Build a modern, user-friendly food delivery platform with a customizable DoorDash Clone App designed for fast launch, smooth ordering, and scalable business growth.
https://whitelabelfox.com/...
#doordashclone #DoorDashCloneApp #doordashlikeappdevelopment #doordashclonescript #applikedoordash #doordashcloneappdevelopmentcompany #doordashcloneappdevelopment #fooddeliveryapp

DoorDash Clone App Development | Launch Your Delivery Service
Build a DoorDash-inspired app with our development solutions. Offer a personalized food delivery platform with features to enhance user experience and streamline operations.
https://whitelabelfox.com/doordash-clone-app/The freelance economy is growing faster than ever, and businesses are looking for ways to tap into this booming market. Building a freelance marketplace from scratch can be time-consuming, expensive, and technically complex. That’s where Fiverr clone scripts come into play.
These ready-made solutions provide entrepreneurs with a quick and cost-effective way to launch their own freelance marketplace. But beyond speed, Fiverr clone scripts also bring flexibility, scalability, and user-friendly features that make them a smart choice for startups and enterprises alike.
How It Speeds Up Development
Pre-Built Features: Everything from dashboards to payment systems comes ready to use.
Customizable Design: Tailor the look and feel to match your brand identity.
Faster Launch Time: Get your marketplace up and running in weeks instead of months.
Cost-Effective: Save money on development and allocate more budget to marketing.
Scalable: Add new features as your platform grows without starting from scratch.
Use Cases of Fiverr Clone Solutions
Startups launching niche marketplaces (e.g., freelance designers, tutors, or consultants).
Enterprises are creating internal gig platforms for their workforce.
Agencies that want to build white-label freelance platforms for clients.
Final Thoughts
The demand for freelance platforms will only grow in 2025 and beyond. “When you use a Fiverr clone script, entrepreneurs can cut down development time, reduce costs, and still deliver a professional, feature-rich marketplace. Whether you’re building a Fiverr clone website or app, the right script can help you focus on what matters most - growing your business and serving your users.
https://www.logicspice.com...
With an Uber for Tow Trucks app, you can automate bookings, reduce response time, and manage drivers effortlessly all while increasing customer trust and revenue.
Visit us: https://www.spotnrides.com...
Whatsapp: https://wa.me/919600695595
#UberForTowTrucks #TowingBusiness #OnDemandApp #UberLikeRoadsideAssistance #TowTruckApp #OnDemandTowing #RoadsideAssistance #TowingBusinessApp #FleetManagement #TowingServices #VehicleRecoveryAppSolution #EmergencyTowingBookingSoftware #SmartTowingAppDevelopment #TowingSoftware #uberfortow #TowBookingApp #AIPoweredTowApp
Book your free call: https://www.beleaftechnolo...
Whatsapp: +91 7904323274
Telegram: BeleafSoftTech
Mail to: businessbeleaftechnologies.com
Launch your own interactive language-learning platform with OyeLabs’ Duolingo Clone. Features include gamified lessons, rewards, progress tracking, multilingual support, and complete admin control.
#DuolingoClone #EdTechStartup #LanguageApp #Gamification #LMS
https://www.appclonescript...
#foodandgrocerydeliveryapp , #OnDemandDeliveryApp , #talabatcloneappdevelopment , #talabatclonescript #MobileAppDevelopment #deliveryappsolution
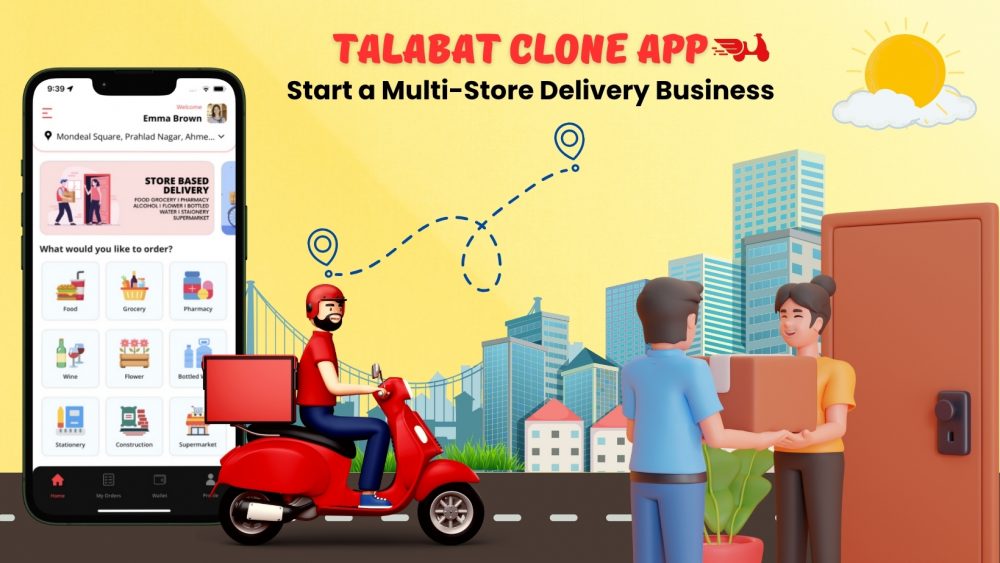
Start a Multi-Store Delivery Business with Talabat Clone App
Launch your Talabat Clone App today! Build an On-Demand Food, Grocery, and Other Items Delivery App and tap into the booming delivery market.
