool of talented cyber professionals among member states.
Responsible Cyber Habits: Launching public campaigns like the "Quad Cyber Challenge" to improve cybersecurity awareness and habits among Internet users.
ASEAN (Association of Southeast Asian Nations):
ASEAN's approach to cyber defense is focused on regional cooperation, capacity building, and harmonizing policies among its diverse member states.
Regional Cybersecurity Cooperation Strategy: ASEAN has a strategy (e.g., 2021-2025) focused on advancing cyber readiness, strengthening regional cyber policies, enhancing trust in cyberspace, and capacity building.
ASEAN CERT Network: Facilitating coordination and information sharing between national-level Computer Emergency Response Teams (CERTs) of member states. An ASEAN CERT is being established to enable timely exchange of threat information.
Cybercrime Operations Desk: Collaborating with INTERPOL to promote information sharing on cybercrime threats and better integrated operations for the region.
Capacity Building and Training: Numerous initiatives (often supported by dialogue partners like Singapore, Japan, and the U.S.) to build technical, policy, and strategic cyber capacity among member states through training programs, workshops, and joint exercises. Examples include the ASEAN Cyber Capacity Programme (ACCP) and the ASEAN–Japan Cybersecurity Capacity Building Centre (AJCCBC).
Cyber Defense Network (ACDN): A defense-focused network aiming to link the cyber defense centers of all member states, assist in developing new centers, and identify information-sharing gaps.
Norms and Responsible Behavior: Encouraging member states to subscribe to voluntary, non-binding norms of responsible State behavior in cyberspace.
Malware Information Sharing Platform (MISP): Launched to allow member states to share timely cybersecurity threat information.
Common Roles Across Alliances:
Despite their differences in scope and structure, these alliances share several common roles in cyber defense:
Information and Threat Intelligence Sharing: This is foundational. By sharing insights into TTPs, vulnerabilities, and ongoing campaigns, members can collectively improve their defenses and develop more effective countermeasures.
Capacity Building: Many alliances invest in programs to uplift the cybersecurity capabilities of their members, especially those with fewer resources. This includes training, exercises, and sharing best practices.
Norm Development: Alliances contribute to the ongoing global dialogue about responsible state behavior in cyberspace, advocating for the application of international law and promoting peaceful conduct.
Policy Coordination: They provide platforms for members to discuss, coordinate, and harmonize national cybersecurity policies and regulatory frameworks, leading to more cohesive responses to transboundary threats.
Collective Response and Deterrence: For military alliances like NATO, this involves explicit commitments to collective defense. For others, it involves coordinated public attribution or diplomatic pressure, aiming to deter malicious actors.
Joint Exercises and Drills: Simulating cyberattacks and responses helps members test their readiness, identify weaknesses, and improve coordination in real-world scenarios.
In summary, global alliances are indispensable in the cyber domain. They recognize that no single nation can effectively combat sophisticated, borderless cyber threats alone, fostering a collaborative environment to enhance collective resilience, deter aggression, and shape the future of cybersecurity governance.
4 months ago
Focus on Cyber Warfare and Fraud-
How do multinational companies protect themselves from state-sponsored cyber espionage?
Multinational companies face a unique and elevated threat from state-sponsored cyber espionage due to their vast intellectual property, critical infrastructure dependencies, global reach, and often, involvement in strategic industries.
Protecting themselves requires a comprehensive, multi-layered, and continuously evolving cybersecurity strategy that goes beyond standard defenses.
Here are the key ways multinational companies protect themselves:
1. Robust Foundational Cybersecurity:
Before anything else, strong basic cybersecurity hygiene is paramount. State-sponsored actors often exploit common weaknesses.
Patch Management: Aggressive and immediate patching of all software, operating systems, and network devices, especially for known exploited vulnerabilities (N-day exploits). This includes out-of-band updates.
Strong Access Controls:
Multi-Factor Authentication (MFA): Mandatory MFA for all employees, especially for remote access, cloud services, and privileged accounts. Hardware tokens are often preferred for highly sensitive access.
Principle of Least Privilege (PoLP): Granting users and systems only the minimum access rights necessary to perform their functions.
Privileged Access Management (PAM): Solutions to secure, manage, and monitor privileged accounts.
Network Segmentation: Dividing the network into isolated zones to limit lateral movement if a part of the network is compromised. Critical data and operational technology (OT) networks should be completely segregated.
Endpoint Detection and Response (EDR) / Extended Detection and Response (XDR): Deploying advanced solutions to continuously monitor, detect, and respond to threats on endpoints (laptops, servers) and across the broader IT ecosystem.
Data Encryption: Encrypting data at rest and in transit, especially sensitive intellectual property and customer data.
2. Advanced Threat Detection and Intelligence:
State-sponsored groups are stealthy; proactive detection is crucial.
Behavioral Analytics & Anomaly Detection: Implementing tools that use AI and machine learning to establish baselines of "normal" user and network behavior, and then flag deviations that could indicate a compromise.
Threat Hunting Teams (Red Teaming/Blue Teaming): Employing internal or external teams to proactively search for hidden threats within the network, rather than just reacting to alerts. This includes simulating attacks (red teaming) to test defenses.
Comprehensive Logging and Monitoring: Centralized collection and analysis of logs from all systems, applications, and network devices to identify suspicious activity.
Threat Intelligence Integration: Subscribing to and actively consuming high-quality threat intelligence feeds from government agencies (like CISA, NCSC), cybersecurity vendors, and industry-specific ISACs (Information Sharing and Analysis Centers). This intelligence provides insights into the latest TTPs of state-sponsored actors, enabling proactive defense.
Dark Web Monitoring: Monitoring for mentions of the company, its employees, or stolen data on underground forums.
3. Supply Chain and Third-Party Risk Management:
State-sponsored actors often target weaker links in the supply chain.
Thorough Vendor Due Diligence: Rigorous cybersecurity assessments of all third-party vendors, suppliers, and partners, especially those with access to sensitive systems or data. This includes contractual security requirements.
Continuous Monitoring of Third-Parties: Not just a one-time assessment, but ongoing monitoring of third-party security postures and potential vulnerabilities in their products or services.
Supply Chain Visibility: Mapping the entire digital supply chain to understand dependencies and identify potential weak points.
Software Bill of Materials (SBOMs): Requiring SBOMs from software vendors to understand all components (including open-source) in their products and track potential vulnerabilities.
4. Human Element and Insider Threat Mitigation:
Employees are often the primary target for initial access.
Security Awareness Training: Regular, up-to-date, and engaging training for all employees on phishing, social engineering tactics, safe Browse, and reporting suspicious activity. Tailored training for executives and high-value targets (HVT) is essential.
Phishing Simulations: Conducting frequent and varied phishing simulations to test employee vigilance and reinforce training.
Insider Threat Programs: Establishing programs to detect and mitigate risks from malicious or unwitting insiders, including monitoring user behavior and data access patterns.
5. Incident Response and Resilience:
Assuming compromise is inevitable, preparation is key.
Well-Defined Incident Response Plan: A detailed, tested, and regularly updated plan for how to detect, contain, eradicate, and recover from a state-sponsored cyberattack. This includes clear roles, responsibilities, and communication protocols.
Secure Backups: Regular, encrypted, and offline backups of critical data and systems to ensure recovery from destructive attacks.
Business Continuity and Disaster Recovery (BCDR) Plans: Comprehensive plans to maintain essential business operations even during and after a significant cyber incident.
Post-Incident Analysis: Conducting thorough post-mortem analyses after any incident to learn lessons and improve defenses.
6. Collaboration with Government and Intelligence Agencies:
Governments often have unique insights into nation-state threats.
Information Sharing: Actively participating in information-sharing initiatives with government cybersecurity agencies (e.g., CISA in the US, NCSC in the UK), industry-specific ISACs, and threat intelligence alliances.
Trusted Relationships: Building direct, trusted relationships with relevant government cyber defense and intelligence agencies to facilitate rapid two-way sharing of classified or sensitive threat intelligence.
Reporting Incidents: Urgently reporting suspected state-sponsored cyberattacks to relevant government authorities to aid in national defense and enable coordinated responses.
By implementing these advanced and comprehensive measures, multinational companies can significantly enhance their resilience against state-sponsored cyber espionage, protect their valuable assets, and maintain their competitive edge in a contested digital landscape.
How do multinational companies protect themselves from state-sponsored cyber espionage?
Multinational companies face a unique and elevated threat from state-sponsored cyber espionage due to their vast intellectual property, critical infrastructure dependencies, global reach, and often, involvement in strategic industries.
Protecting themselves requires a comprehensive, multi-layered, and continuously evolving cybersecurity strategy that goes beyond standard defenses.
Here are the key ways multinational companies protect themselves:
1. Robust Foundational Cybersecurity:
Before anything else, strong basic cybersecurity hygiene is paramount. State-sponsored actors often exploit common weaknesses.
Patch Management: Aggressive and immediate patching of all software, operating systems, and network devices, especially for known exploited vulnerabilities (N-day exploits). This includes out-of-band updates.
Strong Access Controls:
Multi-Factor Authentication (MFA): Mandatory MFA for all employees, especially for remote access, cloud services, and privileged accounts. Hardware tokens are often preferred for highly sensitive access.
Principle of Least Privilege (PoLP): Granting users and systems only the minimum access rights necessary to perform their functions.
Privileged Access Management (PAM): Solutions to secure, manage, and monitor privileged accounts.
Network Segmentation: Dividing the network into isolated zones to limit lateral movement if a part of the network is compromised. Critical data and operational technology (OT) networks should be completely segregated.
Endpoint Detection and Response (EDR) / Extended Detection and Response (XDR): Deploying advanced solutions to continuously monitor, detect, and respond to threats on endpoints (laptops, servers) and across the broader IT ecosystem.
Data Encryption: Encrypting data at rest and in transit, especially sensitive intellectual property and customer data.
2. Advanced Threat Detection and Intelligence:
State-sponsored groups are stealthy; proactive detection is crucial.
Behavioral Analytics & Anomaly Detection: Implementing tools that use AI and machine learning to establish baselines of "normal" user and network behavior, and then flag deviations that could indicate a compromise.
Threat Hunting Teams (Red Teaming/Blue Teaming): Employing internal or external teams to proactively search for hidden threats within the network, rather than just reacting to alerts. This includes simulating attacks (red teaming) to test defenses.
Comprehensive Logging and Monitoring: Centralized collection and analysis of logs from all systems, applications, and network devices to identify suspicious activity.
Threat Intelligence Integration: Subscribing to and actively consuming high-quality threat intelligence feeds from government agencies (like CISA, NCSC), cybersecurity vendors, and industry-specific ISACs (Information Sharing and Analysis Centers). This intelligence provides insights into the latest TTPs of state-sponsored actors, enabling proactive defense.
Dark Web Monitoring: Monitoring for mentions of the company, its employees, or stolen data on underground forums.
3. Supply Chain and Third-Party Risk Management:
State-sponsored actors often target weaker links in the supply chain.
Thorough Vendor Due Diligence: Rigorous cybersecurity assessments of all third-party vendors, suppliers, and partners, especially those with access to sensitive systems or data. This includes contractual security requirements.
Continuous Monitoring of Third-Parties: Not just a one-time assessment, but ongoing monitoring of third-party security postures and potential vulnerabilities in their products or services.
Supply Chain Visibility: Mapping the entire digital supply chain to understand dependencies and identify potential weak points.
Software Bill of Materials (SBOMs): Requiring SBOMs from software vendors to understand all components (including open-source) in their products and track potential vulnerabilities.
4. Human Element and Insider Threat Mitigation:
Employees are often the primary target for initial access.
Security Awareness Training: Regular, up-to-date, and engaging training for all employees on phishing, social engineering tactics, safe Browse, and reporting suspicious activity. Tailored training for executives and high-value targets (HVT) is essential.
Phishing Simulations: Conducting frequent and varied phishing simulations to test employee vigilance and reinforce training.
Insider Threat Programs: Establishing programs to detect and mitigate risks from malicious or unwitting insiders, including monitoring user behavior and data access patterns.
5. Incident Response and Resilience:
Assuming compromise is inevitable, preparation is key.
Well-Defined Incident Response Plan: A detailed, tested, and regularly updated plan for how to detect, contain, eradicate, and recover from a state-sponsored cyberattack. This includes clear roles, responsibilities, and communication protocols.
Secure Backups: Regular, encrypted, and offline backups of critical data and systems to ensure recovery from destructive attacks.
Business Continuity and Disaster Recovery (BCDR) Plans: Comprehensive plans to maintain essential business operations even during and after a significant cyber incident.
Post-Incident Analysis: Conducting thorough post-mortem analyses after any incident to learn lessons and improve defenses.
6. Collaboration with Government and Intelligence Agencies:
Governments often have unique insights into nation-state threats.
Information Sharing: Actively participating in information-sharing initiatives with government cybersecurity agencies (e.g., CISA in the US, NCSC in the UK), industry-specific ISACs, and threat intelligence alliances.
Trusted Relationships: Building direct, trusted relationships with relevant government cyber defense and intelligence agencies to facilitate rapid two-way sharing of classified or sensitive threat intelligence.
Reporting Incidents: Urgently reporting suspected state-sponsored cyberattacks to relevant government authorities to aid in national defense and enable coordinated responses.
By implementing these advanced and comprehensive measures, multinational companies can significantly enhance their resilience against state-sponsored cyber espionage, protect their valuable assets, and maintain their competitive edge in a contested digital landscape.
4 months ago
Focus on Cyber Warfare and Fraud-
Are Southeast Asian nations also developing offensive cyber capabilities? If so, why?
Southeast Asian nations are increasingly developing and investing in their offensive cyber capabilities, albeit to varying degrees depending on their resources and strategic priorities. This development is often more subtle and less publicly acknowledged than defensive measures, but it's a growing trend driven by a complex mix of motivations.
Here's why:
Why Southeast Asian Nations are Developing Offensive Cyber Capabilities:
Deterrence and Self-Defense:
Responding to External Threats: Southeast Asia is a prime target for cyberattacks from major powers (like China, as seen with groups like SharpPanda) and other nation-state actors (e.g., North Korea, Russia). Developing offensive capabilities is seen as a necessary means to deter potential adversaries by demonstrating a credible ability to retaliate or impose costs in cyberspace.
Asymmetric Warfare: For smaller nations with limited conventional military power, cyber capabilities offer an asymmetric advantage. They provide a cost-effective way to project power and defend national interests against larger, more technologically advanced adversaries without resorting to traditional armed conflict.
Maintaining Sovereignty: In an increasingly digital world, the ability to operate effectively in cyberspace, including offensively, is seen as crucial for maintaining national sovereignty and protecting critical infrastructure from foreign interference or attacks.
Intelligence Gathering and Espionage:
National Security Intelligence: Offensive cyber tools are essential for gathering intelligence on geopolitical rivals, regional disputes (e.g., in the South China Sea), terrorist groups, and internal political dynamics in neighboring countries. This intelligence helps inform national security policies and decision-making.
Economic Espionage: Some nations may use offensive cyber capabilities to acquire intellectual property, trade secrets, or economic intelligence to support their national industries and accelerate economic growth. Vietnam's cyber activities, for instance, are often linked to economic espionage.
Support for Conventional Military Operations (Hybrid Warfare):
Force Multiplier: Cyber operations can serve as a force multiplier in military conflicts. They can be used to disrupt enemy command and control systems, communication networks, logistics, and critical infrastructure (e.g., power grids, transportation) before or during kinetic operations.
Preparation of the Battlefield: Offensive cyber capabilities allow for the "preparation of the digital battlefield," including gaining persistent access to adversary networks, mapping vulnerabilities, and planting malware for potential activation in a crisis.
Counter-Cybercrime and Counter-Terrorism:
While distinct from state-sponsored "offensive cyber capabilities" in a military sense, some nations may develop advanced forensic and "active defense" capabilities that blur the lines, allowing them to trace and disrupt cybercriminal or terrorist networks. This can involve operations that might be considered offensive by some definitions.
Protection of Critical National Infrastructure (CNI):
While primarily defensive, the ability to conduct offensive reconnaissance or "hunt" for threats within critical infrastructure (even abroad) might be seen as a necessary part of a comprehensive CNI protection strategy. Knowing how to attack helps inform how to defend.
Regional Geopolitical Dynamics:
The intensifying cybersecurity landscape, with major powers like the U.S. and China actively operating in cyberspace, compels Southeast Asian nations to enhance their own capabilities to avoid being passive targets or proxies in larger cyber conflicts.
Specific regional disputes (like the South China Sea) further incentivize the development of capabilities to protect national interests and gather relevant information.
Varying Degrees of Capability:
It's important to note that the level of offensive cyber capability varies significantly across Southeast Asian nations:
Singapore is widely recognized as a leader in cybersecurity within ASEAN, with significant investments in both defensive and offensive capabilities, sophisticated intelligence agencies, and a strong focus on critical infrastructure protection.
Malaysia, Thailand, and Vietnam also have increasingly sophisticated capabilities, driven by their strategic positions and economic development goals. Vietnam, as mentioned, has known state-sponsored groups engaged in advanced espionage.
Other nations like Cambodia, Laos, and Myanmar generally have more nascent cyber defense infrastructures and limited resources, meaning their offensive capabilities would be far less developed, if present at all, and likely limited to basic actions or rely on foreign assistance.
In conclusion, the development of offensive cyber capabilities in Southeast Asia is a pragmatic response to a rapidly evolving digital threat landscape. It's driven by the need for self-defense, intelligence gathering, strategic deterrence, and the desire to project influence and protect national interests in an increasingly interconnected and contested cyberspace.
Are Southeast Asian nations also developing offensive cyber capabilities? If so, why?
Southeast Asian nations are increasingly developing and investing in their offensive cyber capabilities, albeit to varying degrees depending on their resources and strategic priorities. This development is often more subtle and less publicly acknowledged than defensive measures, but it's a growing trend driven by a complex mix of motivations.
Here's why:
Why Southeast Asian Nations are Developing Offensive Cyber Capabilities:
Deterrence and Self-Defense:
Responding to External Threats: Southeast Asia is a prime target for cyberattacks from major powers (like China, as seen with groups like SharpPanda) and other nation-state actors (e.g., North Korea, Russia). Developing offensive capabilities is seen as a necessary means to deter potential adversaries by demonstrating a credible ability to retaliate or impose costs in cyberspace.
Asymmetric Warfare: For smaller nations with limited conventional military power, cyber capabilities offer an asymmetric advantage. They provide a cost-effective way to project power and defend national interests against larger, more technologically advanced adversaries without resorting to traditional armed conflict.
Maintaining Sovereignty: In an increasingly digital world, the ability to operate effectively in cyberspace, including offensively, is seen as crucial for maintaining national sovereignty and protecting critical infrastructure from foreign interference or attacks.
Intelligence Gathering and Espionage:
National Security Intelligence: Offensive cyber tools are essential for gathering intelligence on geopolitical rivals, regional disputes (e.g., in the South China Sea), terrorist groups, and internal political dynamics in neighboring countries. This intelligence helps inform national security policies and decision-making.
Economic Espionage: Some nations may use offensive cyber capabilities to acquire intellectual property, trade secrets, or economic intelligence to support their national industries and accelerate economic growth. Vietnam's cyber activities, for instance, are often linked to economic espionage.
Support for Conventional Military Operations (Hybrid Warfare):
Force Multiplier: Cyber operations can serve as a force multiplier in military conflicts. They can be used to disrupt enemy command and control systems, communication networks, logistics, and critical infrastructure (e.g., power grids, transportation) before or during kinetic operations.
Preparation of the Battlefield: Offensive cyber capabilities allow for the "preparation of the digital battlefield," including gaining persistent access to adversary networks, mapping vulnerabilities, and planting malware for potential activation in a crisis.
Counter-Cybercrime and Counter-Terrorism:
While distinct from state-sponsored "offensive cyber capabilities" in a military sense, some nations may develop advanced forensic and "active defense" capabilities that blur the lines, allowing them to trace and disrupt cybercriminal or terrorist networks. This can involve operations that might be considered offensive by some definitions.
Protection of Critical National Infrastructure (CNI):
While primarily defensive, the ability to conduct offensive reconnaissance or "hunt" for threats within critical infrastructure (even abroad) might be seen as a necessary part of a comprehensive CNI protection strategy. Knowing how to attack helps inform how to defend.
Regional Geopolitical Dynamics:
The intensifying cybersecurity landscape, with major powers like the U.S. and China actively operating in cyberspace, compels Southeast Asian nations to enhance their own capabilities to avoid being passive targets or proxies in larger cyber conflicts.
Specific regional disputes (like the South China Sea) further incentivize the development of capabilities to protect national interests and gather relevant information.
Varying Degrees of Capability:
It's important to note that the level of offensive cyber capability varies significantly across Southeast Asian nations:
Singapore is widely recognized as a leader in cybersecurity within ASEAN, with significant investments in both defensive and offensive capabilities, sophisticated intelligence agencies, and a strong focus on critical infrastructure protection.
Malaysia, Thailand, and Vietnam also have increasingly sophisticated capabilities, driven by their strategic positions and economic development goals. Vietnam, as mentioned, has known state-sponsored groups engaged in advanced espionage.
Other nations like Cambodia, Laos, and Myanmar generally have more nascent cyber defense infrastructures and limited resources, meaning their offensive capabilities would be far less developed, if present at all, and likely limited to basic actions or rely on foreign assistance.
In conclusion, the development of offensive cyber capabilities in Southeast Asia is a pragmatic response to a rapidly evolving digital threat landscape. It's driven by the need for self-defense, intelligence gathering, strategic deterrence, and the desire to project influence and protect national interests in an increasingly interconnected and contested cyberspace.
4 months ago
Focus Nigeria-
How can public hospitals be improved to serve the poor better?
Improving public hospitals to better serve the poor requires a comprehensive strategy that addresses the core issues of funding, infrastructure, human resources, efficiency, and patient-centered care.
For a country like Nigeria, where the majority of the population relies on public healthcare and poverty is widespread, these improvements are vital for national development and social equity.
Here's a detailed approach:
I. Increased and Transparent Funding:
Allocate More Budgetary Resources: Governments at federal, state, and local levels must significantly increase the percentage of their budgets allocated to healthcare, aiming to meet or exceed international recommendations (e.g., the Abuja Declaration's 15%).
Targeted Funding for the Poor: Earmark specific funds for initiatives that directly benefit low-income patients, such as subsidized or free essential services, medications, and diagnostic tests for those who cannot afford them.
Strengthen Health Insurance Schemes (e.g., NHIS):
Expand Coverage: Aggressively expand the reach of the National Health Insurance Scheme (NHIS) to cover a larger portion of the informal sector and vulnerable populations, potentially through community-based health insurance models or state-led initiatives.
Subsidies for the Poor: Implement government subsidies or premium support for low-income households to ensure they can afford health insurance contributions.
Streamline Processes: Simplify the enrollment and claims processes for the poor to reduce bureaucratic hurdles.
Combat Corruption and Ensure Accountability:
Implement robust financial management systems, regular audits, and strict anti-corruption measures within public hospitals to prevent embezzlement and ensure funds are used for their intended purpose.
Introduce performance-based funding where hospitals receive additional funds based on patient outcomes, efficiency, and satisfaction.
II. Infrastructure and Equipment Upgrade:
Renovation and Modernization: Invest in systematic renovation and modernization of existing public hospital buildings to create clean, safe, and dignified environments.
Equip with Modern Technology: Provide essential, functional diagnostic and treatment equipment (e.g., X-ray machines, ultrasound scanners, laboratory equipment, essential surgical tools). Ensure maintenance contracts and availability of spare parts.
Reliable Utilities: Guarantee constant access to clean water, reliable electricity (invest in solar power as a sustainable backup), and proper waste management systems in all public hospitals.
Basic Amenities: Ensure availability of basic amenities like clean restrooms (separate for male/female), comfortable waiting areas, and proper ventilation.
III. Human Resources Development and Motivation:
Adequate Staffing: Recruit and retain a sufficient number of qualified doctors, nurses, pharmacists, laboratory scientists, and other support staff to reduce workload and improve patient-to-staff ratios.
Competitive Remuneration and Welfare: Offer attractive and timely salaries, allowances, and a comprehensive benefits package (including health insurance and pensions) to stem the brain drain and motivate staff.
Continuous Professional Development (CPD): Provide regular training opportunities to upgrade skills, keep staff abreast of new medical advancements, and improve patient communication.
Ethical Conduct and Empathy Training: Conduct mandatory training on medical ethics, patient rights, empathy, and respectful communication, particularly towards low-income patients who may feel disempowered.
Performance Incentives: Introduce performance-based incentives for staff tied to patient satisfaction, quality of care, and efficiency, rather than just volume.
Safety and Security: Enhance security measures within hospital premises to protect staff from harassment or violence.
IV. Operational Efficiency and Patient-Centered Care:
Streamline Processes: Implement efficient patient flow systems, from registration to consultation, diagnosis, and treatment, to reduce long waiting times and bureaucratic bottlenecks.
Digitalization (Electronic Health Records - EHR):
Implement EHR systems to improve record-keeping, reduce errors, enhance data sharing among departments, and enable better patient tracking.
Digitalize appointment scheduling and billing to minimize human interface and reduce opportunities for corruption.
Focus on Primary Healthcare (PHC): Strengthen the referral system from PHC centers to secondary and tertiary public hospitals. Well-equipped and staffed PHCs can manage common ailments, reducing the burden on hospitals and making basic care accessible at the community level.
Culturally Sensitive Care: Train staff to understand and respect the cultural beliefs and practices of diverse patient populations, which can influence health-seeking behaviors.
Patient Feedback Mechanisms: Establish accessible and confidential channels for patients to provide feedback, lodge complaints, and make suggestions for improvement. Use this feedback to drive continuous improvement.
Transparency and Information: Clearly display service costs (if any), patients' rights, and grievance procedures. Provide clear information about treatment plans in a language patients understand.
V. Innovative Service Delivery Models:
Mobile Clinics and Outreach Programs: Implement mobile health clinics that travel to underserved rural communities, providing basic diagnostic, preventive, and primary care services, as well as health education.
Telemedicine: Leverage telemedicine for remote consultations, specialist opinions, and follow-ups, particularly for patients in remote areas where specialists are scarce. This can reduce travel costs and time for patients.
Community Health Workers (CHWs): Train and deploy CHWs from within the communities to act as a link between the community and the health system, providing basic health education, screening, and facilitating referrals.
Partnerships with NGOs and CSOs: Collaborate with non-governmental organizations and civil society organizations that have experience in delivering healthcare to underserved populations.
By implementing these strategies, public hospitals can move towards becoming trusted, accessible, and high-quality healthcare providers for all, especially the most vulnerable members of society.
How can public hospitals be improved to serve the poor better?
Improving public hospitals to better serve the poor requires a comprehensive strategy that addresses the core issues of funding, infrastructure, human resources, efficiency, and patient-centered care.
For a country like Nigeria, where the majority of the population relies on public healthcare and poverty is widespread, these improvements are vital for national development and social equity.
Here's a detailed approach:
I. Increased and Transparent Funding:
Allocate More Budgetary Resources: Governments at federal, state, and local levels must significantly increase the percentage of their budgets allocated to healthcare, aiming to meet or exceed international recommendations (e.g., the Abuja Declaration's 15%).
Targeted Funding for the Poor: Earmark specific funds for initiatives that directly benefit low-income patients, such as subsidized or free essential services, medications, and diagnostic tests for those who cannot afford them.
Strengthen Health Insurance Schemes (e.g., NHIS):
Expand Coverage: Aggressively expand the reach of the National Health Insurance Scheme (NHIS) to cover a larger portion of the informal sector and vulnerable populations, potentially through community-based health insurance models or state-led initiatives.
Subsidies for the Poor: Implement government subsidies or premium support for low-income households to ensure they can afford health insurance contributions.
Streamline Processes: Simplify the enrollment and claims processes for the poor to reduce bureaucratic hurdles.
Combat Corruption and Ensure Accountability:
Implement robust financial management systems, regular audits, and strict anti-corruption measures within public hospitals to prevent embezzlement and ensure funds are used for their intended purpose.
Introduce performance-based funding where hospitals receive additional funds based on patient outcomes, efficiency, and satisfaction.
II. Infrastructure and Equipment Upgrade:
Renovation and Modernization: Invest in systematic renovation and modernization of existing public hospital buildings to create clean, safe, and dignified environments.
Equip with Modern Technology: Provide essential, functional diagnostic and treatment equipment (e.g., X-ray machines, ultrasound scanners, laboratory equipment, essential surgical tools). Ensure maintenance contracts and availability of spare parts.
