5 days ago
Searching for a smarter, safer way to build trust in your business? Beleaf Technology is here to help you make it real. At Beleaf, we don’t just build blockchains; we build connections. Our private blockchain solutions are crafted to help your business run smoother, safer, and smarter. Whether you’re exploring smart contracts or looking to secure your data, we’ll guide you every step of the way. Because innovation feels better when it’s built on trust, care, and collaboration.
Book your free call: https://www.beleaftechnolo...
Whatsapp: +91 7904323274
Telegram: BeleafSoftTech
Mail to: businessbeleaftechnologies.com
Book your free call: https://www.beleaftechnolo...
Whatsapp: +91 7904323274
Telegram: BeleafSoftTech
Mail to: businessbeleaftechnologies.com
9 days ago
In today’s digital marketplace, your #website isn’t just a storefront it’s the heart of your business. As a leading #EcommerceWebsiteDevelopment Company, at #KrishnaPadamITSolution , we design and develop next-generation #ecommerce platforms powered by modern #technology and innovation. Our Expertise Includes:
#AI -Driven Commerce Intelligence
#AR / #VR Shopping Experiences
#AIVoice & Conversational Commerce
Cloud & #EdgeComputing
#Blockchain -Powered Payments
Predictive #DataAnalytics
#Automation & Workflow Integration
Our mission is simple to help brands sell smarter, scale faster, and deliver seamless digital shopping experiences. We combine modern technology stacks (#React, NodeJS, Next.js, Python) with deep ecommerce expertise to build robust, scalable, and future-ready solutions.
Let our #webdevelopers turn your vision into a powerful online store built for the future.
-------------
: https://www.kpis.in/ecomme...
: infokpis.in
+91-6350359218
-------------
#EcommerceWebDevelopment #EcommerceDevelopment #DigitalTransformation #AIChatbots #WebDevelopment #EcommerceWebsiteDevelopment #WebsiteDevelopment #digitalmarketing #HireeCommerceWebsiteDevelopers #gojekclone #AppDevelopment #ITCompany #KPISPvtLtd #Jaipur
#AI -Driven Commerce Intelligence
#AR / #VR Shopping Experiences
#AIVoice & Conversational Commerce
Cloud & #EdgeComputing
#Blockchain -Powered Payments
Predictive #DataAnalytics
#Automation & Workflow Integration
Our mission is simple to help brands sell smarter, scale faster, and deliver seamless digital shopping experiences. We combine modern technology stacks (#React, NodeJS, Next.js, Python) with deep ecommerce expertise to build robust, scalable, and future-ready solutions.
Let our #webdevelopers turn your vision into a powerful online store built for the future.
-------------
: https://www.kpis.in/ecomme...
: infokpis.in
+91-6350359218
-------------
#EcommerceWebDevelopment #EcommerceDevelopment #DigitalTransformation #AIChatbots #WebDevelopment #EcommerceWebsiteDevelopment #WebsiteDevelopment #digitalmarketing #HireeCommerceWebsiteDevelopers #gojekclone #AppDevelopment #ITCompany #KPISPvtLtd #Jaipur
15 days ago
(E)
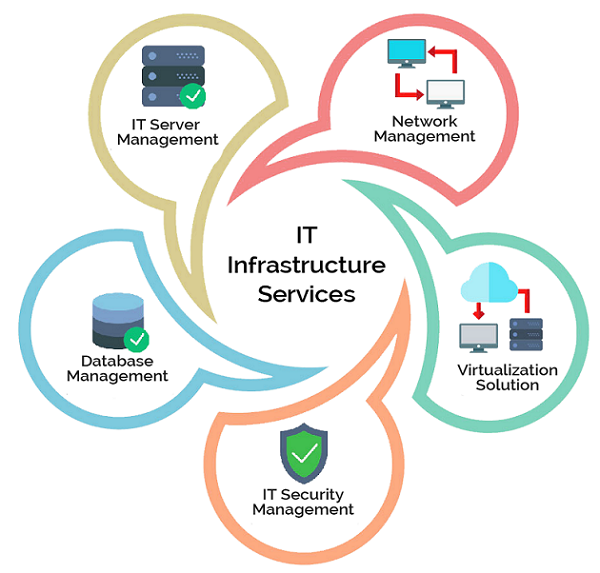
Comprehensive Guide to IT Infrastructure Services: Building a Robust Digital Foundation
Understanding IT Infrastructure Services
IT infrastructure services encompass the essential hardware, software, network resources, and facilities required to develop, manage, and support an organization’s IT environment. These services include data centers, servers, storage systems, networking equipment, and cloud resources. Their primary goal is to ensure seamless connectivity, data processing, and storage, enabling businesses to operate efficiently. Effective IT infrastructure provides a reliable foundation that supports business applications, enhances security, and facilitates innovation. As technology evolves, organizations increasingly rely on a mix of on-premises and cloud-based infrastructure to meet dynamic demands. Proper management of these services ensures high availability, scalability, and security, which are critical for maintaining competitive advantage in today's digital landscape. Investing in robust IT infrastructure is fundamental for digital transformation and long-term success.
Key Components of IT Infrastructure Services
The core components of IT infrastructure services include physical hardware, network systems, data storage solutions, and cloud platforms. Physical hardware involves servers, computers, and networking devices like routers and switches that form the backbone of IT operations. Network systems connect all hardware and enable communication within and outside the organization, ensuring data flows smoothly. Data storage solutions such as SANs and NAS enable organizations to manage vast amounts of information securely. Cloud platforms like AWS, Azure, and Google Cloud provide scalable, flexible resources that adapt to business needs.
Source: https://www.marketresearch...
Understanding IT Infrastructure Services
IT infrastructure services encompass the essential hardware, software, network resources, and facilities required to develop, manage, and support an organization’s IT environment. These services include data centers, servers, storage systems, networking equipment, and cloud resources. Their primary goal is to ensure seamless connectivity, data processing, and storage, enabling businesses to operate efficiently. Effective IT infrastructure provides a reliable foundation that supports business applications, enhances security, and facilitates innovation. As technology evolves, organizations increasingly rely on a mix of on-premises and cloud-based infrastructure to meet dynamic demands. Proper management of these services ensures high availability, scalability, and security, which are critical for maintaining competitive advantage in today's digital landscape. Investing in robust IT infrastructure is fundamental for digital transformation and long-term success.
Key Components of IT Infrastructure Services
The core components of IT infrastructure services include physical hardware, network systems, data storage solutions, and cloud platforms. Physical hardware involves servers, computers, and networking devices like routers and switches that form the backbone of IT operations. Network systems connect all hardware and enable communication within and outside the organization, ensuring data flows smoothly. Data storage solutions such as SANs and NAS enable organizations to manage vast amounts of information securely. Cloud platforms like AWS, Azure, and Google Cloud provide scalable, flexible resources that adapt to business needs.
Source: https://www.marketresearch...
17 days ago
Scaling a handyman business is easier with the right technology. Apps bring transparency, automation, and quick communication with clients. Modern tools are redefining how handyman services grow in the on-demand world.
Learn more: https://www.spotnrides.com...
Whatsapp: https://wa.me/919600695595
#HandymanApp #HandymanBusiness #OnDemandHandyman #HandymanServices #ServiceAppDevelopment #HomeRepairApp #SpotnRides #HandymanStartup #MobileAppSolutions #HandymanBookingApp #UberforHomeservices #HomeServicesApp
Learn more: https://www.spotnrides.com...
Whatsapp: https://wa.me/919600695595
#HandymanApp #HandymanBusiness #OnDemandHandyman #HandymanServices #ServiceAppDevelopment #HomeRepairApp #SpotnRides #HandymanStartup #MobileAppSolutions #HandymanBookingApp #UberforHomeservices #HomeServicesApp
1 month ago
https://ubuntusafa.com/pos...
Which Sectors — Defense, Clean Energy, and Digital Electronics — Depend Most on Rare Earths?
Rare earth elements (REEs) are the invisible threads that weave together much of our 21st-century technology. Though their presence is often measured in grams or even milligrams, their absence would render much of the modern world impossible — from smartphones and satellites to stealth aircraft and electric vehicles. These 17 metallic elements, including neodymium,
Which Sectors — Defense, Clean Energy, and Digital Electronics — Depend Most on Rare Earths?
Rare earth elements (REEs) are the invisible threads that weave together much of our 21st-century technology. Though their presence is often measured in grams or even milligrams, their absence would render much of the modern world impossible — from smartphones and satellites to stealth aircraft and electric vehicles. These 17 metallic elements, including neodymium,

1 month ago
https://ubuntusafa.com/pos...
How can African states protect infant industries while still engaging in global trade? Europeans and American industries and countries now knows what they lost.
One of the greatest challenges facing African economies is how to nurture infant industries—new or emerging sectors that lack the economies of scale, experience, and technology to compete against established global giants. Historically, many now-developed countries, from the United States to Germany to South Korea, used protectionist measures to give their domestic
How can African states protect infant industries while still engaging in global trade? Europeans and American industries and countries now knows what they lost.
One of the greatest challenges facing African economies is how to nurture infant industries—new or emerging sectors that lack the economies of scale, experience, and technology to compete against established global giants. Historically, many now-developed countries, from the United States to Germany to South Korea, used protectionist measures to give their domestic
1 month ago
In the marine and outdoor industry, materials that can withstand constant exposure to water, sun, and abrasion are essential. MSD stands out as a trusted manufacturer of PVC Inflatable Boat Fabric , offering products that combine superior strength, flexibility, and long-term reliability for all types of inflatable boats.
MSD’s PVC Inflatable Boat Fabric is designed with advanced coating and lamination technology to achieve excellent airtightness and weather resistance. Each roll of fabric undergoes rigorous testing to ensure that it performs consistently under high pressure and extreme environmental conditions. From leisure rafts to professional rescue boats, MSD’s materials deliver outstanding stability and protection.
What makes MSD unique is its commitment to research and continuous improvement. The company’s R&D department works closely with global partners to develop materials that balance lightweight design with robust durability. The PVC layers are engineered for exceptional adhesion, tear resistance, and UV protection—ensuring that every inflatable boat remains strong and dependable in any environment.
MSD also provides extensive customization options. Customers can select different fabric thicknesses, colors, and surface textures to fit their design or brand identity. This flexibility allows OEM and ODM clients to create products that match their target markets while maintaining superior performance standards.
Beyond performance, MSD places a strong emphasis on sustainability. Its manufacturing process uses eco-friendly PVC compounds and adheres to environmentally responsible practices. By reducing waste and optimizing energy efficiency, MSD helps clients align with modern green production values.
The versatility of MSD’s PVC Inflatable Boat Fabric makes it a preferred choice for marine manufacturers worldwide. It is suitable for a wide range of applications, including sports boats, rescue inflatables, and high-end leisure equipment. The mate
MSD’s PVC Inflatable Boat Fabric is designed with advanced coating and lamination technology to achieve excellent airtightness and weather resistance. Each roll of fabric undergoes rigorous testing to ensure that it performs consistently under high pressure and extreme environmental conditions. From leisure rafts to professional rescue boats, MSD’s materials deliver outstanding stability and protection.
What makes MSD unique is its commitment to research and continuous improvement. The company’s R&D department works closely with global partners to develop materials that balance lightweight design with robust durability. The PVC layers are engineered for exceptional adhesion, tear resistance, and UV protection—ensuring that every inflatable boat remains strong and dependable in any environment.
MSD also provides extensive customization options. Customers can select different fabric thicknesses, colors, and surface textures to fit their design or brand identity. This flexibility allows OEM and ODM clients to create products that match their target markets while maintaining superior performance standards.
Beyond performance, MSD places a strong emphasis on sustainability. Its manufacturing process uses eco-friendly PVC compounds and adheres to environmentally responsible practices. By reducing waste and optimizing energy efficiency, MSD helps clients align with modern green production values.
The versatility of MSD’s PVC Inflatable Boat Fabric makes it a preferred choice for marine manufacturers worldwide. It is suitable for a wide range of applications, including sports boats, rescue inflatables, and high-end leisure equipment. The mate
1 month ago
In the marine and outdoor industry, materials that can withstand constant exposure to water, sun, and abrasion are essential. MSD stands out as a trusted manufacturer of PVC Inflatable Boat Fabric , offering products that combine superior strength, flexibility, and long-term reliability for all types of inflatable boats.
MSD’s PVC Inflatable Boat Fabric is designed with advanced coating and lamination technology to achieve excellent airtightness and weather resistance. Each roll of fabric undergoes rigorous testing to ensure that it performs consistently under high pressure and extreme environmental conditions. From leisure rafts to professional rescue boats, MSD’s materials deliver outstanding stability and protection.
What makes MSD unique is its commitment to research and continuous improvement. The company’s R&D department works closely with global partners to develop materials that balance lightweight design with robust durability. The PVC layers are engineered for exceptional adhesion, tear resistance, and UV protection—ensuring that every inflatable boat remains strong and dependable in any environment.
MSD also provides extensive customization options. Customers can select different fabric thicknesses, colors, and surface textures to fit their design or brand identity. This flexibility allows OEM and ODM clients to create products that match their target markets while maintaining superior performance standards.
Beyond performance, MSD places a strong emphasis on sustainability. Its manufacturing process uses eco-friendly PVC compounds and adheres to environmentally responsible practices. By reducing waste and optimizing energy efficiency, MSD helps clients align with modern green production values.
The versatility of MSD’s PVC Inflatable Boat Fabric makes it a preferred choice for marine manufacturers worldwide. It is suitable for a wide range of applications, including sports boats, rescue inflatables, and high-end leisure equipment. The mate
MSD’s PVC Inflatable Boat Fabric is designed with advanced coating and lamination technology to achieve excellent airtightness and weather resistance. Each roll of fabric undergoes rigorous testing to ensure that it performs consistently under high pressure and extreme environmental conditions. From leisure rafts to professional rescue boats, MSD’s materials deliver outstanding stability and protection.
What makes MSD unique is its commitment to research and continuous improvement. The company’s R&D department works closely with global partners to develop materials that balance lightweight design with robust durability. The PVC layers are engineered for exceptional adhesion, tear resistance, and UV protection—ensuring that every inflatable boat remains strong and dependable in any environment.
MSD also provides extensive customization options. Customers can select different fabric thicknesses, colors, and surface textures to fit their design or brand identity. This flexibility allows OEM and ODM clients to create products that match their target markets while maintaining superior performance standards.
Beyond performance, MSD places a strong emphasis on sustainability. Its manufacturing process uses eco-friendly PVC compounds and adheres to environmentally responsible practices. By reducing waste and optimizing energy efficiency, MSD helps clients align with modern green production values.
The versatility of MSD’s PVC Inflatable Boat Fabric makes it a preferred choice for marine manufacturers worldwide. It is suitable for a wide range of applications, including sports boats, rescue inflatables, and high-end leisure equipment. The mate
2 months ago
Markets move in milliseconds—are you keeping up? Our High-Frequency Trading (HFT) Bot Development ensures you never miss an opportunity. We build lightning-fast, intelligent bots that execute thousands of trades per second with ultra-low latency, smart algorithms, risk management, and 24/7 support. Whether you’re a hedge fund, exchange, or active trader, we deliver tomorrow’s trading technology today. 🚀
Book your free call: https://www.beleaftechnolo...