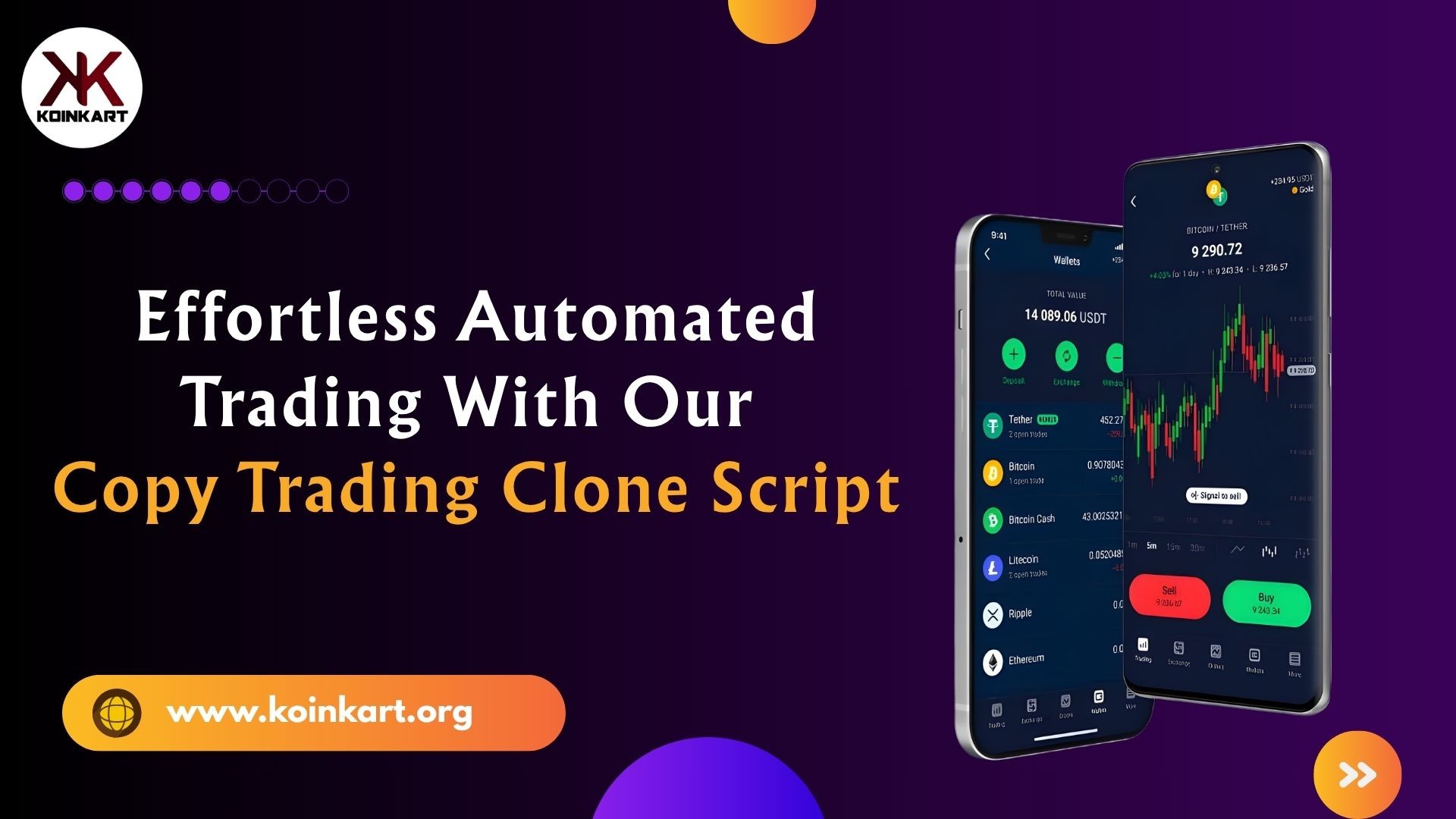
https://www.appclonescript.com/start-multi-store-delivery-business-with-talabat-clone-app/Effortless automated trading is now possible with our advanced Copy Trading Clone Script. Koinkart is the premier Copy Trading Clone Script provider, trusted for high performance and smooth trading automation. Designed for business owners and crypto platforms, this ready-made solution helps your users copy expert trades in real time and grow faster.