Reliable Utilities: Guarantee constant access to clean water, reliable electricity (invest in solar power as a sustainable backup), and proper waste management systems in all public hospitals.
Basic Amenities: Ensure availability of basic amenities like clean restrooms (separate for male/female), comfortable waiting areas, and proper ventilation.
III. Human Resources Development and Motivation:
Adequate Staffing: Recruit and retain a sufficient number of qualified doctors, nurses, pharmacists, laboratory scientists, and other support staff to reduce workload and improve patient-to-staff ratios.
Competitive Remuneration and Welfare: Offer attractive and timely salaries, allowances, and a comprehensive benefits package (including health insurance and pensions) to stem the brain drain and motivate staff.
Continuous Professional Development (CPD): Provide regular training opportunities to upgrade skills, keep staff abreast of new medical advancements, and improve patient communication.
Ethical Conduct and Empathy Training: Conduct mandatory training on medical ethics, patient rights, empathy, and respectful communication, particularly towards low-income patients who may feel disempowered.
Performance Incentives: Introduce performance-based incentives for staff tied to patient satisfaction, quality of care, and efficiency, rather than just volume.
Safety and Security: Enhance security measures within hospital premises to protect staff from harassment or violence.
IV. Operational Efficiency and Patient-Centered Care:
Streamline Processes: Implement efficient patient flow systems, from registration to consultation, diagnosis, and treatment, to reduce long waiting times and bureaucratic bottlenecks.
Digitalization (Electronic Health Records - EHR):
Implement EHR systems to improve record-keeping, reduce errors, enhance data sharing among departments, and enable better patient tracking.
Digitalize appointment scheduling and billing to minimize human interface and reduce opportunities for corruption.
Focus on Primary Healthcare (PHC): Strengthen the referral system from PHC centers to secondary and tertiary public hospitals. Well-equipped and staffed PHCs can manage common ailments, reducing the burden on hospitals and making basic care accessible at the community level.
Culturally Sensitive Care: Train staff to understand and respect the cultural beliefs and practices of diverse patient populations, which can influence health-seeking behaviors.
Patient Feedback Mechanisms: Establish accessible and confidential channels for patients to provide feedback, lodge complaints, and make suggestions for improvement. Use this feedback to drive continuous improvement.
Transparency and Information: Clearly display service costs (if any), patients' rights, and grievance procedures. Provide clear information about treatment plans in a language patients understand.
V. Innovative Service Delivery Models:
Mobile Clinics and Outreach Programs: Implement mobile health clinics that travel to underserved rural communities, providing basic diagnostic, preventive, and primary care services, as well as health education.
Telemedicine: Leverage telemedicine for remote consultations, specialist opinions, and follow-ups, particularly for patients in remote areas where specialists are scarce. This can reduce travel costs and time for patients.
Community Health Workers (CHWs): Train and deploy CHWs from within the communities to act as a link between the community and the health system, providing basic health education, screening, and facilitating referrals.
Partnerships with NGOs and CSOs: Collaborate with non-governmental organizations and civil society organizations that have experience in delivering healthcare to underserved populations.
By implementing these strategies, public hospitals can move towards becoming trusted, accessible, and high-quality healthcare providers for all, especially the most vulnerable members of society.
4 months ago
Focus Africa-
Is cheap always better—or are we paying more in the long run for low-durability products?
No, cheap is not always better. While low-priced products offer a short-term financial gain, consumers and economies often pay a much higher price in the long run for their low durability. This is due to a cycle of frequent replacements and a host of hidden costs.
The True Cost of Cheap Goods-
The upfront price of an item is often just a small part of its total cost. The hidden costs of cheap, low-durability products include:
Frequent Replacement: Products that are not built to last break or wear out quickly. This forces consumers to repurchase the same item repeatedly. The combined cost of buying multiple cheap replacements over a few years often exceeds the initial price of a single, more durable, and higher-quality alternative. This cycle of consumption creates a financial drain on households.
Wasted Time and Effort: The time and effort spent on shopping for, purchasing, and disposing of low-durability products are significant. This includes the hassle of dealing with broken items, seeking repairs that may not be available, or waiting in queues to replace them.
Environmental Damage: The constant production and disposal of low-quality goods have a devastating environmental impact. These products are often made with cheap, non-sustainable materials and toxic chemicals, and are not designed for repair or recycling.
The resulting waste adds to landfills and pollutes local ecosystems, creating a burden on public waste management systems.
The Economic Principle of Planned Obsolescence-
This low-durability model is often driven by a concept known as planned obsolescence, where products are intentionally designed with a limited useful life.
The goal is to shorten the replacement cycle and guarantee repeat purchases, boosting sales and profits in the short term.
While this may seem to stimulate an economy, it is ultimately a flawed model that discourages innovation, creates consumer frustration, and wastes valuable resources.
This strategy works best in markets with limited competition and a large consumer base willing to accept lower quality for a lower price.
Is cheap always better—or are we paying more in the long run for low-durability products?
No, cheap is not always better. While low-priced products offer a short-term financial gain, consumers and economies often pay a much higher price in the long run for their low durability. This is due to a cycle of frequent replacements and a host of hidden costs.
The True Cost of Cheap Goods-
The upfront price of an item is often just a small part of its total cost. The hidden costs of cheap, low-durability products include:
Frequent Replacement: Products that are not built to last break or wear out quickly. This forces consumers to repurchase the same item repeatedly. The combined cost of buying multiple cheap replacements over a few years often exceeds the initial price of a single, more durable, and higher-quality alternative. This cycle of consumption creates a financial drain on households.
Wasted Time and Effort: The time and effort spent on shopping for, purchasing, and disposing of low-durability products are significant. This includes the hassle of dealing with broken items, seeking repairs that may not be available, or waiting in queues to replace them.
Environmental Damage: The constant production and disposal of low-quality goods have a devastating environmental impact. These products are often made with cheap, non-sustainable materials and toxic chemicals, and are not designed for repair or recycling.
The resulting waste adds to landfills and pollutes local ecosystems, creating a burden on public waste management systems.
The Economic Principle of Planned Obsolescence-
This low-durability model is often driven by a concept known as planned obsolescence, where products are intentionally designed with a limited useful life.
The goal is to shorten the replacement cycle and guarantee repeat purchases, boosting sales and profits in the short term.
While this may seem to stimulate an economy, it is ultimately a flawed model that discourages innovation, creates consumer frustration, and wastes valuable resources.
This strategy works best in markets with limited competition and a large consumer base willing to accept lower quality for a lower price.
4 months ago
Focus Nigeria-
How can Nigeria stop the “brain drain” of doctors and nurses?
Stopping the "brain drain" of doctors and nurses from Nigeria requires a comprehensive, sustained, and multi-faceted approach that addresses the root causes of their migration.
It's not just about offering more money, but creating an enabling environment where healthcare professionals can thrive, feel valued, and provide quality care.
Here's a detailed strategy to combat the brain drain:
I. Improve Working Conditions and Environment:
Modernize Infrastructure and Equipment:
Adequate Funding: Significantly increase the healthcare budget allocation (currently far below the Abuja Declaration's 15% target) and ensure transparent and efficient utilization of funds.
Investment in Facilities: Renovate existing hospitals and clinics, and build new, well-equipped facilities, especially in underserved areas.
Modern Technology: Equip hospitals with up-to-date diagnostic tools, surgical equipment, and specialized machinery (e.g., MRI, CT scanners, radiotherapy machines). Ensure regular maintenance and availability of spare parts.
Reliable Utilities: Provide stable electricity (e.g., through solar power solutions and reliable backup generators) and clean water supply in all healthcare facilities.
Ensure Safety and Security:
Protection for Staff: Implement robust security measures within hospitals and clinics to protect healthcare workers from violence, harassment, and kidnapping, especially in high-risk areas.
Occupational Health & Safety: Establish and enforce comprehensive occupational health and safety policies that prioritize the physical and mental well-being of nurses and doctors.
Manage Workload and Staffing:
Adequate Staffing: Recruit more healthcare professionals to reduce the excessive workload on existing staff. This might require increasing training capacity within Nigeria.
Fair Scheduling: Implement equitable work schedules and shifts to prevent burnout and ensure a healthy work-life balance.
II. Enhance Remuneration and Welfare:
Competitive Salaries and Allowances:
Offer competitive salaries and allowances that are comparable to what healthcare professionals could earn in other sectors within Nigeria or in regional countries. While matching Western salaries might be challenging, making local pay significantly better than the current reality is crucial.
Timely Payments: Ensure prompt and consistent payment of salaries and benefits to avoid the frustration caused by arrears.
Attractive Benefits Package:
Health Insurance: Provide comprehensive health insurance for healthcare workers and their families.
Housing and Transportation: Offer subsidized housing, housing allowances, or transportation support, especially for those in rural or high-cost urban areas.
Retirement Benefits: Ensure robust and reliable pension and retirement benefit schemes.
Non-Financial Incentives:
Recognition and Appreciation: Create a culture of recognition and appreciation for healthcare workers' dedication and hard work.
Professional Support: Provide a supportive work environment that values their contributions and addresses their concerns.
III. Professional Development and Career Advancement:
Continuous Professional Development (CPD):
Fund and facilitate regular training programs, workshops, and seminars to keep doctors and nurses updated on the latest medical practices, technologies, and research.
Encourage and sponsor participation in international conferences and training programs where relevant.
Career Progression Opportunities:
Establish clear and transparent career progression pathways based on merit, performance, and further specialization.
Provide opportunities for specialization, postgraduate studies, and leadership roles within the Nigerian healthcare system.
Research Funding:
Allocate dedicated funds for medical research within Nigeria to encourage innovation and give professionals reasons to stay and contribute locally.
Mentorship Programs:
Establish mentorship programs where experienced doctors and nurses guide and support younger professionals.
IV. Strengthening Education and Training within Nigeria:
Increase Training Capacity:
Expand the capacity of medical and nursing schools to train more healthcare professionals, ensuring that the increase in quantity does not compromise quality.
Curriculum Review: Regularly review and update medical and nursing curricula to meet international standards and address Nigeria's specific health challenges.
"Train to Retain" Programs:
Consider policies that incentivize graduates (e.g., scholarships tied to service in Nigeria for a specific period, especially in underserved areas). This must be coupled with improved conditions to avoid simply delaying their eventual departure.
Rural-Focused Training: Develop programs that train healthcare professionals with a specific focus on rural health challenges and encourage them to serve in those areas.
V. Governance, Accountability, and Policy Coherence:
Effective Leadership and Management:
Appoint competent, ethical, and visionary leaders in healthcare institutions who prioritize staff welfare and quality of care.
Ensure efficient administrative management across all levels of the health system.
Robust Accountability:
Establish transparent mechanisms for addressing grievances, investigating misconduct, and ensuring accountability for poor management or corruption within the health sector.
Long-Term National Health Policy:
Develop and consistently implement a stable, long-term national health policy that is insulated from political fluctuations and prioritizes human resources for health. President Tinubu's new health policy is a step in this direction, but consistent implementation is key.
Engage Professional Bodies:
Foster better dialogue and collaboration with professional associations like the Nigerian Medical Association (NMA) and the National Association of Nigerian Nurses and Midwives (NANNM) to address their concerns and gain their buy-in for reforms.
Leverage Diaspora Engagement:
Create structured programs to engage Nigerian healthcare professionals in the diaspora (e.g., for short-term missions, training, mentorship, or tele-medicine consultations). This can help transfer knowledge and build connections without demanding permanent return initially.
Combating the brain drain is a marathon, not a sprint. It requires substantial financial investment, political will, a commitment to systemic change, and a fundamental shift in how healthcare professionals are valued and treated in Nigeria.
How can Nigeria stop the “brain drain” of doctors and nurses?
Stopping the "brain drain" of doctors and nurses from Nigeria requires a comprehensive, sustained, and multi-faceted approach that addresses the root causes of their migration.
It's not just about offering more money, but creating an enabling environment where healthcare professionals can thrive, feel valued, and provide quality care.
Here's a detailed strategy to combat the brain drain:
I. Improve Working Conditions and Environment:
Modernize Infrastructure and Equipment:
Adequate Funding: Significantly increase the healthcare budget allocation (currently far below the Abuja Declaration's 15% target) and ensure transparent and efficient utilization of funds.
Investment in Facilities: Renovate existing hospitals and clinics, and build new, well-equipped facilities, especially in underserved areas.
Modern Technology: Equip hospitals with up-to-date diagnostic tools, surgical equipment, and specialized machinery (e.g., MRI, CT scanners, radiotherapy machines). Ensure regular maintenance and availability of spare parts.
Reliable Utilities: Provide stable electricity (e.g., through solar power solutions and reliable backup generators) and clean water supply in all healthcare facilities.
Ensure Safety and Security:
Protection for Staff: Implement robust security measures within hospitals and clinics to protect healthcare workers from violence, harassment, and kidnapping, especially in high-risk areas.
Occupational Health & Safety: Establish and enforce comprehensive occupational health and safety policies that prioritize the physical and mental well-being of nurses and doctors.
Manage Workload and Staffing:
Adequate Staffing: Recruit more healthcare professionals to reduce the excessive workload on existing staff. This might require increasing training capacity within Nigeria.
Fair Scheduling: Implement equitable work schedules and shifts to prevent burnout and ensure a healthy work-life balance.
II. Enhance Remuneration and Welfare:
Competitive Salaries and Allowances:
Offer competitive salaries and allowances that are comparable to what healthcare professionals could earn in other sectors within Nigeria or in regional countries. While matching Western salaries might be challenging, making local pay significantly better than the current reality is crucial.
Timely Payments: Ensure prompt and consistent payment of salaries and benefits to avoid the frustration caused by arrears.
Attractive Benefits Package:
Health Insurance: Provide comprehensive health insurance for healthcare workers and their families.
Housing and Transportation: Offer subsidized housing, housing allowances, or transportation support, especially for those in rural or high-cost urban areas.
Retirement Benefits: Ensure robust and reliable pension and retirement benefit schemes.
Non-Financial Incentives:
Recognition and Appreciation: Create a culture of recognition and appreciation for healthcare workers' dedication and hard work.
Professional Support: Provide a supportive work environment that values their contributions and addresses their concerns.
III. Professional Development and Career Advancement:
Continuous Professional Development (CPD):
Fund and facilitate regular training programs, workshops, and seminars to keep doctors and nurses updated on the latest medical practices, technologies, and research.
Encourage and sponsor participation in international conferences and training programs where relevant.
Career Progression Opportunities:
Establish clear and transparent career progression pathways based on merit, performance, and further specialization.
Provide opportunities for specialization, postgraduate studies, and leadership roles within the Nigerian healthcare system.
Research Funding:
Allocate dedicated funds for medical research within Nigeria to encourage innovation and give professionals reasons to stay and contribute locally.
Mentorship Programs:
Establish mentorship programs where experienced doctors and nurses guide and support younger professionals.
IV. Strengthening Education and Training within Nigeria:
Increase Training Capacity:
Expand the capacity of medical and nursing schools to train more healthcare professionals, ensuring that the increase in quantity does not compromise quality.
Curriculum Review: Regularly review and update medical and nursing curricula to meet international standards and address Nigeria's specific health challenges.
"Train to Retain" Programs:
Consider policies that incentivize graduates (e.g., scholarships tied to service in Nigeria for a specific period, especially in underserved areas). This must be coupled with improved conditions to avoid simply delaying their eventual departure.
Rural-Focused Training: Develop programs that train healthcare professionals with a specific focus on rural health challenges and encourage them to serve in those areas.
V. Governance, Accountability, and Policy Coherence:
Effective Leadership and Management:
Appoint competent, ethical, and visionary leaders in healthcare institutions who prioritize staff welfare and quality of care.
Ensure efficient administrative management across all levels of the health system.
Robust Accountability:
Establish transparent mechanisms for addressing grievances, investigating misconduct, and ensuring accountability for poor management or corruption within the health sector.
Long-Term National Health Policy:
Develop and consistently implement a stable, long-term national health policy that is insulated from political fluctuations and prioritizes human resources for health. President Tinubu's new health policy is a step in this direction, but consistent implementation is key.
Engage Professional Bodies:
Foster better dialogue and collaboration with professional associations like the Nigerian Medical Association (NMA) and the National Association of Nigerian Nurses and Midwives (NANNM) to address their concerns and gain their buy-in for reforms.
Leverage Diaspora Engagement:
Create structured programs to engage Nigerian healthcare professionals in the diaspora (e.g., for short-term missions, training, mentorship, or tele-medicine consultations). This can help transfer knowledge and build connections without demanding permanent return initially.
Combating the brain drain is a marathon, not a sprint. It requires substantial financial investment, political will, a commitment to systemic change, and a fundamental shift in how healthcare professionals are valued and treated in Nigeria.
4 months ago
The authoritarian voice that all Chinese officials use to intimidate everyone around the world "YOU ARE PLAYING WITH FIRE"
All books texts tells of the Chinese dragon spits fire but no confirmation of burnt out area caused by dragon fire and we haven't seen a skeleton of the Chinese dragon. The world has seen those of dinosaur.
Please let's know when they find a Chinese dragon skeleton.
The phrase "you are playing with fire" is a widely recognized idiom that serves as a strong warning. It's often used to caution someone against a risky or dangerous action that could lead to severe, negative consequences. The "fire" in the phrase represents the potential for danger, destruction, or getting burned, while "playing" suggests a careless or reckless attitude towards that danger.
The phrase has been used in international diplomacy and political rhetoric for decades, but it gained significant traction in the context of discussions around Taiwan's status, particularly from Chinese officials. The Chinese government uses this phrase to signal its unwavering stance that Taiwan is an inalienable part of China and that any actions suggesting otherwise are a direct challenge to its sovereignty and national security.
When directed at individuals, political leaders, or other countries, the phrase serves several purposes:
A direct threat: It implies that continued actions or statements perceived as challenging China's "One China" principle will not be tolerated and could provoke a severe response, including military action.
A show of resolve: It signals to both domestic and international audiences that China is firm in its position and is prepared to take significant steps to defend its interests.
A warning to allies: It's often used to discourage other countries from deepening their political or military ties with Taiwan, framing such actions as provocative and destabilizing to regional peace.
A diplomatic tool: While the phrase is aggressive, it is also a form of diplomatic communication. It's a way of drawing a "red line" without immediately resorting to more drastic measures. It's a warning shot, meant to deter further escalation.
In the context of Taiwan, the "fire" refers to the potential for a military conflict, which would have devastating consequences for all parties involved and could destabilize the entire global economy. The use of the phrase by Chinese officials is a deliberate and consistent part of their strategy to maintain pressure on Taiwan and its international partners, aiming to shape the narrative and prevent any actions that could be seen as moving towards formal independence.
++++++++++++++++++++++++++++++++++++++++++++
China's authoritative and coercive action comment around Asia and the world.
The phrase "you are playing with fire" is a core element of China's diplomatic lexicon, and its use is not limited to the issue of Taiwan. It is a powerful and intentionally provocative idiom that the Chinese government employs to articulate its "red lines" and warn against any actions it views as a direct challenge to its sovereignty, national security, and core interests.
Beyond Taiwan, this phrase and similar language are consistently used in response to criticism or actions regarding:
The South China Sea: When countries like the Philippines or Vietnam, backed by the United States and its allies, challenge China's expansive territorial claims and maritime activities in the South China Sea, Beijing's response often includes strong warnings. These warnings, while not always using the exact phrase, convey the same message of imminent danger and potential for escalation. The "fire" in this context represents the risk of military confrontation over contested islands and waterways.
Human Rights Issues: Criticisms from foreign governments and international organizations regarding China's human rights record, particularly the treatment of Uyghurs in Xinjiang, the suppression of democracy in Hong Kong, and the repression of dissent, are met with fierce rejection. Chinese officials consistently frame such criticism as "interference in China's internal affairs." The "playing with fire" metaphor is used to warn that such meddling could lead to serious damage to diplomatic and economic relationships, and that those who push these issues too far will face consequences.
Economic and Trade Disputes: In the context of economic disputes, such as tariffs, sanctions, or export controls, China may use similar language to warn against actions it sees as a hostile attempt to contain its rise. The "fire" here is the potential for a full-blown trade war or technological decoupling, which would harm not only China but also the global economy.
The "One China" Principle: While Taiwan is the most prominent example, the "One China" principle is a broader issue that also includes Hong Kong, Tibet, and any other region China claims as its own. Any international comment or action that seems to lend legitimacy to separatist movements or challenges Beijing's authority over these regions can provoke this kind of rhetorical warning.
In essence, the phrase "you are playing with fire" is a rhetorical strategy that serves as:
A deterrence signal: It's a clear and unmistakable warning that a specific action is seen as a major provocation.
A framing device: It casts the other party as the aggressor—the one "playing" carelessly with a dangerous situation—and positions China as the rational actor trying to prevent a catastrophe.
A mobilization tool: By using such strong and evocative language, China's leadership can rally domestic nationalistic sentiment and support for its policies, reinforcing the idea that the country is under threat from external forces.
The consistent and broad application of this phrase highlights that it is not a casual or offhand comment, but a deliberate and calculated part of China's diplomatic approach to signal its resolve and to discourage what it perceives as challenges to its authority and interests.
All books texts tells of the Chinese dragon spits fire but no confirmation of burnt out area caused by dragon fire and we haven't seen a skeleton of the Chinese dragon. The world has seen those of dinosaur.
Please let's know when they find a Chinese dragon skeleton.
The phrase "you are playing with fire" is a widely recognized idiom that serves as a strong warning. It's often used to caution someone against a risky or dangerous action that could lead to severe, negative consequences. The "fire" in the phrase represents the potential for danger, destruction, or getting burned, while "playing" suggests a careless or reckless attitude towards that danger.
The phrase has been used in international diplomacy and political rhetoric for decades, but it gained significant traction in the context of discussions around Taiwan's status, particularly from Chinese officials. The Chinese government uses this phrase to signal its unwavering stance that Taiwan is an inalienable part of China and that any actions suggesting otherwise are a direct challenge to its sovereignty and national security.
When directed at individuals, political leaders, or other countries, the phrase serves several purposes:
A direct threat: It implies that continued actions or statements perceived as challenging China's "One China" principle will not be tolerated and could provoke a severe response, including military action.
A show of resolve: It signals to both domestic and international audiences that China is firm in its position and is prepared to take significant steps to defend its interests.
A warning to allies: It's often used to discourage other countries from deepening their political or military ties with Taiwan, framing such actions as provocative and destabilizing to regional peace.
A diplomatic tool: While the phrase is aggressive, it is also a form of diplomatic communication. It's a way of drawing a "red line" without immediately resorting to more drastic measures. It's a warning shot, meant to deter further escalation.
In the context of Taiwan, the "fire" refers to the potential for a military conflict, which would have devastating consequences for all parties involved and could destabilize the entire global economy. The use of the phrase by Chinese officials is a deliberate and consistent part of their strategy to maintain pressure on Taiwan and its international partners, aiming to shape the narrative and prevent any actions that could be seen as moving towards formal independence.
++++++++++++++++++++++++++++++++++++++++++++
China's authoritative and coercive action comment around Asia and the world.
The phrase "you are playing with fire" is a core element of China's diplomatic lexicon, and its use is not limited to the issue of Taiwan. It is a powerful and intentionally provocative idiom that the Chinese government employs to articulate its "red lines" and warn against any actions it views as a direct challenge to its sovereignty, national security, and core interests.
Beyond Taiwan, this phrase and similar language are consistently used in response to criticism or actions regarding:
The South China Sea: When countries like the Philippines or Vietnam, backed by the United States and its allies, challenge China's expansive territorial claims and maritime activities in the South China Sea, Beijing's response often includes strong warnings. These warnings, while not always using the exact phrase, convey the same message of imminent danger and potential for escalation. The "fire" in this context represents the risk of military confrontation over contested islands and waterways.
Human Rights Issues: Criticisms from foreign governments and international organizations regarding China's human rights record, particularly the treatment of Uyghurs in Xinjiang, the suppression of democracy in Hong Kong, and the repression of dissent, are met with fierce rejection. Chinese officials consistently frame such criticism as "interference in China's internal affairs." The "playing with fire" metaphor is used to warn that such meddling could lead to serious damage to diplomatic and economic relationships, and that those who push these issues too far will face consequences.
Economic and Trade Disputes: In the context of economic disputes, such as tariffs, sanctions, or export controls, China may use similar language to warn against actions it sees as a hostile attempt to contain its rise. The "fire" here is the potential for a full-blown trade war or technological decoupling, which would harm not only China but also the global economy.
The "One China" Principle: While Taiwan is the most prominent example, the "One China" principle is a broader issue that also includes Hong Kong, Tibet, and any other region China claims as its own. Any international comment or action that seems to lend legitimacy to separatist movements or challenges Beijing's authority over these regions can provoke this kind of rhetorical warning.
In essence, the phrase "you are playing with fire" is a rhetorical strategy that serves as:
A deterrence signal: It's a clear and unmistakable warning that a specific action is seen as a major provocation.
A framing device: It casts the other party as the aggressor—the one "playing" carelessly with a dangerous situation—and positions China as the rational actor trying to prevent a catastrophe.
A mobilization tool: By using such strong and evocative language, China's leadership can rally domestic nationalistic sentiment and support for its policies, reinforcing the idea that the country is under threat from external forces.
The consistent and broad application of this phrase highlights that it is not a casual or offhand comment, but a deliberate and calculated part of China's diplomatic approach to signal its resolve and to discourage what it perceives as challenges to its authority and interests.
4 months ago
Is the World and mainstream media Rewarding Hamas for Its Atrocities and condemning Israel for defending itself? (Part2)
++++++++++++++++++++++++++++++++++++++++++
HAMAS SURRENDER NOW- WAR GOES ON UNTIL HAMAS SURRENDER.
++++++++++++++++++++++++++++++++++++++++++
The call for Hamas's surrender is not a universally adopted issue for a number of complex and interconnected reasons, which are rooted in political, historical, and ideological factors.
1. Hamas's Ideology and Strategic Goals:
Rejection of Surrender: Hamas, as an organization, fundamentally rejects the idea of surrender. Its charter and core ideology are based on armed resistance against Israel. Surrendering would be seen as a betrayal of its principles and a complete defeat of the Palestinian cause, as the group defines it. From their perspective, their actions are part of a broader "liberation" struggle.
Hostages as Leverage: Hamas uses the hostages as its most powerful bargaining chip. A unilateral surrender would mean giving up this leverage without securing any of its demands, such as a permanent ceasefire, the release of Palestinian prisoners, or the end of the Israeli blockade of Gaza.
2. Diverse International and Regional Perspectives:
Political Alignments: The international community is not a unified entity. Many countries and political groups have different relationships with Israel and the Palestinians. Some, particularly in the Global South and the Middle East, may view Hamas as a legitimate resistance movement against Israeli occupation, rather than solely as a terrorist organization. For these groups, a call for surrender would be seen as siding with Israel and ignoring the Palestinian struggle.
Focus on the Humanitarian Crisis: Many international bodies and humanitarian organizations prioritize the immediate cessation of violence and the delivery of aid to the civilian population in Gaza. They believe that a call for a ceasefire is a more achievable and humane goal than demanding a surrender, which could prolong the conflict and lead to more civilian deaths. Their focus is on alleviating suffering, not on a specific military or political outcome.
Distrust of Israeli Intentions: Some critics of Israel believe that a Hamas surrender would not lead to a lasting peace or a political solution for the Palestinians. They argue that Israel would simply consolidate its control over the region and that a post-Hamas Gaza would not be a viable, self-governing entity. They point to the long history of occupation and conflict as evidence that Israel is not genuinely interested in a two-state solution.
3. The Role of the Palestinian Population:
Hamas's Popularity: While many Palestinians do not support Hamas, the group's popularity has at times been linked to its role in providing social services and its perceived resistance to Israeli policies. For some Palestinians, a call for Hamas's surrender is viewed as a call to accept a status quo of Israeli control, which they oppose.
Lack of a Viable Alternative: There is no universally recognized or powerful alternative to Hamas to govern Gaza. The Palestinian Authority, which governs parts of the West Bank, is widely seen as weak and ineffective by many Palestinians. As a result, a call for Hamas's surrender without a clear and legitimate plan for a post-Hamas Gaza is seen as creating a power vacuum that could lead to even greater instability.