Book your free call: https://www.beleaftechnolo...
2 months ago
What is an AliExpress Clone? A Guide for Multi-Vendor Business
The eCommerce industry has witnessed immersive growth, fueled by new technology innovations and evolving user demands.
AliExpress Clone is one of the top on-demand platforms with a scalable architecture, unique layouts, and standard vendor management. It opens a new opportunity for startups to stand out in a competitive marketplace.
This blog provides a complete guide to building a multi-vendor app using an AliExpress clone script. We covered its essential features, development steps, and latest trends.
Dive in.
Aliexpress Clone: An Introduction
Don’t you know what an AliExpress clone is? Here’s a short overview of it. Let’s check in.
An AliExpress clone is a ready-made solution inspired by the original AliExpress business model, designed with its core functionalities intact. This connects every single user who wants to order products through an online medium. They can compare prices across multiple vendors and finally buy a product from a preferred store. It increases user convenience and satisfaction.
This eCommerce clone script streamlines the complete end-to-end purchasing process with advanced features, including user registration, multiple delivery addresses, shipment tracking, and secure payments.
Partner With Trioangle and Start Today!
Obviously, you are at the right place to start and implement your multi-vendor marketplace idea.
Trioangle's AliExpress Clone Script can help you turn your idea into a robust and revenue-generating eCommerce platform.
Connect with our experts to acknowledge business goals and craft solutions that meet your target audience's needs.
Subscribe now!
https://www.trioangle.com/...
#AliExpressClone #AliExpressCloneScript #AliExpressLikeApp #MultiVendorEcommerce #MarketplaceSoftware #EcommerceScript #ReadymadeEcommerce #B2BMarketplace #OnlineMarketplace
The eCommerce industry has witnessed immersive growth, fueled by new technology innovations and evolving user demands.
AliExpress Clone is one of the top on-demand platforms with a scalable architecture, unique layouts, and standard vendor management. It opens a new opportunity for startups to stand out in a competitive marketplace.
This blog provides a complete guide to building a multi-vendor app using an AliExpress clone script. We covered its essential features, development steps, and latest trends.
Dive in.
Aliexpress Clone: An Introduction
Don’t you know what an AliExpress clone is? Here’s a short overview of it. Let’s check in.
An AliExpress clone is a ready-made solution inspired by the original AliExpress business model, designed with its core functionalities intact. This connects every single user who wants to order products through an online medium. They can compare prices across multiple vendors and finally buy a product from a preferred store. It increases user convenience and satisfaction.
This eCommerce clone script streamlines the complete end-to-end purchasing process with advanced features, including user registration, multiple delivery addresses, shipment tracking, and secure payments.
Partner With Trioangle and Start Today!
Obviously, you are at the right place to start and implement your multi-vendor marketplace idea.
Trioangle's AliExpress Clone Script can help you turn your idea into a robust and revenue-generating eCommerce platform.
Connect with our experts to acknowledge business goals and craft solutions that meet your target audience's needs.
Subscribe now!
https://www.trioangle.com/...
#AliExpressClone #AliExpressCloneScript #AliExpressLikeApp #MultiVendorEcommerce #MarketplaceSoftware #EcommerceScript #ReadymadeEcommerce #B2BMarketplace #OnlineMarketplace
3 months ago
(E)
How to Choose the Right Cab Booking Software? A Quick Guide
The taxi sector is flourishing like never before, allowing businesses to expand, develop, and capture new market possibilities.
Have you ever thought about how the cab booking software can transform your business? It helps you streamline bookings, optimize driver management, and enhance customer satisfaction. Don’t get stressed.
This brief blog outlines critical factors to consider when selecting cab booking software that drives growth and profitability.
Get started now!
What is Cab Booking Software?
A cab booking software is a built-in technology solution with core functionalities designed to power an on-demand mobility app. It facilitates urban users to book a cab or taxi ride with a single tap using mobile or web platforms.
The global taxi market is expected to reach $592.96 billion by 2033, up from $274.6 billion in 2024, boasting a CAGR of 8.93% from 2025 to 2033.
In a Nutshell
Hurray! We’ve reached the end. This is the moment to build your online cab booking app and transform your taxi service into a smart and highly profitable venture.
The right cab booking software can accelerate your launch, streamline operations, and stand out in a rapidly expanding industry.
Don't wait, ride the wave of innovation today!
https://www.trioangle.com/...
#TaxiSoftwareUSA #USATaxiTech #DispatchSoftwareUK #UKTransportTech #TaxiAppCanada #RideshareAU #TaxiSoftwareGermany #FleetManagementSoftware #RideshareTechnology #taxidispatchsoftware
The taxi sector is flourishing like never before, allowing businesses to expand, develop, and capture new market possibilities.
Have you ever thought about how the cab booking software can transform your business? It helps you streamline bookings, optimize driver management, and enhance customer satisfaction. Don’t get stressed.
This brief blog outlines critical factors to consider when selecting cab booking software that drives growth and profitability.
Get started now!
What is Cab Booking Software?
A cab booking software is a built-in technology solution with core functionalities designed to power an on-demand mobility app. It facilitates urban users to book a cab or taxi ride with a single tap using mobile or web platforms.
The global taxi market is expected to reach $592.96 billion by 2033, up from $274.6 billion in 2024, boasting a CAGR of 8.93% from 2025 to 2033.
In a Nutshell
Hurray! We’ve reached the end. This is the moment to build your online cab booking app and transform your taxi service into a smart and highly profitable venture.
The right cab booking software can accelerate your launch, streamline operations, and stand out in a rapidly expanding industry.
Don't wait, ride the wave of innovation today!
https://www.trioangle.com/...
#TaxiSoftwareUSA #USATaxiTech #DispatchSoftwareUK #UKTransportTech #TaxiAppCanada #RideshareAU #TaxiSoftwareGermany #FleetManagementSoftware #RideshareTechnology #taxidispatchsoftware
3 months ago
Did You Know “How Africa’s Gold Still Fuels the Global Economy”
How Africa’s Gold Still Fuels the Global Economy
Africa has been known as the “Gold Continent” for centuries — from the legendary wealth of ancient empires like Ghana, Mali, and Songhai to today’s massive gold mining industries.
Yet, the story of African gold is not just about riches buried underground; it’s about how this precious metal continues to shape global markets, economies, and power dynamics today.
Africa’s Rich Gold Legacy-
For centuries, African gold attracted traders, explorers, and conquerors. The Mali Empire’s Mansa Musa famously showcased his empire’s gold wealth on his pilgrimage to Mecca in the 14th century, placing West Africa on the world map as a source of immense wealth. Gold fueled the rise of kingdoms, financed trade routes, and symbolized power.
Modern Gold Production in Africa
Today, Africa remains a major gold producer. Countries like:
South Africa — once the world’s largest producer, with famous mines like Witwatersrand
Ghana — “the Gold Coast,” rich in both alluvial and deep mines
Mali — home to large-scale gold mining projects
Tanzania, Burkina Faso, Zimbabwe, and others — significant gold producers
Gold mining is a major source of revenue, employment, and foreign exchange for these nations.
How African Gold Fuels the Global Economy
Global Supply Chains
African gold enters complex global supply chains, eventually becoming:
Jewelry worn worldwide
Electronics and smartphones (gold is an excellent conductor used in circuits)
Financial reserves and investment assets
Foreign Investment and Control
Much of Africa’s gold mining industry is operated or financed by multinational corporations headquartered in Europe, North America, and increasingly Asia. These companies:
Extract vast quantities of gold
Export most of it for refining and manufacturing abroad
Repatriate profits, often with limited benefit to local economies
Economic Impact on African Nations
Gold mining can boost economies through taxes and jobs, but challenges remain:
-Environmental degradation and social displacement
-Revenue leakages due to corruption and opaque contracts
-Unequal wealth distribution leaving many mining communities impoverished
-Gold’s Role in Financial Markets
Gold from Africa contributes to global reserves held by central banks and private investors, impacting:
-Currency stability and monetary policy
-Wealth preservation in times of economic uncertainty
The Challenges and Opportunities-
-Transparency and Fair Trade: Efforts like the Kimberley Process for diamonds have parallels in gold to reduce illegal mining and smuggling.
-Sustainable Mining Practices: Balancing economic benefits with environmental protection is crucial.
-Local Empowerment: Increasing African ownership and control over gold resources can boost development.
-Technology and Innovation: New mining technologies and better governance could improve outcomes.
Conclusion-
Africa’s gold is more than a mineral resource — it’s a link between continents, economies, and histories. While it continues to fuel the global economy, the challenge remains to ensure that the wealth generated benefits Africans themselves, helping to build sustainable prosperity across the continent.
Quote for Thought-
“Africa’s gold shines on the world stage, but its brightest future is in African hands.”
— Voices for Change
How Africa’s Gold Still Fuels the Global Economy
Africa has been known as the “Gold Continent” for centuries — from the legendary wealth of ancient empires like Ghana, Mali, and Songhai to today’s massive gold mining industries.
Yet, the story of African gold is not just about riches buried underground; it’s about how this precious metal continues to shape global markets, economies, and power dynamics today.
Africa’s Rich Gold Legacy-
For centuries, African gold attracted traders, explorers, and conquerors. The Mali Empire’s Mansa Musa famously showcased his empire’s gold wealth on his pilgrimage to Mecca in the 14th century, placing West Africa on the world map as a source of immense wealth. Gold fueled the rise of kingdoms, financed trade routes, and symbolized power.
Modern Gold Production in Africa
Today, Africa remains a major gold producer. Countries like:
South Africa — once the world’s largest producer, with famous mines like Witwatersrand
Ghana — “the Gold Coast,” rich in both alluvial and deep mines
Mali — home to large-scale gold mining projects
Tanzania, Burkina Faso, Zimbabwe, and others — significant gold producers
Gold mining is a major source of revenue, employment, and foreign exchange for these nations.
How African Gold Fuels the Global Economy
Global Supply Chains
African gold enters complex global supply chains, eventually becoming:
Jewelry worn worldwide
Electronics and smartphones (gold is an excellent conductor used in circuits)
Financial reserves and investment assets
Foreign Investment and Control
Much of Africa’s gold mining industry is operated or financed by multinational corporations headquartered in Europe, North America, and increasingly Asia. These companies:
Extract vast quantities of gold
Export most of it for refining and manufacturing abroad
Repatriate profits, often with limited benefit to local economies
Economic Impact on African Nations
Gold mining can boost economies through taxes and jobs, but challenges remain:
-Environmental degradation and social displacement
-Revenue leakages due to corruption and opaque contracts
-Unequal wealth distribution leaving many mining communities impoverished
-Gold’s Role in Financial Markets
Gold from Africa contributes to global reserves held by central banks and private investors, impacting:
-Currency stability and monetary policy
-Wealth preservation in times of economic uncertainty
The Challenges and Opportunities-
-Transparency and Fair Trade: Efforts like the Kimberley Process for diamonds have parallels in gold to reduce illegal mining and smuggling.
-Sustainable Mining Practices: Balancing economic benefits with environmental protection is crucial.
-Local Empowerment: Increasing African ownership and control over gold resources can boost development.
-Technology and Innovation: New mining technologies and better governance could improve outcomes.
Conclusion-
Africa’s gold is more than a mineral resource — it’s a link between continents, economies, and histories. While it continues to fuel the global economy, the challenge remains to ensure that the wealth generated benefits Africans themselves, helping to build sustainable prosperity across the continent.
Quote for Thought-
“Africa’s gold shines on the world stage, but its brightest future is in African hands.”
— Voices for Change
3 months ago
Focus on Cyber Warfare and Fraud-
How do multinational companies protect themselves from state-sponsored cyber espionage?
Multinational companies face a unique and elevated threat from state-sponsored cyber espionage due to their vast intellectual property, critical infrastructure dependencies, global reach, and often, involvement in strategic industries.
Protecting themselves requires a comprehensive, multi-layered, and continuously evolving cybersecurity strategy that goes beyond standard defenses.
Here are the key ways multinational companies protect themselves:
1. Robust Foundational Cybersecurity:
Before anything else, strong basic cybersecurity hygiene is paramount. State-sponsored actors often exploit common weaknesses.
Patch Management: Aggressive and immediate patching of all software, operating systems, and network devices, especially for known exploited vulnerabilities (N-day exploits). This includes out-of-band updates.
Strong Access Controls:
Multi-Factor Authentication (MFA): Mandatory MFA for all employees, especially for remote access, cloud services, and privileged accounts. Hardware tokens are often preferred for highly sensitive access.
Principle of Least Privilege (PoLP): Granting users and systems only the minimum access rights necessary to perform their functions.
Privileged Access Management (PAM): Solutions to secure, manage, and monitor privileged accounts.
Network Segmentation: Dividing the network into isolated zones to limit lateral movement if a part of the network is compromised. Critical data and operational technology (OT) networks should be completely segregated.
Endpoint Detection and Response (EDR) / Extended Detection and Response (XDR): Deploying advanced solutions to continuously monitor, detect, and respond to threats on endpoints (laptops, servers) and across the broader IT ecosystem.
Data Encryption: Encrypting data at rest and in transit, especially sensitive intellectual property and customer data.
2. Advanced Threat Detection and Intelligence:
State-sponsored groups are stealthy; proactive detection is crucial.
Behavioral Analytics & Anomaly Detection: Implementing tools that use AI and machine learning to establish baselines of "normal" user and network behavior, and then flag deviations that could indicate a compromise.
Threat Hunting Teams (Red Teaming/Blue Teaming): Employing internal or external teams to proactively search for hidden threats within the network, rather than just reacting to alerts. This includes simulating attacks (red teaming) to test defenses.
Comprehensive Logging and Monitoring: Centralized collection and analysis of logs from all systems, applications, and network devices to identify suspicious activity.
Threat Intelligence Integration: Subscribing to and actively consuming high-quality threat intelligence feeds from government agencies (like CISA, NCSC), cybersecurity vendors, and industry-specific ISACs (Information Sharing and Analysis Centers). This intelligence provides insights into the latest TTPs of state-sponsored actors, enabling proactive defense.
Dark Web Monitoring: Monitoring for mentions of the company, its employees, or stolen data on underground forums.
3. Supply Chain and Third-Party Risk Management:
State-sponsored actors often target weaker links in the supply chain.
Thorough Vendor Due Diligence: Rigorous cybersecurity assessments of all third-party vendors, suppliers, and partners, especially those with access to sensitive systems or data. This includes contractual security requirements.
Continuous Monitoring of Third-Parties: Not just a one-time assessment, but ongoing monitoring of third-party security postures and potential vulnerabilities in their products or services.
Supply Chain Visibility: Mapping the entire digital supply chain to understand dependencies and identify potential weak points.
Software Bill of Materials (SBOMs): Requiring SBOMs from software vendors to understand all components (including open-source) in their products and track potential vulnerabilities.
4. Human Element and Insider Threat Mitigation:
Employees are often the primary target for initial access.
Security Awareness Training: Regular, up-to-date, and engaging training for all employees on phishing, social engineering tactics, safe Browse, and reporting suspicious activity. Tailored training for executives and high-value targets (HVT) is essential.
Phishing Simulations: Conducting frequent and varied phishing simulations to test employee vigilance and reinforce training.