Explore the features designed for our clients:
Auto-copy trades from top-performing traders
Secure architecture with high-level encryption
Real-time analytics and performance dashboards
Multi-asset support for flexible trading
Easy admin control with revenue-driven modules
Get Live Demo or Quote Now!
Website: https://www.koinkart.org/c...
WhatsApp: +91 93842 63771
Mail: businesskoinkart.org
Get a ready-made, white-label Gojek Clone Script to launch your on-demand business. 100% customizable with advanced features to manage 101+ services in one seamless platform. Visit our website for more information: https://whitelabelfox.com/...
#gojekclone #gojekcloneapp #gojekcloneappdevelopment
#applikegojek #gojekappclone #gojekclonescript #ondemandbusiness #OnDemandApps #allinoneapp #gojekclonescript #multiservicesapp #ubercloneapp #fooddeliveryapp #GroceryDeliveryApp #ondemandmultiservicesapp #OnDemandServices #ondemandappdevelopmentcompany
💻 Launch instantly with our Vinted Clone Script from Sangvish! 🚀
Visit - https://sangvish.com/vinte...
#vintedclone #Sangvish #business #vintedcloneapp #usa #uk #fashion #marketplace
✨ Launch your app. Grow your brand. Drive your success.
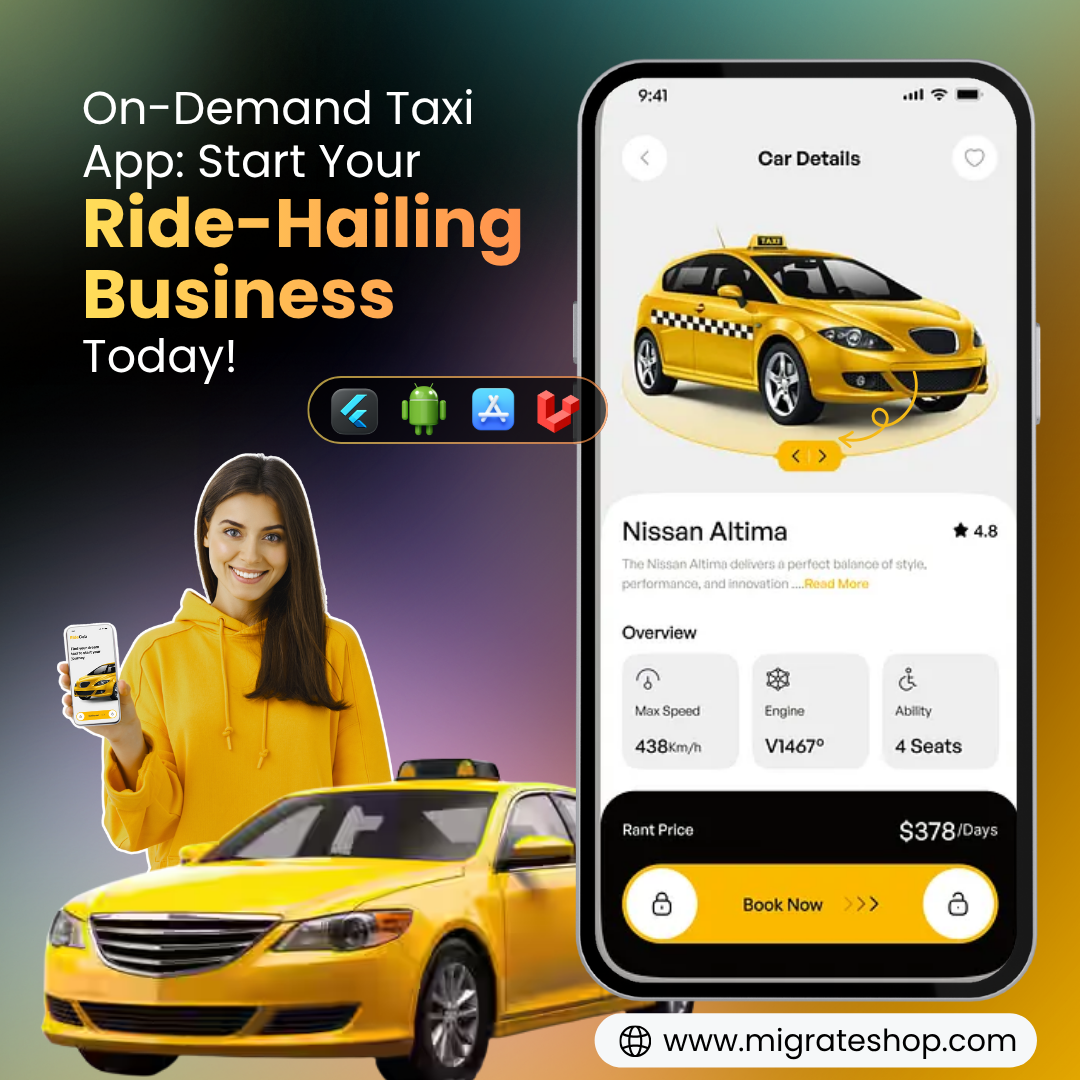
Start Now: https://migrateshop.com/ub...