4. The Practical and Strategic Unlikelihood of Surrender:
Military Futility: From a purely practical standpoint, many observers believe that a call for Hamas's surrender is a futile gesture. Hamas is a decentralized and ideologically driven organization. Even if its top leaders were killed or captured, the group's ideology and capacity for resistance could persist, as has been the case with other armed groups in the past.
The "Forever War" Narrative: Some analysts argue that a call for Hamas's total elimination by force is a strategy that leads to a "forever war" and that a political solution, even if imperfect, is the only way to achieve a lasting peace. They believe that military action alone cannot solve a deeply rooted political and ideological conflict.
In essence, while the desire to see an end to violence is widespread, the specific demand for Hamas's unconditional surrender is not universally adopted because it is seen by different groups as either unrealistic, politically biased, counterproductive to humanitarian goals, or a failure to address the underlying causes of the conflict.
+++++++++++++++++++++++++++++++++++++++++++
++++++++++++++++++++++++++++++++++++++++++
HAMAS SURRENDER NOW- WAR GOES ON UNTIL HAMAS SURRENDER.
++++++++++++++++++++++++++++++++++++++++++
The call for Hamas's surrender is not a universally adopted issue for a number of complex and interconnected reasons, which are rooted in political, historical, and ideological factors.
1. Hamas's Ideology and Strategic Goals:
Rejection of Surrender: Hamas, as an organization, fundamentally rejects the idea of surrender. Its charter and core ideology are based on armed resistance against Israel. Surrendering would be seen as a betrayal of its principles and a complete defeat of the Palestinian cause, as the group defines it. From their perspective, their actions are part of a broader "liberation" struggle.
Hostages as Leverage: Hamas uses the hostages as its most powerful bargaining chip. A unilateral surrender would mean giving up this leverage without securing any of its demands, such as a permanent ceasefire, the release of Palestinian prisoners, or the end of the Israeli blockade of Gaza.
2. Diverse International and Regional Perspectives:
Political Alignments: The international community is not a unified entity. Many countries and political groups have different relationships with Israel and the Palestinians. Some, particularly in the Global South and the Middle East, may view Hamas as a legitimate resistance movement against Israeli occupation, rather than solely as a terrorist organization. For these groups, a call for surrender would be seen as siding with Israel and ignoring the Palestinian struggle.
Focus on the Humanitarian Crisis: Many international bodies and humanitarian organizations prioritize the immediate cessation of violence and the delivery of aid to the civilian population in Gaza. They believe that a call for a ceasefire is a more achievable and humane goal than demanding a surrender, which could prolong the conflict and lead to more civilian deaths. Their focus is on alleviating suffering, not on a specific military or political outcome.
Distrust of Israeli Intentions: Some critics of Israel believe that a Hamas surrender would not lead to a lasting peace or a political solution for the Palestinians. They argue that Israel would simply consolidate its control over the region and that a post-Hamas Gaza would not be a viable, self-governing entity. They point to the long history of occupation and conflict as evidence that Israel is not genuinely interested in a two-state solution.
3. The Role of the Palestinian Population:
Hamas's Popularity: While many Palestinians do not support Hamas, the group's popularity has at times been linked to its role in providing social services and its perceived resistance to Israeli policies. For some Palestinians, a call for Hamas's surrender is viewed as a call to accept a status quo of Israeli control, which they oppose.
Lack of a Viable Alternative: There is no universally recognized or powerful alternative to Hamas to govern Gaza. The Palestinian Authority, which governs parts of the West Bank, is widely seen as weak and ineffective by many Palestinians. As a result, a call for Hamas's surrender without a clear and legitimate plan for a post-Hamas Gaza is seen as creating a power vacuum that could lead to even greater instability.
4. The Practical and Strategic Unlikelihood of Surrender:
Military Futility: From a purely practical standpoint, many observers believe that a call for Hamas's surrender is a futile gesture. Hamas is a decentralized and ideologically driven organization. Even if its top leaders were killed or captured, the group's ideology and capacity for resistance could persist, as has been the case with other armed groups in the past.
The "Forever War" Narrative: Some analysts argue that a call for Hamas's total elimination by force is a strategy that leads to a "forever war" and that a political solution, even if imperfect, is the only way to achieve a lasting peace. They believe that military action alone cannot solve a deeply rooted political and ideological conflict.
In essence, while the desire to see an end to violence is widespread, the specific demand for Hamas's unconditional surrender is not universally adopted because it is seen by different groups as either unrealistic, politically biased, counterproductive to humanitarian goals, or a failure to address the underlying causes of the conflict.
+++++++++++++++++++++++++++++++++++++++++++
4 months ago
How to Implement AI‑Powered Product Recommendations in an Amazon clone app
What if your app could predict what users want, before they even type in a search? That’s the power of AI recommendations. Do you want to know how to implement AI-powered product recommendations in your Amazon clone? Here are some steps. Let's dive in.
What is AI-Powered Recommendation?
An artificially intelligent system that makes real-time product recommendations to consumers based on their interests, behaviour, and previous purchases is known as an AI-powered recommendation system in e-commerce. AI customises the shopping experience to boost sales, engagement, and customer satisfaction rather than displaying the same product list to every user.
Types of recommendation strategies:
1. Collaborative Filtering
Collaborative Filtering is a recommendation strategy that recommends products based on user activity and preferences rather than product information in an Amazon-like app.
User-based collaborative filtering detects folks who share similar interests. If a user likes a product, it will be recommended to another person who shares their interests.
Item-based collaborative filtering: This type of filtering shows recommendations based on similarities. For example, it recommends a phone case to the people who purchased New phones.
2. Content-based Filtering:
Content-based filtering recommends products based on the traits or features that the customer has previously purchased. For example, if you frequently buy or see bags, the algorithm would suggest alternatives or products with comparable characteristics such as brand, style, price range, or material.
3. Hybrid Filtering:
Hybrid filtering blends collaborative filtering, which proposes products based on the preferences of other users, with content-based filtering, which recommends items similar to those a user has previously liked. This strategy takes advantage of both methods' strengths while correcting their faults, yielding more accurate and personalised recommendations.
4. Trending and popular items:
In an Amazon clone website, Trending or Popular Items recommendations highlight things that are currently best-sellers, most viewed, or highly rated throughout the platform or within a category. Helping consumers find popular, in-demand items while increasing interaction and revenue.
5. Personalized rankings:
Personalized rankings reorder the search results or other lists of items based on users' preferences and behaviour. Instead of showing the same products to every user, it improves the user experience and increases the platform engagement.
Implementing AI-powered recommendations in an Amazon clone app:
Implement AI-powered suggestions in your Amazon clone. You should concentrate on collecting data, selecting the best AI solution, and optimising recommendations.
1. Data Collection and analysis:
Collect vast data: Gather the users' purchase history, product preferences, browsing habits, and product interactions such as clicks, add to cart, and reviews. Collecting these diverse data points provides a detailed picture of each customer's interests and habits.
2. Choosing the Right AI Solution:
Utilise data points: Analyse individual consumer preferences, detect bigger trends across users, and create dynamic customer profiles that evolve as new data is received.
Ensure data privacy: When developing AI-powered product suggestions, you must protect the privacy and security of user data. Encryption, secure servers, and access controls can all help to protect user data from unauthorised access. This is especially important when dealing with sensitive information such as purchasing history, behaviour, or personal details.
Consider Your Needs: Before deciding on an AI recommendation, you should first understand your business goals, budget, and technical resources.
Investigate diverse AI models: There are several recommendation models, each with a unique function. There are three types of filtering: collaborative, content-based, and hybrid.
Look for user-friendly options: If you're not ready to start from scratch with an Amazon clone website, look for choices that are easy to use. Many e-commerce platforms have built-in AI recommendation algorithms or third-party applications.
3. Implementing and optimizing recommendations:
Integrate cross-platform: Ensure that your recommendations are consistent and personalised across all platforms, including the website, email marketing, mobile app, and even customer support chat. This will improve the user experience and maintain personalisation seamlessly.
Use various formats: Use several recommendation styles, such as pop-ups and inline sections, to keep shoppers' attention at different phases of their purchasing journey.
A/B testing and optimisation: Continuously monitor the performance of the recommendations and make improvements depending on data and user input.
Focus on user experience: Make sure that recommendations are not only appropriate but also easy to navigate, quick to load, and visually integrated on mobile sites.
Prioritise Explainability: Be open about how recommendations are made, and give users control over their preferences.
Begin small, then scale: Start with a pilot or test group to validate performance and get feedback. Use this feedback to develop and expand your recommendation system throughout the platform.
Benefits of AI-powered recommendations:
1. Improved conversion performance:
The AI algorithm examines clients' browsing histories and purchasing habits to help them get what they want without using their hands. This will boost your Amazon clone conversion rate.
2. Enhanced user experience:
This AI-powered customised suggestion saves users time and effort by guiding them to the proper products. The end outcome is customer satisfaction and a good purchasing experience.
3. Increased average order value:
AI-powered suggestions in your Amazon clone app encourage customers to buy complementary, upsell, and cross-sell items, which raises the overall order value.
4. Insights based on data:
Artificial intelligence (AI) recommendation systems gather and analyse consumer data to learn about preferences and purchasing habits. Businesses can use this to enhance their marketing, select better products to sell, and more effectively manage their inventory.
5. Improved customer retention:
When users consistently receive relevant product recommendations, they are more likely to return to the platform. This strengthens brand presence and generates recurring sales.
6. Enhanced marketing strategies:
AI-powered recommendations customize marketing strategies based on each customer’s individual preferences and behaviors. This personalized approach results in more relevant and engaging marketing campaigns that resonate better with customers, ultimately increasing their interest and likelihood to respond positively.
7. Reduced cart abandonment:
AI-powered recommendations lower cart abandonment by using personalized recommendations, timely reminders, and providing discounts or free shipping. These strategies help users complete their purchases and increase the overall sales rates in your Amazon clone website.
8. Real-time discovery:
This enables AI to make real-time product recommendations to users based on their interests, assisting consumers in finding things they may not have previously found. It is most helpful in vast product catalogues where customers may find manual searching daunting. AI speeds up, simplifies, and enhances the pleasure of shopping by providing timely and pertinent recommendations.
Summing up:
I hope this blog helps you understand the importance of Artificial Intelligence in product recommendations for your Amazon clone app.
It covers the implementation of AI-powered recommendation systems, different types of recommendation strategies, and their benefits.
Now is the perfect time to launch AI-powered recommendations in your Amazon clone app.
https://www.trioangle.com/...
#EcommercePlatform #TechForBusiness #AmazonCloneScript #USAeCommerce #EcommerceLondon #MiddleEastEcommerce #SAOnlineStore # OnlineMarketplace
#MultiVendorMarketplace #DigitalRetailUSA #UAEStartupScene #MarketplaceTrends
What if your app could predict what users want, before they even type in a search? That’s the power of AI recommendations. Do you want to know how to implement AI-powered product recommendations in your Amazon clone? Here are some steps. Let's dive in.
What is AI-Powered Recommendation?
An artificially intelligent system that makes real-time product recommendations to consumers based on their interests, behaviour, and previous purchases is known as an AI-powered recommendation system in e-commerce. AI customises the shopping experience to boost sales, engagement, and customer satisfaction rather than displaying the same product list to every user.
Types of recommendation strategies:
1. Collaborative Filtering
Collaborative Filtering is a recommendation strategy that recommends products based on user activity and preferences rather than product information in an Amazon-like app.
User-based collaborative filtering detects folks who share similar interests. If a user likes a product, it will be recommended to another person who shares their interests.
Item-based collaborative filtering: This type of filtering shows recommendations based on similarities. For example, it recommends a phone case to the people who purchased New phones.
2. Content-based Filtering:
Content-based filtering recommends products based on the traits or features that the customer has previously purchased. For example, if you frequently buy or see bags, the algorithm would suggest alternatives or products with comparable characteristics such as brand, style, price range, or material.
3. Hybrid Filtering:
Hybrid filtering blends collaborative filtering, which proposes products based on the preferences of other users, with content-based filtering, which recommends items similar to those a user has previously liked. This strategy takes advantage of both methods' strengths while correcting their faults, yielding more accurate and personalised recommendations.
4. Trending and popular items:
In an Amazon clone website, Trending or Popular Items recommendations highlight things that are currently best-sellers, most viewed, or highly rated throughout the platform or within a category. Helping consumers find popular, in-demand items while increasing interaction and revenue.
5. Personalized rankings:
Personalized rankings reorder the search results or other lists of items based on users' preferences and behaviour. Instead of showing the same products to every user, it improves the user experience and increases the platform engagement.
Implementing AI-powered recommendations in an Amazon clone app:
Implement AI-powered suggestions in your Amazon clone. You should concentrate on collecting data, selecting the best AI solution, and optimising recommendations.
1. Data Collection and analysis:
Collect vast data: Gather the users' purchase history, product preferences, browsing habits, and product interactions such as clicks, add to cart, and reviews. Collecting these diverse data points provides a detailed picture of each customer's interests and habits.
2. Choosing the Right AI Solution:
Utilise data points: Analyse individual consumer preferences, detect bigger trends across users, and create dynamic customer profiles that evolve as new data is received.
Ensure data privacy: When developing AI-powered product suggestions, you must protect the privacy and security of user data. Encryption, secure servers, and access controls can all help to protect user data from unauthorised access. This is especially important when dealing with sensitive information such as purchasing history, behaviour, or personal details.
Consider Your Needs: Before deciding on an AI recommendation, you should first understand your business goals, budget, and technical resources.
Investigate diverse AI models: There are several recommendation models, each with a unique function. There are three types of filtering: collaborative, content-based, and hybrid.
Look for user-friendly options: If you're not ready to start from scratch with an Amazon clone website, look for choices that are easy to use. Many e-commerce platforms have built-in AI recommendation algorithms or third-party applications.
3. Implementing and optimizing recommendations:
Integrate cross-platform: Ensure that your recommendations are consistent and personalised across all platforms, including the website, email marketing, mobile app, and even customer support chat. This will improve the user experience and maintain personalisation seamlessly.
Use various formats: Use several recommendation styles, such as pop-ups and inline sections, to keep shoppers' attention at different phases of their purchasing journey.
A/B testing and optimisation: Continuously monitor the performance of the recommendations and make improvements depending on data and user input.
Focus on user experience: Make sure that recommendations are not only appropriate but also easy to navigate, quick to load, and visually integrated on mobile sites.
Prioritise Explainability: Be open about how recommendations are made, and give users control over their preferences.
Begin small, then scale: Start with a pilot or test group to validate performance and get feedback. Use this feedback to develop and expand your recommendation system throughout the platform.
Benefits of AI-powered recommendations:
1. Improved conversion performance:
The AI algorithm examines clients' browsing histories and purchasing habits to help them get what they want without using their hands. This will boost your Amazon clone conversion rate.
2. Enhanced user experience:
This AI-powered customised suggestion saves users time and effort by guiding them to the proper products. The end outcome is customer satisfaction and a good purchasing experience.
3. Increased average order value:
AI-powered suggestions in your Amazon clone app encourage customers to buy complementary, upsell, and cross-sell items, which raises the overall order value.
4. Insights based on data:
Artificial intelligence (AI) recommendation systems gather and analyse consumer data to learn about preferences and purchasing habits. Businesses can use this to enhance their marketing, select better products to sell, and more effectively manage their inventory.
5. Improved customer retention:
When users consistently receive relevant product recommendations, they are more likely to return to the platform. This strengthens brand presence and generates recurring sales.
6. Enhanced marketing strategies:
AI-powered recommendations customize marketing strategies based on each customer’s individual preferences and behaviors. This personalized approach results in more relevant and engaging marketing campaigns that resonate better with customers, ultimately increasing their interest and likelihood to respond positively.
7. Reduced cart abandonment:
AI-powered recommendations lower cart abandonment by using personalized recommendations, timely reminders, and providing discounts or free shipping. These strategies help users complete their purchases and increase the overall sales rates in your Amazon clone website.
8. Real-time discovery:
This enables AI to make real-time product recommendations to users based on their interests, assisting consumers in finding things they may not have previously found. It is most helpful in vast product catalogues where customers may find manual searching daunting. AI speeds up, simplifies, and enhances the pleasure of shopping by providing timely and pertinent recommendations.
Summing up:
I hope this blog helps you understand the importance of Artificial Intelligence in product recommendations for your Amazon clone app.
It covers the implementation of AI-powered recommendation systems, different types of recommendation strategies, and their benefits.
Now is the perfect time to launch AI-powered recommendations in your Amazon clone app.
https://www.trioangle.com/...
#EcommercePlatform #TechForBusiness #AmazonCloneScript #USAeCommerce #EcommerceLondon #MiddleEastEcommerce #SAOnlineStore # OnlineMarketplace
#MultiVendorMarketplace #DigitalRetailUSA #UAEStartupScene #MarketplaceTrends
4 months ago
How has North Korea allegedly used cybercrime (crypto theft, ransomware) to fund its regime?
North Korea has allegedly leveraged cybercrime, particularly cryptocurrency theft and ransomware, as a crucial and increasingly preferred method to fund its regime and, specifically, its illicit weapons programs.
This strategy is a direct response to the crippling international sanctions imposed on the country.
Here's how they've allegedly done it:
1. Circumventing Sanctions for Hard Currency:
Financial Isolation: North Korea faces severe international sanctions that cut off its access to traditional global financial systems. This makes it extremely difficult for the regime to acquire the foreign currency (like U.S. dollars or Euros) needed to import goods, technology, and components for its military and luxury items for its elite.
Cryptocurrency as an Alternative: Cryptocurrencies operate largely outside traditional banking regulations and centralized financial institutions. This makes them an attractive alternative for a sanctioned state. By stealing crypto, North Korea effectively generates hard currency that is harder to trace and block.
Funding WMD Programs: UN reports, U.S. government assessments, and cybersecurity firm analyses consistently state that the proceeds from these cybercrimes directly fund North Korea's prohibited weapons of mass destruction (WMD) programs, including nuclear weapons and ballistic missiles. Some estimates suggest cybercrime accounts for a significant portion, potentially 40% to 50% or more, of the regime's foreign currency income.
2. Cryptocurrency Theft: The Primary Goldmine
Massive Scale: North Korean hacking groups, notably the Lazarus Group and its sub-units like BlueNoroff, have stolen billions of dollars in cryptocurrency. For example, UN experts reported investigating 58 suspected North Korean cyberattacks between 2017 and 2023, valued at approximately $3 billion. The FBI recently attributed a single $1.5 billion hack against Bybit in February 2025 to North Korean actors.
Targeting Crypto Exchanges and DeFi Platforms:
Direct Hacks: They target centralized cryptocurrency exchanges, exploiting vulnerabilities in their security systems to steal large amounts of various cryptocurrencies.
Decentralized Finance (DeFi) Exploits: As the crypto landscape evolved, North Korean hackers shifted to more vulnerable DeFi platforms and "bridges" (which facilitate asset transfer between different blockchains). Notorious examples include the Harmony Horizon Bridge ($100 million+) and the Sky Mavis Ronin Bridge ($600 million+). DeFi platforms often have less stringent security and regulatory oversight, making them "softer targets."
Sophisticated Social Engineering: They employ elaborate social engineering tactics to gain initial access:
Fake Job Offers: Creating fake companies, LinkedIn profiles, and seemingly legitimate job opportunities to trick employees of crypto firms into downloading malicious software or revealing credentials.
Impersonation: Impersonating venture capitalists, recruiters, or other legitimate business contacts.
Deepfake Technology: Increasingly, they use AI-enabled deepfake technologies in video calls to disguise their appearance and build trust with targets.
Laundering Stolen Funds: After stealing the cryptocurrency, they employ sophisticated laundering techniques to convert it into fiat currency (like USD). This involves:
Mixing Services: Using "crypto mixers" like Tornado Cash (which was sanctioned by the U.S. Treasury for its role in laundering North Korean funds) to obscure the origin of the stolen assets.
Chain Hopping: Moving funds across multiple different blockchains to complicate tracing efforts.
Dispersing Funds: Spreading stolen assets across thousands of addresses to make tracking harder.
Conversion to Fiat: Eventually converting the "cleaned" crypto into traditional currencies through various brokers, often in countries with weaker anti-money laundering regulations.
3. Ransomware Attacks: Another Revenue Stream
Extortion and Disruption: Groups like Andariel, a Lazarus sub-group, have deployed ransomware (e.g., Maui ransomware) against a range of targets, including U.S. hospitals and healthcare providers.
Demanding Crypto Payments: Ransomware payments are typically demanded in cryptocurrency, providing another direct avenue for generating funds that are difficult to trace.
Double Extortion: Beyond just encrypting data, some groups engage in "double extortion," threatening to leak stolen sensitive data if the ransom isn't paid, increasing pressure on victims.
4. Illicit IT Worker Schemes:
While not strictly "cybercrime" in the hacking sense, this is a related and significant revenue stream that leverages North Korea's cyber talent.
Disguised Workers: North Korean IT workers, often highly skilled in programming and software development, fraudulently obtain remote freelance jobs globally, using false identities and documentation.
Funneling Wages: The wages earned from these legitimate-looking jobs are then funneled back to the North Korean regime, providing another source of foreign currency. Some reports indicate these workers also insert backdoors or malware into corporate systems they work on, potentially enabling future cybercrime or espionage.
In essence, North Korea has become an innovator in state-sponsored cybercrime out of necessity. Facing stringent sanctions, its regime has adapted by exploiting the nascent and less-regulated cryptocurrency ecosystem to generate a consistent and substantial stream of revenue, directly funding its strategic weapons programs and circumventing international efforts to curb its proliferation activities.
North Korea has allegedly leveraged cybercrime, particularly cryptocurrency theft and ransomware, as a crucial and increasingly preferred method to fund its regime and, specifically, its illicit weapons programs.
This strategy is a direct response to the crippling international sanctions imposed on the country.
Here's how they've allegedly done it:
1. Circumventing Sanctions for Hard Currency:
Financial Isolation: North Korea faces severe international sanctions that cut off its access to traditional global financial systems. This makes it extremely difficult for the regime to acquire the foreign currency (like U.S. dollars or Euros) needed to import goods, technology, and components for its military and luxury items for its elite.
Cryptocurrency as an Alternative: Cryptocurrencies operate largely outside traditional banking regulations and centralized financial institutions. This makes them an attractive alternative for a sanctioned state. By stealing crypto, North Korea effectively generates hard currency that is harder to trace and block.
Funding WMD Programs: UN reports, U.S. government assessments, and cybersecurity firm analyses consistently state that the proceeds from these cybercrimes directly fund North Korea's prohibited weapons of mass destruction (WMD) programs, including nuclear weapons and ballistic missiles. Some estimates suggest cybercrime accounts for a significant portion, potentially 40% to 50% or more, of the regime's foreign currency income.
2. Cryptocurrency Theft: The Primary Goldmine
Massive Scale: North Korean hacking groups, notably the Lazarus Group and its sub-units like BlueNoroff, have stolen billions of dollars in cryptocurrency. For example, UN experts reported investigating 58 suspected North Korean cyberattacks between 2017 and 2023, valued at approximately $3 billion. The FBI recently attributed a single $1.5 billion hack against Bybit in February 2025 to North Korean actors.
Targeting Crypto Exchanges and DeFi Platforms:
Direct Hacks: They target centralized cryptocurrency exchanges, exploiting vulnerabilities in their security systems to steal large amounts of various cryptocurrencies.
Decentralized Finance (DeFi) Exploits: As the crypto landscape evolved, North Korean hackers shifted to more vulnerable DeFi platforms and "bridges" (which facilitate asset transfer between different blockchains). Notorious examples include the Harmony Horizon Bridge ($100 million+) and the Sky Mavis Ronin Bridge ($600 million+). DeFi platforms often have less stringent security and regulatory oversight, making them "softer targets."
Sophisticated Social Engineering: They employ elaborate social engineering tactics to gain initial access:
Fake Job Offers: Creating fake companies, LinkedIn profiles, and seemingly legitimate job opportunities to trick employees of crypto firms into downloading malicious software or revealing credentials.
Impersonation: Impersonating venture capitalists, recruiters, or other legitimate business contacts.
Deepfake Technology: Increasingly, they use AI-enabled deepfake technologies in video calls to disguise their appearance and build trust with targets.
Laundering Stolen Funds: After stealing the cryptocurrency, they employ sophisticated laundering techniques to convert it into fiat currency (like USD). This involves:
Mixing Services: Using "crypto mixers" like Tornado Cash (which was sanctioned by the U.S. Treasury for its role in laundering North Korean funds) to obscure the origin of the stolen assets.
Chain Hopping: Moving funds across multiple different blockchains to complicate tracing efforts.
Dispersing Funds: Spreading stolen assets across thousands of addresses to make tracking harder.
Conversion to Fiat: Eventually converting the "cleaned" crypto into traditional currencies through various brokers, often in countries with weaker anti-money laundering regulations.
3. Ransomware Attacks: Another Revenue Stream
Extortion and Disruption: Groups like Andariel, a Lazarus sub-group, have deployed ransomware (e.g., Maui ransomware) against a range of targets, including U.S. hospitals and healthcare providers.
Demanding Crypto Payments: Ransomware payments are typically demanded in cryptocurrency, providing another direct avenue for generating funds that are difficult to trace.
Double Extortion: Beyond just encrypting data, some groups engage in "double extortion," threatening to leak stolen sensitive data if the ransom isn't paid, increasing pressure on victims.
4. Illicit IT Worker Schemes:
While not strictly "cybercrime" in the hacking sense, this is a related and significant revenue stream that leverages North Korea's cyber talent.
Disguised Workers: North Korean IT workers, often highly skilled in programming and software development, fraudulently obtain remote freelance jobs globally, using false identities and documentation.
Funneling Wages: The wages earned from these legitimate-looking jobs are then funneled back to the North Korean regime, providing another source of foreign currency. Some reports indicate these workers also insert backdoors or malware into corporate systems they work on, potentially enabling future cybercrime or espionage.
In essence, North Korea has become an innovator in state-sponsored cybercrime out of necessity. Facing stringent sanctions, its regime has adapted by exploiting the nascent and less-regulated cryptocurrency ecosystem to generate a consistent and substantial stream of revenue, directly funding its strategic weapons programs and circumventing international efforts to curb its proliferation activities.
4 months ago
Should countries name and shame China for cyberattacks, or work diplomatically behind the scenes?
The decision of whether to "name and shame" China for cyberattacks or work diplomatically behind the scenes is a complex one, with both approaches having potential benefits and drawbacks.
Many countries, including the U.S., its Five Eyes allies (UK, Canada, Australia, New Zealand), and increasingly the EU and Japan, often employ a combination of both, adapting their strategy based on the severity of the attack, the geopolitical context, and their specific objectives.
Arguments for Naming and Shaming (Public Attribution):
Imposing Reputational Costs: China, like any major power, is sensitive to its international image. Publicly calling out its malicious cyber activities, especially when done in a coordinated manner by a coalition of states (as seen with the Microsoft Exchange hack attribution), can impose reputational damage and diplomatic costs.
Deterrence (Long-Term): While direct deterrence of nation-state cyberattacks is difficult, public attribution can contribute to a long-term deterrence strategy. It signals that:
The victim state has the capability to identify the attacker, challenging the notion of anonymity in cyberspace.
There will be consequences, even if not immediate kinetic retaliation.
Such behavior is unacceptable and violates international norms.
Norm-Setting: Public attribution, especially when accompanied by legal condemnations and statements about international law (even if not universally agreed upon), helps build and reinforce norms of responsible state behavior in cyberspace. It draws a line in the sand and clarifies what actions are considered unacceptable.
Rallying Allies and Partners: Coordinated public attribution strengthens alliances and fosters collective security. It encourages intelligence sharing and collaboration on cybersecurity defense among like-minded nations, presenting a united front.
Raising Awareness and Improving Defenses: Public disclosures of nation-state TTPs (Tactics, Techniques, and Procedures) force organizations and governments to update their defenses against specific threats. The Hafnium attribution, for example, spurred widespread patching and improved vigilance.
Domestic Accountability/Public Opinion: In democratic countries, public attribution can inform citizens about threats to national security and critical infrastructure, potentially generating public support for stronger cybersecurity measures or policy responses.
Arguments for Diplomatic, Behind-the-Scenes Engagement:
De-escalation: Public accusations can sometimes lead to an escalatory cycle. Diplomatic channels allow for discreet communication, negotiation, and de-escalation, especially in sensitive situations where a public spat could worsen tensions.
Preserving Channels for Cooperation: Despite competition, there are areas where cooperation with China is necessary (e.g., climate change, pandemic response, nuclear non-proliferation). Public "shaming" could jeopardize these essential diplomatic avenues.