Insider Threat Programs: Establishing programs to detect and mitigate risks from malicious or unwitting insiders, including monitoring user behavior and data access patterns.
5. Incident Response and Resilience:
Assuming compromise is inevitable, preparation is key.
Well-Defined Incident Response Plan: A detailed, tested, and regularly updated plan for how to detect, contain, eradicate, and recover from a state-sponsored cyberattack. This includes clear roles, responsibilities, and communication protocols.
Secure Backups: Regular, encrypted, and offline backups of critical data and systems to ensure recovery from destructive attacks.
Business Continuity and Disaster Recovery (BCDR) Plans: Comprehensive plans to maintain essential business operations even during and after a significant cyber incident.
Post-Incident Analysis: Conducting thorough post-mortem analyses after any incident to learn lessons and improve defenses.
6. Collaboration with Government and Intelligence Agencies:
Governments often have unique insights into nation-state threats.
Information Sharing: Actively participating in information-sharing initiatives with government cybersecurity agencies (e.g., CISA in the US, NCSC in the UK), industry-specific ISACs, and threat intelligence alliances.
Trusted Relationships: Building direct, trusted relationships with relevant government cyber defense and intelligence agencies to facilitate rapid two-way sharing of classified or sensitive threat intelligence.
Reporting Incidents: Urgently reporting suspected state-sponsored cyberattacks to relevant government authorities to aid in national defense and enable coordinated responses.
By implementing these advanced and comprehensive measures, multinational companies can significantly enhance their resilience against state-sponsored cyber espionage, protect their valuable assets, and maintain their competitive edge in a contested digital landscape.
How do multinational companies protect themselves from state-sponsored cyber espionage?
Multinational companies face a unique and elevated threat from state-sponsored cyber espionage due to their vast intellectual property, critical infrastructure dependencies, global reach, and often, involvement in strategic industries.
Protecting themselves requires a comprehensive, multi-layered, and continuously evolving cybersecurity strategy that goes beyond standard defenses.
Here are the key ways multinational companies protect themselves:
1. Robust Foundational Cybersecurity:
Before anything else, strong basic cybersecurity hygiene is paramount. State-sponsored actors often exploit common weaknesses.
Patch Management: Aggressive and immediate patching of all software, operating systems, and network devices, especially for known exploited vulnerabilities (N-day exploits). This includes out-of-band updates.
Strong Access Controls:
Multi-Factor Authentication (MFA): Mandatory MFA for all employees, especially for remote access, cloud services, and privileged accounts. Hardware tokens are often preferred for highly sensitive access.
Principle of Least Privilege (PoLP): Granting users and systems only the minimum access rights necessary to perform their functions.
Privileged Access Management (PAM): Solutions to secure, manage, and monitor privileged accounts.
Network Segmentation: Dividing the network into isolated zones to limit lateral movement if a part of the network is compromised. Critical data and operational technology (OT) networks should be completely segregated.
Endpoint Detection and Response (EDR) / Extended Detection and Response (XDR): Deploying advanced solutions to continuously monitor, detect, and respond to threats on endpoints (laptops, servers) and across the broader IT ecosystem.
Data Encryption: Encrypting data at rest and in transit, especially sensitive intellectual property and customer data.
2. Advanced Threat Detection and Intelligence:
State-sponsored groups are stealthy; proactive detection is crucial.
Behavioral Analytics & Anomaly Detection: Implementing tools that use AI and machine learning to establish baselines of "normal" user and network behavior, and then flag deviations that could indicate a compromise.
Threat Hunting Teams (Red Teaming/Blue Teaming): Employing internal or external teams to proactively search for hidden threats within the network, rather than just reacting to alerts. This includes simulating attacks (red teaming) to test defenses.
Comprehensive Logging and Monitoring: Centralized collection and analysis of logs from all systems, applications, and network devices to identify suspicious activity.
Threat Intelligence Integration: Subscribing to and actively consuming high-quality threat intelligence feeds from government agencies (like CISA, NCSC), cybersecurity vendors, and industry-specific ISACs (Information Sharing and Analysis Centers). This intelligence provides insights into the latest TTPs of state-sponsored actors, enabling proactive defense.
Dark Web Monitoring: Monitoring for mentions of the company, its employees, or stolen data on underground forums.
3. Supply Chain and Third-Party Risk Management:
State-sponsored actors often target weaker links in the supply chain.
Thorough Vendor Due Diligence: Rigorous cybersecurity assessments of all third-party vendors, suppliers, and partners, especially those with access to sensitive systems or data. This includes contractual security requirements.
Continuous Monitoring of Third-Parties: Not just a one-time assessment, but ongoing monitoring of third-party security postures and potential vulnerabilities in their products or services.
Supply Chain Visibility: Mapping the entire digital supply chain to understand dependencies and identify potential weak points.
Software Bill of Materials (SBOMs): Requiring SBOMs from software vendors to understand all components (including open-source) in their products and track potential vulnerabilities.
4. Human Element and Insider Threat Mitigation:
Employees are often the primary target for initial access.
Security Awareness Training: Regular, up-to-date, and engaging training for all employees on phishing, social engineering tactics, safe Browse, and reporting suspicious activity. Tailored training for executives and high-value targets (HVT) is essential.
Phishing Simulations: Conducting frequent and varied phishing simulations to test employee vigilance and reinforce training.
Insider Threat Programs: Establishing programs to detect and mitigate risks from malicious or unwitting insiders, including monitoring user behavior and data access patterns.
5. Incident Response and Resilience:
Assuming compromise is inevitable, preparation is key.
Well-Defined Incident Response Plan: A detailed, tested, and regularly updated plan for how to detect, contain, eradicate, and recover from a state-sponsored cyberattack. This includes clear roles, responsibilities, and communication protocols.
Secure Backups: Regular, encrypted, and offline backups of critical data and systems to ensure recovery from destructive attacks.
Business Continuity and Disaster Recovery (BCDR) Plans: Comprehensive plans to maintain essential business operations even during and after a significant cyber incident.
Post-Incident Analysis: Conducting thorough post-mortem analyses after any incident to learn lessons and improve defenses.
6. Collaboration with Government and Intelligence Agencies:
Governments often have unique insights into nation-state threats.
Information Sharing: Actively participating in information-sharing initiatives with government cybersecurity agencies (e.g., CISA in the US, NCSC in the UK), industry-specific ISACs, and threat intelligence alliances.
Trusted Relationships: Building direct, trusted relationships with relevant government cyber defense and intelligence agencies to facilitate rapid two-way sharing of classified or sensitive threat intelligence.
Reporting Incidents: Urgently reporting suspected state-sponsored cyberattacks to relevant government authorities to aid in national defense and enable coordinated responses.
By implementing these advanced and comprehensive measures, multinational companies can significantly enhance their resilience against state-sponsored cyber espionage, protect their valuable assets, and maintain their competitive edge in a contested digital landscape.
3 months ago
Focus Nigeria-
How can public hospitals be improved to serve the poor better?
Improving public hospitals to better serve the poor requires a comprehensive strategy that addresses the core issues of funding, infrastructure, human resources, efficiency, and patient-centered care.
For a country like Nigeria, where the majority of the population relies on public healthcare and poverty is widespread, these improvements are vital for national development and social equity.
Here's a detailed approach:
I. Increased and Transparent Funding:
Allocate More Budgetary Resources: Governments at federal, state, and local levels must significantly increase the percentage of their budgets allocated to healthcare, aiming to meet or exceed international recommendations (e.g., the Abuja Declaration's 15%).
Targeted Funding for the Poor: Earmark specific funds for initiatives that directly benefit low-income patients, such as subsidized or free essential services, medications, and diagnostic tests for those who cannot afford them.
Strengthen Health Insurance Schemes (e.g., NHIS):
Expand Coverage: Aggressively expand the reach of the National Health Insurance Scheme (NHIS) to cover a larger portion of the informal sector and vulnerable populations, potentially through community-based health insurance models or state-led initiatives.
Subsidies for the Poor: Implement government subsidies or premium support for low-income households to ensure they can afford health insurance contributions.
Streamline Processes: Simplify the enrollment and claims processes for the poor to reduce bureaucratic hurdles.
Combat Corruption and Ensure Accountability:
Implement robust financial management systems, regular audits, and strict anti-corruption measures within public hospitals to prevent embezzlement and ensure funds are used for their intended purpose.
Introduce performance-based funding where hospitals receive additional funds based on patient outcomes, efficiency, and satisfaction.
II. Infrastructure and Equipment Upgrade:
Renovation and Modernization: Invest in systematic renovation and modernization of existing public hospital buildings to create clean, safe, and dignified environments.
Equip with Modern Technology: Provide essential, functional diagnostic and treatment equipment (e.g., X-ray machines, ultrasound scanners, laboratory equipment, essential surgical tools). Ensure maintenance contracts and availability of spare parts.
Reliable Utilities: Guarantee constant access to clean water, reliable electricity (invest in solar power as a sustainable backup), and proper waste management systems in all public hospitals.
Basic Amenities: Ensure availability of basic amenities like clean restrooms (separate for male/female), comfortable waiting areas, and proper ventilation.
III. Human Resources Development and Motivation:
Adequate Staffing: Recruit and retain a sufficient number of qualified doctors, nurses, pharmacists, laboratory scientists, and other support staff to reduce workload and improve patient-to-staff ratios.
Competitive Remuneration and Welfare: Offer attractive and timely salaries, allowances, and a comprehensive benefits package (including health insurance and pensions) to stem the brain drain and motivate staff.
Continuous Professional Development (CPD): Provide regular training opportunities to upgrade skills, keep staff abreast of new medical advancements, and improve patient communication.
Ethical Conduct and Empathy Training: Conduct mandatory training on medical ethics, patient rights, empathy, and respectful communication, particularly towards low-income patients who may feel disempowered.
Performance Incentives: Introduce performance-based incentives for staff tied to patient satisfaction, quality of care, and efficiency, rather than just volume.
Safety and Security: Enhance security measures within hospital premises to protect staff from harassment or violence.
IV. Operational Efficiency and Patient-Centered Care:
Streamline Processes: Implement efficient patient flow systems, from registration to consultation, diagnosis, and treatment, to reduce long waiting times and bureaucratic bottlenecks.
Digitalization (Electronic Health Records - EHR):
Implement EHR systems to improve record-keeping, reduce errors, enhance data sharing among departments, and enable better patient tracking.
Digitalize appointment scheduling and billing to minimize human interface and reduce opportunities for corruption.
Focus on Primary Healthcare (PHC): Strengthen the referral system from PHC centers to secondary and tertiary public hospitals. Well-equipped and staffed PHCs can manage common ailments, reducing the burden on hospitals and making basic care accessible at the community level.
Culturally Sensitive Care: Train staff to understand and respect the cultural beliefs and practices of diverse patient populations, which can influence health-seeking behaviors.
Patient Feedback Mechanisms: Establish accessible and confidential channels for patients to provide feedback, lodge complaints, and make suggestions for improvement. Use this feedback to drive continuous improvement.
Transparency and Information: Clearly display service costs (if any), patients' rights, and grievance procedures. Provide clear information about treatment plans in a language patients understand.
V. Innovative Service Delivery Models:
Mobile Clinics and Outreach Programs: Implement mobile health clinics that travel to underserved rural communities, providing basic diagnostic, preventive, and primary care services, as well as health education.
Telemedicine: Leverage telemedicine for remote consultations, specialist opinions, and follow-ups, particularly for patients in remote areas where specialists are scarce. This can reduce travel costs and time for patients.
Community Health Workers (CHWs): Train and deploy CHWs from within the communities to act as a link between the community and the health system, providing basic health education, screening, and facilitating referrals.
Partnerships with NGOs and CSOs: Collaborate with non-governmental organizations and civil society organizations that have experience in delivering healthcare to underserved populations.
By implementing these strategies, public hospitals can move towards becoming trusted, accessible, and high-quality healthcare providers for all, especially the most vulnerable members of society.
How can public hospitals be improved to serve the poor better?
Improving public hospitals to better serve the poor requires a comprehensive strategy that addresses the core issues of funding, infrastructure, human resources, efficiency, and patient-centered care.
For a country like Nigeria, where the majority of the population relies on public healthcare and poverty is widespread, these improvements are vital for national development and social equity.
Here's a detailed approach:
I. Increased and Transparent Funding:
Allocate More Budgetary Resources: Governments at federal, state, and local levels must significantly increase the percentage of their budgets allocated to healthcare, aiming to meet or exceed international recommendations (e.g., the Abuja Declaration's 15%).
Targeted Funding for the Poor: Earmark specific funds for initiatives that directly benefit low-income patients, such as subsidized or free essential services, medications, and diagnostic tests for those who cannot afford them.
Strengthen Health Insurance Schemes (e.g., NHIS):
Expand Coverage: Aggressively expand the reach of the National Health Insurance Scheme (NHIS) to cover a larger portion of the informal sector and vulnerable populations, potentially through community-based health insurance models or state-led initiatives.
Subsidies for the Poor: Implement government subsidies or premium support for low-income households to ensure they can afford health insurance contributions.
Streamline Processes: Simplify the enrollment and claims processes for the poor to reduce bureaucratic hurdles.
Combat Corruption and Ensure Accountability:
Implement robust financial management systems, regular audits, and strict anti-corruption measures within public hospitals to prevent embezzlement and ensure funds are used for their intended purpose.
Introduce performance-based funding where hospitals receive additional funds based on patient outcomes, efficiency, and satisfaction.
II. Infrastructure and Equipment Upgrade:
Renovation and Modernization: Invest in systematic renovation and modernization of existing public hospital buildings to create clean, safe, and dignified environments.
Equip with Modern Technology: Provide essential, functional diagnostic and treatment equipment (e.g., X-ray machines, ultrasound scanners, laboratory equipment, essential surgical tools). Ensure maintenance contracts and availability of spare parts.
Reliable Utilities: Guarantee constant access to clean water, reliable electricity (invest in solar power as a sustainable backup), and proper waste management systems in all public hospitals.
Basic Amenities: Ensure availability of basic amenities like clean restrooms (separate for male/female), comfortable waiting areas, and proper ventilation.
III. Human Resources Development and Motivation:
Adequate Staffing: Recruit and retain a sufficient number of qualified doctors, nurses, pharmacists, laboratory scientists, and other support staff to reduce workload and improve patient-to-staff ratios.
Competitive Remuneration and Welfare: Offer attractive and timely salaries, allowances, and a comprehensive benefits package (including health insurance and pensions) to stem the brain drain and motivate staff.
Continuous Professional Development (CPD): Provide regular training opportunities to upgrade skills, keep staff abreast of new medical advancements, and improve patient communication.
Ethical Conduct and Empathy Training: Conduct mandatory training on medical ethics, patient rights, empathy, and respectful communication, particularly towards low-income patients who may feel disempowered.
Performance Incentives: Introduce performance-based incentives for staff tied to patient satisfaction, quality of care, and efficiency, rather than just volume.
Safety and Security: Enhance security measures within hospital premises to protect staff from harassment or violence.
IV. Operational Efficiency and Patient-Centered Care:
Streamline Processes: Implement efficient patient flow systems, from registration to consultation, diagnosis, and treatment, to reduce long waiting times and bureaucratic bottlenecks.