#migrateshop #uberclone #ubercloneapp #OnDemandTaxiApp #OnDemandServices #TaxiAppDevelopment #RideHailing #taxiapp #entreprenure #business #apps
#AI -Driven Commerce Intelligence
#AR / #VR Shopping Experiences
#AIVoice & Conversational Commerce
Cloud & #EdgeComputing
#Blockchain -Powered Payments
Predictive #DataAnalytics
#Automation & Workflow Integration
Our mission is simple to help brands sell smarter, scale faster, and deliver seamless digital shopping experiences. We combine modern technology stacks (#React, NodeJS, Next.js, Python) with deep ecommerce expertise to build robust, scalable, and future-ready solutions.
Let our #webdevelopers turn your vision into a powerful online store built for the future.
-------------
: https://www.kpis.in/ecomme...
: infokpis.in
+91-6350359218
-------------
#EcommerceWebDevelopment #EcommerceDevelopment #DigitalTransformation #AIChatbots #WebDevelopment #EcommerceWebsiteDevelopment #WebsiteDevelopment #digitalmarketing #HireeCommerceWebsiteDevelopers #gojekclone #AppDevelopment #ITCompany #KPISPvtLtd #Jaipur
Kickstart your on-demand business with our Gojek Clone Script. A robust and scalable solution that lets startups and enterprises offer taxi rides, food and grocery delivery, courier services, and more — all within one unified super app platform. Visit our website for more info: https://gojekcloneapp.com/
#gojekclone #gojekcloneapp #gojekcloneappdevelopment #gojekclonescript #gojekappclone #applikegojek #gojeklikeapp #gojekcloneappscript #gojekclonesolution #allinoneapp #multiservicesapp #gojekclonesoftware #appclonegojek
Get a Gojek Clone App Script for Multi-Service Business
The Gojek Clone is a smart and efficient on-demand multiservice platform offering 130+ online services. Get a demo of the Gojek Clone script to start your business today.
https://gojekcloneapp.com/Start your own food delivery platform like Zomato with our ready-made Zomato Clone App.
Easily connect restaurants, delivery partners, and customers in one smart app.
✅ User-friendly design
✅ Fast and secure orders
✅ 100% customizable for your brand
Make your food delivery dream a reality today! 🌟
Get a Free Demo
Mail id : sales @abservetech .com
Phone number: + 91 9222479222
#ZomatoClone #fooddeliveryapp #OnDemandApp #AppDevelopment #startup #Abservetech #usa #uk #india #australia #inland #india #greenland #Delivery #business #zomoto #southamerica #Canada #spain #russia #madurai #AppDevelopment #cloneapp #clone script #dubai #egypt #mexico #japan
https://www.webdevelopment...
Koinkart is the leading provider of a Coinbase Clone Script, crafted to help entrepreneurs and enterprises build a highly profitable, ROI-focused crypto trading platform that drives growth and long-term financial success. Our script is developed with advanced technologies to ensure smooth performance, scalability, and continuous revenue flow.
We list out the features offered for our clients:
Multiple Revenue Streams
High-Performance Trading Engine
Advanced Liquidity & Market-Making Tools
Native Token Integration:
Comprehensive Admin Control:
WhatsApp: +91 93842 63771
Mail: businesskoinkart.org
Website: https://www.koinkart.org/c...
Build your own Zillow Clone App with advanced real estate features, custom design, and seamless property listing management for your business growth.
https://whitelabelfox.com/...
#ZillowClone #zillowcloneapp #ZillowCloneScript #zillowcloneappsolution #zillowcloneappdevelopement #RealEstateApp #realestatebusiness #AppDevelopment #startupsolution #OnDemandApp
Get your own Uber Clone Script for your business
Spotnrides offers a reliable Uber Clone solution designed to provide riders with a safe and convenient travel experience while helping businesses build lasting customer relationships. Our white-label Uber Clone app supports multiple languages, enabling better communication and service for users across regions. The platform features helpful tools such as trip history tracking, customer feedback, and maintenance support.