Intelligence Protection: Revealing attribution publicly often requires disclosing intelligence sources and methods, which can compromise future intelligence gathering capabilities. Behind-the-scenes diplomacy allows intelligence to be leveraged without exposure.
Lack of Immediate Impact: China routinely denies all accusations of state-sponsored hacking. Critics argue that "naming and shaming" has little immediate impact on China's behavior, as it simply issues boilerplate denials and continues operations.
Risk of Misattribution/Retaliation: Despite advances, definitive attribution can be challenging. A mistaken public accusation could severely damage diplomatic relations and potentially trigger retaliatory actions against the falsely accused state.
Specific Objectives: Sometimes the goal is to recover stolen data, gain access to compromised systems, or secure specific commitments. These objectives might be better achieved through quiet negotiations than public confrontation.
Maintaining Strategic Ambiguity: Some states prefer to keep their red lines and response capabilities ambiguous in cyberspace, believing this ambiguity can enhance deterrence. Public attribution might reduce this ambiguity.
A Hybrid Approach is Often Preferred:
In practice, many countries (like the US, UK, EU, and now increasingly Taiwan, as seen with recent public statements about UNC3886) adopt a hybrid approach:
Public Attribution for Major Incidents: When attacks are widespread, highly impactful (like the Microsoft Exchange hack or critical infrastructure targeting), or involve significant intellectual property theft, public attribution (especially when multilateral) is used to impose costs and set norms.
Behind-the-Scenes for Ongoing Issues or Sensitive Intelligence: For continuous espionage, specific intelligence exchanges, or when sensitive sources might be compromised, quiet diplomatic engagement or private warnings are often preferred.
Layered Response: Public attribution can be followed by diplomatic démarches, sanctions, or other policy responses, combining different tools of statecraft.
Given Taiwan's unique geopolitical position and direct exposure to Chinese cyber threats, a carefully calibrated approach is crucial.
Publicly exposing certain attacks can rally international support and highlight Beijing's aggressive cyber posture, which aligns with Taiwan's strategy of garnering international sympathy and support.
However, it must also balance this with pragmatic considerations for maintaining stability across the Strait and managing potential escalations.
The recent public statements from Singapore regarding UNC3886, despite initial Chinese denials, indicate a growing willingness among affected nations to be more transparent about the origins of serious cyberattacks.
The decision of whether to "name and shame" China for cyberattacks or work diplomatically behind the scenes is a complex one, with both approaches having potential benefits and drawbacks.
Many countries, including the U.S., its Five Eyes allies (UK, Canada, Australia, New Zealand), and increasingly the EU and Japan, often employ a combination of both, adapting their strategy based on the severity of the attack, the geopolitical context, and their specific objectives.
Arguments for Naming and Shaming (Public Attribution):
Imposing Reputational Costs: China, like any major power, is sensitive to its international image. Publicly calling out its malicious cyber activities, especially when done in a coordinated manner by a coalition of states (as seen with the Microsoft Exchange hack attribution), can impose reputational damage and diplomatic costs.
Deterrence (Long-Term): While direct deterrence of nation-state cyberattacks is difficult, public attribution can contribute to a long-term deterrence strategy. It signals that:
The victim state has the capability to identify the attacker, challenging the notion of anonymity in cyberspace.
There will be consequences, even if not immediate kinetic retaliation.
Such behavior is unacceptable and violates international norms.
Norm-Setting: Public attribution, especially when accompanied by legal condemnations and statements about international law (even if not universally agreed upon), helps build and reinforce norms of responsible state behavior in cyberspace. It draws a line in the sand and clarifies what actions are considered unacceptable.
Rallying Allies and Partners: Coordinated public attribution strengthens alliances and fosters collective security. It encourages intelligence sharing and collaboration on cybersecurity defense among like-minded nations, presenting a united front.
Raising Awareness and Improving Defenses: Public disclosures of nation-state TTPs (Tactics, Techniques, and Procedures) force organizations and governments to update their defenses against specific threats. The Hafnium attribution, for example, spurred widespread patching and improved vigilance.
Domestic Accountability/Public Opinion: In democratic countries, public attribution can inform citizens about threats to national security and critical infrastructure, potentially generating public support for stronger cybersecurity measures or policy responses.
Arguments for Diplomatic, Behind-the-Scenes Engagement:
De-escalation: Public accusations can sometimes lead to an escalatory cycle. Diplomatic channels allow for discreet communication, negotiation, and de-escalation, especially in sensitive situations where a public spat could worsen tensions.
Preserving Channels for Cooperation: Despite competition, there are areas where cooperation with China is necessary (e.g., climate change, pandemic response, nuclear non-proliferation). Public "shaming" could jeopardize these essential diplomatic avenues.
Intelligence Protection: Revealing attribution publicly often requires disclosing intelligence sources and methods, which can compromise future intelligence gathering capabilities. Behind-the-scenes diplomacy allows intelligence to be leveraged without exposure.
Lack of Immediate Impact: China routinely denies all accusations of state-sponsored hacking. Critics argue that "naming and shaming" has little immediate impact on China's behavior, as it simply issues boilerplate denials and continues operations.
Risk of Misattribution/Retaliation: Despite advances, definitive attribution can be challenging. A mistaken public accusation could severely damage diplomatic relations and potentially trigger retaliatory actions against the falsely accused state.
Specific Objectives: Sometimes the goal is to recover stolen data, gain access to compromised systems, or secure specific commitments. These objectives might be better achieved through quiet negotiations than public confrontation.
Maintaining Strategic Ambiguity: Some states prefer to keep their red lines and response capabilities ambiguous in cyberspace, believing this ambiguity can enhance deterrence. Public attribution might reduce this ambiguity.
A Hybrid Approach is Often Preferred:
In practice, many countries (like the US, UK, EU, and now increasingly Taiwan, as seen with recent public statements about UNC3886) adopt a hybrid approach:
Public Attribution for Major Incidents: When attacks are widespread, highly impactful (like the Microsoft Exchange hack or critical infrastructure targeting), or involve significant intellectual property theft, public attribution (especially when multilateral) is used to impose costs and set norms.
Behind-the-Scenes for Ongoing Issues or Sensitive Intelligence: For continuous espionage, specific intelligence exchanges, or when sensitive sources might be compromised, quiet diplomatic engagement or private warnings are often preferred.
Layered Response: Public attribution can be followed by diplomatic démarches, sanctions, or other policy responses, combining different tools of statecraft.
Given Taiwan's unique geopolitical position and direct exposure to Chinese cyber threats, a carefully calibrated approach is crucial.
Publicly exposing certain attacks can rally international support and highlight Beijing's aggressive cyber posture, which aligns with Taiwan's strategy of garnering international sympathy and support.
However, it must also balance this with pragmatic considerations for maintaining stability across the Strait and managing potential escalations.
The recent public statements from Singapore regarding UNC3886, despite initial Chinese denials, indicate a growing willingness among affected nations to be more transparent about the origins of serious cyberattacks.
4 months ago
“Sky Is NOT The Limit”: Su-57, S-500, R-37M In Spotlight As IAF Thrilled By Super Success Of S-400 & BrahMos (Part1)
Speaking at the “Katre Memorial Lecture,” a function organised by the Air Force Association at Bengaluru, the Indian Air Force (IAF) Chief, AP Singh made a specific mention of the deterrent capability of the S-400 Air Defence system, and the accuracy of BrahMos supersonic cruise missiles that had a game changer role in “Op Sindoor”.
For long, IAF strategy, tactics, and inventories have been designed for offensive strikes against the Western neighbour with whom India has had three full-fledged wars and many shorter skirmishes.
Having a smaller economy and military, Pakistan was conscious and built an air force that is air defence oriented. In recent decades, India has also had to prepare to take on a potential threat from China.
Notwithstanding the known positions, the Indian strikes against both terror and military targets all across Pakistan proved very successful, and Pakistan’s defensive systems could not engage or thwart them.
Op Sindoor saw weapon platforms and armaments belonging to many countries at play. These included the USA, Russia, China, France, and Turkey, among others.
Most analysts have been comparing and analysing the performance of major weapons. This was also of interest to the manufacturing companies and their host countries.
Some of the writings were also part of the narrative building to introduce motivated biases with politico-commercial considerations. Both sides claimed to have shot down each other’s aircraft on the opening round, but since no aircraft crossed the border, or even came close to it, the wreckage, if at all, would have fallen in their own territories, and so proof may have been concealed.
But 3 months after the operation, more facts have come out.
The Air Chief talked of nearly five Pakistani fighter aircraft having been shot down in the air by an Indian S-400. Interestingly, the S-400 achieved its farthest kill ever by destroying a High Value Air asset (HVAA) at nearly 300 kilometres. In addition, at least three F-16s and one C-130 were destroyed during airfield strikes, Air Chief said.
Major Weapons at Play
The proof of the results of the strikes by French Scalp and BrahMos anti-surface cruise missiles, and indigenous SkyStriker loiter munitions (LM) was available from Battle Damage Assessment (BDA) satellite pictures. Israeli Harop, large Loiter Munitions, were also very effective.
The Chinese HQ-9 Surface-to-Air Missile (SAM) system, a poor copy of the Russian S-300, could not intercept any of the Indian strikes. Nor did Pakistan claim any aircraft had been shot down using these SAMs, as all claims were being assigned to the much-touted Chinese PL-15 Air-to-Air Missile (AAM).
Pakistan claimed shooting down a few Indian aircraft and attributed all kills to the Chinese PL-15. A few of them landed in India in complete form, perhaps having been fired at ranges outside the envelope or having had technical failures, and will allow India to evaluate the system and technology.
There were also doubts about the variant of PL-15 supplied to Pakistan. The upend variant with China has a claimed range of 180 kilometres. Pakistan was supposed to have the export variant, the PL-15E, with a range of 145 kilometres.
There was a unanimous opinion of all global experts on the good performance of two weapons, the S-400 SAM system and the BrahMos anti-surface missiles (ASM).
Both performed flawlessly. Both are of Russian origin, and both are universally feared (respected) for their range, speed of engagement, and precision. At least 15 Indo-Russian BrahMos missiles were fired. The number of S-400 system missiles fired is still not in the public domain.
Cross-Border Air Strikes
Just to recap, in the early hours of 7 May 2025, India launched air strikes on nine terrorist targets in Pakistan using 24 stand-off weapons. The missiles targeted only the camps and infrastructure of militant groups Jaish-e-Mohammed and Lashkar-e-Taiba, and no Pakistani military or civilian facilities were engaged.
The 23-minute duration initial Indian strikes were reportedly carried out by the Rafale aircraft using SCALP missiles, and Su-30 MKI firing BrahMos cruise missiles as well as the Indian Army’s Indo-Israeli SkyStriker loitering munitions.
Satellite and intelligence photographic proof of the success of strikes was presented to the Indian and Global media.
Pakistan responded with significant drone and missile strikes at Indian military and civilian targets under the operation codenamed Operation Bunyan-un-Marsoos.
This included targeting airfields from Kashmir to Gujarat. India negated these strikes with its integrated air defence and counter-drone systems.
The S-400 missile system was deployed, marking India’s first combat use of this missile system. India’s indigenous Akash AD system played a huge role.
Pakistani strikes caused insignificant damage and very few civilian casualties. Meanwhile, the IAF carried out SEAD/DEAD operations, neutralizing Pakistani air defence systems, including the Chinese HQ-9 in Lahore, starting on 9th May.
On 10 May, in response to Pakistani strikes against Indian military targets, the IAF made a major airstrike across the length and depth of the country, targeting a variety of military targets, including airfields, AD systems, weapons, and logistic storage sites.
The “Nur Khan” military airfield at Chaklala, which is just next to the Capital, Islamabad, and the Pakistan Army’s HQs at Rawalpindi were also hit.
Other airfields hit were Sargoda, Rafiqi, Rahim Yar Khan, and radars and storage dumps at Pasrur, Malir, Chunian, Sukkur, Pasrur, and the Sialkot aviation base. India also inflicted extensive damage on air bases at Skardu, Jacobabad, and Bholari in Pakistan.
During its retaliatory strikes on Indian military targets, Pakistan claimed that the BrahMos storage facilities at Beas and Nagrota were destroyed, and that two S-400 systems at Adampur and Bhuj were neutralised.
International media acknowledged that all such claims were false. Immediately after the ceasefire, Indian Prime Minister Modi visited Adampur and addressed the personnel with the S-400 launcher forming the background. A similar visit was made by Defence Minister Rajnath Singh to Bhuj.
Debt-ridden Pakistan, which was already seeking financial bailout from the IMF, was rattled by the audacity and accuracy of the air strikes, and its Director General of Military Operations (DGMO) called his Indian counterpart on the hotline, requesting a ceasefire.
A new normal had been set between the two nuclear-armed neighbours. Similar strikes could be triggered again in case of another Pakistan-backed terror attack.
There was significant cyber warfare. There was also a war of narratives fought across the globe, especially to highlight the success or failure of specific military hardware for commercial reasons.
Turkey had supplied a large quantity of drones to Pakistan. These were used, but caused little damage on the ground. While the two sides were effectively at war, neither side had fully mobilized its ground forces. A fragile ceasefire was achieved around midday on 10 May. India called it a pause in hostilities. But it has held ever since.
India said that 21 of its civilians and five military personnel had died in the conflict. The casualties and the majority of the injuries occurred due to cross-LoC firing.
Pakistan said that 51 of its people had died in the clashes, including 40 civilians and 11 military personnel.
India claimed nearly 130 terrorists had been killed. India got global backing against terror; however, not many were willing to take sides during the conflict.
Few systems got universal praise. These included the S-400 AD System, India’s indigenous Akash AD system, the DRDO 4D (Drone, Detect, Deter, Destroy) counter-drone system, and the BrahMos anti-surface missiles. The French Scalp missile proved extremely accurate and destructive.
Speaking at the “Katre Memorial Lecture,” a function organised by the Air Force Association at Bengaluru, the Indian Air Force (IAF) Chief, AP Singh made a specific mention of the deterrent capability of the S-400 Air Defence system, and the accuracy of BrahMos supersonic cruise missiles that had a game changer role in “Op Sindoor”.
For long, IAF strategy, tactics, and inventories have been designed for offensive strikes against the Western neighbour with whom India has had three full-fledged wars and many shorter skirmishes.
Having a smaller economy and military, Pakistan was conscious and built an air force that is air defence oriented. In recent decades, India has also had to prepare to take on a potential threat from China.
Notwithstanding the known positions, the Indian strikes against both terror and military targets all across Pakistan proved very successful, and Pakistan’s defensive systems could not engage or thwart them.
Op Sindoor saw weapon platforms and armaments belonging to many countries at play. These included the USA, Russia, China, France, and Turkey, among others.
Most analysts have been comparing and analysing the performance of major weapons. This was also of interest to the manufacturing companies and their host countries.
Some of the writings were also part of the narrative building to introduce motivated biases with politico-commercial considerations. Both sides claimed to have shot down each other’s aircraft on the opening round, but since no aircraft crossed the border, or even came close to it, the wreckage, if at all, would have fallen in their own territories, and so proof may have been concealed.
But 3 months after the operation, more facts have come out.
The Air Chief talked of nearly five Pakistani fighter aircraft having been shot down in the air by an Indian S-400. Interestingly, the S-400 achieved its farthest kill ever by destroying a High Value Air asset (HVAA) at nearly 300 kilometres. In addition, at least three F-16s and one C-130 were destroyed during airfield strikes, Air Chief said.
Major Weapons at Play
The proof of the results of the strikes by French Scalp and BrahMos anti-surface cruise missiles, and indigenous SkyStriker loiter munitions (LM) was available from Battle Damage Assessment (BDA) satellite pictures. Israeli Harop, large Loiter Munitions, were also very effective.
The Chinese HQ-9 Surface-to-Air Missile (SAM) system, a poor copy of the Russian S-300, could not intercept any of the Indian strikes. Nor did Pakistan claim any aircraft had been shot down using these SAMs, as all claims were being assigned to the much-touted Chinese PL-15 Air-to-Air Missile (AAM).
Pakistan claimed shooting down a few Indian aircraft and attributed all kills to the Chinese PL-15. A few of them landed in India in complete form, perhaps having been fired at ranges outside the envelope or having had technical failures, and will allow India to evaluate the system and technology.
There were also doubts about the variant of PL-15 supplied to Pakistan. The upend variant with China has a claimed range of 180 kilometres. Pakistan was supposed to have the export variant, the PL-15E, with a range of 145 kilometres.
There was a unanimous opinion of all global experts on the good performance of two weapons, the S-400 SAM system and the BrahMos anti-surface missiles (ASM).
Both performed flawlessly. Both are of Russian origin, and both are universally feared (respected) for their range, speed of engagement, and precision. At least 15 Indo-Russian BrahMos missiles were fired. The number of S-400 system missiles fired is still not in the public domain.
Cross-Border Air Strikes
Just to recap, in the early hours of 7 May 2025, India launched air strikes on nine terrorist targets in Pakistan using 24 stand-off weapons. The missiles targeted only the camps and infrastructure of militant groups Jaish-e-Mohammed and Lashkar-e-Taiba, and no Pakistani military or civilian facilities were engaged.
The 23-minute duration initial Indian strikes were reportedly carried out by the Rafale aircraft using SCALP missiles, and Su-30 MKI firing BrahMos cruise missiles as well as the Indian Army’s Indo-Israeli SkyStriker loitering munitions.
Satellite and intelligence photographic proof of the success of strikes was presented to the Indian and Global media.
Pakistan responded with significant drone and missile strikes at Indian military and civilian targets under the operation codenamed Operation Bunyan-un-Marsoos.
This included targeting airfields from Kashmir to Gujarat. India negated these strikes with its integrated air defence and counter-drone systems.
The S-400 missile system was deployed, marking India’s first combat use of this missile system. India’s indigenous Akash AD system played a huge role.
Pakistani strikes caused insignificant damage and very few civilian casualties. Meanwhile, the IAF carried out SEAD/DEAD operations, neutralizing Pakistani air defence systems, including the Chinese HQ-9 in Lahore, starting on 9th May.
On 10 May, in response to Pakistani strikes against Indian military targets, the IAF made a major airstrike across the length and depth of the country, targeting a variety of military targets, including airfields, AD systems, weapons, and logistic storage sites.
The “Nur Khan” military airfield at Chaklala, which is just next to the Capital, Islamabad, and the Pakistan Army’s HQs at Rawalpindi were also hit.
Other airfields hit were Sargoda, Rafiqi, Rahim Yar Khan, and radars and storage dumps at Pasrur, Malir, Chunian, Sukkur, Pasrur, and the Sialkot aviation base. India also inflicted extensive damage on air bases at Skardu, Jacobabad, and Bholari in Pakistan.
During its retaliatory strikes on Indian military targets, Pakistan claimed that the BrahMos storage facilities at Beas and Nagrota were destroyed, and that two S-400 systems at Adampur and Bhuj were neutralised.
International media acknowledged that all such claims were false. Immediately after the ceasefire, Indian Prime Minister Modi visited Adampur and addressed the personnel with the S-400 launcher forming the background. A similar visit was made by Defence Minister Rajnath Singh to Bhuj.
Debt-ridden Pakistan, which was already seeking financial bailout from the IMF, was rattled by the audacity and accuracy of the air strikes, and its Director General of Military Operations (DGMO) called his Indian counterpart on the hotline, requesting a ceasefire.
A new normal had been set between the two nuclear-armed neighbours. Similar strikes could be triggered again in case of another Pakistan-backed terror attack.
There was significant cyber warfare. There was also a war of narratives fought across the globe, especially to highlight the success or failure of specific military hardware for commercial reasons.
Turkey had supplied a large quantity of drones to Pakistan. These were used, but caused little damage on the ground. While the two sides were effectively at war, neither side had fully mobilized its ground forces. A fragile ceasefire was achieved around midday on 10 May. India called it a pause in hostilities. But it has held ever since.
India said that 21 of its civilians and five military personnel had died in the conflict. The casualties and the majority of the injuries occurred due to cross-LoC firing.
Pakistan said that 51 of its people had died in the clashes, including 40 civilians and 11 military personnel.
India claimed nearly 130 terrorists had been killed. India got global backing against terror; however, not many were willing to take sides during the conflict.
Few systems got universal praise. These included the S-400 AD System, India’s indigenous Akash AD system, the DRDO 4D (Drone, Detect, Deter, Destroy) counter-drone system, and the BrahMos anti-surface missiles. The French Scalp missile proved extremely accurate and destructive.
4 months ago
Russia’s S-500 Missiles Blinded? Ukraine Claims Eliminating S-500 AD System’s Yenisei Radar In Crimea.
Ukraine’s Prymary (Ghosts) special unit has claimed destroying a 98L6 Yenisei radar, deep inside Crimea. The system, part of Russia’s cutting-edge S-500 Prometey air defense network, is designed to track some of the most difficult aerial threats.
The Yenisei wasn’t the original target. During the operation, Ukraine’s intelligence (HUR) operators first believed they had located a component of the S-400 Triumf. Only after analysing combat footage did they realize the fact that they had eyes on one of Russia’s most valuable and elusive radar stations.
Destroying Yenisei is more than just a symbolic victory. It deprives Russia’s forces in Crimea of a crucial early warning tool. The radar not only serves the S 500 but can also be integrated with the S 400 Triumf, significantly boosting detection and interception capabilities across the peninsula.
By eliminating it, Ukraine has punched a hole in Russia’s air defense shield over Crimea, making it harder for Moscow to spot and respond to incoming threats in time.
A video released by HUR shows the strike in action, underscoring how Ukrainian forces have shifted toward precision operations designed to neutralize high-value assets that can not be easily replaced.
The S-500 Prometey: Russia’s Ambitious Shield
The S-500 Property is touted as Russia’s crown jewel in long-range air defense. After state trials in 2020-2021, it was officially accepted into service in April 2021, with Moscow presenting it as a next-generation system capable of countering virtually any modern aerial threat.
On paper, the Prometey’s mission set is ambitious. It is designed to intercept medium and intercontinental range ballistic missiles during their final flight phase, track and engage hypersonic weapons, destroy low orbit satellites, and shoot down enemy aircraft before they can approach Russian airspace.
Central to this defensive web is the 98L6 Yenisei radar, ‘Eyes’ of the S-500s. It is responsible for detecting and tracking high-speed, high-altitude targets, and without it, the system’s overall effectiveness drops dramatically.
According to Russian claims, the Yenisei’s core is a multielement active electronically scanned array (AESA) designed to resist heavy electronic jamming. It can in theory detect both aerodynamic and ballistic targets at ranges up to 600 km and altitudes reaching 100 km. The data it gathers is then fed to command posts, where other air defense assets such as missile batteries can act on it.
Visually, the Yenisei resembles the older 97L6E radar, sharing the same four axle MZKT chassis and a similar configuration, including a fully rotatable antenna unit mounted alongside an equipment container.
However, the two systems diverge in their antenna design. The 96L6E’s primary antenna is split into two sections of different sizes, while the Yenisei features a different array structure optimized for its expanded mission set.
One of Yenisei’s advantages is operational flexibility. It can scan in a full 360-degree mode for wide area surveillance, or focus on a narrow sector to improve its ability to spot ballistic threats. This makes it the standard radar for the S-500 systems and a critical component of Russia’s layered air defense network.
Yet, real-world performance tells a more complicated story. In 2024, when the S-500 was deployed to Crimea to protect the Kerch Bridge, it reportedly failed to intercept an incoming MGM-140 ATACMS ballistic missile.
That failure raised uncomfortable questions about whether Russia’s most advanced air defense system can live up to its sweeping promises when facing fast, unpredictable, and well-planned attacks.
A Broader Ukrainian Strategy
The Prymary unit’s Yenisei strike is part of a larger operational pattern. Ukrainian forces have adopted a methodical approach. Identify and strike the nerve centers of the Russians’ detection network, rather than just the launch systems. By doing so, they render missile batteries less effective or even blind.
Another HUR special unit, Artan, has been conducting similar missions using FPV drones. These strikes have hit Russian vehicles, ammunition depots, and communications hubs, all documented with stark, close-up footage that shows drones weaving between obstacles before detonating on target.
The Prymary unit’s recent Yenisei strike fits into this wider strategy of targeting critical radar and missile systems that threaten Ukraine’s skies.
In one recent compilation video, HUR showcased hits on several high-value assets in occupied Crimea, including Nebo SVU, Podlet 1K, and 96L6E radars, as well as a BK 16 landing craft. Russian air defense and fighter jets scrambled to stop the drones, but they dodged missiles with near cinematic agility “like Neo in the Matrix”, as Ukrainian operators quipped.
Russia’s Radar Network Under Strain
The Prymary unit’s Yenisei strike is part of a larger operational pattern. Ukrainian forces have adopted a methodical approach. Identify and strike the nerve centers of the Russian’s detection network, rather than just the launch systems. By doing so, they render missile batteries less effective or even blind.
The Yenisei’s destruction comes at a time when Russia’s radar network is already under strain.
According to ‘Euromaidanpress’, Russia may have lost up to half of its radar capabilities since the full-scale invasion began in 2022.
One of the most costly setbacks has been the loss of Beriev A-50U airborne early warning aircraft, essential for detecting threats at long range. Ukraine has destroyed or damaged at least four of these aircraft, with the most recent hit occurring during Operation Spider Web in June 2024.
At the start of the war, Russia had an estimated seven A-50U aircraft. By winter 2024, aviation analyst Tom Cooper assessed that only four remained, and by mid-2025, possibly just three.
One surviving aircraft has been spotted in Vorkuta, far in Russia’s Arctic permafrost zone, likely to keep it out of Ukrainian strike range.
Moscow has been developing a next-generation A-100 radar aircraft, but none of the three prototypes are believed to be operational.
Strategic Implications
Each radar destroyed, whether mounted on a mast in Crimea or in the nose of an A-50U circling high above Russia, weakens Moscow’s early warning net. Fewer radars mean more blind spots, and more blind spots mean greater vulnerability for high-value targets, such as the Kerch Bridge, key air bases, naval facilities, and command centers.
This depletion also forces a change in Russian operating patterns. The remaining radar assets have become too precious to risk in exposed positions.
That means fewer sorties for the A-50Us, fewer deployments of rare ground-based systems like the Yenisei near contested areas, and an overall shift toward holding these assets in reserve. While this may protect them from destruction, it also reduces their deterrent effect and limits Russia’s ability to respond to fast-moving threats.
For Ukraine, the strategy is clear. By systematically targeting the rearrest and most capable radars, Kyiv not only weakens Russia’s current defences but also imposes a long-term cost.
The Road Ahead
If current trends continue, Russia’s radar coverage over Crimea and other contested areas will continue to thin.
Ukraine’s forces have shown they can find and hit even heavily guarded assets, and each successful strike emboldens further operations. The destruction of the Yenisei shows that no part of Russia’s high-end air defense network is beyond reach.
In modern warfare, control of the skies often comes down to who can see and act first. By dismantling Russia’s ‘electronic eye’, Ukraine is betting that blinding its adversary will open the way for strikes that could reshape the battlefield in its favour.
The loss of the Yenisei radar is one more step in that process and perhaps one of the most consequential yet.
Ukraine’s Prymary (Ghosts) special unit has claimed destroying a 98L6 Yenisei radar, deep inside Crimea. The system, part of Russia’s cutting-edge S-500 Prometey air defense network, is designed to track some of the most difficult aerial threats.
The Yenisei wasn’t the original target. During the operation, Ukraine’s intelligence (HUR) operators first believed they had located a component of the S-400 Triumf. Only after analysing combat footage did they realize the fact that they had eyes on one of Russia’s most valuable and elusive radar stations.
Destroying Yenisei is more than just a symbolic victory. It deprives Russia’s forces in Crimea of a crucial early warning tool. The radar not only serves the S 500 but can also be integrated with the S 400 Triumf, significantly boosting detection and interception capabilities across the peninsula.
By eliminating it, Ukraine has punched a hole in Russia’s air defense shield over Crimea, making it harder for Moscow to spot and respond to incoming threats in time.
A video released by HUR shows the strike in action, underscoring how Ukrainian forces have shifted toward precision operations designed to neutralize high-value assets that can not be easily replaced.
The S-500 Prometey: Russia’s Ambitious Shield
The S-500 Property is touted as Russia’s crown jewel in long-range air defense. After state trials in 2020-2021, it was officially accepted into service in April 2021, with Moscow presenting it as a next-generation system capable of countering virtually any modern aerial threat.