Digitalization (Electronic Health Records - EHR):
Implement EHR systems to improve record-keeping, reduce errors, enhance data sharing among departments, and enable better patient tracking.
Digitalize appointment scheduling and billing to minimize human interface and reduce opportunities for corruption.
Focus on Primary Healthcare (PHC): Strengthen the referral system from PHC centers to secondary and tertiary public hospitals. Well-equipped and staffed PHCs can manage common ailments, reducing the burden on hospitals and making basic care accessible at the community level.
Culturally Sensitive Care: Train staff to understand and respect the cultural beliefs and practices of diverse patient populations, which can influence health-seeking behaviors.
Patient Feedback Mechanisms: Establish accessible and confidential channels for patients to provide feedback, lodge complaints, and make suggestions for improvement. Use this feedback to drive continuous improvement.
Transparency and Information: Clearly display service costs (if any), patients' rights, and grievance procedures. Provide clear information about treatment plans in a language patients understand.
V. Innovative Service Delivery Models:
Mobile Clinics and Outreach Programs: Implement mobile health clinics that travel to underserved rural communities, providing basic diagnostic, preventive, and primary care services, as well as health education.
Telemedicine: Leverage telemedicine for remote consultations, specialist opinions, and follow-ups, particularly for patients in remote areas where specialists are scarce. This can reduce travel costs and time for patients.
Community Health Workers (CHWs): Train and deploy CHWs from within the communities to act as a link between the community and the health system, providing basic health education, screening, and facilitating referrals.
Partnerships with NGOs and CSOs: Collaborate with non-governmental organizations and civil society organizations that have experience in delivering healthcare to underserved populations.
By implementing these strategies, public hospitals can move towards becoming trusted, accessible, and high-quality healthcare providers for all, especially the most vulnerable members of society.
3 months ago
Focus Africa-
How does economic dependency translate into political or cultural influence from foreign powers?
Economic dependency translates into political or cultural influence from foreign powers through a process often referred to as soft power.
This influence is non-coercive and stems from the ability to attract and persuade rather than to threaten or force. When a country becomes heavily reliant on another for trade, investment, or aid, it becomes vulnerable to both direct and indirect forms of external influence.
Political Influence-
Economic dependency gives foreign powers significant political leverage. The dominant country can use its economic relationship to pressure the dependent country into aligning its policies with its own interests.
Conditional Aid and Loans: International organizations or dominant countries often attach conditions to aid or loans. These conditions may require the recipient country to adopt specific economic policies, such as deregulation, privatization, or trade liberalization, which can open up its markets to foreign corporations.
Trade Sanctions and Incentives: A foreign power can threaten to impose trade sanctions or restrict market access to influence a dependent country's political decisions, such as its stance on human rights, territorial disputes, or voting patterns in international forums like the UN. For example, a country heavily reliant on another for a specific good may be forced to make political concessions to ensure that supply chain remains open.
Foreign Direct Investment (FDI): Foreign companies, backed by their home governments, can gain significant influence over the host country's domestic policy. They may pressure the government for tax breaks, relaxed labor laws, or a more favorable regulatory environment in exchange for continued investment and job creation.
Cultural Influence-
Economic dependency is a key vehicle for the spread of cultural influence. When a country's products, media, and technology dominate a market, they bring with them a set of values, norms, and lifestyles.
Media and Consumerism: The proliferation of foreign media, films, music, and social media platforms can shape a local population's tastes, values, and aspirations. This can lead to a shift away from traditional cultural practices toward a more global, often Western or Chinese, consumer culture. The popularity of a country's culture can increase demand for its goods, creating a self-reinforcing cycle.
Educational and Ideological Influence: Economic ties often lead to educational exchanges and the establishment of foreign-funded institutions. This can influence the curriculum and academic values of the dependent country. For example, a country offering scholarships or establishing cultural centers can promote its language, history, and political ideology, shaping the worldview of a new generation of leaders and professionals.
How does economic dependency translate into political or cultural influence from foreign powers?
Economic dependency translates into political or cultural influence from foreign powers through a process often referred to as soft power.
This influence is non-coercive and stems from the ability to attract and persuade rather than to threaten or force. When a country becomes heavily reliant on another for trade, investment, or aid, it becomes vulnerable to both direct and indirect forms of external influence.
Political Influence-
Economic dependency gives foreign powers significant political leverage. The dominant country can use its economic relationship to pressure the dependent country into aligning its policies with its own interests.
Conditional Aid and Loans: International organizations or dominant countries often attach conditions to aid or loans. These conditions may require the recipient country to adopt specific economic policies, such as deregulation, privatization, or trade liberalization, which can open up its markets to foreign corporations.
Trade Sanctions and Incentives: A foreign power can threaten to impose trade sanctions or restrict market access to influence a dependent country's political decisions, such as its stance on human rights, territorial disputes, or voting patterns in international forums like the UN. For example, a country heavily reliant on another for a specific good may be forced to make political concessions to ensure that supply chain remains open.
Foreign Direct Investment (FDI): Foreign companies, backed by their home governments, can gain significant influence over the host country's domestic policy. They may pressure the government for tax breaks, relaxed labor laws, or a more favorable regulatory environment in exchange for continued investment and job creation.
Cultural Influence-
Economic dependency is a key vehicle for the spread of cultural influence. When a country's products, media, and technology dominate a market, they bring with them a set of values, norms, and lifestyles.
Media and Consumerism: The proliferation of foreign media, films, music, and social media platforms can shape a local population's tastes, values, and aspirations. This can lead to a shift away from traditional cultural practices toward a more global, often Western or Chinese, consumer culture. The popularity of a country's culture can increase demand for its goods, creating a self-reinforcing cycle.
Educational and Ideological Influence: Economic ties often lead to educational exchanges and the establishment of foreign-funded institutions. This can influence the curriculum and academic values of the dependent country. For example, a country offering scholarships or establishing cultural centers can promote its language, history, and political ideology, shaping the worldview of a new generation of leaders and professionals.
3 months ago
Former Google exec says AI's going to lead to a 'short-term dystopia' because the idea it will create new jobs for the ones it's replacing is '100% crap'.
Something funny happened as I was watching Google X's former chief business officer Mo Gawdat, on the Google-owned platform YouTube, outline his exact take on the AI dystopia he thinks is coming. The host began to ask Gawdat about the idea AI will create new jobs, then the video halted while Google ads served me a 15-second clip showing someone using Microsoft CoPilot to do their job.
When Gawdat returns, he begins his answer by talking about the idea of the West transitioning into service or knowledge economies: people, as he puts it, who "type on a keyboard and use a mouse." Oh dear. Gawdat's economics lesson concludes that "all we produce in the West is words [...] and designs. All of these things can be produced by AI."
One thing is impossible to deny: the business world is very interested in the idea of replacing humans with AI and, where it can be done, will not hesitate to do so. There's also the fact that every big tech company is pushing AI into their products and our lives.
The AI industry has something of a stock line about its technology replacing existing careers: AI will simultaneously create new jobs we can't even imagine, and people will start working in those fields. But Gawdat doesn't buy that line, and in straightforward language calls the whole idea "100% crap" (thanks, Windows Central).
Gawdat left Google to form an AI startup, Emma.love, and cites this company as an example of what he's talking about: the app was apparently built with only two other developers, a job that Gawdat reckons would have taken "over 350 developers" without AI assistance.
"Artificial general intelligence is going to be better than humans at everything, including being a CEO," says Gawdat, referring to the idea that the industry will eventually produce an AI model capable of reasoning and more intelligent than humans. "There will be a time where most incompetent CEOs will be replaced.”
https://youtu.be/S9a1nLw70...
Gawdat's spin on this, however, is that society has to undergo a paradigm shift in how we think about our lives: "We were never made to wake up every morning and just occupy 20 hours of our day with work. We’re not made for that. We defined our purpose as work. That’s a capitalist lie."
Tell me more, comrade! Gawdat generally seems to hold a rather low view of executives and their priorities, pointing out that the AI future is subject to human "hunger for power, greed, and ego” because the tools themselves will be controlled by "stupid leaders." I'm not sure I'd characterise Elon Musk as stupid, but I doubt I'm alone in thinking I'd rather not have him in charge of re-arranging society.
"There is no doubt that lots of jobs will be lost," says Gawdat. "Are we prepared to tell our governments, this is an ideological shift similar to socialism, similar to Communism, and are we ready from a budget point of view? Instead of spending a trillion dollars a year on arms and explosives and autonomous weapons to suppress people because we can't feed them."
Gawdat runs through some beermat maths, offering an estimate that $2.4-2.7 dollars is spent on military hardware every year, a fraction of which could solve a problem like world hunger, or lift the global population out of extreme poverty. Then we get into the truly starry-eyed stuff like universal healthcare worldwide and the end of war, with Gawdat saying for AI these things would be "simple decisions."
Hmm. I'll have some of what he's smoking.
Gawdat's take on AI starts out more persuasive than many others I've seen, but when it gets onto the more fantastical ramifications the caveat is simply enormous. If the singularity happens and AI just takes over running the planet then, sure, all bets are off: who knows whether we'll end up with dystopia or utopia. But that day may never come and, until then, there will still be human beings somewhere pulling all the levers. And as history shows, time and again, humans can be horrendous at making simple decisions: and that's rarely good for the rest of us.
Something funny happened as I was watching Google X's former chief business officer Mo Gawdat, on the Google-owned platform YouTube, outline his exact take on the AI dystopia he thinks is coming. The host began to ask Gawdat about the idea AI will create new jobs, then the video halted while Google ads served me a 15-second clip showing someone using Microsoft CoPilot to do their job.
When Gawdat returns, he begins his answer by talking about the idea of the West transitioning into service or knowledge economies: people, as he puts it, who "type on a keyboard and use a mouse." Oh dear. Gawdat's economics lesson concludes that "all we produce in the West is words [...] and designs. All of these things can be produced by AI."
One thing is impossible to deny: the business world is very interested in the idea of replacing humans with AI and, where it can be done, will not hesitate to do so. There's also the fact that every big tech company is pushing AI into their products and our lives.
The AI industry has something of a stock line about its technology replacing existing careers: AI will simultaneously create new jobs we can't even imagine, and people will start working in those fields. But Gawdat doesn't buy that line, and in straightforward language calls the whole idea "100% crap" (thanks, Windows Central).
Gawdat left Google to form an AI startup, Emma.love, and cites this company as an example of what he's talking about: the app was apparently built with only two other developers, a job that Gawdat reckons would have taken "over 350 developers" without AI assistance.
"Artificial general intelligence is going to be better than humans at everything, including being a CEO," says Gawdat, referring to the idea that the industry will eventually produce an AI model capable of reasoning and more intelligent than humans. "There will be a time where most incompetent CEOs will be replaced.”
https://youtu.be/S9a1nLw70...
Gawdat's spin on this, however, is that society has to undergo a paradigm shift in how we think about our lives: "We were never made to wake up every morning and just occupy 20 hours of our day with work. We’re not made for that. We defined our purpose as work. That’s a capitalist lie."
Tell me more, comrade! Gawdat generally seems to hold a rather low view of executives and their priorities, pointing out that the AI future is subject to human "hunger for power, greed, and ego” because the tools themselves will be controlled by "stupid leaders." I'm not sure I'd characterise Elon Musk as stupid, but I doubt I'm alone in thinking I'd rather not have him in charge of re-arranging society.
"There is no doubt that lots of jobs will be lost," says Gawdat. "Are we prepared to tell our governments, this is an ideological shift similar to socialism, similar to Communism, and are we ready from a budget point of view? Instead of spending a trillion dollars a year on arms and explosives and autonomous weapons to suppress people because we can't feed them."
Gawdat runs through some beermat maths, offering an estimate that $2.4-2.7 dollars is spent on military hardware every year, a fraction of which could solve a problem like world hunger, or lift the global population out of extreme poverty. Then we get into the truly starry-eyed stuff like universal healthcare worldwide and the end of war, with Gawdat saying for AI these things would be "simple decisions."
Hmm. I'll have some of what he's smoking.
Gawdat's take on AI starts out more persuasive than many others I've seen, but when it gets onto the more fantastical ramifications the caveat is simply enormous. If the singularity happens and AI just takes over running the planet then, sure, all bets are off: who knows whether we'll end up with dystopia or utopia. But that day may never come and, until then, there will still be human beings somewhere pulling all the levers. And as history shows, time and again, humans can be horrendous at making simple decisions: and that's rarely good for the rest of us.
3 months ago
Who Owns The Future-
From Colonies to Coalitions: Can Africa Build a Unified Voice?
Africa’s history is a story of fragmentation imposed from without—borders drawn by colonial powers with no regard for people, cultures, or economic logic.
Today, the continent still wrestles with division, yet the stakes have never been higher.
As global powers jostle for influence, resources, and strategic advantage, can Africa transcend its fractured past to build a truly unified voice—one that speaks with power and purpose on the world stage?
The Colonial Legacy: A Fractured Foundation
Africa’s 54 countries were carved out in the Berlin Conference (1884-85), ignoring ethnic, linguistic, and cultural realities.
Arbitrary borders created states too small to wield global influence and often internally divided.
Colonial administrations prioritized resource extraction, not integration or development.
This legacy of division has made continental unity challenging—fostering conflict, mistrust, and fragmented policies.
Current Steps Toward Unity-
The dream of African unity is far from dead. Key initiatives include:
African Union (AU): Founded in 2001, replacing the Organization of African Unity, with a stronger mandate for political and economic integration.
African Continental Free Trade Area (AfCFTA): Launched in 2021, aiming to create the largest free trade zone in the world, boosting intra-African commerce.
Regional Economic Communities (RECs): ECOWAS, SADC, EAC, and others work regionally on trade, security, and infrastructure.
Agenda 2063: Africa’s strategic framework for socio-economic transformation and integration over 50 years.
Challenges to a Unified Voice-
Despite progress, obstacles remain:
1. Sovereignty vs. Supranationalism
Many nations fear losing sovereignty. Leaders hesitate to cede power to continental institutions, weakening enforcement and cooperation.
2. Economic Disparities
From Nigeria’s oil wealth to Malawi’s agrarian economy, disparities create conflicting interests and competition.
3. Political Instability and Conflicts
Civil wars, coups, and political repression distract from unity goals and complicate common foreign policy.
4. External Interference
Foreign powers exploit divisions through “divide and rule,” bilateral deals, and proxy conflicts.
5. Infrastructure and Connectivity Gaps
Poor transport, energy, and digital infrastructure hinder integration.
Why a Unified African Voice Matters Now-
-Global Bargaining Power: United, Africa can negotiate better trade terms, debt relief, and technology transfers.
-Security and Peace: Coordinated responses to terrorism, piracy, and conflicts reduce human and economic costs.
-Economic Growth: Integrated markets attract investment and enable industrialization.
-Cultural Renaissance: A shared African identity can empower youth, diaspora, and global cultural diplomacy.
How Can Africa Build This Voice?