Try our free live demo to explore how Spotnrides can simplify ride management for your business. https://www.spotnrides.com...
#uberclone #ubercloneapp #aipoweredtaxibookingapp #taximanagementsoftware #dispatchsystemfortaxibusiness #cabbookingsoftware #taxifleetmanagement #automatedtaxidispatch #airporttaxidispatchsoftware #airportshuttleservicesoftware #shuttletaxidispatchsoftware #taxischedulingsoftware #taxifleetdispatch #passengertransportationsoftware #passengertaxidispatchsoftware #cabmanagementplatform #carrentalmanagementsystem #drivermonitoringsoftware #usermonitoringsoftware #customermonitoringsoftware
#multilocationtaxidispatchsoftware #affordabletaxidispatchsystem #besttaximanagementsoftware #cloudbaseddispatchsystem
100% customizable & scalable solution
Real-time booking & secure payment integration
Advanced admin panel & analytics dashboard
iOS + Android + Web support
Start your on-demand service business today with a ready-made UrbanClap Clone that’s built to scale!
Learn more: https://oyelabs.com/urbanc...
#urbanclapclone #OnDemandApp #ServiceMarketplace #oyelabs #AppDevelopment
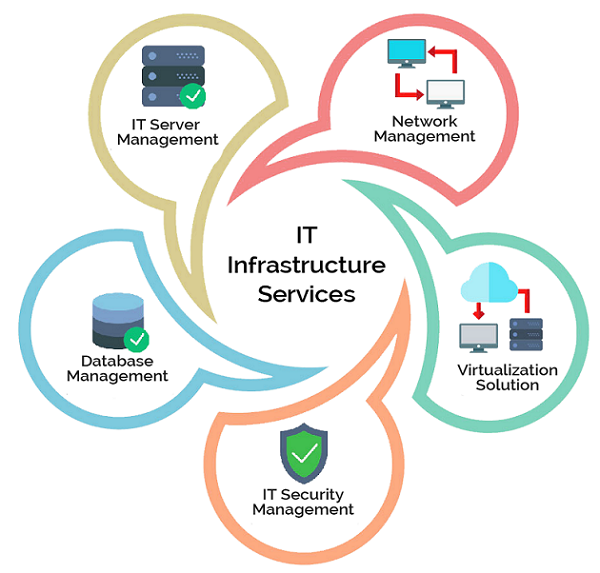
Understanding IT Infrastructure Services
IT infrastructure services encompass the essential hardware, software, network resources, and facilities required to develop, manage, and support an organization’s IT environment. These services include data centers, servers, storage systems, networking equipment, and cloud resources. Their primary goal is to ensure seamless connectivity, data processing, and storage, enabling businesses to operate efficiently. Effective IT infrastructure provides a reliable foundation that supports business applications, enhances security, and facilitates innovation. As technology evolves, organizations increasingly rely on a mix of on-premises and cloud-based infrastructure to meet dynamic demands. Proper management of these services ensures high availability, scalability, and security, which are critical for maintaining competitive advantage in today's digital landscape. Investing in robust IT infrastructure is fundamental for digital transformation and long-term success.
Key Components of IT Infrastructure Services
The core components of IT infrastructure services include physical hardware, network systems, data storage solutions, and cloud platforms. Physical hardware involves servers, computers, and networking devices like routers and switches that form the backbone of IT operations. Network systems connect all hardware and enable communication within and outside the organization, ensuring data flows smoothly. Data storage solutions such as SANs and NAS enable organizations to manage vast amounts of information securely. Cloud platforms like AWS, Azure, and Google Cloud provide scalable, flexible resources that adapt to business needs.
Source: https://www.marketresearch...
Learn more: https://www.spotnrides.com...