On paper, the Prometey’s mission set is ambitious. It is designed to intercept medium and intercontinental range ballistic missiles during their final flight phase, track and engage hypersonic weapons, destroy low orbit satellites, and shoot down enemy aircraft before they can approach Russian airspace.
Central to this defensive web is the 98L6 Yenisei radar, ‘Eyes’ of the S-500s. It is responsible for detecting and tracking high-speed, high-altitude targets, and without it, the system’s overall effectiveness drops dramatically.
According to Russian claims, the Yenisei’s core is a multielement active electronically scanned array (AESA) designed to resist heavy electronic jamming. It can in theory detect both aerodynamic and ballistic targets at ranges up to 600 km and altitudes reaching 100 km. The data it gathers is then fed to command posts, where other air defense assets such as missile batteries can act on it.
Visually, the Yenisei resembles the older 97L6E radar, sharing the same four axle MZKT chassis and a similar configuration, including a fully rotatable antenna unit mounted alongside an equipment container.
However, the two systems diverge in their antenna design. The 96L6E’s primary antenna is split into two sections of different sizes, while the Yenisei features a different array structure optimized for its expanded mission set.
One of Yenisei’s advantages is operational flexibility. It can scan in a full 360-degree mode for wide area surveillance, or focus on a narrow sector to improve its ability to spot ballistic threats. This makes it the standard radar for the S-500 systems and a critical component of Russia’s layered air defense network.
Yet, real-world performance tells a more complicated story. In 2024, when the S-500 was deployed to Crimea to protect the Kerch Bridge, it reportedly failed to intercept an incoming MGM-140 ATACMS ballistic missile.
That failure raised uncomfortable questions about whether Russia’s most advanced air defense system can live up to its sweeping promises when facing fast, unpredictable, and well-planned attacks.
A Broader Ukrainian Strategy
The Prymary unit’s Yenisei strike is part of a larger operational pattern. Ukrainian forces have adopted a methodical approach. Identify and strike the nerve centers of the Russians’ detection network, rather than just the launch systems. By doing so, they render missile batteries less effective or even blind.
Another HUR special unit, Artan, has been conducting similar missions using FPV drones. These strikes have hit Russian vehicles, ammunition depots, and communications hubs, all documented with stark, close-up footage that shows drones weaving between obstacles before detonating on target.
The Prymary unit’s recent Yenisei strike fits into this wider strategy of targeting critical radar and missile systems that threaten Ukraine’s skies.
In one recent compilation video, HUR showcased hits on several high-value assets in occupied Crimea, including Nebo SVU, Podlet 1K, and 96L6E radars, as well as a BK 16 landing craft. Russian air defense and fighter jets scrambled to stop the drones, but they dodged missiles with near cinematic agility “like Neo in the Matrix”, as Ukrainian operators quipped.
Russia’s Radar Network Under Strain
The Prymary unit’s Yenisei strike is part of a larger operational pattern. Ukrainian forces have adopted a methodical approach. Identify and strike the nerve centers of the Russian’s detection network, rather than just the launch systems. By doing so, they render missile batteries less effective or even blind.
The Yenisei’s destruction comes at a time when Russia’s radar network is already under strain.
According to ‘Euromaidanpress’, Russia may have lost up to half of its radar capabilities since the full-scale invasion began in 2022.
One of the most costly setbacks has been the loss of Beriev A-50U airborne early warning aircraft, essential for detecting threats at long range. Ukraine has destroyed or damaged at least four of these aircraft, with the most recent hit occurring during Operation Spider Web in June 2024.
At the start of the war, Russia had an estimated seven A-50U aircraft. By winter 2024, aviation analyst Tom Cooper assessed that only four remained, and by mid-2025, possibly just three.
One surviving aircraft has been spotted in Vorkuta, far in Russia’s Arctic permafrost zone, likely to keep it out of Ukrainian strike range.
Moscow has been developing a next-generation A-100 radar aircraft, but none of the three prototypes are believed to be operational.
Strategic Implications
Each radar destroyed, whether mounted on a mast in Crimea or in the nose of an A-50U circling high above Russia, weakens Moscow’s early warning net. Fewer radars mean more blind spots, and more blind spots mean greater vulnerability for high-value targets, such as the Kerch Bridge, key air bases, naval facilities, and command centers.
This depletion also forces a change in Russian operating patterns. The remaining radar assets have become too precious to risk in exposed positions.
That means fewer sorties for the A-50Us, fewer deployments of rare ground-based systems like the Yenisei near contested areas, and an overall shift toward holding these assets in reserve. While this may protect them from destruction, it also reduces their deterrent effect and limits Russia’s ability to respond to fast-moving threats.
For Ukraine, the strategy is clear. By systematically targeting the rearrest and most capable radars, Kyiv not only weakens Russia’s current defences but also imposes a long-term cost.
The Road Ahead
If current trends continue, Russia’s radar coverage over Crimea and other contested areas will continue to thin.
Ukraine’s forces have shown they can find and hit even heavily guarded assets, and each successful strike emboldens further operations. The destruction of the Yenisei shows that no part of Russia’s high-end air defense network is beyond reach.
In modern warfare, control of the skies often comes down to who can see and act first. By dismantling Russia’s ‘electronic eye’, Ukraine is betting that blinding its adversary will open the way for strikes that could reshape the battlefield in its favour.
The loss of the Yenisei radar is one more step in that process and perhaps one of the most consequential yet.
4 months ago
Macron slams disaster waiting to happen in Gaza, wants UN mission.
French President Emmanuel Macron on Monday slammed Israel's plans to step up its military operation in Gaza as a disaster waiting to happen and proposed an international coalition under a United Nations mandate to stabilize Gaza.
Last week, Israel's security cabinet approved a plan to take control of Gaza City, in a move that expanded its military operations in the shattered Palestinian territory and drew strong criticism at home and abroad.
"The Israeli cabinet's announcement of an expansion of its operations in Gaza City and the Mawasi camps and for a re-occupation heralds a disaster of unprecedented gravity waiting to happen and of a drift towards a never-ending war," said Macron, in remarks sent by his office to reporters.
"The Israeli hostages and the people of Gaza will continue to be the primary victims of this strategy," added Macron.
Israeli Prime Minister Benjamin Netanyahu's office did not immediately return a request for comment. Responding to international criticism in a press conference on Sunday, he said Israel is "applying force judiciously".
By proposing a U.N.-mandated mission in Gaza, Macron is seeking to build on the momentum created by his recognition of a Palestinian state last month, which set off a domino of recognitions, with Britain and Canada following suit.
Macron said the U.N. mission would be tasked with securing the Gaza Strip, protecting civilians and working in support of unspecified Palestinian governance. He said the U.N. Security Council should work on establishing the mission.
"I have asked my teams to work on that with our partners without delay," he added.
+++++++++++++++++++++++++++++++++++++++++++
Macron: Israel’s ‘disastrous’ Gaza plan will lead to permanent war.
Emmanuel Macron has condemned Israel’s plans to expand its offensive in Gaza as a “disaster” and a move towards a “never-ending war”.
Israel’s security cabinet last week approved a plan to invade Gaza City, in effect moving towards the full occupation of the war-battered Strip, which drew severe criticism from home and abroad.
The French president said on Monday: “The Israeli cabinet’s announcement of an expansion of its operations in Gaza City and the Mawasi camps and for a re-occupation heralds a disaster of unprecedented gravity waiting to happen and of a move towards a never-ending war.”
“The Israeli hostages and the people of Gaza will continue to be the primary victims of this strategy,” added Mr. Macron, who last month pledged to recognize Palestinian statehood.
Mr. Macron said it was important to establish a UN-mandated stabilization mission to secure the Gaza Strip. “I have asked my teams to work on this without delay with our partners,” he added.
Benjamin Netanyahu, Israel’s prime minister, defended the plan on Sunday, despite calls from the military to change course, saying “Israel has no choice but to finish the job and complete the defeat of Hamas”.
However, Israeli officials have said it could take until October to evacuate civilians from Gaza City, allowing the possibility of a ceasefire to be achieved before the new offensive could start.
It comes as Israel killed Anas al-Sharif, a prominent Al Jazeera correspondent, and four of his colleagues in a targeted strike on Sunday, which has been condemned by journalists and rights groups.
Israel’s military accused the 28-year-old, one of the network’s most recognizable faces, of leading a Hamas terror cell and being involved in rocket attacks on Israel.
Al Jazeera rejected that accusation and said the attack was a “desperate attempt to silence voices in anticipation of the occupation of Gaza”.
Sir Keir Starmer said he was “gravely concerned” about the repeated targeting of journalists in Gaza, while the UN said it was a “grave breach of international humanitarian law”.
At least 69 people have been killed in Gaza over the past 24 hours, says the Hamas-run health ministry in the Strip.
That includes five people who died of malnutrition, the ministry said, bringing the overall claimed death toll to 61,499.
It comes as Norway’s sovereign wealth fund, the largest in the world, said on Monday that it was selling its investments in 11 Israeli companies.
Nicolai Tangen, chief of Norges Bank Investment Management, which manages the $1.8tn fund, cited the “serious humanitarian crisis” in Gaza and the worsening conditions in the West Bank as the reasons behind the decision.
French President Emmanuel Macron on Monday slammed Israel's plans to step up its military operation in Gaza as a disaster waiting to happen and proposed an international coalition under a United Nations mandate to stabilize Gaza.
Last week, Israel's security cabinet approved a plan to take control of Gaza City, in a move that expanded its military operations in the shattered Palestinian territory and drew strong criticism at home and abroad.
"The Israeli cabinet's announcement of an expansion of its operations in Gaza City and the Mawasi camps and for a re-occupation heralds a disaster of unprecedented gravity waiting to happen and of a drift towards a never-ending war," said Macron, in remarks sent by his office to reporters.
"The Israeli hostages and the people of Gaza will continue to be the primary victims of this strategy," added Macron.
Israeli Prime Minister Benjamin Netanyahu's office did not immediately return a request for comment. Responding to international criticism in a press conference on Sunday, he said Israel is "applying force judiciously".
By proposing a U.N.-mandated mission in Gaza, Macron is seeking to build on the momentum created by his recognition of a Palestinian state last month, which set off a domino of recognitions, with Britain and Canada following suit.
Macron said the U.N. mission would be tasked with securing the Gaza Strip, protecting civilians and working in support of unspecified Palestinian governance. He said the U.N. Security Council should work on establishing the mission.
"I have asked my teams to work on that with our partners without delay," he added.
+++++++++++++++++++++++++++++++++++++++++++
Macron: Israel’s ‘disastrous’ Gaza plan will lead to permanent war.
Emmanuel Macron has condemned Israel’s plans to expand its offensive in Gaza as a “disaster” and a move towards a “never-ending war”.
Israel’s security cabinet last week approved a plan to invade Gaza City, in effect moving towards the full occupation of the war-battered Strip, which drew severe criticism from home and abroad.
The French president said on Monday: “The Israeli cabinet’s announcement of an expansion of its operations in Gaza City and the Mawasi camps and for a re-occupation heralds a disaster of unprecedented gravity waiting to happen and of a move towards a never-ending war.”
“The Israeli hostages and the people of Gaza will continue to be the primary victims of this strategy,” added Mr. Macron, who last month pledged to recognize Palestinian statehood.
Mr. Macron said it was important to establish a UN-mandated stabilization mission to secure the Gaza Strip. “I have asked my teams to work on this without delay with our partners,” he added.
Benjamin Netanyahu, Israel’s prime minister, defended the plan on Sunday, despite calls from the military to change course, saying “Israel has no choice but to finish the job and complete the defeat of Hamas”.
However, Israeli officials have said it could take until October to evacuate civilians from Gaza City, allowing the possibility of a ceasefire to be achieved before the new offensive could start.
It comes as Israel killed Anas al-Sharif, a prominent Al Jazeera correspondent, and four of his colleagues in a targeted strike on Sunday, which has been condemned by journalists and rights groups.
Israel’s military accused the 28-year-old, one of the network’s most recognizable faces, of leading a Hamas terror cell and being involved in rocket attacks on Israel.
Al Jazeera rejected that accusation and said the attack was a “desperate attempt to silence voices in anticipation of the occupation of Gaza”.
Sir Keir Starmer said he was “gravely concerned” about the repeated targeting of journalists in Gaza, while the UN said it was a “grave breach of international humanitarian law”.
At least 69 people have been killed in Gaza over the past 24 hours, says the Hamas-run health ministry in the Strip.
That includes five people who died of malnutrition, the ministry said, bringing the overall claimed death toll to 61,499.
It comes as Norway’s sovereign wealth fund, the largest in the world, said on Monday that it was selling its investments in 11 Israeli companies.
Nicolai Tangen, chief of Norges Bank Investment Management, which manages the $1.8tn fund, cited the “serious humanitarian crisis” in Gaza and the worsening conditions in the West Bank as the reasons behind the decision.
4 months ago
Macron warns Israel that Gaza occupation plan risks ‘war without end’
French President Emmanuel Macron has sharply criticised Israel’s planned takeover of Gaza City, warning it would be a 'disaster' leading to endless war.
President Macron has denounced Israel’s plan to expand its operations and seize control of Gaza City, warning it was a "disaster" that risked locking the region into "permanent war".
This conflict "must end now with a lasting ceasefire," Macron urged in a statement this Monday, describing Israel’s proposed takeover of Gaza City as "a disaster of unprecedented gravity – a headlong rush into a war without end."
"The Israeli hostages and the people of Gaza will remain the main victims of such a strategy," he added.
Israeli plan for Gaza takeover must be halted immediately: UN rights chief
Israel announced its military would "take control" of Gaza City, a plan signed off by Prime Minister Benjamin Netanyahu’s security cabinet which has drawn sharp criticism from across the globe.
Macron called for the creation of a UN-mandated stabilisation mission to help secure the Gaza Strip.
"The Security Council must now act to establish such a mission and grant it the necessary mandate,” he said. “I have instructed my teams to begin work on this immediately with our partners."
Israel defends Gaza occupation plan
On Sunday, Netanyahu defended the plan, insisting: “Israel has no choice but to finish the job and ensure the complete defeat of Hamas. We already have about 70 to 75 percent of Gaza under military control – but two strongholds remain: Gaza City and the central camps in Al Mawasi.”
Palestinian witnesses reported the heaviest bombardments in weeks on Monday in the eastern suburbs of Gaza City, just hours after Netanyahu said he had ordered the Israeli Defence Forces to speed up their timetable for seizing the city.
Tanks and warplanes pounded areas including Sabra, Zeitoun and Shejaia, forcing families to flee westwards.
Germany's Merz defends stopping weapons deliveries to Israel
Although the Israeli military said it was targeting Hamas militants and dismantling launch sites, residents described one of the worst nights in weeks, raising fears that preparations were under way for a deeper push into the city, which now shelters around a million displaced people.
The latest military plans have intensified alarm abroad. Alongside Macron’s condemnation, Germany announced it would halt exports of military equipment that could be used in Gaza, while Britain and other European allies urged Israel to rethink its policy.
The United States’ ambassador to Israel criticised what he saw as some countries pressuring Israel rather than Hamas.
Famine unfolding
Meanwhile, the United Nations and humanitarian agencies have condemned the planned expansion.
"If these plans are implemented, they will likely trigger another calamity in Gaza," UN Assistant Secretary General Miroslav Jenca told the Security Council on Sunday.
UN agencies warned last month that famine was unfolding in the territory, with Israel severely restricting the entry of aid.
Defining famine: the complex process behind Gaza's hunger crisis
Israel's offensive has killed at least 61,430 Palestinians, according to Gaza's health ministry, figures the United Nations says are reliable.
Hamas's October, 2023 attack on Israel, which triggered the war, resulted in the deaths of 1,219 people, according to a tally kept by French news agency AFP, based on official figures.
French President Emmanuel Macron has sharply criticised Israel’s planned takeover of Gaza City, warning it would be a 'disaster' leading to endless war.
President Macron has denounced Israel’s plan to expand its operations and seize control of Gaza City, warning it was a "disaster" that risked locking the region into "permanent war".
This conflict "must end now with a lasting ceasefire," Macron urged in a statement this Monday, describing Israel’s proposed takeover of Gaza City as "a disaster of unprecedented gravity – a headlong rush into a war without end."
"The Israeli hostages and the people of Gaza will remain the main victims of such a strategy," he added.
Israeli plan for Gaza takeover must be halted immediately: UN rights chief
Israel announced its military would "take control" of Gaza City, a plan signed off by Prime Minister Benjamin Netanyahu’s security cabinet which has drawn sharp criticism from across the globe.
Macron called for the creation of a UN-mandated stabilisation mission to help secure the Gaza Strip.
"The Security Council must now act to establish such a mission and grant it the necessary mandate,” he said. “I have instructed my teams to begin work on this immediately with our partners."
Israel defends Gaza occupation plan
On Sunday, Netanyahu defended the plan, insisting: “Israel has no choice but to finish the job and ensure the complete defeat of Hamas. We already have about 70 to 75 percent of Gaza under military control – but two strongholds remain: Gaza City and the central camps in Al Mawasi.”
Palestinian witnesses reported the heaviest bombardments in weeks on Monday in the eastern suburbs of Gaza City, just hours after Netanyahu said he had ordered the Israeli Defence Forces to speed up their timetable for seizing the city.
Tanks and warplanes pounded areas including Sabra, Zeitoun and Shejaia, forcing families to flee westwards.
Germany's Merz defends stopping weapons deliveries to Israel
Although the Israeli military said it was targeting Hamas militants and dismantling launch sites, residents described one of the worst nights in weeks, raising fears that preparations were under way for a deeper push into the city, which now shelters around a million displaced people.
The latest military plans have intensified alarm abroad. Alongside Macron’s condemnation, Germany announced it would halt exports of military equipment that could be used in Gaza, while Britain and other European allies urged Israel to rethink its policy.
The United States’ ambassador to Israel criticised what he saw as some countries pressuring Israel rather than Hamas.
Famine unfolding
Meanwhile, the United Nations and humanitarian agencies have condemned the planned expansion.
"If these plans are implemented, they will likely trigger another calamity in Gaza," UN Assistant Secretary General Miroslav Jenca told the Security Council on Sunday.
UN agencies warned last month that famine was unfolding in the territory, with Israel severely restricting the entry of aid.
Defining famine: the complex process behind Gaza's hunger crisis
Israel's offensive has killed at least 61,430 Palestinians, according to Gaza's health ministry, figures the United Nations says are reliable.
Hamas's October, 2023 attack on Israel, which triggered the war, resulted in the deaths of 1,219 people, according to a tally kept by French news agency AFP, based on official figures.
4 months ago
From Joke to Jackpot — Turn Ideas into Powerful Meme Coins
The right meme coin can capture attention, grow a loyal community, and create real value. We combine secure blockchain technology, smart tokenomics, and eye-catching branding to bring your vision to life.
Every step is managed with precision so your coin is ready for the market and built for trust.
Our Services Include:
Custom meme coin development
Smart contract creation
Tokenomics strategy
Creative branding and visuals
Exchange listing support
Long-term technical assistance
Visit Us >>>> https://www.beleaftechnolo...
Let’s Talk >>>> WhatsApp: +91 7904323274
Telegram: BeleafSoftTech
Email: businessbeleaftechnologies.com
The right meme coin can capture attention, grow a loyal community, and create real value. We combine secure blockchain technology, smart tokenomics, and eye-catching branding to bring your vision to life.
Every step is managed with precision so your coin is ready for the market and built for trust.
Our Services Include:
Custom meme coin development
Smart contract creation
Tokenomics strategy
Creative branding and visuals
Exchange listing support
Long-term technical assistance
Visit Us >>>> https://www.beleaftechnolo...
Let’s Talk >>>> WhatsApp: +91 7904323274
Telegram: BeleafSoftTech
Email: businessbeleaftechnologies.com
6 months ago
Taiwan’s top envoy to the U.S. urged the Senate to ease tax burdens between the two countries and asked Congress to fast-track foreign military sales, following a closed-door lunch Wednesday with the House.
Ambassador Alexander Tah-Ray Yui, Taipei’s top representative in Washington, told Fox News Digital that he is encouraged that U.S. leaders recognize the urgent existential threat China poses, but emphasized the need to get weapons into the hands of the Taiwanese military more quickly and to address issues impeding two-way investment.
"We appreciate the United States prioritizing Taiwan and helping us strengthen our defense capabilities," Yui said. "We’re cheering on more military commitments to the states and [a] joint effort to speed up the delivery of the products that we bought."
Yui called on the Senate to advance a stalled double taxation agreement, which has already cleared the House.
"That’s an important incentive for Taiwanese companies to come to the United States and invest – but also vice versa for U.S. companies to go to Taiwan," he said. "We are the only one of the large trading partners without this treatment, which is worrying for the whole country right now."
By a vote of 423 to 1, the House last Congress passed the United States-Taiwan Expedited Double-Tax Relief Act, legislation that prevents double taxation on cross-border investments.
The ambassador also offered a sobering assessment of China’s increasingly belligerent posture in the Taiwan Strait and across the Indo-Pacific.
"We are concerned," Yui said. "The [People’s Liberation] Army and Navy are increasing their activities around Taiwan, harassing our territorial waters and airspace. These provocations are constant."
While emphasizing that "we don’t want war," he noted that the U.S. and regional partners have begun ramping up their own defenses, recognizing the threat.
Rep. August Pfluger, who chairs the influential RSC, told Fox News Digital that the meeting was a show of solidarity with Taiwan’s democratic government and a rebuke of China’s authoritarian policies.
"China is an existential threat to Taiwan," said Pfluger, a Texas Republican. "The difference between mainland China and Taiwan is how they treat human life. Taiwan values openness. China suppresses free speech, targets groups like the Uyghur Muslims – it’s deeply concerning."
The lunch meeting, attended by dozens of House Republicans, comes amid rising tensions in the region – but just as President Donald Trump announced a deal with Chinese President Xi Jinping to ease the trade war.
While Pfluger did not commit to further supplemental aid, he said he supports efforts by both nations to strengthen military readiness, including Taiwan’s move to increase defense spending to 3% of GDP.
"It stands to reason that Taiwan increasing their own internal spending on defense, as well as the U.S. recapitalizing our Navy and Air and Space Forces, is vitally important," he said.
Asked what message Congress wants to send to the Taiwanese people, Pfluger was unequivocal:
"We stand by them – as an ally, as a trading partner, as a democracy facing tyranny just next door."
The conversation came at a time when U.S. military officials are warning China is readying for battle in the Indo-Pacific in an effort to "dominate" the region.
"Beijing is preparing for war in the Indo-Pacific as part of its broader strategy to dominate that region and then the world," Defense Secretary Pete Hegseth told Congress this week. He added that such an outcome could put the U.S. economy and its supply chains in a choke hold.
"China is undertaking a historic military buildup and actively rehearsing for an invasion of Taiwan," he said.
"These aggressive maneuvers are not routine exercises, they are rehearsals for a forced unification," Gen. Dan Caine, chairman of the Joint Chiefs of Staff, added in his own testimony.
Taiwan has recently renewed an effort to purge its ranks of Chinese sympathizers, indicting four people on Tuesday suspected of spying for China that had infiltrated the presidential office.
Two Chinese aircraft carriers spotted conducting operations in the Pacific demonstrated the country’s "expansionist" aims, Taiwan Defense Minister Wellington Koo said Wednesday.
"Crossing from the first island chain into the second island chain sends a definite political message and their expansionist nature can be seen," he told reporters in Taipei.
The first island chain refers to the region from Japan to Taiwan and the Philippines to Borneo and the second island chain spreads farther into the Pacific, toward the U.S. territory of Guam.
Ambassador Alexander Tah-Ray Yui, Taipei’s top representative in Washington, told Fox News Digital that he is encouraged that U.S. leaders recognize the urgent existential threat China poses, but emphasized the need to get weapons into the hands of the Taiwanese military more quickly and to address issues impeding two-way investment.
"We appreciate the United States prioritizing Taiwan and helping us strengthen our defense capabilities," Yui said. "We’re cheering on more military commitments to the states and [a] joint effort to speed up the delivery of the products that we bought."
Yui called on the Senate to advance a stalled double taxation agreement, which has already cleared the House.
"That’s an important incentive for Taiwanese companies to come to the United States and invest – but also vice versa for U.S. companies to go to Taiwan," he said. "We are the only one of the large trading partners without this treatment, which is worrying for the whole country right now."
By a vote of 423 to 1, the House last Congress passed the United States-Taiwan Expedited Double-Tax Relief Act, legislation that prevents double taxation on cross-border investments.
The ambassador also offered a sobering assessment of China’s increasingly belligerent posture in the Taiwan Strait and across the Indo-Pacific.
"We are concerned," Yui said. "The [People’s Liberation] Army and Navy are increasing their activities around Taiwan, harassing our territorial waters and airspace. These provocations are constant."
While emphasizing that "we don’t want war," he noted that the U.S. and regional partners have begun ramping up their own defenses, recognizing the threat.
Rep. August Pfluger, who chairs the influential RSC, told Fox News Digital that the meeting was a show of solidarity with Taiwan’s democratic government and a rebuke of China’s authoritarian policies.
"China is an existential threat to Taiwan," said Pfluger, a Texas Republican. "The difference between mainland China and Taiwan is how they treat human life. Taiwan values openness. China suppresses free speech, targets groups like the Uyghur Muslims – it’s deeply concerning."
The lunch meeting, attended by dozens of House Republicans, comes amid rising tensions in the region – but just as President Donald Trump announced a deal with Chinese President Xi Jinping to ease the trade war.
While Pfluger did not commit to further supplemental aid, he said he supports efforts by both nations to strengthen military readiness, including Taiwan’s move to increase defense spending to 3% of GDP.
"It stands to reason that Taiwan increasing their own internal spending on defense, as well as the U.S. recapitalizing our Navy and Air and Space Forces, is vitally important," he said.
Asked what message Congress wants to send to the Taiwanese people, Pfluger was unequivocal:
"We stand by them – as an ally, as a trading partner, as a democracy facing tyranny just next door."
The conversation came at a time when U.S. military officials are warning China is readying for battle in the Indo-Pacific in an effort to "dominate" the region.
"Beijing is preparing for war in the Indo-Pacific as part of its broader strategy to dominate that region and then the world," Defense Secretary Pete Hegseth told Congress this week. He added that such an outcome could put the U.S. economy and its supply chains in a choke hold.
"China is undertaking a historic military buildup and actively rehearsing for an invasion of Taiwan," he said.
"These aggressive maneuvers are not routine exercises, they are rehearsals for a forced unification," Gen. Dan Caine, chairman of the Joint Chiefs of Staff, added in his own testimony.
Taiwan has recently renewed an effort to purge its ranks of Chinese sympathizers, indicting four people on Tuesday suspected of spying for China that had infiltrated the presidential office.
Two Chinese aircraft carriers spotted conducting operations in the Pacific demonstrated the country’s "expansionist" aims, Taiwan Defense Minister Wellington Koo said Wednesday.
"Crossing from the first island chain into the second island chain sends a definite political message and their expansionist nature can be seen," he told reporters in Taipei.
The first island chain refers to the region from Japan to Taiwan and the Philippines to Borneo and the second island chain spreads farther into the Pacific, toward the U.S. territory of Guam.
6 months ago
Opinion - Eurasia is the future — the US needs to get on board.
A major discovery of rare earth elements in central Kazakhstan earlier this year sent a jolt through global markets and policymaking circles, with early estimates suggesting it could place the country among the world’s top three holders of rare earth reserves. As the Trump administration scrambles to secure alternatives to China’s near-monopoly over these critical materials, used in modern technology such as smartphones, electric cars and computers, the spotlight is once again turning to a region long overlooked by Washington: the post-Soviet Turkic world.
These Turkic nations — Kazakhstan, Uzbekistan, Azerbaijan, Turkmenistan and Kyrgyzstan — are unfamiliar to most Americans. Yet U.S. officials have long recognized the region’s value, measured in energy, strategic minerals, rare earth elements and alternative supply routes.
For many thorny reasons, Washington has failed to establish firm allies there. Diplomatic presence tells the story: while Chinese leader Xi Jinping and Russian President Vladimir Putin have visited Central Asia 14 and 83 times, respectively, since taking office, no U.S. president has visited any Turkic nation besides Turkey.
And now the U.S. has fallen behind.