- Strengthen Continental Institutions
Empower the AU with real enforcement mechanisms
-Foster transparency and accountability in continental governance
- Promote Economic Integration
Accelerate AfCFTA implementation
Harmonize regulations and remove non-tariff barriers
- Invest in Connectivity
Build cross-border infrastructure (roads, rail, energy grids, internet)
-Support regional digital identity and payment systems
-Encourage Political Will and Vision
Cultivate leaders who prioritize continental unity over narrow nationalism
-Engage youth and civil society in pan-African projects
-Manage External Relations Strategically
Present a united front in dealing with China, the West, and others
-Develop African-led development banks and investment funds
Conclusion: From Colonies to Coalitions
Africa’s future will not be written by outsiders but by Africans themselves—if they unite.
Building a unified voice is not easy. It requires courage to overcome colonial legacies, trust to bridge diverse peoples, and vision to see beyond immediate gains.
But in this moment of global flux, a strong, united Africa could transform from a continent of fragmented colonies to a coalition of powerful nations—one that shapes its destiny and helps shape the world.
The question is not if Africa can unite—but when and how it will seize this historic opportunity.
From Colonies to Coalitions: Can Africa Build a Unified Voice?
Africa’s history is a story of fragmentation imposed from without—borders drawn by colonial powers with no regard for people, cultures, or economic logic.
Today, the continent still wrestles with division, yet the stakes have never been higher.
As global powers jostle for influence, resources, and strategic advantage, can Africa transcend its fractured past to build a truly unified voice—one that speaks with power and purpose on the world stage?
The Colonial Legacy: A Fractured Foundation
Africa’s 54 countries were carved out in the Berlin Conference (1884-85), ignoring ethnic, linguistic, and cultural realities.
Arbitrary borders created states too small to wield global influence and often internally divided.
Colonial administrations prioritized resource extraction, not integration or development.
This legacy of division has made continental unity challenging—fostering conflict, mistrust, and fragmented policies.
Current Steps Toward Unity-
The dream of African unity is far from dead. Key initiatives include:
African Union (AU): Founded in 2001, replacing the Organization of African Unity, with a stronger mandate for political and economic integration.
African Continental Free Trade Area (AfCFTA): Launched in 2021, aiming to create the largest free trade zone in the world, boosting intra-African commerce.
Regional Economic Communities (RECs): ECOWAS, SADC, EAC, and others work regionally on trade, security, and infrastructure.
Agenda 2063: Africa’s strategic framework for socio-economic transformation and integration over 50 years.
Challenges to a Unified Voice-
Despite progress, obstacles remain:
1. Sovereignty vs. Supranationalism
Many nations fear losing sovereignty. Leaders hesitate to cede power to continental institutions, weakening enforcement and cooperation.
2. Economic Disparities
From Nigeria’s oil wealth to Malawi’s agrarian economy, disparities create conflicting interests and competition.
3. Political Instability and Conflicts
Civil wars, coups, and political repression distract from unity goals and complicate common foreign policy.
4. External Interference
Foreign powers exploit divisions through “divide and rule,” bilateral deals, and proxy conflicts.
5. Infrastructure and Connectivity Gaps
Poor transport, energy, and digital infrastructure hinder integration.
Why a Unified African Voice Matters Now-
-Global Bargaining Power: United, Africa can negotiate better trade terms, debt relief, and technology transfers.
-Security and Peace: Coordinated responses to terrorism, piracy, and conflicts reduce human and economic costs.
-Economic Growth: Integrated markets attract investment and enable industrialization.
-Cultural Renaissance: A shared African identity can empower youth, diaspora, and global cultural diplomacy.
How Can Africa Build This Voice?
- Strengthen Continental Institutions
Empower the AU with real enforcement mechanisms
-Foster transparency and accountability in continental governance
- Promote Economic Integration
Accelerate AfCFTA implementation
Harmonize regulations and remove non-tariff barriers
- Invest in Connectivity
Build cross-border infrastructure (roads, rail, energy grids, internet)
-Support regional digital identity and payment systems
-Encourage Political Will and Vision
Cultivate leaders who prioritize continental unity over narrow nationalism
-Engage youth and civil society in pan-African projects
-Manage External Relations Strategically
Present a united front in dealing with China, the West, and others
-Develop African-led development banks and investment funds
Conclusion: From Colonies to Coalitions
Africa’s future will not be written by outsiders but by Africans themselves—if they unite.
Building a unified voice is not easy. It requires courage to overcome colonial legacies, trust to bridge diverse peoples, and vision to see beyond immediate gains.
But in this moment of global flux, a strong, united Africa could transform from a continent of fragmented colonies to a coalition of powerful nations—one that shapes its destiny and helps shape the world.
The question is not if Africa can unite—but when and how it will seize this historic opportunity.
3 months ago
How do cyber operations from groups in Iran and Vietnam compare in tactics and targets?
While both Iranian and Vietnamese cyber groups engage in state-sponsored cyber operations, their primary motivations, geopolitical contexts, and consequently, their tactics and targets, differ significantly.
Iranian Cyber Groups (e.g., APT33/Elfin, APT34/OilRig, APT35/Charming Kitten, MuddyWater)
Main Motives:
Iran's cyber activities are strongly driven by its geopolitical aspirations, regional rivalries (especially with Saudi Arabia and Israel), and desire to counter international sanctions. Their motivations include:
Espionage: Gathering intelligence on political, military, and economic developments, particularly in the Middle East, U.S., Europe, and Israel.
Disruption and Retaliation: Disrupting critical infrastructure, especially against perceived adversaries (e.g., in response to sanctions or political actions). They are willing to engage in destructive attacks.
Influence Operations: Spreading propaganda, manipulating public opinion, and sowing discord in rival nations.
Intellectual Property Theft (Secondary): While they do engage in this, it's often more opportunistic or tied to specific military/dual-use technologies rather than broad economic development.
Internal Control: Surveillance and repression of dissidents, both domestically and abroad.
Tactics:
Iranian groups often leverage a blend of technical sophistication and social engineering.
Aggressive Spear-Phishing & Social Engineering: Highly sophisticated and persistent phishing campaigns are a hallmark. They often impersonate legitimate entities (journalists, academics, government officials, recruiters) to build trust and trick targets into revealing credentials or downloading malware. They're known for using compromised accounts for further phishing.
Exploitation of Known Vulnerabilities: They are quick to exploit newly disclosed vulnerabilities (N-days) in widely used software and internet-facing systems (VPNs, firewalls, Exchange servers) to gain initial access.
Living Off The Land (LotL) & OSINT: They frequently use legitimate system tools (PowerShell, RDP, Mimikatz) and open-source intelligence (OSINT) to evade detection and understand victim networks.
Web Shells & Backdoors: Deployment of web shells for persistent access and custom backdoors.
Destructive Malware/Wipers: Iranian groups have a history of deploying destructive malware (e.g., Shamoon, ZeroCleare) to wipe data and disable systems, particularly against targets in the energy and industrial sectors.
Hybrid Operations: Increasingly, they combine hacking and data theft with information operations, leaking stolen data online, and using social media for amplification and harassment.
Ransomware (Collaborative/Opportunistic): While not their primary goal like North Korea, some Iranian groups have been observed collaborating with cybercriminal ransomware affiliates or directly deploying ransomware for financial gain or disruption.
Targets:
Middle East Region: Heavily focused on Gulf Cooperation Council (GCC) countries (especially Saudi Arabia, UAE), Israel, and other regional rivals.
Government & Military: Foreign ministries, defense contractors, intelligence agencies, and government officials, particularly those involved in nuclear policy, sanctions, or regional security.
Energy Sector (Oil & Gas): A long-standing target for both espionage and potential disruption, reflecting Iran's strategic interests.
Critical Infrastructure (OT/ICS): Increasing focus on industrial control systems and operational technology, potentially for pre-positioning or disruptive attacks.
Telecommunications & Financial Services: For intelligence gathering and network access.
Journalists, Academics, Dissidents, Human Rights Activists: Both within Iran and among the diaspora, for surveillance and repression.
Vietnamese Cyber Groups (e.g., APT32/OceanLotus, APT30/Naikon)
Main Motives:
Vietnamese cyber operations are strongly linked to national economic development, protecting sovereignty claims (especially in the South China Sea), and maintaining political stability.
Economic Espionage: Stealing intellectual property, trade secrets, and competitive intelligence to support Vietnamese industries and accelerate economic growth. This is a very significant motivation.
Political Espionage: Gathering intelligence on foreign governments, political organizations, and diplomats relevant to Vietnam's geopolitical interests, particularly concerning regional rivals and partners.
Surveillance and Monitoring: Tracking and monitoring political dissidents, journalists, NGOs, and foreign entities perceived as a threat to the ruling party or national stability.
South China Sea Disputes: Gaining intelligence on rival claimants and international actors involved in the South China Sea disputes.
Tactics:
Vietnamese groups often demonstrate high levels of sophistication and persistence, with a focus on long-term access and stealth.
Sophisticated Spear-Phishing: Highly customized and contextualized spear-phishing emails, often impersonating trusted contacts or organizations, are a primary initial access vector.
Watering Hole Attacks: Compromising websites frequented by specific targets and implanting malware to infect visitors.
Custom Malware and Backdoors: Development and use of sophisticated custom malware (Remote Access Trojans, info-stealers) designed for covert data exfiltration and persistent access.
Exploitation of Zero-Day and N-Day Vulnerabilities: While less frequent than Iranian groups' aggressive N-day exploitation, they are capable of exploiting zero-days.
Supply Chain Attacks: There have been instances where Vietnamese groups have targeted software or hardware vendors to compromise their clients downstream.
Leveraging Cloud Services: Using legitimate cloud services for command and control (C2) or data exfiltration to blend in with normal network traffic.
Evasion Techniques: Employing various techniques to avoid detection by security software, including code obfuscation and anti-analysis checks.
Targets:
Southeast Asian Governments: Particularly those involved in the South China Sea disputes, for political intelligence.
Foreign Businesses & Multinational Corporations: Across various sectors (e.g., automotive, media, hospitality, manufacturing, technology, healthcare, e-commerce) for economic espionage and IP theft.
Political Dissidents & Human Rights Activists: Both domestic and international, for surveillance and control.
Journalists and NGOs: Especially those reporting on Vietnam or human rights issues.
Critical Infrastructure (Limited Public Reporting): While less publicly highlighted than Iranian or Chinese groups, there have been some reports of Vietnamese groups targeting critical infrastructure, but often for intelligence gathering rather than overt disruption.
Comparison Summary:
Feature- Iranian Cyber Groups----
Primary Motive- Geopolitical influence, regional rivalries, countering sanctions, disruption, espionage, retaliation.
Willingness for Disruption- High – known for destructive attacks/wipers.
Key Regions of Focus- Middle East (GCC, Israel), U.S., Europe.
Tactics Emphasis- Aggressive spear-phishing, N-day exploitation, LotL, web shells, destructive malware, information operations.
Financial Crime- Opportunistic ransomware or collaboration with criminals.
Vietnamese Cyber Groups-
Primary Motive-
Economic development (IP theft), political espionage (Sovereignty, South China Sea), internal control.
Willingness for Disruption-
Lower – focus on stealth, long-term access, and data exfiltration, less on overt disruption.
Key Regions of Focus-
Southeast Asia (ASEAN), U.S. (related to economic/political ties).
Tactics Emphasis-
Sophisticated spear-phishing, custom malware, watering holes, supply chain (less common), long-term stealth, cloud usage.
Financial Crime-Less prominent, but some engagement in cybercrime for revenue.
Export to Sheets-
In essence, Iranian groups are more overt and willing to engage in destructive actions driven by immediate geopolitical tensions, while Vietnamese groups are generally more focused on stealthy, long-term espionage and IP theft to support national development and strategic interests in their region.
While both Iranian and Vietnamese cyber groups engage in state-sponsored cyber operations, their primary motivations, geopolitical contexts, and consequently, their tactics and targets, differ significantly.
Iranian Cyber Groups (e.g., APT33/Elfin, APT34/OilRig, APT35/Charming Kitten, MuddyWater)
Main Motives:
Iran's cyber activities are strongly driven by its geopolitical aspirations, regional rivalries (especially with Saudi Arabia and Israel), and desire to counter international sanctions. Their motivations include:
Espionage: Gathering intelligence on political, military, and economic developments, particularly in the Middle East, U.S., Europe, and Israel.
Disruption and Retaliation: Disrupting critical infrastructure, especially against perceived adversaries (e.g., in response to sanctions or political actions). They are willing to engage in destructive attacks.
Influence Operations: Spreading propaganda, manipulating public opinion, and sowing discord in rival nations.
Intellectual Property Theft (Secondary): While they do engage in this, it's often more opportunistic or tied to specific military/dual-use technologies rather than broad economic development.
Internal Control: Surveillance and repression of dissidents, both domestically and abroad.
Tactics:
Iranian groups often leverage a blend of technical sophistication and social engineering.
Aggressive Spear-Phishing & Social Engineering: Highly sophisticated and persistent phishing campaigns are a hallmark. They often impersonate legitimate entities (journalists, academics, government officials, recruiters) to build trust and trick targets into revealing credentials or downloading malware. They're known for using compromised accounts for further phishing.
Exploitation of Known Vulnerabilities: They are quick to exploit newly disclosed vulnerabilities (N-days) in widely used software and internet-facing systems (VPNs, firewalls, Exchange servers) to gain initial access.
Living Off The Land (LotL) & OSINT: They frequently use legitimate system tools (PowerShell, RDP, Mimikatz) and open-source intelligence (OSINT) to evade detection and understand victim networks.
Web Shells & Backdoors: Deployment of web shells for persistent access and custom backdoors.
Destructive Malware/Wipers: Iranian groups have a history of deploying destructive malware (e.g., Shamoon, ZeroCleare) to wipe data and disable systems, particularly against targets in the energy and industrial sectors.
Hybrid Operations: Increasingly, they combine hacking and data theft with information operations, leaking stolen data online, and using social media for amplification and harassment.
Ransomware (Collaborative/Opportunistic): While not their primary goal like North Korea, some Iranian groups have been observed collaborating with cybercriminal ransomware affiliates or directly deploying ransomware for financial gain or disruption.
Targets:
Middle East Region: Heavily focused on Gulf Cooperation Council (GCC) countries (especially Saudi Arabia, UAE), Israel, and other regional rivals.
Government & Military: Foreign ministries, defense contractors, intelligence agencies, and government officials, particularly those involved in nuclear policy, sanctions, or regional security.
Energy Sector (Oil & Gas): A long-standing target for both espionage and potential disruption, reflecting Iran's strategic interests.
Critical Infrastructure (OT/ICS): Increasing focus on industrial control systems and operational technology, potentially for pre-positioning or disruptive attacks.
Telecommunications & Financial Services: For intelligence gathering and network access.
Journalists, Academics, Dissidents, Human Rights Activists: Both within Iran and among the diaspora, for surveillance and repression.
Vietnamese Cyber Groups (e.g., APT32/OceanLotus, APT30/Naikon)
Main Motives:
Vietnamese cyber operations are strongly linked to national economic development, protecting sovereignty claims (especially in the South China Sea), and maintaining political stability.
Economic Espionage: Stealing intellectual property, trade secrets, and competitive intelligence to support Vietnamese industries and accelerate economic growth. This is a very significant motivation.
Political Espionage: Gathering intelligence on foreign governments, political organizations, and diplomats relevant to Vietnam's geopolitical interests, particularly concerning regional rivals and partners.