Whatsapp: https://wa.me/919600695595
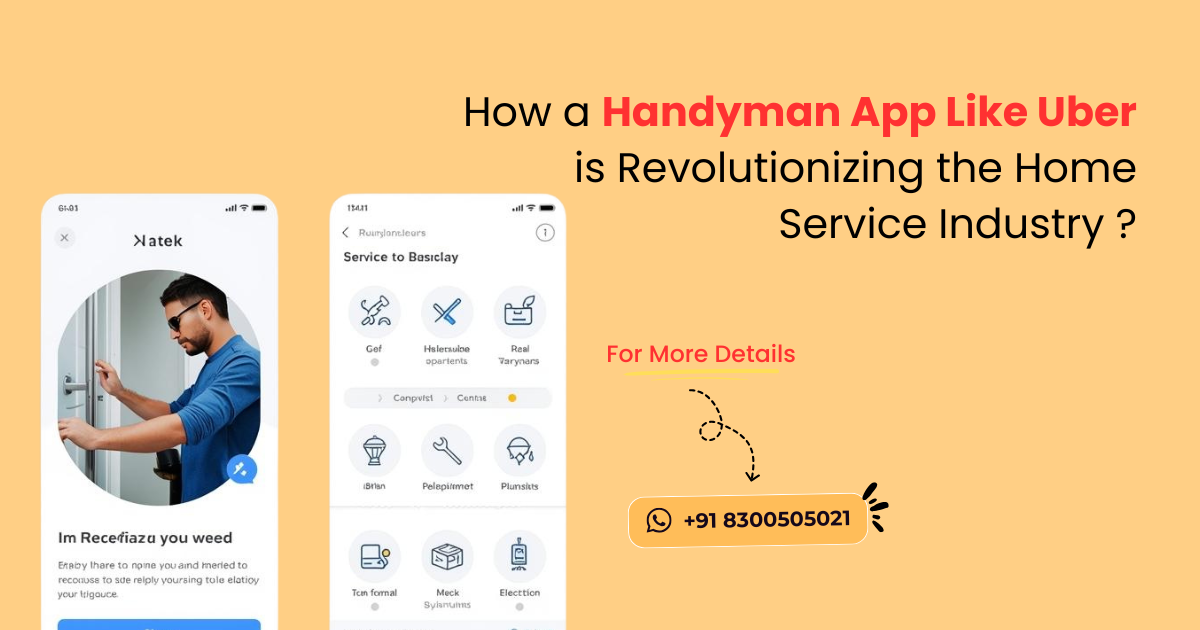
#HandymanApp #HandymanBusiness #OnDemandHandyman #HandymanServices #ServiceAppDevelopment #HomeRepairApp #SpotnRides #HandymanStartup #MobileAppSolutions #HandymanBookingApp #UberforHomeservices #HomeServicesApp
Tired of searching for a reliable handyman? A Handyman App Like Uber connects you with skilled professionals for quick home repairs, installations, and maintenance — anytime, anywhere!
👉 Explore more at - https://sangvish.com/handy...
#HandymanApp #handymanservice #applikeuber #handymen #business #startups
Visit us : https://www.spotnrides.com...
Whatsapp: https://wa.me/919600695595
#ubercloneapp #AIPoweredApp #SpotnRides #TaxiAppSolution #RideHailingApp #OnDemandTaxiApp #EasyTaxiCloneApp #TaxiSoftware #RideSharingApp #TaxiBusinessGrowth #lyftcloneapp #cabifycloneapp #GettCloneApp #CareemCloneApp #BoltCloneApp #99CloneApp #YellowCabClone
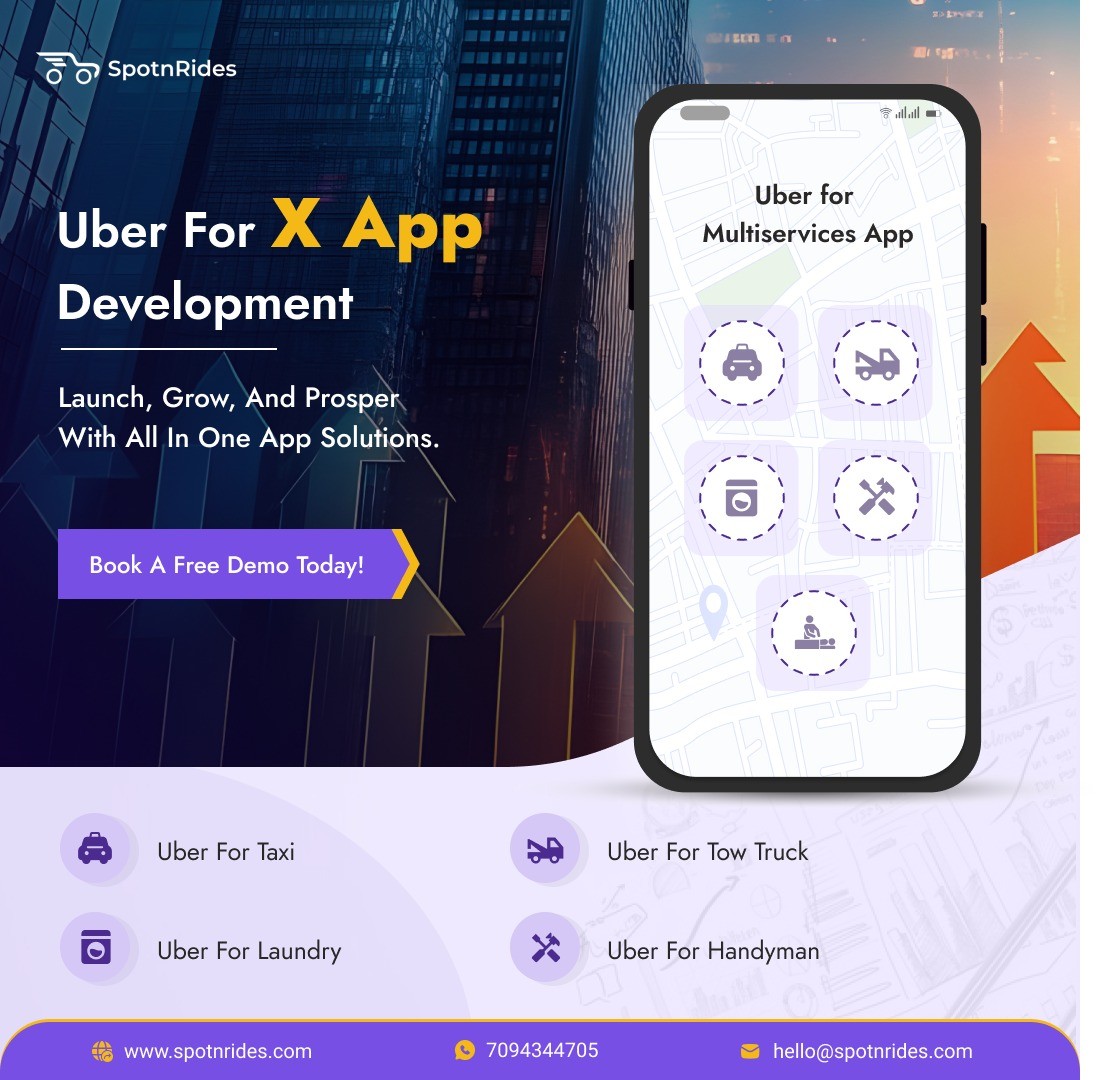
Launch your dream business with SpotnRides’ Uber for X platform, designed for any niche — from beauty to delivery. One platform, endless possibilities.
Visit us: https://www.spotnrides.com...
Whatsapp: https://wa.me/919600695595
#FutureTrendsofUberforX #uberformultiservicesapp #ubeforx #uberforxappdevelopment #uberforxbusiness #uberforxbusinessmodel #uberforxscript #allinoneappservices #SpotnRides #superapps #multiservicebusiness #gojekclone #goieckcloneapp #SuperAppDevelopment #multiservicesbookingapp