Russia, China and the European Union have all successfully made inroads in the Turkic world in recent years. Moscow, which has traditionally dominated the region, has largely taken control of Uzbekistan’s gas industry, while partnering with Kazakhstan on gas and oil exports and nuclear technology for a planned power plant. In 2023, China increased trade with Central Asia by 27 percent from the year prior while signing strategic partnerships with Uzbekistan, Kazakhstan and Azerbaijan. And the EU recently held a large summit with Central Asian countries in Uzbekistan, announcing it would invest $12 billion in the region.
These global powers understand the stakes. Kazakhstan, Turkmenistan, Uzbekistan and Azerbaijan together hold 6.5 percent of global gas reserves. Turkmenistan ranks sixth worldwide in gas, and Kazakhstan and Azerbaijan are major oil producers. And over the past several months, Astana has massively exceeded OPEC-plus production targets without signs of slowing.
But most important today is the region’s supply of minerals and rare earth elements. Besides Kazakhstan, Uzbekistan also has significant reserves and recently invested $2.6 billion to develop mineral extraction. Both Kazakhstan and Uzbekistan also have large reserves of strategic minerals with military, economic and technological uses, like gold, uranium, copper, tungsten, silicon, lithium and titanium.
Given Central Asia’s large reserves, Washington should invest in refining and mining rare earth elements, to break Beijing’s dominance. Refining is particularly important, as these countries lack the ability to refine important strategic minerals like lithium, uranium, nickel and cobalt and often do so in China or Russia. To pave the way for such investment, Congress should consider granting the Turkic world Permanent Normal Trade Relations status.
Besides having valuable resources, the region plays an important role in supply routes. During the height of the ancient Silk Road’s importance, the Turkic world glued the continent together, serving as a thoroughfare between China, India and Europe. Today, it may be resuming its historic role as a bridge between the East and West, as the Middle Corridor gains in popularity — a transit route from East Asia to Europe bypassing both Russia and Iran. U.S. officials have spoken of the importance of the Middle Corridor in the past, and last year, Washington and Europe signed a Memorandum of Understanding to further develop the route.
Such developments give the U.S. a clear opportunity. Should Washington start seriously developing the corridor, it would give Kazakhstani energy a bypass through Azerbaijan while weakening Russia’s hold on Kazakhstan. An important step would be brokering a final peace deal between Armenia and Azerbaijan, widening the corridor and giving an alternative to Georgia, which has become closer to Russia in recent years.
Many Turkic leaders, including former Kazakhstani President Nursultan Nazarbayev, former Kyrgyz President Almazbek Atambayev and former Azerbaijani President Heydar Aliyev, have spoken about decreasing their outward reliance by forming a Turkic bloc. The bloc would represent a total of roughly 175 million inhabitants, with a GDP of some $1.9 trillion — about 95 percent of the Russian GDP, and a growth rate 2 percent higher than the global average. Currently, Turkic countries have deepened cooperation through the Organization of Turkic States.
Should Turkic countries increase cooperation further, they will be better able to dictate their own terms. Although Turkey was once expected to lead a unified Turkic bloc, Recep Tayyip Erdoğan’s Islamist policies and Ankara’s focus on the Arab world have alienated key regional powers. The secular Turkic governments are wary of ideological influence, and of becoming subordinate to Ankara. This has led to a leadership vacuum — although possibly not for long.
After the conclusion of the 2020 Karabakh war with Armenia, Azerbaijan has begun to position itself along with Kazakhstan as a leader of the Turkic world. Both countries hold the largest reserves of energy and minerals and are most crucial to trade routes. Azerbaijan is located on the very bottleneck between Iran and Russia that crosses the Middle Corridor. Kazakhstan’s location makes it the most feasible country for Chinese products to cross over to Europe.
The U.S. must take the Turkic world seriously, and soon — not just in words, but with a presidential visit, sustained investment and a new Silk Road strategy.
A major discovery of rare earth elements in central Kazakhstan earlier this year sent a jolt through global markets and policymaking circles, with early estimates suggesting it could place the country among the world’s top three holders of rare earth reserves. As the Trump administration scrambles to secure alternatives to China’s near-monopoly over these critical materials, used in modern technology such as smartphones, electric cars and computers, the spotlight is once again turning to a region long overlooked by Washington: the post-Soviet Turkic world.
These Turkic nations — Kazakhstan, Uzbekistan, Azerbaijan, Turkmenistan and Kyrgyzstan — are unfamiliar to most Americans. Yet U.S. officials have long recognized the region’s value, measured in energy, strategic minerals, rare earth elements and alternative supply routes.
For many thorny reasons, Washington has failed to establish firm allies there. Diplomatic presence tells the story: while Chinese leader Xi Jinping and Russian President Vladimir Putin have visited Central Asia 14 and 83 times, respectively, since taking office, no U.S. president has visited any Turkic nation besides Turkey.
And now the U.S. has fallen behind.
Russia, China and the European Union have all successfully made inroads in the Turkic world in recent years. Moscow, which has traditionally dominated the region, has largely taken control of Uzbekistan’s gas industry, while partnering with Kazakhstan on gas and oil exports and nuclear technology for a planned power plant. In 2023, China increased trade with Central Asia by 27 percent from the year prior while signing strategic partnerships with Uzbekistan, Kazakhstan and Azerbaijan. And the EU recently held a large summit with Central Asian countries in Uzbekistan, announcing it would invest $12 billion in the region.
These global powers understand the stakes. Kazakhstan, Turkmenistan, Uzbekistan and Azerbaijan together hold 6.5 percent of global gas reserves. Turkmenistan ranks sixth worldwide in gas, and Kazakhstan and Azerbaijan are major oil producers. And over the past several months, Astana has massively exceeded OPEC-plus production targets without signs of slowing.
But most important today is the region’s supply of minerals and rare earth elements. Besides Kazakhstan, Uzbekistan also has significant reserves and recently invested $2.6 billion to develop mineral extraction. Both Kazakhstan and Uzbekistan also have large reserves of strategic minerals with military, economic and technological uses, like gold, uranium, copper, tungsten, silicon, lithium and titanium.
Given Central Asia’s large reserves, Washington should invest in refining and mining rare earth elements, to break Beijing’s dominance. Refining is particularly important, as these countries lack the ability to refine important strategic minerals like lithium, uranium, nickel and cobalt and often do so in China or Russia. To pave the way for such investment, Congress should consider granting the Turkic world Permanent Normal Trade Relations status.
Besides having valuable resources, the region plays an important role in supply routes. During the height of the ancient Silk Road’s importance, the Turkic world glued the continent together, serving as a thoroughfare between China, India and Europe. Today, it may be resuming its historic role as a bridge between the East and West, as the Middle Corridor gains in popularity — a transit route from East Asia to Europe bypassing both Russia and Iran. U.S. officials have spoken of the importance of the Middle Corridor in the past, and last year, Washington and Europe signed a Memorandum of Understanding to further develop the route.
Such developments give the U.S. a clear opportunity. Should Washington start seriously developing the corridor, it would give Kazakhstani energy a bypass through Azerbaijan while weakening Russia’s hold on Kazakhstan. An important step would be brokering a final peace deal between Armenia and Azerbaijan, widening the corridor and giving an alternative to Georgia, which has become closer to Russia in recent years.
Many Turkic leaders, including former Kazakhstani President Nursultan Nazarbayev, former Kyrgyz President Almazbek Atambayev and former Azerbaijani President Heydar Aliyev, have spoken about decreasing their outward reliance by forming a Turkic bloc. The bloc would represent a total of roughly 175 million inhabitants, with a GDP of some $1.9 trillion — about 95 percent of the Russian GDP, and a growth rate 2 percent higher than the global average. Currently, Turkic countries have deepened cooperation through the Organization of Turkic States.
Should Turkic countries increase cooperation further, they will be better able to dictate their own terms. Although Turkey was once expected to lead a unified Turkic bloc, Recep Tayyip Erdoğan’s Islamist policies and Ankara’s focus on the Arab world have alienated key regional powers. The secular Turkic governments are wary of ideological influence, and of becoming subordinate to Ankara. This has led to a leadership vacuum — although possibly not for long.
After the conclusion of the 2020 Karabakh war with Armenia, Azerbaijan has begun to position itself along with Kazakhstan as a leader of the Turkic world. Both countries hold the largest reserves of energy and minerals and are most crucial to trade routes. Azerbaijan is located on the very bottleneck between Iran and Russia that crosses the Middle Corridor. Kazakhstan’s location makes it the most feasible country for Chinese products to cross over to Europe.
The U.S. must take the Turkic world seriously, and soon — not just in words, but with a presidential visit, sustained investment and a new Silk Road strategy.
6 months ago
Opinion - Netanyahu’s West Bank miscalculation is uniting the Arab world on Palestine.
Israeli Prime Minister Benjamin Netanyahu has long thrived on regional fragmentation, most recently cutting normalization deals, known as the Abraham Accords, with Arab states while sidelining the Palestinian issue. But that strategy is collapsing.
In a historic miscalculation, Netanyahu’s refusal to allow Saudi Foreign Minister Prince Faisal bin Farhan and a delegation of Arab foreign ministers to visit the West Bank has provoked outrage and accelerated Arab unity behind the formal recognition of a Palestinian state.
To be clear, Hamas bears full responsibility for its brutal Oct. 7 terrorist attacks against Israel that ignited the Gaza War. Hamas’s continued rejection of U.S.-backed cease-fire proposals has prolonged the problem. At the same time, Netanyahu’s response — marked by the indiscriminate killing of civilians and disregard for international law — has further isolated Israel on the world stage.
Prince Faisal’s visit would have marked the first official Saudi stop in Palestinian territory since 1967. Coordinated by Saudi Arabia, Egypt, Jordan, Qatar, Turkey and the United Arab Emirates, the delegation aimed to meet Palestinian President Mahmoud Abbas in Ramallah and send a clear diplomatic message that the Palestinian cause is a central priority for the Arab and Muslim world. Instead, Netanyahu’s government denied the group entry, labeling the trip “provocative.”
The message received in the region was very different: Israeli leadership is so entrenched in its rejection of Palestinian statehood that it would rather slam doors on long-standing Arab allies such as Egypt and Jordan than allow symbolic gestures of solidarity. Palestinian officials called the move dangerous and unprecedented. Countries like the UAE — recently aligned with Netanyahu under the Abraham Accords — joined the delegation, underscoring a notable shift in Arab consensus.
This is not an isolated diplomatic fallout. It’s a turning point — and Saudi Arabia is leading the change. Crown Prince Mohammed bin Salman embodies the heart and pulse of the Middle East. His government, once rumored to be nearing normalization with Israel, has taken a firm stance: no recognition without Palestinian statehood.
Not only did the prince push the blocked West Bank visit, but Saudi Arabia is now co-chairing a high-level international conference with France in June to revive the two-state solution.
This French-Saudi coordination is not merely symbolic — it reflects the emergence of a serious diplomatic front pushing for global recognition of Palestine. French President Emmanuel Macron has called such recognition both a moral duty and a political necessity. The upcoming summit, supported by Arab League consensus and broader international momentum, could see a growing number of countries moving in that direction. Recent recognitions of Palestine by Norway, Spain and Ireland may be just the beginning.
The Arab world has come full circle. Where once there was hesitancy, fragmentation and quiet diplomacy, now there is relative cohesion and conviction. The Palestinian issue is back at the forefront — not because of an intifada or pressure from Western capitals, but because of regional realignment rooted in shared values and strategic recalibration. Netanyahu, who once claimed victory in separating Israel’s relations with Arab states from the Palestinian question, now faces a wall of Arab opposition.
Across Arab capitals, young people are increasingly vocal and engaged. They see the horrific images from Gaza in real time. Their identification with the Palestinian cause is not inherited but lived. Their message to governments is clear: Enough symbolism, take action.
Bin Salman has made clear that normalization with Israel is off the table without meaningful progress on Palestinian statehood. The Saudi calculus is realistic and strategic: Long-term regional stability depends on resolving the Palestinian question, not ignoring it.
This realignment is reshaping the global conversation, and Washington must take note. In this new era, Arab states are not waiting for U.S. mediation or Israeli approval — they are leading with their own initiatives, backed by global partners. Whether the Trump administration supports these moves or not, the facts on the ground are shifting.
Netanyahu’s defiance is isolating Israel at a time when it needs allies. Refusing entry to foreign ministers attempting peaceful diplomacy doesn’t project strength — it reveals fear. And in the process, it is galvanizing exactly what Netanyahu sought to avoid.
A few years ago, the regional narrative focused on normalization. Today, it’s about liberation. The next few months will be critical. If the French-Saudi summit catalyzes broader international recognition of Palestine, Netanyahu’s strategy will be seen not as visionary but as the catalyst for a historic reversal.
Arab leaders are no longer divided or deferring. They are vocal, aligned and following bin Salman’s lead. The road to lasting peace runs through a two-state solution, which begins with recognition of a Palestinian state.
Israelis and Palestinians deserve peace and security, not endless conflict. The world should help deliver this.
Israeli Prime Minister Benjamin Netanyahu has long thrived on regional fragmentation, most recently cutting normalization deals, known as the Abraham Accords, with Arab states while sidelining the Palestinian issue. But that strategy is collapsing.
In a historic miscalculation, Netanyahu’s refusal to allow Saudi Foreign Minister Prince Faisal bin Farhan and a delegation of Arab foreign ministers to visit the West Bank has provoked outrage and accelerated Arab unity behind the formal recognition of a Palestinian state.
To be clear, Hamas bears full responsibility for its brutal Oct. 7 terrorist attacks against Israel that ignited the Gaza War. Hamas’s continued rejection of U.S.-backed cease-fire proposals has prolonged the problem. At the same time, Netanyahu’s response — marked by the indiscriminate killing of civilians and disregard for international law — has further isolated Israel on the world stage.
Prince Faisal’s visit would have marked the first official Saudi stop in Palestinian territory since 1967. Coordinated by Saudi Arabia, Egypt, Jordan, Qatar, Turkey and the United Arab Emirates, the delegation aimed to meet Palestinian President Mahmoud Abbas in Ramallah and send a clear diplomatic message that the Palestinian cause is a central priority for the Arab and Muslim world. Instead, Netanyahu’s government denied the group entry, labeling the trip “provocative.”
The message received in the region was very different: Israeli leadership is so entrenched in its rejection of Palestinian statehood that it would rather slam doors on long-standing Arab allies such as Egypt and Jordan than allow symbolic gestures of solidarity. Palestinian officials called the move dangerous and unprecedented. Countries like the UAE — recently aligned with Netanyahu under the Abraham Accords — joined the delegation, underscoring a notable shift in Arab consensus.
This is not an isolated diplomatic fallout. It’s a turning point — and Saudi Arabia is leading the change. Crown Prince Mohammed bin Salman embodies the heart and pulse of the Middle East. His government, once rumored to be nearing normalization with Israel, has taken a firm stance: no recognition without Palestinian statehood.
Not only did the prince push the blocked West Bank visit, but Saudi Arabia is now co-chairing a high-level international conference with France in June to revive the two-state solution.
This French-Saudi coordination is not merely symbolic — it reflects the emergence of a serious diplomatic front pushing for global recognition of Palestine. French President Emmanuel Macron has called such recognition both a moral duty and a political necessity. The upcoming summit, supported by Arab League consensus and broader international momentum, could see a growing number of countries moving in that direction. Recent recognitions of Palestine by Norway, Spain and Ireland may be just the beginning.
The Arab world has come full circle. Where once there was hesitancy, fragmentation and quiet diplomacy, now there is relative cohesion and conviction. The Palestinian issue is back at the forefront — not because of an intifada or pressure from Western capitals, but because of regional realignment rooted in shared values and strategic recalibration. Netanyahu, who once claimed victory in separating Israel’s relations with Arab states from the Palestinian question, now faces a wall of Arab opposition.
Across Arab capitals, young people are increasingly vocal and engaged. They see the horrific images from Gaza in real time. Their identification with the Palestinian cause is not inherited but lived. Their message to governments is clear: Enough symbolism, take action.
Bin Salman has made clear that normalization with Israel is off the table without meaningful progress on Palestinian statehood. The Saudi calculus is realistic and strategic: Long-term regional stability depends on resolving the Palestinian question, not ignoring it.
This realignment is reshaping the global conversation, and Washington must take note. In this new era, Arab states are not waiting for U.S. mediation or Israeli approval — they are leading with their own initiatives, backed by global partners. Whether the Trump administration supports these moves or not, the facts on the ground are shifting.
Netanyahu’s defiance is isolating Israel at a time when it needs allies. Refusing entry to foreign ministers attempting peaceful diplomacy doesn’t project strength — it reveals fear. And in the process, it is galvanizing exactly what Netanyahu sought to avoid.
A few years ago, the regional narrative focused on normalization. Today, it’s about liberation. The next few months will be critical. If the French-Saudi summit catalyzes broader international recognition of Palestine, Netanyahu’s strategy will be seen not as visionary but as the catalyst for a historic reversal.
Arab leaders are no longer divided or deferring. They are vocal, aligned and following bin Salman’s lead. The road to lasting peace runs through a two-state solution, which begins with recognition of a Palestinian state.
Israelis and Palestinians deserve peace and security, not endless conflict. The world should help deliver this.
6 months ago
Opinion - Despite military purges, China’s next war ‘could be imminent’ and spread fast.
“There’s no reason to sugarcoat it,” Defense Secretary Pete Hegseth said on May 31 at the Shangri-La Dialogue, Asia’s premier security conference. “The threat China poses is real. And it could be imminent.”
Hegseth is right: America needs to urgently prepare for war.
War is coming to East Asia, and Taiwan — to which Hegseth was referring — is a target of Chinese aggression. Chinese President Xi Jinping, after all, has staked his personal legitimacy on annexing it as China’s 34th province.
Yet the U.S. and its partners have to be ready for anything at any place and at any time.
Why?
The Chinese regime, which is mobilizing all of society for war, is now unstable. It is not clear who, if anyone, is in charge. Therefore, the regime could take us by surprise.
One thing we know: Xi’s most senior loyalist in uniform has disappeared from public view. Gen. He Weidong, a vice chairman of the Communist Party’s Central Military Commission and the second highest-ranked uniformed officer, was last seen in public on March 11, at the end of the Communist Party’s major political event of the year, the so-called Two Sessions.
Many report that Xi sacked He. It’s true that Xi, since being named general secretary of the party in November 2012, has purged many military officers, ostensibly for “corruption,” and restructured the People’s Liberation Army. Both moves resulted in his taking firm control of the military.
Some have therefore assumed that Xi, for some reason, turned on his most important supporter in the military in March. However, it is not likely that Xi took down He.
On the contrary, it is much more probable that Xi’s adversaries removed that general.
While Xi loyalists were being removed from public view, PLA Daily, the Chinese military’s main propaganda organ, ran a series of articles praising “collective leadership,” a direct rejection of Xi’s continual calls for unity, centralization of control and complete obedience to his rule.
These articles, which began appearing last July, were written by people aligned with the top-ranked uniformed officer, Central Military Commission Vice Chairman Gen. Zhang Youxia. The propaganda pieces could not have appeared if Xi were in complete control of the military.
Moreover, He’s disappearance was followed by the disappearance of another Xi loyalist, Gen. He Hongjun. Rumors started that both generals had died by suicide in May at the military’s 301 Hospital in Beijing. Whether they are alive or not, they are out of the way, so their disappearance spells trouble for Xi.
“Gen. He Weidong was instrumental in Xi’s earlier purges in the military, so his disappearance could indicate a great threat to Xi’s authority,” Charles Burton of the Sinopsis think tank noted in comments to me this month.
The recent disappearances follow the sackings of, among others, Gen. Li Shangfu, a defense minister, Gen. Wei Fenghe, one of Li’s predecessors and perhaps as many as 70 in the Rocket Force, the branch responsible for the country’s nuclear weapons.
Given all the turmoil in the Chinese military, America and its partners need to focus on more than just Taiwan. In fact, the main island of Taiwan might be the least likely target.
To start hostilities by attacking Taiwan’s main island, China would need to launch a combined air-land-sea operation. To do that, Xi would have to give a general or admiral almost complete control over the military. The appointed flag officer would thereby become the most powerful figure in China.
Even in the calmest of times, Xi would be reluctant to create such a rival for power, but this is by no means a calm moment in Beijing. China’s leader seems to have lost substantial influence recently — so much so that there is speculation he could be pushed out of power in the coming months.
Whoever is controlling the purges — Xi or his political enemies — the Chinese military does not look ready to launch a complex operation such as a Taiwan invasion. Either Xi does not have the power to order an invasion because the military no longer answers to him, or Xi does not trust the most senior officers, a precondition for such a complex undertaking.
Despite all the turmoil in the leadership ranks, Hegseth was right to talk about an imminent war. The disruptive leadership moves in China have not prevented the Chinese military from engaging in low-level but especially provocative actions in the last couple of months against countries to China’s south and east.
We do not know whether China’s regime has made the decision to go to war, but its series of dangerous actions clearly reveals it has made the decision to risk war.
And war, if it begins somewhere, will likely spread. For one thing, the Chinese leadership will not be able to deal with incidents responsibly. In senior Communist Party circles these days, only the most hostile answers are considered acceptable.
Another factor is the existence of alliance and semi-alliance networks in the region. Four of China’s targets, South Korea, Japan, the Philippines, and Australia, are U.S. treaty allies, and one, Taiwan, is protected by the United States. China, for its part, could bring in its friends.
Moreover, the U.S. should be prepared for conflict with the world’s most destructive weapons.
“China has spent the last five decades investing in building nuclear proxy forces in Pakistan, North Korea and Iran to create nuclear crises to divert Washington’s attention away from the Taiwan Strait,” Richard Fisher of the International Assessment and Strategy Center told me this month. “China’s investment in Russia’s war in Ukraine is in the same vein.”
As Blaine Holt, a retired U.S. Air Force brigadier general, said after Hegseth’s comments, “Millions of lives now hang in the balance.”
Gordon G. Chang is the author of “Plan Red: China’s Project to Destroy America” and “The Coming Collapse of China.”
“There’s no reason to sugarcoat it,” Defense Secretary Pete Hegseth said on May 31 at the Shangri-La Dialogue, Asia’s premier security conference. “The threat China poses is real. And it could be imminent.”
Hegseth is right: America needs to urgently prepare for war.
War is coming to East Asia, and Taiwan — to which Hegseth was referring — is a target of Chinese aggression. Chinese President Xi Jinping, after all, has staked his personal legitimacy on annexing it as China’s 34th province.
Yet the U.S. and its partners have to be ready for anything at any place and at any time.
Why?
The Chinese regime, which is mobilizing all of society for war, is now unstable. It is not clear who, if anyone, is in charge. Therefore, the regime could take us by surprise.
One thing we know: Xi’s most senior loyalist in uniform has disappeared from public view. Gen. He Weidong, a vice chairman of the Communist Party’s Central Military Commission and the second highest-ranked uniformed officer, was last seen in public on March 11, at the end of the Communist Party’s major political event of the year, the so-called Two Sessions.
Many report that Xi sacked He. It’s true that Xi, since being named general secretary of the party in November 2012, has purged many military officers, ostensibly for “corruption,” and restructured the People’s Liberation Army. Both moves resulted in his taking firm control of the military.
Some have therefore assumed that Xi, for some reason, turned on his most important supporter in the military in March. However, it is not likely that Xi took down He.
On the contrary, it is much more probable that Xi’s adversaries removed that general.
While Xi loyalists were being removed from public view, PLA Daily, the Chinese military’s main propaganda organ, ran a series of articles praising “collective leadership,” a direct rejection of Xi’s continual calls for unity, centralization of control and complete obedience to his rule.
These articles, which began appearing last July, were written by people aligned with the top-ranked uniformed officer, Central Military Commission Vice Chairman Gen. Zhang Youxia. The propaganda pieces could not have appeared if Xi were in complete control of the military.
Moreover, He’s disappearance was followed by the disappearance of another Xi loyalist, Gen. He Hongjun. Rumors started that both generals had died by suicide in May at the military’s 301 Hospital in Beijing. Whether they are alive or not, they are out of the way, so their disappearance spells trouble for Xi.
“Gen. He Weidong was instrumental in Xi’s earlier purges in the military, so his disappearance could indicate a great threat to Xi’s authority,” Charles Burton of the Sinopsis think tank noted in comments to me this month.
The recent disappearances follow the sackings of, among others, Gen. Li Shangfu, a defense minister, Gen. Wei Fenghe, one of Li’s predecessors and perhaps as many as 70 in the Rocket Force, the branch responsible for the country’s nuclear weapons.
Given all the turmoil in the Chinese military, America and its partners need to focus on more than just Taiwan. In fact, the main island of Taiwan might be the least likely target.
To start hostilities by attacking Taiwan’s main island, China would need to launch a combined air-land-sea operation. To do that, Xi would have to give a general or admiral almost complete control over the military. The appointed flag officer would thereby become the most powerful figure in China.
Even in the calmest of times, Xi would be reluctant to create such a rival for power, but this is by no means a calm moment in Beijing. China’s leader seems to have lost substantial influence recently — so much so that there is speculation he could be pushed out of power in the coming months.
Whoever is controlling the purges — Xi or his political enemies — the Chinese military does not look ready to launch a complex operation such as a Taiwan invasion. Either Xi does not have the power to order an invasion because the military no longer answers to him, or Xi does not trust the most senior officers, a precondition for such a complex undertaking.
Despite all the turmoil in the leadership ranks, Hegseth was right to talk about an imminent war. The disruptive leadership moves in China have not prevented the Chinese military from engaging in low-level but especially provocative actions in the last couple of months against countries to China’s south and east.
We do not know whether China’s regime has made the decision to go to war, but its series of dangerous actions clearly reveals it has made the decision to risk war.
And war, if it begins somewhere, will likely spread. For one thing, the Chinese leadership will not be able to deal with incidents responsibly. In senior Communist Party circles these days, only the most hostile answers are considered acceptable.
Another factor is the existence of alliance and semi-alliance networks in the region. Four of China’s targets, South Korea, Japan, the Philippines, and Australia, are U.S. treaty allies, and one, Taiwan, is protected by the United States. China, for its part, could bring in its friends.
Moreover, the U.S. should be prepared for conflict with the world’s most destructive weapons.
“China has spent the last five decades investing in building nuclear proxy forces in Pakistan, North Korea and Iran to create nuclear crises to divert Washington’s attention away from the Taiwan Strait,” Richard Fisher of the International Assessment and Strategy Center told me this month. “China’s investment in Russia’s war in Ukraine is in the same vein.”
As Blaine Holt, a retired U.S. Air Force brigadier general, said after Hegseth’s comments, “Millions of lives now hang in the balance.”
Gordon G. Chang is the author of “Plan Red: China’s Project to Destroy America” and “The Coming Collapse of China.”
6 months ago
NATO's dilemma: how Zelenskiy can attend summit without provoking Trump.
Officials organising a NATO summit in The Hague this month are expected to keep it short, restrict discussion of Ukraine, and choreograph meetings so that Volodymyr Zelenskiy can somehow be in town without provoking Donald Trump.
Though the Ukrainian president is widely expected to attend the summit in some form, NATO has yet to confirm whether he is actually invited. Diplomats say he may attend a pre-summit dinner but be kept away from the main summit meeting.
Whether the brief summit statement will even identify Russia as a threat or express support for Ukraine is still up in the air.
The careful steps are all being taken to avoid angering Washington, much less provoking any repeat of February's White House blow-up between Trump and Zelenskiy that almost torpedoed the international coalition supporting Kyiv.
NATO's European members, who see Russia as an existential threat and NATO as the principal means of countering it, want to signal their continued strong support for Ukraine. But they are also desperate to avoid upsetting a volatile Trump, who stunned them at a summit seven years ago by threatening to quit the alliance altogether.
If Zelenskiy does not attend in some form, it would be "at least a PR disaster", acknowledged a senior NATO diplomat.
Since Russia's invasion three years ago, Zelenskiy has regularly attended NATO summits as the guest of honour, where alliance members pledged billions in weapons and condemned Russia for an illegal war of conquest. Leaders repeatedly promised that Ukraine would one day join NATO.
But since Washington's shift under Trump towards partly accepting Russia's justifications for the war and disparaging Zelenskiy, the 32-member alliance no longer speaks with a single voice about Europe's deadliest conflict since World War Two. Trump has taken Ukraine's NATO membership off the table, unilaterally granting Moscow one of its main demands.
After dressing down Zelenskiy in the Oval Office in February, Trump cut vital U.S. military and intelligence support for Ukraine for days.