Surveillance and Monitoring: Tracking and monitoring political dissidents, journalists, NGOs, and foreign entities perceived as a threat to the ruling party or national stability.
South China Sea Disputes: Gaining intelligence on rival claimants and international actors involved in the South China Sea disputes.
Tactics:
Vietnamese groups often demonstrate high levels of sophistication and persistence, with a focus on long-term access and stealth.
Sophisticated Spear-Phishing: Highly customized and contextualized spear-phishing emails, often impersonating trusted contacts or organizations, are a primary initial access vector.
Watering Hole Attacks: Compromising websites frequented by specific targets and implanting malware to infect visitors.
Custom Malware and Backdoors: Development and use of sophisticated custom malware (Remote Access Trojans, info-stealers) designed for covert data exfiltration and persistent access.
Exploitation of Zero-Day and N-Day Vulnerabilities: While less frequent than Iranian groups' aggressive N-day exploitation, they are capable of exploiting zero-days.
Supply Chain Attacks: There have been instances where Vietnamese groups have targeted software or hardware vendors to compromise their clients downstream.
Leveraging Cloud Services: Using legitimate cloud services for command and control (C2) or data exfiltration to blend in with normal network traffic.
Evasion Techniques: Employing various techniques to avoid detection by security software, including code obfuscation and anti-analysis checks.
Targets:
Southeast Asian Governments: Particularly those involved in the South China Sea disputes, for political intelligence.
Foreign Businesses & Multinational Corporations: Across various sectors (e.g., automotive, media, hospitality, manufacturing, technology, healthcare, e-commerce) for economic espionage and IP theft.
Political Dissidents & Human Rights Activists: Both domestic and international, for surveillance and control.
Journalists and NGOs: Especially those reporting on Vietnam or human rights issues.
Critical Infrastructure (Limited Public Reporting): While less publicly highlighted than Iranian or Chinese groups, there have been some reports of Vietnamese groups targeting critical infrastructure, but often for intelligence gathering rather than overt disruption.
Comparison Summary:
Feature- Iranian Cyber Groups----
Primary Motive- Geopolitical influence, regional rivalries, countering sanctions, disruption, espionage, retaliation.
Willingness for Disruption- High – known for destructive attacks/wipers.
Key Regions of Focus- Middle East (GCC, Israel), U.S., Europe.
Tactics Emphasis- Aggressive spear-phishing, N-day exploitation, LotL, web shells, destructive malware, information operations.
Financial Crime- Opportunistic ransomware or collaboration with criminals.
Vietnamese Cyber Groups-
Primary Motive-
Economic development (IP theft), political espionage (Sovereignty, South China Sea), internal control.
Willingness for Disruption-
Lower – focus on stealth, long-term access, and data exfiltration, less on overt disruption.
Key Regions of Focus-
Southeast Asia (ASEAN), U.S. (related to economic/political ties).
Tactics Emphasis-
Sophisticated spear-phishing, custom malware, watering holes, supply chain (less common), long-term stealth, cloud usage.
Financial Crime-Less prominent, but some engagement in cybercrime for revenue.
Export to Sheets-
In essence, Iranian groups are more overt and willing to engage in destructive actions driven by immediate geopolitical tensions, while Vietnamese groups are generally more focused on stealthy, long-term espionage and IP theft to support national development and strategic interests in their region.
3 months ago
Focus Nigeria-
How can Nigeria stop the “brain drain” of doctors and nurses?
Stopping the "brain drain" of doctors and nurses from Nigeria requires a comprehensive, sustained, and multi-faceted approach that addresses the root causes of their migration.
It's not just about offering more money, but creating an enabling environment where healthcare professionals can thrive, feel valued, and provide quality care.
Here's a detailed strategy to combat the brain drain:
I. Improve Working Conditions and Environment:
Modernize Infrastructure and Equipment:
Adequate Funding: Significantly increase the healthcare budget allocation (currently far below the Abuja Declaration's 15% target) and ensure transparent and efficient utilization of funds.
Investment in Facilities: Renovate existing hospitals and clinics, and build new, well-equipped facilities, especially in underserved areas.
Modern Technology: Equip hospitals with up-to-date diagnostic tools, surgical equipment, and specialized machinery (e.g., MRI, CT scanners, radiotherapy machines). Ensure regular maintenance and availability of spare parts.
Reliable Utilities: Provide stable electricity (e.g., through solar power solutions and reliable backup generators) and clean water supply in all healthcare facilities.
Ensure Safety and Security:
Protection for Staff: Implement robust security measures within hospitals and clinics to protect healthcare workers from violence, harassment, and kidnapping, especially in high-risk areas.
Occupational Health & Safety: Establish and enforce comprehensive occupational health and safety policies that prioritize the physical and mental well-being of nurses and doctors.
Manage Workload and Staffing:
Adequate Staffing: Recruit more healthcare professionals to reduce the excessive workload on existing staff. This might require increasing training capacity within Nigeria.
Fair Scheduling: Implement equitable work schedules and shifts to prevent burnout and ensure a healthy work-life balance.
II. Enhance Remuneration and Welfare:
Competitive Salaries and Allowances:
Offer competitive salaries and allowances that are comparable to what healthcare professionals could earn in other sectors within Nigeria or in regional countries. While matching Western salaries might be challenging, making local pay significantly better than the current reality is crucial.
Timely Payments: Ensure prompt and consistent payment of salaries and benefits to avoid the frustration caused by arrears.
Attractive Benefits Package:
Health Insurance: Provide comprehensive health insurance for healthcare workers and their families.
Housing and Transportation: Offer subsidized housing, housing allowances, or transportation support, especially for those in rural or high-cost urban areas.
Retirement Benefits: Ensure robust and reliable pension and retirement benefit schemes.
Non-Financial Incentives:
Recognition and Appreciation: Create a culture of recognition and appreciation for healthcare workers' dedication and hard work.
Professional Support: Provide a supportive work environment that values their contributions and addresses their concerns.
III. Professional Development and Career Advancement:
Continuous Professional Development (CPD):
Fund and facilitate regular training programs, workshops, and seminars to keep doctors and nurses updated on the latest medical practices, technologies, and research.
Encourage and sponsor participation in international conferences and training programs where relevant.
Career Progression Opportunities:
Establish clear and transparent career progression pathways based on merit, performance, and further specialization.
Provide opportunities for specialization, postgraduate studies, and leadership roles within the Nigerian healthcare system.
Research Funding:
Allocate dedicated funds for medical research within Nigeria to encourage innovation and give professionals reasons to stay and contribute locally.
Mentorship Programs:
Establish mentorship programs where experienced doctors and nurses guide and support younger professionals.
IV. Strengthening Education and Training within Nigeria:
Increase Training Capacity:
Expand the capacity of medical and nursing schools to train more healthcare professionals, ensuring that the increase in quantity does not compromise quality.
Curriculum Review: Regularly review and update medical and nursing curricula to meet international standards and address Nigeria's specific health challenges.
"Train to Retain" Programs:
Consider policies that incentivize graduates (e.g., scholarships tied to service in Nigeria for a specific period, especially in underserved areas). This must be coupled with improved conditions to avoid simply delaying their eventual departure.
Rural-Focused Training: Develop programs that train healthcare professionals with a specific focus on rural health challenges and encourage them to serve in those areas.
V. Governance, Accountability, and Policy Coherence:
Effective Leadership and Management:
Appoint competent, ethical, and visionary leaders in healthcare institutions who prioritize staff welfare and quality of care.
Ensure efficient administrative management across all levels of the health system.
Robust Accountability:
Establish transparent mechanisms for addressing grievances, investigating misconduct, and ensuring accountability for poor management or corruption within the health sector.
Long-Term National Health Policy:
Develop and consistently implement a stable, long-term national health policy that is insulated from political fluctuations and prioritizes human resources for health. President Tinubu's new health policy is a step in this direction, but consistent implementation is key.
Engage Professional Bodies:
Foster better dialogue and collaboration with professional associations like the Nigerian Medical Association (NMA) and the National Association of Nigerian Nurses and Midwives (NANNM) to address their concerns and gain their buy-in for reforms.
Leverage Diaspora Engagement:
Create structured programs to engage Nigerian healthcare professionals in the diaspora (e.g., for short-term missions, training, mentorship, or tele-medicine consultations). This can help transfer knowledge and build connections without demanding permanent return initially.
Combating the brain drain is a marathon, not a sprint. It requires substantial financial investment, political will, a commitment to systemic change, and a fundamental shift in how healthcare professionals are valued and treated in Nigeria.
How can Nigeria stop the “brain drain” of doctors and nurses?
Stopping the "brain drain" of doctors and nurses from Nigeria requires a comprehensive, sustained, and multi-faceted approach that addresses the root causes of their migration.
It's not just about offering more money, but creating an enabling environment where healthcare professionals can thrive, feel valued, and provide quality care.
Here's a detailed strategy to combat the brain drain:
I. Improve Working Conditions and Environment:
Modernize Infrastructure and Equipment:
Adequate Funding: Significantly increase the healthcare budget allocation (currently far below the Abuja Declaration's 15% target) and ensure transparent and efficient utilization of funds.
Investment in Facilities: Renovate existing hospitals and clinics, and build new, well-equipped facilities, especially in underserved areas.
Modern Technology: Equip hospitals with up-to-date diagnostic tools, surgical equipment, and specialized machinery (e.g., MRI, CT scanners, radiotherapy machines). Ensure regular maintenance and availability of spare parts.
Reliable Utilities: Provide stable electricity (e.g., through solar power solutions and reliable backup generators) and clean water supply in all healthcare facilities.
Ensure Safety and Security:
Protection for Staff: Implement robust security measures within hospitals and clinics to protect healthcare workers from violence, harassment, and kidnapping, especially in high-risk areas.
Occupational Health & Safety: Establish and enforce comprehensive occupational health and safety policies that prioritize the physical and mental well-being of nurses and doctors.
Manage Workload and Staffing:
Adequate Staffing: Recruit more healthcare professionals to reduce the excessive workload on existing staff. This might require increasing training capacity within Nigeria.
Fair Scheduling: Implement equitable work schedules and shifts to prevent burnout and ensure a healthy work-life balance.
II. Enhance Remuneration and Welfare:
Competitive Salaries and Allowances:
Offer competitive salaries and allowances that are comparable to what healthcare professionals could earn in other sectors within Nigeria or in regional countries. While matching Western salaries might be challenging, making local pay significantly better than the current reality is crucial.
Timely Payments: Ensure prompt and consistent payment of salaries and benefits to avoid the frustration caused by arrears.
Attractive Benefits Package:
Health Insurance: Provide comprehensive health insurance for healthcare workers and their families.
Housing and Transportation: Offer subsidized housing, housing allowances, or transportation support, especially for those in rural or high-cost urban areas.
Retirement Benefits: Ensure robust and reliable pension and retirement benefit schemes.
Non-Financial Incentives:
Recognition and Appreciation: Create a culture of recognition and appreciation for healthcare workers' dedication and hard work.
Professional Support: Provide a supportive work environment that values their contributions and addresses their concerns.
III. Professional Development and Career Advancement:
Continuous Professional Development (CPD):
Fund and facilitate regular training programs, workshops, and seminars to keep doctors and nurses updated on the latest medical practices, technologies, and research.
Encourage and sponsor participation in international conferences and training programs where relevant.
Career Progression Opportunities:
Establish clear and transparent career progression pathways based on merit, performance, and further specialization.
Provide opportunities for specialization, postgraduate studies, and leadership roles within the Nigerian healthcare system.
Research Funding:
Allocate dedicated funds for medical research within Nigeria to encourage innovation and give professionals reasons to stay and contribute locally.
Mentorship Programs:
Establish mentorship programs where experienced doctors and nurses guide and support younger professionals.
IV. Strengthening Education and Training within Nigeria:
Increase Training Capacity:
Expand the capacity of medical and nursing schools to train more healthcare professionals, ensuring that the increase in quantity does not compromise quality.
Curriculum Review: Regularly review and update medical and nursing curricula to meet international standards and address Nigeria's specific health challenges.
"Train to Retain" Programs:
Consider policies that incentivize graduates (e.g., scholarships tied to service in Nigeria for a specific period, especially in underserved areas). This must be coupled with improved conditions to avoid simply delaying their eventual departure.
Rural-Focused Training: Develop programs that train healthcare professionals with a specific focus on rural health challenges and encourage them to serve in those areas.
V. Governance, Accountability, and Policy Coherence:
Effective Leadership and Management:
Appoint competent, ethical, and visionary leaders in healthcare institutions who prioritize staff welfare and quality of care.
Ensure efficient administrative management across all levels of the health system.
Robust Accountability:
Establish transparent mechanisms for addressing grievances, investigating misconduct, and ensuring accountability for poor management or corruption within the health sector.
Long-Term National Health Policy:
Develop and consistently implement a stable, long-term national health policy that is insulated from political fluctuations and prioritizes human resources for health. President Tinubu's new health policy is a step in this direction, but consistent implementation is key.
Engage Professional Bodies:
Foster better dialogue and collaboration with professional associations like the Nigerian Medical Association (NMA) and the National Association of Nigerian Nurses and Midwives (NANNM) to address their concerns and gain their buy-in for reforms.
Leverage Diaspora Engagement:
Create structured programs to engage Nigerian healthcare professionals in the diaspora (e.g., for short-term missions, training, mentorship, or tele-medicine consultations). This can help transfer knowledge and build connections without demanding permanent return initially.
Combating the brain drain is a marathon, not a sprint. It requires substantial financial investment, political will, a commitment to systemic change, and a fundamental shift in how healthcare professionals are valued and treated in Nigeria.
3 months ago
Focus Nigeria-
Why do so many Nigerians seek medical treatment abroad?
Nigerians, across various socioeconomic strata, frequently seek medical treatment abroad for a multitude of reasons, highlighting significant systemic issues within Nigeria's healthcare sector. This phenomenon, known as medical tourism, has a substantial economic drain on the country.
Here are the primary reasons why so many Nigerians opt for foreign medical care:
Inadequate Healthcare Infrastructure and Technology:
Obsolete Equipment: Many Nigerian hospitals, especially public ones, lack modern medical equipment (e.g., advanced MRI/CT scanners, specialized surgical tools, radiotherapy machines for cancer treatment). Where equipment exists, it's often poorly maintained or frequently breaks down.
Lack of Specialization: While Nigeria has many general practitioners, there's a severe shortage of highly specialized medical professionals in complex fields like oncology, neurosurgery, advanced cardiology, organ transplantation, and specialized orthopedics.
Dilapidated Facilities: Many hospitals suffer from poor maintenance, overcrowding, unreliable power supply (leading to dependence on expensive generators), and lack of basic amenities like clean water and proper waste disposal.
Shortage and Brain Drain of Medical Professionals:
Mass Exodus: Nigeria faces a severe "brain drain" of qualified doctors, nurses, and other healthcare professionals. Lured by better remuneration, working conditions, access to advanced technology, and professional development opportunities, many migrate to countries like the UK, USA, Canada, and Saudi Arabia.
High Patient-to-Doctor Ratio: The emigration of medical personnel exacerbates the existing shortage, leading to an extremely high patient-to-doctor ratio (far below WHO recommendations), overworking the remaining staff and compromising patient care.