Create a powerful peer-to-peer car rental app using Oyelabs’ white-label Turo clone solution. Packed with advanced features like vehicle management, GPS tracking, secure payment gateways, and a user-friendly admin panel — it’s the fastest way for entrepreneurs to launch their car rental business.
🔗 https://oyelabs.com/turo-c...
#TuroClone #CarRentalApp #CarSharingBusiness #OnDemandApp #MobilitySolutions
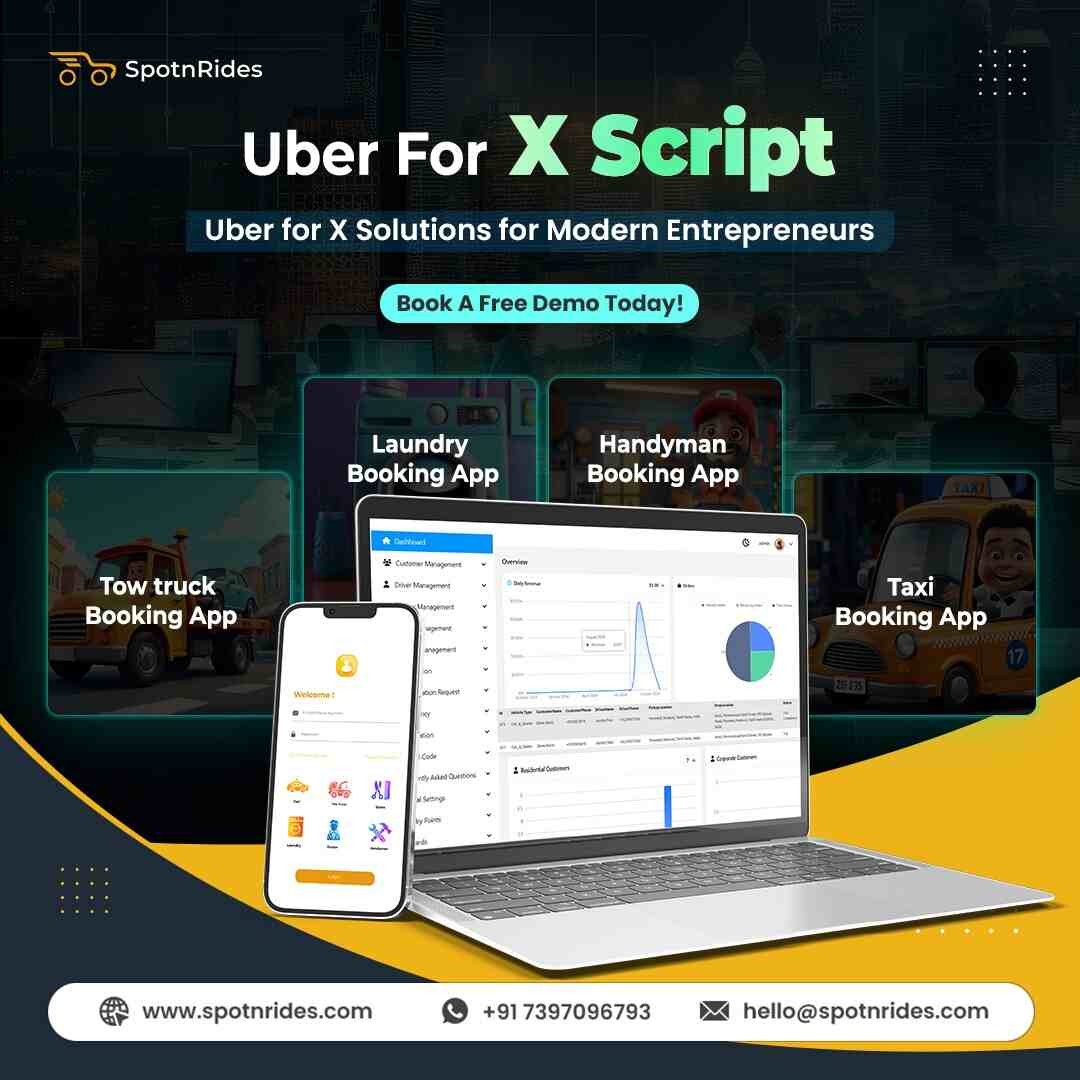
With SpotnRides’ Uber for X App, you can automate bookings, manage service providers, and scale your operations effortlessly.
Bring innovation, speed, and transparency to your on-demand business today!
Visit us: https://www.spotnrides.com...
Whatsapp: https://wa.me/919600695595
#FutureTrendsofUberforX #uberformultiservicesapp #ubeforx #uberforxappdevelopment #uberforxbusiness #uberforxbusinessmodel #uberforxscript #allinoneappservices #SpotnRides #superapps #multiservicebusiness #gojekclone #goieckcloneapp
Create a powerful peer-to-peer car rental app using Oyelabs’ white-label Turo clone solution. Packed with advanced features like vehicle management, GPS tracking, secure payment gateways, and a user-friendly admin panel — it’s the fastest way for entrepreneurs to launch their car rental business.
🔗 https://oyelabs.com/turo-c...
#TuroClone #CarRentalApp #CarSharingBusiness #OnDemandApp #MobilitySolutions