Since then, the two men publicly mended fences in a meeting in St Peter's Basilica for the funeral of Pope Francis. But mostly they have spoken remotely, with Zelenskiy twice phoning the White House on speakerphone while surrounded by four friendly Europeans -- Britain's Keir Starmer, France's Emmanuel Macron, Germany's Friedrich Merz and Poland's Donald Tusk.
SPENDING BOOST-
Trump is expected to come away from The Hague with a big diplomatic victory as NATO members heed his longstanding complaints that they do not spend enough on defence and agree a much higher target.
They are expected to boost their goal for traditional military spending to 3.5% of economic output from 2%. A further pledge to spend 1.5% on related expenses such as infrastructure and cyber defence would raise the total to 5% demanded by Trump.
But the summit itself and its accompanying written statement are expected to be unusually short, minimising the chances of flare-ups or disagreements. A pledge to develop recommendations for a new Russia strategy has been kicked into the long grass.
Meanwhile, Zelenskiy may have to be content with an invitation to a pre-summit dinner, hosted by Dutch King Willem-Alexander, diplomats say.
Unlike at NATO’s previous two annual summits, the leaders do not plan to hold a formal meeting of the NATO-Ukraine Council, the official venue for talks between the alliance and Kyiv. The senior NATO diplomat said a working dinner with either foreign ministers or defence ministers could instead serve as an NUC.
'PROPERLY REPRESENTED'
On Wednesday, NATO boss Mark Rutte said he had invited Ukraine to the summit, but sidestepped a question on whether the invitation included Zelenskiy himself.
After meeting Rutte on Monday, Zelenskiy said on X that it was "important that Ukraine is properly represented" at the summit. "That would send the right signal to Russia," he said.
U.S. and Ukrainian officials did not reply to questions about the nature of any invitation to Ukraine.
Some European countries are still willing to say in public that they hope to see Zelenskiy invited as the head of the Ukrainian delegation.
Estonian Defence Minister Hanno Pevkur said he would like to see a "delegation led by President Zelenskiy". Asked about an invitation for Zelenskiy, German Defence Minister Boris Pistorius said "I, for my part, strongly welcome the invitation" without giving further details.
But diplomats have tried to play down the importance of the formal status of Zelenskiy's role: "Many allies want to have Zelenskiy at the summit, but there is flexibility on the precise format that would allow his presence," said a second senior NATO diplomat.
A senior European diplomat said: "We should not get stuck on ‘NUC or no NUC’. If he comes to the leaders’ dinner, that would be the minimum."
Officials organising a NATO summit in The Hague this month are expected to keep it short, restrict discussion of Ukraine, and choreograph meetings so that Volodymyr Zelenskiy can somehow be in town without provoking Donald Trump.
Though the Ukrainian president is widely expected to attend the summit in some form, NATO has yet to confirm whether he is actually invited. Diplomats say he may attend a pre-summit dinner but be kept away from the main summit meeting.
Whether the brief summit statement will even identify Russia as a threat or express support for Ukraine is still up in the air.
The careful steps are all being taken to avoid angering Washington, much less provoking any repeat of February's White House blow-up between Trump and Zelenskiy that almost torpedoed the international coalition supporting Kyiv.
NATO's European members, who see Russia as an existential threat and NATO as the principal means of countering it, want to signal their continued strong support for Ukraine. But they are also desperate to avoid upsetting a volatile Trump, who stunned them at a summit seven years ago by threatening to quit the alliance altogether.
If Zelenskiy does not attend in some form, it would be "at least a PR disaster", acknowledged a senior NATO diplomat.
Since Russia's invasion three years ago, Zelenskiy has regularly attended NATO summits as the guest of honour, where alliance members pledged billions in weapons and condemned Russia for an illegal war of conquest. Leaders repeatedly promised that Ukraine would one day join NATO.
But since Washington's shift under Trump towards partly accepting Russia's justifications for the war and disparaging Zelenskiy, the 32-member alliance no longer speaks with a single voice about Europe's deadliest conflict since World War Two. Trump has taken Ukraine's NATO membership off the table, unilaterally granting Moscow one of its main demands.
After dressing down Zelenskiy in the Oval Office in February, Trump cut vital U.S. military and intelligence support for Ukraine for days.
Since then, the two men publicly mended fences in a meeting in St Peter's Basilica for the funeral of Pope Francis. But mostly they have spoken remotely, with Zelenskiy twice phoning the White House on speakerphone while surrounded by four friendly Europeans -- Britain's Keir Starmer, France's Emmanuel Macron, Germany's Friedrich Merz and Poland's Donald Tusk.
SPENDING BOOST-
Trump is expected to come away from The Hague with a big diplomatic victory as NATO members heed his longstanding complaints that they do not spend enough on defence and agree a much higher target.
They are expected to boost their goal for traditional military spending to 3.5% of economic output from 2%. A further pledge to spend 1.5% on related expenses such as infrastructure and cyber defence would raise the total to 5% demanded by Trump.
But the summit itself and its accompanying written statement are expected to be unusually short, minimising the chances of flare-ups or disagreements. A pledge to develop recommendations for a new Russia strategy has been kicked into the long grass.
Meanwhile, Zelenskiy may have to be content with an invitation to a pre-summit dinner, hosted by Dutch King Willem-Alexander, diplomats say.
Unlike at NATO’s previous two annual summits, the leaders do not plan to hold a formal meeting of the NATO-Ukraine Council, the official venue for talks between the alliance and Kyiv. The senior NATO diplomat said a working dinner with either foreign ministers or defence ministers could instead serve as an NUC.
'PROPERLY REPRESENTED'
On Wednesday, NATO boss Mark Rutte said he had invited Ukraine to the summit, but sidestepped a question on whether the invitation included Zelenskiy himself.
After meeting Rutte on Monday, Zelenskiy said on X that it was "important that Ukraine is properly represented" at the summit. "That would send the right signal to Russia," he said.
U.S. and Ukrainian officials did not reply to questions about the nature of any invitation to Ukraine.
Some European countries are still willing to say in public that they hope to see Zelenskiy invited as the head of the Ukrainian delegation.
Estonian Defence Minister Hanno Pevkur said he would like to see a "delegation led by President Zelenskiy". Asked about an invitation for Zelenskiy, German Defence Minister Boris Pistorius said "I, for my part, strongly welcome the invitation" without giving further details.
But diplomats have tried to play down the importance of the formal status of Zelenskiy's role: "Many allies want to have Zelenskiy at the summit, but there is flexibility on the precise format that would allow his presence," said a second senior NATO diplomat.
A senior European diplomat said: "We should not get stuck on ‘NUC or no NUC’. If he comes to the leaders’ dinner, that would be the minimum."
6 months ago
The war mongers at work. Fight your war and don't call America. EU and NATO agreed not to extend to it's borders but Britain, France and Germany forced Russian border countries to join EU and NATO.
Russia is at war with Britain, the US is no longer a reliable ally and the UK has to respond by becoming more cohesive and more resilient, according to one of the three authors of the strategic defence review.
Fiona Hill, from County Durham, became the White House’s chief Russia adviser during Donald Trump’s first term and contributed to the British government’s strategy. She made the remarks in an interview with the Guardian.
“We’re in pretty big trouble,” Hill said, describing the UK’s geopolitical situation as caught between “the rock” of Vladimir Putin’s Russia and “the hard place” of Donald Trump’s increasingly unpredictable US.
Hill, 59, is perhaps the best known of the reviewers appointed by Labour, alongside Lord Robertson, a former Nato secretary general, and the retired general Sir Richard Barrons. She said she was happy to take on the role because it was “such a major pivot point in global affairs”. She remains a dual national after living in the US for more than 30 years.
“Russia has hardened as an adversary in ways that we probably hadn’t fully anticipated,” Hill said, arguing that Putin saw the Ukraine war as a starting point to Moscow becoming “a dominant military power in all of Europe”.
As part of that long-term effort, Russia was already “menacing the UK in various different ways,” she said, citing “the poisonings, assassinations, sabotage operations, all kinds of cyber-attacks and influence operations. The sensors that we see that they’re putting down around critical pipelines, efforts to butcher undersea cables.”
The conclusion, Hill said, was that “Russia is at war with us”. The foreign policy expert, a longtime Russia watcher, said she had first made a similar warning in 2015, in a revised version of a book she wrote about the Russian president with Clifford Gaddy, reflecting on the invasion and annexation of Crimea.
“We said Putin had declared war on the west,” she said. At the time, other experts disagreed, but Hill said events since had demonstrated “he obviously had, and we haven’t been paying attention to it”. The Russian leader, she argues, sees the fight in Ukraine as “part of a proxy war with the United States; that’s how he has persuaded China, North Korea and Iran to join in”.
Putin believed that Ukraine had already been decoupled from the US relationship, Hill said, because “Trump really wants to have a separate relationship with Putin to do arms control agreements and also business that will probably enrich their entourages further, though Putin doesn’t need any more enrichment”.
Russia is at war with Britain, the US is no longer a reliable ally and the UK has to respond by becoming more cohesive and more resilient, according to one of the three authors of the strategic defence review.
Fiona Hill, from County Durham, became the White House’s chief Russia adviser during Donald Trump’s first term and contributed to the British government’s strategy. She made the remarks in an interview with the Guardian.
“We’re in pretty big trouble,” Hill said, describing the UK’s geopolitical situation as caught between “the rock” of Vladimir Putin’s Russia and “the hard place” of Donald Trump’s increasingly unpredictable US.
Hill, 59, is perhaps the best known of the reviewers appointed by Labour, alongside Lord Robertson, a former Nato secretary general, and the retired general Sir Richard Barrons. She said she was happy to take on the role because it was “such a major pivot point in global affairs”. She remains a dual national after living in the US for more than 30 years.
“Russia has hardened as an adversary in ways that we probably hadn’t fully anticipated,” Hill said, arguing that Putin saw the Ukraine war as a starting point to Moscow becoming “a dominant military power in all of Europe”.
As part of that long-term effort, Russia was already “menacing the UK in various different ways,” she said, citing “the poisonings, assassinations, sabotage operations, all kinds of cyber-attacks and influence operations. The sensors that we see that they’re putting down around critical pipelines, efforts to butcher undersea cables.”
The conclusion, Hill said, was that “Russia is at war with us”. The foreign policy expert, a longtime Russia watcher, said she had first made a similar warning in 2015, in a revised version of a book she wrote about the Russian president with Clifford Gaddy, reflecting on the invasion and annexation of Crimea.
“We said Putin had declared war on the west,” she said. At the time, other experts disagreed, but Hill said events since had demonstrated “he obviously had, and we haven’t been paying attention to it”. The Russian leader, she argues, sees the fight in Ukraine as “part of a proxy war with the United States; that’s how he has persuaded China, North Korea and Iran to join in”.
Putin believed that Ukraine had already been decoupled from the US relationship, Hill said, because “Trump really wants to have a separate relationship with Putin to do arms control agreements and also business that will probably enrich their entourages further, though Putin doesn’t need any more enrichment”.
6 months ago
China has signalled for more than 15 years that it was looking to weaponise areas of the global supply chain, a strategy modelled on longstanding American export controls Beijing views as aimed at stalling its rise.
The scramble in recent weeks to secure export licences for rare earths, capped by Thursday's telephone call between U.S. and Chinese leaders Donald Trump and Xi Jinping, shows China has devised a better, more precisely targeted weapon for trade war.
Industry executives and analysts say while China is showing signs of approving more exports of the key elements, it will not dismantle its new system.
Modelled on the United States' own, Beijing's export licence system gives it unprecedented insight into supplier chokepoints in areas ranging from motors for electric vehicles to flight-control systems for guided missiles.
"China originally took inspiration for these export control methods from the comprehensive U.S. sanctions regime," said Zhu Junwei, a scholar at the Grandview Institution, a Beijing-based think tank focused on international relations.
"China has been trying to build its own export control systems since then, to be used as a last resort."
After Thursday's call, Trump said both leaders had been "straightening out some of the points, having to do mostly with rare earth magnets and some other things".
He did not say whether China committed to speeding up licences for exports of rare earth magnets, after Washington curbed exports of chip design software and jet engines to Beijing in response to its perceived slow-rolling on licences.
China holds a near-monopoly on rare earth magnets, a crucial component in EV motors.
In April it added some of the most sophisticated types to an export control list in its trade war with the United States, forcing all exporters to apply to Beijing for licences.
That put a once-obscure department of China's commerce ministry, with a staff of about 60, in charge of a chokepoint for global manufacturing.
The scramble in recent weeks to secure export licences for rare earths, capped by Thursday's telephone call between U.S. and Chinese leaders Donald Trump and Xi Jinping, shows China has devised a better, more precisely targeted weapon for trade war.
Industry executives and analysts say while China is showing signs of approving more exports of the key elements, it will not dismantle its new system.
Modelled on the United States' own, Beijing's export licence system gives it unprecedented insight into supplier chokepoints in areas ranging from motors for electric vehicles to flight-control systems for guided missiles.
"China originally took inspiration for these export control methods from the comprehensive U.S. sanctions regime," said Zhu Junwei, a scholar at the Grandview Institution, a Beijing-based think tank focused on international relations.
"China has been trying to build its own export control systems since then, to be used as a last resort."
After Thursday's call, Trump said both leaders had been "straightening out some of the points, having to do mostly with rare earth magnets and some other things".
He did not say whether China committed to speeding up licences for exports of rare earth magnets, after Washington curbed exports of chip design software and jet engines to Beijing in response to its perceived slow-rolling on licences.
China holds a near-monopoly on rare earth magnets, a crucial component in EV motors.
In April it added some of the most sophisticated types to an export control list in its trade war with the United States, forcing all exporters to apply to Beijing for licences.
That put a once-obscure department of China's commerce ministry, with a staff of about 60, in charge of a chokepoint for global manufacturing.
6 months ago
Less Than 10 Russian Bombers Destroyed In Ukraine’s “Shock Attack”; Kyiv Mostly Struck Defunct Aircraft: Russian Claims
Ukraine’s recent drone attack on four Russian Air Bases, where scores of bombers were destroyed, not only shocked Moscow but also led to a rewriting of the rules of modern warfare. But, how many bombers did Russia lose?
Firstly, the Ukrainian narrative!
Kyiv used inexpensive drones at the weekend to destroy Russian nuclear-capable bombers worth billions of dollars in an operation carried out after months of planning.
“Spider’s Web” dealt a blow to Russia more than three years after it invaded Ukraine, and the operation will now be studied closely by militaries around the world as a new strategy in asymmetric warfare.
Ukraine said it destroyed $7 billion worth of Russian aircraft parked at airbases thousands of kilometres across the border, mainly Tu-95 and Tu-22 long-range strategic bombers.
While the attacks at Belaya deep in Siberia and Olenya on the Kola Peninsula in the Arctic Circle are unlikely to change the course of the war, they will limit Moscow’s ability to launch long-range missile strikes against Ukraine.
Yohann Michel, a researcher at the French university Lyon-3, said the loss of the aircraft was “a serious blow to Russian offensive capabilities”.
“The main impact could be felt in several weeks’ time with a reduction in the number of sorties by the rest of the fleet” due to difficulties in finding spare parts for the Soviet-era planes, which are no longer in production, he told AFP.
Maxim Starchak, a fellow at the Centre for International and Defence Policy at Queen’s University in Canada, said it would take Russia a long time to replace the lost aircraft.
“Russia is extremely slow and inefficient in developing new aircraft for its nuclear forces,” he told AFP.
The drones, launched from trucks near air bases deep inside Russia, destroyed or damaged aircraft parked in the open.
Congratulating Ukraine’s Security Service chief, Vasyl Malyuk, President Volodymyr Zelensky said it had taken 18 months of preparation for the 117 drones to be concealed inside trucks near the airbases, and that all the Ukrainian agents had safely left Russia.
Michael Shurkin, a former CIA officer, said Ukraine’s operation was likely to have struck fear into militaries across the world, adding that potential targets for such drone attacks could include refineries, ballistic missile silos or military bases.
“This technology is akin to stealth technology: The threat is difficult to detect both because it emerges near the target and is too small and too low to be picked up by sensors designed to catch aircraft or missiles,” said Shurkin, director of global programs for the consultancy 14 North Strategies.
Ukrainian military analyst Oleksii Kopytko said anyone delivering a pizza or driving a horse-drawn cart could present a danger. “The organisers and main perpetrators are essentially untraceable,” he said.
A French arms manufacturing executive said Ukraine could have even trained AI algorithms to recognize aircraft or guide drones in case of jamming.
“New tools are forcing us to completely rethink defence systems and how they are produced,” said the executive, who asked not to be named.
“It opens up possibilities that we hadn’t even imagined.”
Zelensky “just proved that he and Ukraine are more than able to pull aces out of their combat fatigue sleeves,” said Timothy Ash, an emerging market economist focused on Russia.
The attacks exposed Russia’s air base vulnerabilities, providing a significant morale boost for Kyiv after months of being on the defensive in the conflict.
“The protection of military air bases does not meet security requirements,” said Starchak. “The dispersal of military aircraft across different airfields did not help either.”
Russia’s vast size is also a disadvantage in this regard.
“Usually, the vastness of Russia’s territory is an advantage; you can hide your bombers thousands of kilometres away where they would be safe,” said Michel.
“The problem is that this means you have to monitor thousands of square kilometres, which is simply impossible.”
The attacks dealt a blow to Moscow’s nuclear triad of ground, sea, and air-launched missiles, said Starchak.
If it were possible to target an airbase, it is also possible to hit bases hosting nuclear submarines, Starchak said.
“An attack on long-range aircraft bases is a potential threat to the entire nuclear triad, which can be easily hit, thereby weakening it to the point that it cannot respond with a nuclear strike.”
John Herbst, senior director of the Atlantic Council’s Eurasia Center, stated that Ukraine’s operation provided US President Donald Trump with leverage against Russian President Vladimir Putin in their quest for a settlement.
“It is a strong counter to the dubious ‘common wisdom’ that the war is moving inevitably in Moscow’s favour,” wrote the former US ambassador to Ukraine.
Counter Reports
Ex-IAF fighter pilot and Russia expert, Vijainder TK Thakur, believes that Ukraine might have mostly struck “Christmas Trees,” and not combat-ready Bombers.
He writes: What Zelensky touts as an 18-month masterstroke of planning is increasingly looking like a miscalculated, amateur effort.
Ukraine seems to have worked off a flawed assumption: that anything parked on a Russian tarmac was a functional military aircraft. In reality, of the ~200 Tu-95MS strategic bombers the Soviet Union built, Russia’s Aerospace Forces operate only around 60.
The rest—roughly 140—have long been relegated to open-air storage, stripped for spare parts. Ukrainian planners apparently believed these mothballed aircraft would be kept out of sight in hangars, while operational bombers would be conveniently left in the open.
The reality is precisely the opposite: Russia stores both retired and active aircraft out in the open. As a result, most of the Ukrainian drone strikes targeted what are effectively “Christmas Tree” decoys—hulks with no engines, no fluids, and no combat value.
Footage released by Ukraine itself shows hits on A-50s without engines and multiple strikes that triggered no fires, betraying the absence of combustible fluids. A real operational Tu-95MS would at least leak hydraulic or lubricating oil, even if empty of fuel.
Zelensky’s “strategic success” may have been little more than a fireworks show on a junkyard.
The following post by the FighterBomber Telegram Channel (closely linked with the Russian Air Force and the Kremlin), Google translated into English, explains what might have happened.
=== Translated Post ===
“The hohols posted a more detailed video of drone attacks on our five airfields, well, nothing new was added. As I said earlier, the number of destroyed planes is in the single digits. Not in the dozens.
By the will of fate, the overwhelming majority of planes attacked by the hohols were non-flying aircraft from the “iron row”. They could have attacked monuments on pedestals with the same success and effectiveness.
Fuel burns in planes; there is nothing else to burn. But when it burns, even the concrete nearby burns. The holes in the sides directly indicate that they are scrap metal, empty, and without fuel.
Of course, no one refuels faulty, written-off aircraft. They have the fattest layer of tires, because they are parked, the best for a photo report.
You will get tired of carrying tires on an aircraft that flies. Yes, in theory, of course, they can be restored and turned into a combat aircraft, but by that logic, monuments can also be restored. Attacked in Belarus at the beginning of the SVO by the same drone, our A-50, after a hellish explosion and a spectacular video, flew away to Russia under its power a couple of hours later and continued to carry out combat missions a little later.
Here, you only need to count those sides that are burning.” And, unfortunately, quite a few of them burned. And as I said on the stream, our long-range and strategic aviation did not receive critical losses as a result of this attack. But if such a blow is repeated…!
Ukraine’s recent drone attack on four Russian Air Bases, where scores of bombers were destroyed, not only shocked Moscow but also led to a rewriting of the rules of modern warfare. But, how many bombers did Russia lose?
Firstly, the Ukrainian narrative!
Kyiv used inexpensive drones at the weekend to destroy Russian nuclear-capable bombers worth billions of dollars in an operation carried out after months of planning.
“Spider’s Web” dealt a blow to Russia more than three years after it invaded Ukraine, and the operation will now be studied closely by militaries around the world as a new strategy in asymmetric warfare.
Ukraine said it destroyed $7 billion worth of Russian aircraft parked at airbases thousands of kilometres across the border, mainly Tu-95 and Tu-22 long-range strategic bombers.
While the attacks at Belaya deep in Siberia and Olenya on the Kola Peninsula in the Arctic Circle are unlikely to change the course of the war, they will limit Moscow’s ability to launch long-range missile strikes against Ukraine.
Yohann Michel, a researcher at the French university Lyon-3, said the loss of the aircraft was “a serious blow to Russian offensive capabilities”.
“The main impact could be felt in several weeks’ time with a reduction in the number of sorties by the rest of the fleet” due to difficulties in finding spare parts for the Soviet-era planes, which are no longer in production, he told AFP.
Maxim Starchak, a fellow at the Centre for International and Defence Policy at Queen’s University in Canada, said it would take Russia a long time to replace the lost aircraft.
“Russia is extremely slow and inefficient in developing new aircraft for its nuclear forces,” he told AFP.
The drones, launched from trucks near air bases deep inside Russia, destroyed or damaged aircraft parked in the open.
Congratulating Ukraine’s Security Service chief, Vasyl Malyuk, President Volodymyr Zelensky said it had taken 18 months of preparation for the 117 drones to be concealed inside trucks near the airbases, and that all the Ukrainian agents had safely left Russia.
Michael Shurkin, a former CIA officer, said Ukraine’s operation was likely to have struck fear into militaries across the world, adding that potential targets for such drone attacks could include refineries, ballistic missile silos or military bases.
“This technology is akin to stealth technology: The threat is difficult to detect both because it emerges near the target and is too small and too low to be picked up by sensors designed to catch aircraft or missiles,” said Shurkin, director of global programs for the consultancy 14 North Strategies.
Ukrainian military analyst Oleksii Kopytko said anyone delivering a pizza or driving a horse-drawn cart could present a danger. “The organisers and main perpetrators are essentially untraceable,” he said.
A French arms manufacturing executive said Ukraine could have even trained AI algorithms to recognize aircraft or guide drones in case of jamming.
“New tools are forcing us to completely rethink defence systems and how they are produced,” said the executive, who asked not to be named.
“It opens up possibilities that we hadn’t even imagined.”
Zelensky “just proved that he and Ukraine are more than able to pull aces out of their combat fatigue sleeves,” said Timothy Ash, an emerging market economist focused on Russia.
The attacks exposed Russia’s air base vulnerabilities, providing a significant morale boost for Kyiv after months of being on the defensive in the conflict.
“The protection of military air bases does not meet security requirements,” said Starchak. “The dispersal of military aircraft across different airfields did not help either.”
Russia’s vast size is also a disadvantage in this regard.
“Usually, the vastness of Russia’s territory is an advantage; you can hide your bombers thousands of kilometres away where they would be safe,” said Michel.
“The problem is that this means you have to monitor thousands of square kilometres, which is simply impossible.”
The attacks dealt a blow to Moscow’s nuclear triad of ground, sea, and air-launched missiles, said Starchak.
If it were possible to target an airbase, it is also possible to hit bases hosting nuclear submarines, Starchak said.
“An attack on long-range aircraft bases is a potential threat to the entire nuclear triad, which can be easily hit, thereby weakening it to the point that it cannot respond with a nuclear strike.”
John Herbst, senior director of the Atlantic Council’s Eurasia Center, stated that Ukraine’s operation provided US President Donald Trump with leverage against Russian President Vladimir Putin in their quest for a settlement.
“It is a strong counter to the dubious ‘common wisdom’ that the war is moving inevitably in Moscow’s favour,” wrote the former US ambassador to Ukraine.
Counter Reports
Ex-IAF fighter pilot and Russia expert, Vijainder TK Thakur, believes that Ukraine might have mostly struck “Christmas Trees,” and not combat-ready Bombers.
He writes: What Zelensky touts as an 18-month masterstroke of planning is increasingly looking like a miscalculated, amateur effort.
Ukraine seems to have worked off a flawed assumption: that anything parked on a Russian tarmac was a functional military aircraft. In reality, of the ~200 Tu-95MS strategic bombers the Soviet Union built, Russia’s Aerospace Forces operate only around 60.
The rest—roughly 140—have long been relegated to open-air storage, stripped for spare parts. Ukrainian planners apparently believed these mothballed aircraft would be kept out of sight in hangars, while operational bombers would be conveniently left in the open.
The reality is precisely the opposite: Russia stores both retired and active aircraft out in the open. As a result, most of the Ukrainian drone strikes targeted what are effectively “Christmas Tree” decoys—hulks with no engines, no fluids, and no combat value.
Footage released by Ukraine itself shows hits on A-50s without engines and multiple strikes that triggered no fires, betraying the absence of combustible fluids. A real operational Tu-95MS would at least leak hydraulic or lubricating oil, even if empty of fuel.
Zelensky’s “strategic success” may have been little more than a fireworks show on a junkyard.
The following post by the FighterBomber Telegram Channel (closely linked with the Russian Air Force and the Kremlin), Google translated into English, explains what might have happened.
=== Translated Post ===
“The hohols posted a more detailed video of drone attacks on our five airfields, well, nothing new was added. As I said earlier, the number of destroyed planes is in the single digits. Not in the dozens.
By the will of fate, the overwhelming majority of planes attacked by the hohols were non-flying aircraft from the “iron row”. They could have attacked monuments on pedestals with the same success and effectiveness.
Fuel burns in planes; there is nothing else to burn. But when it burns, even the concrete nearby burns. The holes in the sides directly indicate that they are scrap metal, empty, and without fuel.
Of course, no one refuels faulty, written-off aircraft. They have the fattest layer of tires, because they are parked, the best for a photo report.
You will get tired of carrying tires on an aircraft that flies. Yes, in theory, of course, they can be restored and turned into a combat aircraft, but by that logic, monuments can also be restored. Attacked in Belarus at the beginning of the SVO by the same drone, our A-50, after a hellish explosion and a spectacular video, flew away to Russia under its power a couple of hours later and continued to carry out combat missions a little later.
Here, you only need to count those sides that are burning.” And, unfortunately, quite a few of them burned. And as I said on the stream, our long-range and strategic aviation did not receive critical losses as a result of this attack. But if such a blow is repeated…!
6 months ago
U.S. Air Force “Shoots Down” U.S. Navy Aircraft Yet Again As Pentagon Prioritizes F-47 Over F/A-XX Program
The US Navy’s next-generation F/A-XX program could face potential delays as the Pentagon has stated that it wants to prioritize the funding of the US Air Force (USAF) F-47 fighter program instead.
The Pentagon wants to prioritize the Air Force’s F-47 stealth fighter over the US Navy’s ambitions to construct its own next-generation jet, arguing that pursuing the two programs simultaneously could cause delays for both, Bloomberg reported.
“Simultaneously pursuing two sixth-generation fighters risks under-delivery on both,” the Department of Defense reportedly said last month to a House and Senate defense policy committee in a request.
The Defense Department requested that the committee divert $500 million from the “accelerated development” of a Navy stealth fighter to the F-47, a contract for which was awarded by President Donald Trump to Boeing in March 2025.
The Pentagon argued that the F-47, “which has full presidential support,” should receive the additional $500 million instead of the US Navy.
“Given the schedule delays and cost growth across numerous airframes, DoD recommends a focus on the F-47, giving the Navy’s F/A-XX program time for technical maturity and development,” the Defense Department stated. “Phasing the F/A-XX after the Air Force’s initial F-47 development will alleviate capacity concerns in the industrial base.”
The latest report comes days after Reuters reported that Congress and the Trump administration were locking horns, causing delays in awarding the contract for the F/A-XX program.