Loss of Expertise: The departure of highly skilled specialists means that certain complex procedures or sophisticated diagnostic interpretations are simply not available in Nigeria.
Lack of Trust in the Local Healthcare System:
Perceived Low Quality of Care: Decades of underfunding and poor performance have eroded public confidence in the Nigerian healthcare system. Many Nigerians, including the elite, believe they will receive superior care, more accurate diagnoses, and better treatment outcomes abroad.
Fear of Misdiagnosis/Malpractice: There's a widespread fear of misdiagnosis, medical negligence, and inadequate follow-up care within Nigeria, prompting individuals to seek second opinions or primary treatment elsewhere.
High-Profile Cases: When prominent Nigerians (including politicians and government officials) consistently seek medical attention abroad, it further reinforces the perception that the local system is not good enough, even for the nation's leaders.
Poor Funding and High Out-of-Pocket Payments:
Low Budgetary Allocation: The Nigerian government's allocation to healthcare consistently falls far below international recommendations (e.g., the Abuja Declaration's 15% target). This limits investment in infrastructure, training, and research.
Out-of-Pocket Expenses: The vast majority of Nigerians pay for healthcare directly out of their pockets, as the National Health Insurance Scheme (NHIS) covers a very small percentage of the population. This means that even basic care can be financially burdensome. For complex treatments, the cost can be prohibitive, making the "all-inclusive" price for treatment abroad (which often seems high in Naira) sometimes comparable or even more appealing if it guarantees a better outcome.
Long Waiting Times and Bureaucracy:
Even when certain treatments are available, patients might face long waiting lists for appointments, diagnostic tests, or surgeries in public hospitals, leading them to seek faster access abroad.
Bureaucratic hurdles and administrative inefficiencies can also frustrate patients and their families.
Desire for Privacy and Confidentiality:
Some high-profile individuals or those seeking treatments for sensitive conditions may travel abroad for greater privacy and confidentiality, away from public scrutiny.
Aggressive Marketing by Foreign Hospitals:
Countries like India, Turkey, and some in the Middle East have developed robust medical tourism industries. They actively market their advanced facilities, specialized doctors, and relatively affordable (compared to Western countries) treatment packages directly to Nigerians.
The collective impact of this medical tourism is a significant drain on Nigeria's foreign exchange reserves (estimated to be billions of dollars annually), a disincentive for investment in local healthcare, and a perpetuation of a system where those who can afford it simply bypass local services, undermining efforts to improve the domestic health sector for the general populace.
Why do so many Nigerians seek medical treatment abroad?
Nigerians, across various socioeconomic strata, frequently seek medical treatment abroad for a multitude of reasons, highlighting significant systemic issues within Nigeria's healthcare sector. This phenomenon, known as medical tourism, has a substantial economic drain on the country.
Here are the primary reasons why so many Nigerians opt for foreign medical care:
Inadequate Healthcare Infrastructure and Technology:
Obsolete Equipment: Many Nigerian hospitals, especially public ones, lack modern medical equipment (e.g., advanced MRI/CT scanners, specialized surgical tools, radiotherapy machines for cancer treatment). Where equipment exists, it's often poorly maintained or frequently breaks down.
Lack of Specialization: While Nigeria has many general practitioners, there's a severe shortage of highly specialized medical professionals in complex fields like oncology, neurosurgery, advanced cardiology, organ transplantation, and specialized orthopedics.
Dilapidated Facilities: Many hospitals suffer from poor maintenance, overcrowding, unreliable power supply (leading to dependence on expensive generators), and lack of basic amenities like clean water and proper waste disposal.
Shortage and Brain Drain of Medical Professionals:
Mass Exodus: Nigeria faces a severe "brain drain" of qualified doctors, nurses, and other healthcare professionals. Lured by better remuneration, working conditions, access to advanced technology, and professional development opportunities, many migrate to countries like the UK, USA, Canada, and Saudi Arabia.
High Patient-to-Doctor Ratio: The emigration of medical personnel exacerbates the existing shortage, leading to an extremely high patient-to-doctor ratio (far below WHO recommendations), overworking the remaining staff and compromising patient care.
Loss of Expertise: The departure of highly skilled specialists means that certain complex procedures or sophisticated diagnostic interpretations are simply not available in Nigeria.
Lack of Trust in the Local Healthcare System:
Perceived Low Quality of Care: Decades of underfunding and poor performance have eroded public confidence in the Nigerian healthcare system. Many Nigerians, including the elite, believe they will receive superior care, more accurate diagnoses, and better treatment outcomes abroad.
Fear of Misdiagnosis/Malpractice: There's a widespread fear of misdiagnosis, medical negligence, and inadequate follow-up care within Nigeria, prompting individuals to seek second opinions or primary treatment elsewhere.
High-Profile Cases: When prominent Nigerians (including politicians and government officials) consistently seek medical attention abroad, it further reinforces the perception that the local system is not good enough, even for the nation's leaders.
Poor Funding and High Out-of-Pocket Payments:
Low Budgetary Allocation: The Nigerian government's allocation to healthcare consistently falls far below international recommendations (e.g., the Abuja Declaration's 15% target). This limits investment in infrastructure, training, and research.
Out-of-Pocket Expenses: The vast majority of Nigerians pay for healthcare directly out of their pockets, as the National Health Insurance Scheme (NHIS) covers a very small percentage of the population. This means that even basic care can be financially burdensome. For complex treatments, the cost can be prohibitive, making the "all-inclusive" price for treatment abroad (which often seems high in Naira) sometimes comparable or even more appealing if it guarantees a better outcome.
Long Waiting Times and Bureaucracy:
Even when certain treatments are available, patients might face long waiting lists for appointments, diagnostic tests, or surgeries in public hospitals, leading them to seek faster access abroad.
Bureaucratic hurdles and administrative inefficiencies can also frustrate patients and their families.
Desire for Privacy and Confidentiality:
Some high-profile individuals or those seeking treatments for sensitive conditions may travel abroad for greater privacy and confidentiality, away from public scrutiny.
Aggressive Marketing by Foreign Hospitals:
Countries like India, Turkey, and some in the Middle East have developed robust medical tourism industries. They actively market their advanced facilities, specialized doctors, and relatively affordable (compared to Western countries) treatment packages directly to Nigerians.
The collective impact of this medical tourism is a significant drain on Nigeria's foreign exchange reserves (estimated to be billions of dollars annually), a disincentive for investment in local healthcare, and a perpetuation of a system where those who can afford it simply bypass local services, undermining efforts to improve the domestic health sector for the general populace.
3 months ago
Focus Nigeria-
Should education be completely free and compulsory until a certain level?
The question of whether education should be completely free and compulsory up to a certain level is a widely debated topic, but the consensus among international human rights bodies and most developed and many developing nations is a resounding "yes" for at least primary education, and increasingly for secondary education.
Here's a breakdown of the arguments for and against, and the general global trend:
Arguments for Free and Compulsory Education (Up to a Certain Level):
Human Right: International human rights law, enshrined in documents like the Universal Declaration of Human Rights and the International Covenant on Economic, Social and Cultural Rights (ICESCR), recognizes education as a fundamental human right.
Primary education is explicitly stated as needing to be compulsory and free, with secondary and higher education progressively made free.
Increased Access and Equity:
Breaks the Cycle of Poverty: Financial barriers are a major reason why children, especially from low-income families, do not attend school. Free education removes these barriers, allowing all children, regardless of socioeconomic background, to access learning opportunities.
Reduces Inequalities: It helps to level the playing field, giving marginalized groups (girls, rural children, minorities) a better chance at education and future opportunities.
Societal Benefits:
Economic Growth: A more educated populace leads to a more skilled workforce, higher productivity, increased innovation, and greater economic competitiveness. Educated citizens are more likely to find employment, earn higher wages, and contribute more taxes, stimulating the economy.
Improved Health Outcomes: Educated individuals (especially women) tend to make more informed health decisions, leading to better public health outcomes, lower child mortality rates, and improved maternal health.
Reduced Crime and Social Stability: Education is correlated with lower crime rates. It fosters critical thinking, civic responsibility, and social cohesion, contributing to a more stable and peaceful society.
Active Citizenship: An educated populace is more likely to be engaged in civic life, understand their rights, and hold their leaders accountable, strengthening democratic institutions.
Child Protection: Compulsory education keeps children in schools and out of exploitative labor, reducing child labor and protecting them from harmful practices like early marriage.
National Development: Education is a cornerstone of sustainable national development across all sectors – agriculture, health, technology, governance, etc.
Arguments Against (or Challenges to) Fully Free and Compulsory Education:
Financial Burden on Governments: Providing truly free and quality education for all is incredibly expensive. It requires massive public investment in infrastructure, teacher salaries, learning materials, and technology. This is a significant challenge for developing countries with limited tax bases.
Quality Concerns:
Overcrowding: If not managed properly, universal free education can lead to overcrowded classrooms, diluting the quality of instruction.
Resource Strain: Spreading limited resources across a much larger student population can lead to inadequate supplies, poor facilities, and overworked teachers.
Reduced Accountability (Perceived): Some argue that if education is free, students might take it less seriously, and parents might be less invested, potentially leading to lower academic performance. However, this is often debated and depends heavily on the quality of the system.
Opportunity Costs for Families:
Even if tuition is free, there are indirect costs (uniforms, books, transport, food). For very poor families, the opportunity cost of sending a child to school (i.e., the income the child could have earned) can still be a significant barrier.
Curriculum Relevance (if not updated): Making education compulsory without ensuring its relevance to the job market or societal needs can lead to graduates who are educated but still unemployable, creating frustration.
Global Trend and Conclusion:
Globally, almost all countries have laws for compulsory education, and a significant majority provide free primary education. There's a growing trend towards making secondary education free and compulsory as well, recognizing its increasing importance in a knowledge-based economy. For instance, India's National Education Policy 2020 aims to make education free and compulsory for children aged 3 to 18.
For Nigeria, the argument for making education completely free and compulsory until a certain level (at least up to senior secondary school) is overwhelmingly strong.
It is not just an aspiration but a fundamental necessity for social equity, economic development, and national stability. The challenges, primarily funding and quality control, are significant but must be overcome.
These are investments that yield substantial long-term returns in human capital and national prosperity. The current system where primary education is nominally free but plagued by hidden costs, and secondary education often carries fees, still leaves millions of children out of school and perpetuates cycles of poverty and inequality.
Should education be completely free and compulsory until a certain level?
The question of whether education should be completely free and compulsory up to a certain level is a widely debated topic, but the consensus among international human rights bodies and most developed and many developing nations is a resounding "yes" for at least primary education, and increasingly for secondary education.
Here's a breakdown of the arguments for and against, and the general global trend:
Arguments for Free and Compulsory Education (Up to a Certain Level):
Human Right: International human rights law, enshrined in documents like the Universal Declaration of Human Rights and the International Covenant on Economic, Social and Cultural Rights (ICESCR), recognizes education as a fundamental human right.
Primary education is explicitly stated as needing to be compulsory and free, with secondary and higher education progressively made free.
Increased Access and Equity:
Breaks the Cycle of Poverty: Financial barriers are a major reason why children, especially from low-income families, do not attend school. Free education removes these barriers, allowing all children, regardless of socioeconomic background, to access learning opportunities.
Reduces Inequalities: It helps to level the playing field, giving marginalized groups (girls, rural children, minorities) a better chance at education and future opportunities.
Societal Benefits:
Economic Growth: A more educated populace leads to a more skilled workforce, higher productivity, increased innovation, and greater economic competitiveness. Educated citizens are more likely to find employment, earn higher wages, and contribute more taxes, stimulating the economy.
Improved Health Outcomes: Educated individuals (especially women) tend to make more informed health decisions, leading to better public health outcomes, lower child mortality rates, and improved maternal health.
Reduced Crime and Social Stability: Education is correlated with lower crime rates. It fosters critical thinking, civic responsibility, and social cohesion, contributing to a more stable and peaceful society.
Active Citizenship: An educated populace is more likely to be engaged in civic life, understand their rights, and hold their leaders accountable, strengthening democratic institutions.
Child Protection: Compulsory education keeps children in schools and out of exploitative labor, reducing child labor and protecting them from harmful practices like early marriage.
National Development: Education is a cornerstone of sustainable national development across all sectors – agriculture, health, technology, governance, etc.
Arguments Against (or Challenges to) Fully Free and Compulsory Education:
Financial Burden on Governments: Providing truly free and quality education for all is incredibly expensive. It requires massive public investment in infrastructure, teacher salaries, learning materials, and technology. This is a significant challenge for developing countries with limited tax bases.
Quality Concerns:
Overcrowding: If not managed properly, universal free education can lead to overcrowded classrooms, diluting the quality of instruction.
Resource Strain: Spreading limited resources across a much larger student population can lead to inadequate supplies, poor facilities, and overworked teachers.
Reduced Accountability (Perceived): Some argue that if education is free, students might take it less seriously, and parents might be less invested, potentially leading to lower academic performance. However, this is often debated and depends heavily on the quality of the system.
Opportunity Costs for Families:
Even if tuition is free, there are indirect costs (uniforms, books, transport, food). For very poor families, the opportunity cost of sending a child to school (i.e., the income the child could have earned) can still be a significant barrier.
Curriculum Relevance (if not updated): Making education compulsory without ensuring its relevance to the job market or societal needs can lead to graduates who are educated but still unemployable, creating frustration.
Global Trend and Conclusion:
Globally, almost all countries have laws for compulsory education, and a significant majority provide free primary education. There's a growing trend towards making secondary education free and compulsory as well, recognizing its increasing importance in a knowledge-based economy. For instance, India's National Education Policy 2020 aims to make education free and compulsory for children aged 3 to 18.
For Nigeria, the argument for making education completely free and compulsory until a certain level (at least up to senior secondary school) is overwhelmingly strong.
It is not just an aspiration but a fundamental necessity for social equity, economic development, and national stability. The challenges, primarily funding and quality control, are significant but must be overcome.
These are investments that yield substantial long-term returns in human capital and national prosperity. The current system where primary education is nominally free but plagued by hidden costs, and secondary education often carries fees, still leaves millions of children out of school and perpetuates cycles of poverty and inequality.
3 months ago
Focus Africa-
Are we importing goods—or exporting our future potential and human capital?
We are effectively exporting our future potential and human capital by heavily relying on imports.
While we get affordable goods in the short term, the long-term consequences of a shrinking industrial base and limited opportunities for our youth are a significant and often overlooked cost.
Exporting Future Potential-
Importing goods on a massive scale directly undermines a nation's ability to develop its own industrial capacity.
When local manufacturers cannot compete with cheap foreign products, factories close, and the chance to build a diversified, self-sufficient economy is lost.
This isn't just about selling a product; it's about the entire ecosystem of innovation and development that disappears with it. The nation's potential to become a creator and a producer is sacrificed for the immediate benefit of low consumer prices.
Exporting Human Capital-
A lack of local industries means there are fewer opportunities for young people to acquire valuable skills and build careers in manufacturing, engineering, and technology.
Instead of becoming engineers and entrepreneurs, a significant portion of the youth may be limited to jobs in retail, sales, or the informal sector, which offer less potential for career growth and wealth creation.