Whether you’re a startup or an established brand, we deliver impactful digital strategies that boost your online presence and drive long-term growth. Choose Techfinad — your trusted digital growth partner in Noida.
Visit Us : https://techfinad.com/
Want to create a Forex trading app that helps traders maximize profits and gives your business an edge? Koinkart delivers Forex Trading App Development with smart automation and advanced analytics to boost ROI.
Explore the features designed for our clients:
AI-based trade insights
Automated trading bots
Low-latency order execution
Advanced risk management modules
We develop apps that make trading efficient, profitable, and user-friendly. Build your personalized Forex app today with Koinkart!
📲 Get Live Demo or Quote Now!
🌐 Website: https://www.koinkart.org/f...
📞 WhatsApp: +91 93842 63771
https://www.esiteworld.com...
#grocerydelivery #jeebclone #groceryapp #DeliveryApp #startup #qatarbusiness #mobileapp
Create a powerful peer-to-peer car rental app using Oyelabs’ white-label Turo clone solution. Packed with advanced features like vehicle management, GPS tracking, secure payment gateways, and a user-friendly admin panel — it’s the fastest way for entrepreneurs to launch their car rental business.
🔗 https://oyelabs.com/turo-c...
#TuroClone #CarRentalApp #CarSharingBusiness #OnDemandApp #MobilitySolutions