The Navy was earlier poised to award the contract in March, the same month when Boeing received the official green light to build the F-47.
The Trump administration has stated that the F-47 will become operational before the end of Donald Trump’s term in 2029. This may be the reason behind an enhanced push for expansion in funding for the F-47.
Nonetheless, the House Armed Services Committee remains unconvinced by the Pentagon’s argument. Denying the request made by the Pentagon under Defense Secretary Pete Hegseth, the committee added the $500 million for the Navy’s F/A-XX in the $3.9 trillion package that was sent to the Senate.
The Senate Armed Services Committee on June 3 unveiled its defense section of the tax, or reconciliation, bill. It includes $750 million to “accelerate the FA/XX aircraft.” The Pentagon request was turned down, although Republicans currently lead the Senate and the House.
Heather Vaughan, a committee spokesperson, said the committee is not on board with the Pentagon’s decision to reroute the funds to the F-47 because the department has not fully explained why that was needed.
The spokesperson noted that the Pentagon “has yet to brief the committee on any changes for its plans to develop and procure the new Navy fighter.
“Absent any new information from the Navy concerning revision to defined capability gaps and shortfalls, mission requirements, cost, or acquisition strategy for F/A-XX, the committee continues to support the development of this critical platform,” she said.
The US Navy requires the F/A-XX to replace the aging F/A-18E/F Super Hornet and EA-18G Growler. After Lockheed Martin withdrew from the program in March, two contractors—Boeing and Northrop Grumman—are competing to build the Navy’s next-generation fighter.
Historically, the US Navy’s fighter jet program has trailed the USAF’s fighter program. For instance, the Navy’s F/A-18E/F Super Hornet faced delays in the 1990s due to budget constraints and debates over its effectiveness, with several members of Congress advising the upgrade of the Hornets instead.
A comparable multirole fighter of the USAF–the F-15E Strike Eagle–entered service in 1989. Meanwhile, the Super Hornet’s first flight was in 1995, and operational capability was achieved in 2001.
These delays were partly caused by the Navy’s desire to strike a balance between carrier-specific requirements and financial constraints.
Later, the F-35 program, managed by the Joint Program Office, prioritized the F-35A and F-35B due to their earlier operational needs and less complex technical requirements compared to the F-35C. In fact, the F-35C carrier variant was the last to achieve Initial Operational Capability (IOC) in 2019, following the F-35A (2016) and the F-35B (2015).
Since the F-35 was already so expensive, the variants might have had to compete for resources. The Marine Corps, which urgently needed to replace its old AV-8B Harriers, and the USAF, which had a larger aircraft inventory and a wider mission scope, were able to induct the aircraft sooner than the Navy. In general, Navy carrier-variant aircraft have some extensive technical modifications tailored to carrier operations.
The Navy’s F-35C, while critical for carrier air wings, relied on F/A-18E/F Super Hornets as a stopgap for a significant amount of time. However, this has since turned around, and the F-35C is now being prioritised for purchase, even by the US Marine Corps.
Having said that, US lawmakers and experts have repeatedly warned against delays in the next-generation fighter jet program, particularly as the threat of conflict with China in the Indo-Pacific remains a constant concern.
F/A-XX Needed In A China Conflict
Last month, Rep. Ken Calvert, R-Calif, the head of the House Appropriations subcommittee on defense, said that “any hesitancy” to move forward with the Navy’s proposed F/A-XX program will leave the service “outmatched” in a future conflict with China, as reported by Breaking Defense at the time.
Speaking at a posture hearing, he said, “We need sixth-generation fighters. The US Navy needs sixth-generation fighters. I’m concerned that any hesitancy on our part to proceed with the planned procurement of the sixth-gen fighters for the Navy will leave us dangerously outmatched in a China fight.”
“We cannot wait,” the appropriator added. “Further, we cannot expect to grow the defense industrial base by undermining it. Aviation programs that rely on highly specialized supply chains and skilled labor cannot be turned on and off like a switch.”
A previous Reuters report stated that postponing contract award by three years “would effectively cancel the program as it is currently defined,” as prices and contracts would expire during that time, almost guaranteeing a new competition.
Though little is known about the fighter jet’s capabilities, it is expected that the aircraft would be able to operate from a carrier deck and have advanced capabilities, including increased range, stealth, and AI integration.
The F/A-XX will be developed with the premise that it will need to travel vast distances in the Indo-Pacific and withstand the rising threat from China’s air defenses. The sixth-generation fighter will be fighting in contested territory.
The US Navy’s Rear Adm. Michael Donnelly had earlier said the design will have a 25% longer range than existing tactical aircraft systems, such as the F/A-18E/F and F-35C. The sixth-generation fighter will be specifically designed to work closely with unmanned aircraft using a control method known as “man-on-the-loop.”
Acting Chief of Naval Operations Adm. James Kilby said on the first day of the Navy-centric Sea Air Space exhibition outside of Washington, DC, that the US Navy requires the F/A-XX just like the USAF. “I mean, we’re talking about a fight in the Pacific. We fight together as a joint force, so having that capability is very important for us,” he added.
Later, speaking at a posture hearing, Kilby said, “The carrier is the most survivable airfield we have, period, and stop. The sixth-gen fighter is the keystone of our air wing of the future.” The aircraft carrier “brings mass volume fires over and over and over again, where a submarine will have to be reloaded and a destroyer will have to be reloaded … and take it offline. That carrier has got sustainment power, and the thing that delivers it is a fifth-gen and sixth-generation fighter into the future.”
While internal discussions rage over the future of the F/A-XX program, which is largely being developed to battle in the Pacific, China has already begun flight testing its two next-generation fighter-like aircraft. One is widely, albeit unofficially, referred to as the J-36, and the other is known as the J-XDS, or J-50.
The US Navy’s next-generation F/A-XX program could face potential delays as the Pentagon has stated that it wants to prioritize the funding of the US Air Force (USAF) F-47 fighter program instead.
The Pentagon wants to prioritize the Air Force’s F-47 stealth fighter over the US Navy’s ambitions to construct its own next-generation jet, arguing that pursuing the two programs simultaneously could cause delays for both, Bloomberg reported.
“Simultaneously pursuing two sixth-generation fighters risks under-delivery on both,” the Department of Defense reportedly said last month to a House and Senate defense policy committee in a request.
The Defense Department requested that the committee divert $500 million from the “accelerated development” of a Navy stealth fighter to the F-47, a contract for which was awarded by President Donald Trump to Boeing in March 2025.
The Pentagon argued that the F-47, “which has full presidential support,” should receive the additional $500 million instead of the US Navy.
“Given the schedule delays and cost growth across numerous airframes, DoD recommends a focus on the F-47, giving the Navy’s F/A-XX program time for technical maturity and development,” the Defense Department stated. “Phasing the F/A-XX after the Air Force’s initial F-47 development will alleviate capacity concerns in the industrial base.”
The latest report comes days after Reuters reported that Congress and the Trump administration were locking horns, causing delays in awarding the contract for the F/A-XX program.
The Navy was earlier poised to award the contract in March, the same month when Boeing received the official green light to build the F-47.
The Trump administration has stated that the F-47 will become operational before the end of Donald Trump’s term in 2029. This may be the reason behind an enhanced push for expansion in funding for the F-47.
Nonetheless, the House Armed Services Committee remains unconvinced by the Pentagon’s argument. Denying the request made by the Pentagon under Defense Secretary Pete Hegseth, the committee added the $500 million for the Navy’s F/A-XX in the $3.9 trillion package that was sent to the Senate.
The Senate Armed Services Committee on June 3 unveiled its defense section of the tax, or reconciliation, bill. It includes $750 million to “accelerate the FA/XX aircraft.” The Pentagon request was turned down, although Republicans currently lead the Senate and the House.
Heather Vaughan, a committee spokesperson, said the committee is not on board with the Pentagon’s decision to reroute the funds to the F-47 because the department has not fully explained why that was needed.
The spokesperson noted that the Pentagon “has yet to brief the committee on any changes for its plans to develop and procure the new Navy fighter.
“Absent any new information from the Navy concerning revision to defined capability gaps and shortfalls, mission requirements, cost, or acquisition strategy for F/A-XX, the committee continues to support the development of this critical platform,” she said.
The US Navy requires the F/A-XX to replace the aging F/A-18E/F Super Hornet and EA-18G Growler. After Lockheed Martin withdrew from the program in March, two contractors—Boeing and Northrop Grumman—are competing to build the Navy’s next-generation fighter.
Historically, the US Navy’s fighter jet program has trailed the USAF’s fighter program. For instance, the Navy’s F/A-18E/F Super Hornet faced delays in the 1990s due to budget constraints and debates over its effectiveness, with several members of Congress advising the upgrade of the Hornets instead.
A comparable multirole fighter of the USAF–the F-15E Strike Eagle–entered service in 1989. Meanwhile, the Super Hornet’s first flight was in 1995, and operational capability was achieved in 2001.
These delays were partly caused by the Navy’s desire to strike a balance between carrier-specific requirements and financial constraints.
Later, the F-35 program, managed by the Joint Program Office, prioritized the F-35A and F-35B due to their earlier operational needs and less complex technical requirements compared to the F-35C. In fact, the F-35C carrier variant was the last to achieve Initial Operational Capability (IOC) in 2019, following the F-35A (2016) and the F-35B (2015).
Since the F-35 was already so expensive, the variants might have had to compete for resources. The Marine Corps, which urgently needed to replace its old AV-8B Harriers, and the USAF, which had a larger aircraft inventory and a wider mission scope, were able to induct the aircraft sooner than the Navy. In general, Navy carrier-variant aircraft have some extensive technical modifications tailored to carrier operations.
The Navy’s F-35C, while critical for carrier air wings, relied on F/A-18E/F Super Hornets as a stopgap for a significant amount of time. However, this has since turned around, and the F-35C is now being prioritised for purchase, even by the US Marine Corps.
Having said that, US lawmakers and experts have repeatedly warned against delays in the next-generation fighter jet program, particularly as the threat of conflict with China in the Indo-Pacific remains a constant concern.
F/A-XX Needed In A China Conflict
Last month, Rep. Ken Calvert, R-Calif, the head of the House Appropriations subcommittee on defense, said that “any hesitancy” to move forward with the Navy’s proposed F/A-XX program will leave the service “outmatched” in a future conflict with China, as reported by Breaking Defense at the time.
Speaking at a posture hearing, he said, “We need sixth-generation fighters. The US Navy needs sixth-generation fighters. I’m concerned that any hesitancy on our part to proceed with the planned procurement of the sixth-gen fighters for the Navy will leave us dangerously outmatched in a China fight.”
“We cannot wait,” the appropriator added. “Further, we cannot expect to grow the defense industrial base by undermining it. Aviation programs that rely on highly specialized supply chains and skilled labor cannot be turned on and off like a switch.”
A previous Reuters report stated that postponing contract award by three years “would effectively cancel the program as it is currently defined,” as prices and contracts would expire during that time, almost guaranteeing a new competition.
Though little is known about the fighter jet’s capabilities, it is expected that the aircraft would be able to operate from a carrier deck and have advanced capabilities, including increased range, stealth, and AI integration.
The F/A-XX will be developed with the premise that it will need to travel vast distances in the Indo-Pacific and withstand the rising threat from China’s air defenses. The sixth-generation fighter will be fighting in contested territory.
The US Navy’s Rear Adm. Michael Donnelly had earlier said the design will have a 25% longer range than existing tactical aircraft systems, such as the F/A-18E/F and F-35C. The sixth-generation fighter will be specifically designed to work closely with unmanned aircraft using a control method known as “man-on-the-loop.”
Acting Chief of Naval Operations Adm. James Kilby said on the first day of the Navy-centric Sea Air Space exhibition outside of Washington, DC, that the US Navy requires the F/A-XX just like the USAF. “I mean, we’re talking about a fight in the Pacific. We fight together as a joint force, so having that capability is very important for us,” he added.
Later, speaking at a posture hearing, Kilby said, “The carrier is the most survivable airfield we have, period, and stop. The sixth-gen fighter is the keystone of our air wing of the future.” The aircraft carrier “brings mass volume fires over and over and over again, where a submarine will have to be reloaded and a destroyer will have to be reloaded … and take it offline. That carrier has got sustainment power, and the thing that delivers it is a fifth-gen and sixth-generation fighter into the future.”
While internal discussions rage over the future of the F/A-XX program, which is largely being developed to battle in the Pacific, China has already begun flight testing its two next-generation fighter-like aircraft. One is widely, albeit unofficially, referred to as the J-36, and the other is known as the J-XDS, or J-50.
6 months ago
In A Rare Move, China Releases Crucial Details About 12,000-KM Nuclear Missile That Can Strike The U.S. Anywhere!
Known for its secretive nuclear weapons program, China has for the first time revealed key details of one of the country’s nuclear weapons.
In a rare gesture that has taken China watchers by surprise, China’s state broadcaster CCTV has released crucial details about one of the country’s premier nuclear-capable missile systems, the DF-5.
China’s nuclear program has traditionally been highly secretive, particularly regarding specific missile capabilities and deployments, and it was not clear why the information about the DF-5, an intercontinental ballistic missile (ICBM), was made public.
The timing of the disclosure is also interesting, as it comes just days after the 2025 Shangri-La Dialogue in Singapore, Asia’s largest defense and security forum.
Here, the US delivered a clear message: The Indo-Pacific is a top priority for the Trump administration amid what it sees as China’s aggressive posturing.
At the dialogue, US Defense Secretary Pete Hegseth urged Asian allies to step up their defense in response to China’s military build-up near Taiwan.
Hegseth mentioned China more than 20 times in his first-ever speech at Shangri-La and issued a direct warning to Beijing.
“Any attempt by Communist China to conquer Taiwan by force would result in devastating consequences for the Indo-Pacific and the world. There’s no reason to sugarcoat it,” Hegseth said.
He also underlined that the US is serious about countering China’s rising influence in the West as well.
“We’re also increasing security in the Western Hemisphere and taking back the Panama Canal from malign Chinese influence. It is key terrain, after all. China did not build that canal. We did. And we will not allow China to weaponize it or control it,” he said.
The tone of Hegseth’s speech took many by surprise. China, certainly, was taken aback.
“If deterrence fails, and if called upon by my Commander in Chief, we are prepared to do what the Department of Defense does best – fight and win — decisively,” he said.
The public unveiling of DF-5 could be a response to Hegseth’s speech. The ICBM DF-5 has a range of 12,000 km and is capable of reaching the US mainland as well as Western European countries.
This could be China’s way of showing its capabilities and sending a message that Beijing is serious about protecting its sovereignty and interests.
The DF-5 And Its Capabilities
In China, official disclosures typically use vague language, avoiding precise details about the weapons. However, the broadcast on June 2 was unique in that it provided specific and in-depth information about a strategic Chinese nuclear missile.
It disclosed that the two-stage missile, which it described as China’s “first-generation strategic ICBM,” could deliver a single nuclear warhead with an explosive yield of between 3 and 4 megatons of TNT.
For perspective, this is roughly 200 times greater than the atomic bombs dropped by the US on Hiroshima and Nagasaki at the end of World War II.
It added that the missile had a maximum range of 12,000 km (7,460 miles), sufficient to strike the continental United States and western Europe, and was accurate to within 500 meters.
The report further said that the missile was “32.6 meters in length with a diameter of 3.35 meters and a launch weight of 183 tons.”
During the broadcast, former People’s Liberation Army instructor Song Zhongping said the missile, which was developed in the early 1970s and entered service in 1981, played a critical role in China’s nuclear deterrence strategy.
“Without the DF-5, China wouldn’t be regarded as a nation with credible intercontinental strike capability. It was instrumental in China’s emergence as a nuclear power, demonstrating to the world that China must be taken seriously,” Song said.
According to Missile Threat, a platform dedicated to missile technology, “The DF-5 (Dong Feng-5 / CSS-4) is a silo-based intercontinental ballistic missile (ICBM). It was the first ICBM that China developed, and has one of the longest ranges. These missiles are capable of delivering large nuclear payloads throughout the United States and Western Europe.”
The DF-5 also served as the basis for several other military and space programs. “These efforts included the Long March-2C space launch vehicle, the DF-6 fractional orbital bombardment program (cancelled), the PRC penetration aid program, and the DF-5B,” it said.
The DF-5B is similar to the capabilities of the DF-5, but can carry MIRVed warheads. The MIRV, or Multiple Independently Targetable Reentry Vehicle, technology enables a single missile to carry and release multiple nuclear warheads, each capable of striking a different target across a wide geographic area.
Furthermore, in 2017, media reports surfaced that China had tested a new variant of the missile, the DF-5C, which is equipped with 10 multiple independently targetable reentry vehicles (MIRVs).
A Hidden Warning To The World?
Former PLA instructor Song Zhongping suggested that revealing details about the DF-5 could also mean that China is now in possession of much more advanced nuclear weapons and missile silos. Thus, Beijing feels confident in releasing key specifications of the DF-5 into the public domain.
“What we’re seeing is the phasing out of older systems – ones that have already served their purpose. The message is clear: China has far more powerful capabilities it has not shown the world.”
It is worth noting that China also has ICBMs like DF-31 and DF-41 in its arsenal. Last year, China conducted a successful test of the DF-31. Incidentally, this was the first time in four decades that China acknowledged testing an ICBM.
According to SIPRI, China is the third-biggest nuclear power in the world after Russia and the US. In 2024, Beijing had over 500 nuclear warheads in its arsenal.
However, according to the Pentagon estimates, China already has over 600 nuclear warheads, and it will have an arsenal of over 1,000 nuclear weapons by 2030.
Known for its secretive nuclear weapons program, China has for the first time revealed key details of one of the country’s nuclear weapons.
In a rare gesture that has taken China watchers by surprise, China’s state broadcaster CCTV has released crucial details about one of the country’s premier nuclear-capable missile systems, the DF-5.
China’s nuclear program has traditionally been highly secretive, particularly regarding specific missile capabilities and deployments, and it was not clear why the information about the DF-5, an intercontinental ballistic missile (ICBM), was made public.
The timing of the disclosure is also interesting, as it comes just days after the 2025 Shangri-La Dialogue in Singapore, Asia’s largest defense and security forum.
Here, the US delivered a clear message: The Indo-Pacific is a top priority for the Trump administration amid what it sees as China’s aggressive posturing.
At the dialogue, US Defense Secretary Pete Hegseth urged Asian allies to step up their defense in response to China’s military build-up near Taiwan.
Hegseth mentioned China more than 20 times in his first-ever speech at Shangri-La and issued a direct warning to Beijing.
“Any attempt by Communist China to conquer Taiwan by force would result in devastating consequences for the Indo-Pacific and the world. There’s no reason to sugarcoat it,” Hegseth said.
He also underlined that the US is serious about countering China’s rising influence in the West as well.
“We’re also increasing security in the Western Hemisphere and taking back the Panama Canal from malign Chinese influence. It is key terrain, after all. China did not build that canal. We did. And we will not allow China to weaponize it or control it,” he said.
The tone of Hegseth’s speech took many by surprise. China, certainly, was taken aback.
“If deterrence fails, and if called upon by my Commander in Chief, we are prepared to do what the Department of Defense does best – fight and win — decisively,” he said.
The public unveiling of DF-5 could be a response to Hegseth’s speech. The ICBM DF-5 has a range of 12,000 km and is capable of reaching the US mainland as well as Western European countries.
This could be China’s way of showing its capabilities and sending a message that Beijing is serious about protecting its sovereignty and interests.
The DF-5 And Its Capabilities
In China, official disclosures typically use vague language, avoiding precise details about the weapons. However, the broadcast on June 2 was unique in that it provided specific and in-depth information about a strategic Chinese nuclear missile.
It disclosed that the two-stage missile, which it described as China’s “first-generation strategic ICBM,” could deliver a single nuclear warhead with an explosive yield of between 3 and 4 megatons of TNT.
For perspective, this is roughly 200 times greater than the atomic bombs dropped by the US on Hiroshima and Nagasaki at the end of World War II.
It added that the missile had a maximum range of 12,000 km (7,460 miles), sufficient to strike the continental United States and western Europe, and was accurate to within 500 meters.
The report further said that the missile was “32.6 meters in length with a diameter of 3.35 meters and a launch weight of 183 tons.”
During the broadcast, former People’s Liberation Army instructor Song Zhongping said the missile, which was developed in the early 1970s and entered service in 1981, played a critical role in China’s nuclear deterrence strategy.
“Without the DF-5, China wouldn’t be regarded as a nation with credible intercontinental strike capability. It was instrumental in China’s emergence as a nuclear power, demonstrating to the world that China must be taken seriously,” Song said.
According to Missile Threat, a platform dedicated to missile technology, “The DF-5 (Dong Feng-5 / CSS-4) is a silo-based intercontinental ballistic missile (ICBM). It was the first ICBM that China developed, and has one of the longest ranges. These missiles are capable of delivering large nuclear payloads throughout the United States and Western Europe.”
The DF-5 also served as the basis for several other military and space programs. “These efforts included the Long March-2C space launch vehicle, the DF-6 fractional orbital bombardment program (cancelled), the PRC penetration aid program, and the DF-5B,” it said.
The DF-5B is similar to the capabilities of the DF-5, but can carry MIRVed warheads. The MIRV, or Multiple Independently Targetable Reentry Vehicle, technology enables a single missile to carry and release multiple nuclear warheads, each capable of striking a different target across a wide geographic area.
Furthermore, in 2017, media reports surfaced that China had tested a new variant of the missile, the DF-5C, which is equipped with 10 multiple independently targetable reentry vehicles (MIRVs).
A Hidden Warning To The World?
Former PLA instructor Song Zhongping suggested that revealing details about the DF-5 could also mean that China is now in possession of much more advanced nuclear weapons and missile silos. Thus, Beijing feels confident in releasing key specifications of the DF-5 into the public domain.
“What we’re seeing is the phasing out of older systems – ones that have already served their purpose. The message is clear: China has far more powerful capabilities it has not shown the world.”
It is worth noting that China also has ICBMs like DF-31 and DF-41 in its arsenal. Last year, China conducted a successful test of the DF-31. Incidentally, this was the first time in four decades that China acknowledged testing an ICBM.
According to SIPRI, China is the third-biggest nuclear power in the world after Russia and the US. In 2024, Beijing had over 500 nuclear warheads in its arsenal.
However, according to the Pentagon estimates, China already has over 600 nuclear warheads, and it will have an arsenal of over 1,000 nuclear weapons by 2030.
6 months ago
Challenges posed by Trump and Putin push UK to adopt new NATO first defense policy
The U.K. on Monday announced new plans to overhaul its defensive posture in the wake of Russian President Vladimir Putin’s invasion of Ukraine and potential challenges posed by President Donald Trump's threat to withdraw U.S. troops from the continent.
British Prime Minister Keir Starmer said he would bring his country to "war-fighting readiness" by investing dozens of billions of dollars in the building of 12 submarines, weapons and munitions manufacturing, AI and other tech, and most notably, a significant investment in nuclear deterrence.
The announcement came after a Strategic Defense Review by an external board found several areas in the U.K. that need to improve in order to effectively deter aggressors like Russia, as well as North Korea, Iran and China.
While the review heavily focused on changes that need to be made to the U.K.’s defense readiness, it also identified a need to bolster societal resilience and support.
"Our response cannot be confined to increasing defense spending," Starmer said in a statement from the report. "We also need to see the biggest shift in mindset in my lifetime: to put security and defense front and center—to make it the fundamental organizing principle of government."
The 144-page plan released by the British government on Monday laid out a new defense strategy to tackle threats "more serious and less predictable than at any time since the Cold War."
However, the biggest investment the U.K. revealed in its defense overhaul is a near $20.3 billion commitment to its nuclear warhead program in a move to expand its deterrence level, which, the report said, "sends the ultimate warning to anyone who seeks to do us harm."
The push has been described as a "NATO first" policy that will heavily focus on the immediate threats posed by Russia to the European continent. However, the plan is not a "NATO only" policy.
The U.K. plans to produce a new submarine every 18 months until it secures a fleet of up to 12 nuclear-powered attack submarines under the AUKUS program, which is a trilateral security partnership between Australia, the U.K. and the U.S. – which focuses on security and stability in the Indo-Pacific, particularly in the face of increased Chinese aggression in the region.
Defense Secretary John Healey said, "We are in a new era of threat, which demands a new era for U.K. defense."
Starmer ordered the review last summer, shortly after he secured the top job.
Security experts have warned that the threat Russia poses as it advances its war machine is assessed to be a generational threat, and one that will likely out-live the war in Ukraine or even a Putin presidency, and European nations have been scrambling to react to the new reality.
The re-election of Trump became another challenge European leaders have grappled with.
Though Trump pushed Nato leaders to increase their defense spending during his first term, most nations did not meet their GDP defense spending commitments under NATO until after Russia invaded Ukraine.
Now, just eight of the 32 NATO nations do not meet the 2% GDP spending commitments, while five nations, including the U.S. spend more than 3%.
NATO nations have increasingly called for an increase in defense spending and a push to be less dependent on the U.S.’s military industrial base.
While the U.K. has pledged to spend 2.5% of its GDP on defense by 2027, with an increase to 3% by 2030, Trump has called for NATO nations to spend 5% -- though the alliance has not yet agreed to such a plan, which the U.S. also falls short on, spending 3.38% according to figures released in 2024.
The U.K. is also looking to take more of a leadership role in NATO, particularly as the reliability of the U.S. has been called into question amid the war in Russia, and amid threats by Trump that he may drawdown troop numbers in Europe.
The U.K. on Monday announced new plans to overhaul its defensive posture in the wake of Russian President Vladimir Putin’s invasion of Ukraine and potential challenges posed by President Donald Trump's threat to withdraw U.S. troops from the continent.
British Prime Minister Keir Starmer said he would bring his country to "war-fighting readiness" by investing dozens of billions of dollars in the building of 12 submarines, weapons and munitions manufacturing, AI and other tech, and most notably, a significant investment in nuclear deterrence.
The announcement came after a Strategic Defense Review by an external board found several areas in the U.K. that need to improve in order to effectively deter aggressors like Russia, as well as North Korea, Iran and China.
While the review heavily focused on changes that need to be made to the U.K.’s defense readiness, it also identified a need to bolster societal resilience and support.
"Our response cannot be confined to increasing defense spending," Starmer said in a statement from the report. "We also need to see the biggest shift in mindset in my lifetime: to put security and defense front and center—to make it the fundamental organizing principle of government."
The 144-page plan released by the British government on Monday laid out a new defense strategy to tackle threats "more serious and less predictable than at any time since the Cold War."
However, the biggest investment the U.K. revealed in its defense overhaul is a near $20.3 billion commitment to its nuclear warhead program in a move to expand its deterrence level, which, the report said, "sends the ultimate warning to anyone who seeks to do us harm."
The push has been described as a "NATO first" policy that will heavily focus on the immediate threats posed by Russia to the European continent. However, the plan is not a "NATO only" policy.
The U.K. plans to produce a new submarine every 18 months until it secures a fleet of up to 12 nuclear-powered attack submarines under the AUKUS program, which is a trilateral security partnership between Australia, the U.K. and the U.S. – which focuses on security and stability in the Indo-Pacific, particularly in the face of increased Chinese aggression in the region.
Defense Secretary John Healey said, "We are in a new era of threat, which demands a new era for U.K. defense."
Starmer ordered the review last summer, shortly after he secured the top job.
Security experts have warned that the threat Russia poses as it advances its war machine is assessed to be a generational threat, and one that will likely out-live the war in Ukraine or even a Putin presidency, and European nations have been scrambling to react to the new reality.
The re-election of Trump became another challenge European leaders have grappled with.
Though Trump pushed Nato leaders to increase their defense spending during his first term, most nations did not meet their GDP defense spending commitments under NATO until after Russia invaded Ukraine.
Now, just eight of the 32 NATO nations do not meet the 2% GDP spending commitments, while five nations, including the U.S. spend more than 3%.
NATO nations have increasingly called for an increase in defense spending and a push to be less dependent on the U.S.’s military industrial base.
While the U.K. has pledged to spend 2.5% of its GDP on defense by 2027, with an increase to 3% by 2030, Trump has called for NATO nations to spend 5% -- though the alliance has not yet agreed to such a plan, which the U.S. also falls short on, spending 3.38% according to figures released in 2024.
The U.K. is also looking to take more of a leadership role in NATO, particularly as the reliability of the U.S. has been called into question amid the war in Russia, and amid threats by Trump that he may drawdown troop numbers in Europe.