The result is a brain drain, where talented individuals may leave the country in search of better opportunities. By failing to create a robust local economy, we are essentially forcing our most talented and ambitious citizens to build the economies of other nations.
Are we importing goods—or exporting our future potential and human capital?
We are effectively exporting our future potential and human capital by heavily relying on imports.
While we get affordable goods in the short term, the long-term consequences of a shrinking industrial base and limited opportunities for our youth are a significant and often overlooked cost.
Exporting Future Potential-
Importing goods on a massive scale directly undermines a nation's ability to develop its own industrial capacity.
When local manufacturers cannot compete with cheap foreign products, factories close, and the chance to build a diversified, self-sufficient economy is lost.
This isn't just about selling a product; it's about the entire ecosystem of innovation and development that disappears with it. The nation's potential to become a creator and a producer is sacrificed for the immediate benefit of low consumer prices.
Exporting Human Capital-
A lack of local industries means there are fewer opportunities for young people to acquire valuable skills and build careers in manufacturing, engineering, and technology.
Instead of becoming engineers and entrepreneurs, a significant portion of the youth may be limited to jobs in retail, sales, or the informal sector, which offer less potential for career growth and wealth creation.
The result is a brain drain, where talented individuals may leave the country in search of better opportunities. By failing to create a robust local economy, we are essentially forcing our most talented and ambitious citizens to build the economies of other nations.
3 months ago
What percentage of our national budget or consumer goods is spent on imports, and what’s the hidden cost?
There isn't a single, universally applicable percentage for the amount of a national budget or consumer spending dedicated to imports, as this varies drastically by country and is influenced by a nation's size, economic structure, and trade policies. For example, some data from the U.S. suggests that around 10-11% of personal consumer spending can be traced to imported goods, but this figure includes a complex mix of finished products and imported components used in domestic manufacturing.
The hidden costs of this over-reliance on imports are substantial and go far beyond the price tag of a single product.
The Hidden Costs of Over-Importation
The true cost of a reliance on imports isn't just the money spent, but the long-term damage to a country's economic and strategic health.
Decline of Local Industries: The most significant hidden cost is the erosion of domestic manufacturing. Cheap imports often make it impossible for local producers to compete on price, leading to factory closures, job losses, and the loss of critical skills and expertise. This stunts a nation's ability to innovate and diversify its economy, trapping it in a cycle of dependency.
Increased Economic Vulnerability: An over-reliance on imports makes a country's supply chains fragile and susceptible to external shocks. A global pandemic, geopolitical conflict, or trade dispute could disrupt the flow of essential goods, such as food, medical supplies, or technology components, with severe consequences for the economy and national security.
Currency Depreciation and Inflation: A trade deficit, where a country imports more than it exports, puts downward pressure on its currency. To pay for more imports, the country needs to sell more of its own currency to buy foreign currency. This increases the supply of the local currency and drives down its value. A weaker currency then makes all imports, including raw materials for local producers, more expensive, leading to imported inflation that hurts consumers' purchasing power.
Reduced National Sovereignty: Long-term economic dependence on a few key trading partners can be used as a form of leverage. A dependent nation may be pressured to align its foreign policy with its suppliers' interests to avoid trade sanctions or embargos. This compromises a country's ability to act independently on the global stage.
There isn't a single, universally applicable percentage for the amount of a national budget or consumer spending dedicated to imports, as this varies drastically by country and is influenced by a nation's size, economic structure, and trade policies. For example, some data from the U.S. suggests that around 10-11% of personal consumer spending can be traced to imported goods, but this figure includes a complex mix of finished products and imported components used in domestic manufacturing.
The hidden costs of this over-reliance on imports are substantial and go far beyond the price tag of a single product.
The Hidden Costs of Over-Importation
The true cost of a reliance on imports isn't just the money spent, but the long-term damage to a country's economic and strategic health.
Decline of Local Industries: The most significant hidden cost is the erosion of domestic manufacturing. Cheap imports often make it impossible for local producers to compete on price, leading to factory closures, job losses, and the loss of critical skills and expertise. This stunts a nation's ability to innovate and diversify its economy, trapping it in a cycle of dependency.
Increased Economic Vulnerability: An over-reliance on imports makes a country's supply chains fragile and susceptible to external shocks. A global pandemic, geopolitical conflict, or trade dispute could disrupt the flow of essential goods, such as food, medical supplies, or technology components, with severe consequences for the economy and national security.
Currency Depreciation and Inflation: A trade deficit, where a country imports more than it exports, puts downward pressure on its currency. To pay for more imports, the country needs to sell more of its own currency to buy foreign currency. This increases the supply of the local currency and drives down its value. A weaker currency then makes all imports, including raw materials for local producers, more expensive, leading to imported inflation that hurts consumers' purchasing power.
Reduced National Sovereignty: Long-term economic dependence on a few key trading partners can be used as a form of leverage. A dependent nation may be pressured to align its foreign policy with its suppliers' interests to avoid trade sanctions or embargos. This compromises a country's ability to act independently on the global stage.
3 months ago
Data, Dollars, and Drones: Who Controls Tomorrow’s Tools?
“He who controls the data, programs the future. He who owns the drones, defends—or dictates—it. And he who prints the dollars, plays God with the global economy.”
The 21st century won’t be ruled by empires of land—it will be ruled by empires of data, capital, and surveillance technology. In this new world, algorithms shape minds, money moves faster than people, and drones fly where diplomacy dares not go.
But who truly owns these tools? Who benefits? And who is being left behind—or watched from above?
Data: The New Oil or the New Chains?
4.6 billion people are now online—most on mobile phones
Africa contributes a massive stream of digital behavior—but stores little of it locally
American and Chinese tech giants own 90% of global data traffic and storage
While data is harvested from Africa, Latin America, and Southeast Asia, it’s analyzed in Silicon Valley, processed in Shenzhen, and monetized without consent.
“We are not just users—we are the unpaid labor feeding AI.”
Even worse: data colonialism is rising—where nations are reduced to mere sources of behavioral raw material.
Dollars: Still King of a Decaying Kingdom
Despite talk of "de-dollarization":
The US dollar dominates 88% of global trade
Countries like Ghana, Pakistan, and Sri Lanka still face currency collapse based on Fed decisions
Dollar scarcity creates austerity, debt dependency, and policy handcuffs for many Global South nations
The IMF and World Bank, still largely Western-controlled, act as gatekeepers to emergency funds—often in exchange for structural reforms that weaken local industries and sovereignty.
“When Washington sneezes, African currencies catch pneumonia.”
Meanwhile, crypto and fintechs try to provide escape routes—but they face crackdowns or co-option.
Drones: From Warfare to Watchdogs
Once a futuristic fantasy, drones are now:
Weapons in proxy wars (Libya, Ethiopia, Ukraine)
Surveillance tools for regimes monitoring protests
Delivery agents for aid and vaccines in hard-to-reach zones
Business tools for agriculture and logistics
But who owns the skies?
China’s DJI controls over 70% of the global commercial drone market
US and Israeli military drones dominate combat zones
African countries import rather than manufacture—despite strong use cases
Drones may save lives—or spy on them. Liberate farmers—or be used to suppress dissent.
Who’s Really in Control?
Let’s break it down:
Tool Controlled By Impact on Global South
Data Big Tech (US, China) Extracted, not owned
Dollars US Federal Reserve Externalized pain
Drones China, US, Israel Imported, rarely made
In all three, the Global South is a consumer, not a controller. And Africa, in particular, risks becoming the testing ground, resource mine, and data farm for tomorrow’s tech empires.
The Risks of Dependency
Surveillance authoritarianism (via foreign-built tech)
Digital dictatorships (where information flow is centralized)
Economic instability (due to external financial control)
Policy blackmail (based on foreign data or financial leverage)
If tomorrow’s tools are not domestically owned or ethically governed, Africa and other regions may end up technologically colonized—even as they go digital.
What Can Be Done?
-Data Sovereignty
-Build local data centers
-Enact data protection laws
Push for digital commons and open-source alternatives
Financial Autonomy
Explore pan-African payment systems and stable coins
Create sovereign wealth tech funds
Reduce dependency on external aid tied to conditionalities
Drone & Tech Manufacturing
Invest in STEM education and hardware innovation
Support tech hubs and partnerships with ethical manufacturers
Use drones for development, not just surveillance
Conclusion: Tools Are Not Neutral
Data, dollars, and drones will define this century. But they are not just neutral instruments—they are extensions of power, control, and ideology.
Africa and the rest of the Global South must ask:
Will we own the tools of tomorrow—or be owned by them?
This is not just a tech question.
It’s a question of sovereignty, freedom, and the shape of the future.
“He who controls the data, programs the future. He who owns the drones, defends—or dictates—it. And he who prints the dollars, plays God with the global economy.”
The 21st century won’t be ruled by empires of land—it will be ruled by empires of data, capital, and surveillance technology. In this new world, algorithms shape minds, money moves faster than people, and drones fly where diplomacy dares not go.
But who truly owns these tools? Who benefits? And who is being left behind—or watched from above?
Data: The New Oil or the New Chains?
4.6 billion people are now online—most on mobile phones
Africa contributes a massive stream of digital behavior—but stores little of it locally
American and Chinese tech giants own 90% of global data traffic and storage
While data is harvested from Africa, Latin America, and Southeast Asia, it’s analyzed in Silicon Valley, processed in Shenzhen, and monetized without consent.
“We are not just users—we are the unpaid labor feeding AI.”
Even worse: data colonialism is rising—where nations are reduced to mere sources of behavioral raw material.
Dollars: Still King of a Decaying Kingdom
Despite talk of "de-dollarization":
The US dollar dominates 88% of global trade
Countries like Ghana, Pakistan, and Sri Lanka still face currency collapse based on Fed decisions
Dollar scarcity creates austerity, debt dependency, and policy handcuffs for many Global South nations
The IMF and World Bank, still largely Western-controlled, act as gatekeepers to emergency funds—often in exchange for structural reforms that weaken local industries and sovereignty.
“When Washington sneezes, African currencies catch pneumonia.”
Meanwhile, crypto and fintechs try to provide escape routes—but they face crackdowns or co-option.
Drones: From Warfare to Watchdogs
Once a futuristic fantasy, drones are now:
Weapons in proxy wars (Libya, Ethiopia, Ukraine)
Surveillance tools for regimes monitoring protests
Delivery agents for aid and vaccines in hard-to-reach zones
Business tools for agriculture and logistics
But who owns the skies?
China’s DJI controls over 70% of the global commercial drone market
US and Israeli military drones dominate combat zones
African countries import rather than manufacture—despite strong use cases
Drones may save lives—or spy on them. Liberate farmers—or be used to suppress dissent.
Who’s Really in Control?
Let’s break it down:
Tool Controlled By Impact on Global South
Data Big Tech (US, China) Extracted, not owned
Dollars US Federal Reserve Externalized pain
Drones China, US, Israel Imported, rarely made
In all three, the Global South is a consumer, not a controller. And Africa, in particular, risks becoming the testing ground, resource mine, and data farm for tomorrow’s tech empires.
The Risks of Dependency
Surveillance authoritarianism (via foreign-built tech)
Digital dictatorships (where information flow is centralized)
Economic instability (due to external financial control)
Policy blackmail (based on foreign data or financial leverage)
If tomorrow’s tools are not domestically owned or ethically governed, Africa and other regions may end up technologically colonized—even as they go digital.
What Can Be Done?
-Data Sovereignty
-Build local data centers
-Enact data protection laws
Push for digital commons and open-source alternatives
Financial Autonomy
Explore pan-African payment systems and stable coins
Create sovereign wealth tech funds
Reduce dependency on external aid tied to conditionalities
Drone & Tech Manufacturing
Invest in STEM education and hardware innovation
Support tech hubs and partnerships with ethical manufacturers
Use drones for development, not just surveillance
Conclusion: Tools Are Not Neutral
Data, dollars, and drones will define this century. But they are not just neutral instruments—they are extensions of power, control, and ideology.
Africa and the rest of the Global South must ask:
Will we own the tools of tomorrow—or be owned by them?
This is not just a tech question.
It’s a question of sovereignty, freedom, and the shape of the future.
3 months ago
How has North Korea allegedly used cybercrime (crypto theft, ransomware) to fund its regime?
North Korea has allegedly leveraged cybercrime, particularly cryptocurrency theft and ransomware, as a crucial and increasingly preferred method to fund its regime and, specifically, its illicit weapons programs.
This strategy is a direct response to the crippling international sanctions imposed on the country.
Here's how they've allegedly done it:
1. Circumventing Sanctions for Hard Currency:
Financial Isolation: North Korea faces severe international sanctions that cut off its access to traditional global financial systems. This makes it extremely difficult for the regime to acquire the foreign currency (like U.S. dollars or Euros) needed to import goods, technology, and components for its military and luxury items for its elite.
Cryptocurrency as an Alternative: Cryptocurrencies operate largely outside traditional banking regulations and centralized financial institutions. This makes them an attractive alternative for a sanctioned state. By stealing crypto, North Korea effectively generates hard currency that is harder to trace and block.
Funding WMD Programs: UN reports, U.S. government assessments, and cybersecurity firm analyses consistently state that the proceeds from these cybercrimes directly fund North Korea's prohibited weapons of mass destruction (WMD) programs, including nuclear weapons and ballistic missiles. Some estimates suggest cybercrime accounts for a significant portion, potentially 40% to 50% or more, of the regime's foreign currency income.
2. Cryptocurrency Theft: The Primary Goldmine
Massive Scale: North Korean hacking groups, notably the Lazarus Group and its sub-units like BlueNoroff, have stolen billions of dollars in cryptocurrency. For example, UN experts reported investigating 58 suspected North Korean cyberattacks between 2017 and 2023, valued at approximately $3 billion. The FBI recently attributed a single $1.5 billion hack against Bybit in February 2025 to North Korean actors.
Targeting Crypto Exchanges and DeFi Platforms:
Direct Hacks: They target centralized cryptocurrency exchanges, exploiting vulnerabilities in their security systems to steal large amounts of various cryptocurrencies.
Decentralized Finance (DeFi) Exploits: As the crypto landscape evolved, North Korean hackers shifted to more vulnerable DeFi platforms and "bridges" (which facilitate asset transfer between different blockchains). Notorious examples include the Harmony Horizon Bridge ($100 million+) and the Sky Mavis Ronin Bridge ($600 million+). DeFi platforms often have less stringent security and regulatory oversight, making them "softer targets."
Sophisticated Social Engineering: They employ elaborate social engineering tactics to gain initial access:
Fake Job Offers: Creating fake companies, LinkedIn profiles, and seemingly legitimate job opportunities to trick employees of crypto firms into downloading malicious software or revealing credentials.
Impersonation: Impersonating venture capitalists, recruiters, or other legitimate business contacts.
Deepfake Technology: Increasingly, they use AI-enabled deepfake technologies in video calls to disguise their appearance and build trust with targets.
Laundering Stolen Funds: After stealing the cryptocurrency, they employ sophisticated laundering techniques to convert it into fiat currency (like USD). This involves:
Mixing Services: Using "crypto mixers" like Tornado Cash (which was sanctioned by the U.S. Treasury for its role in laundering North Korean funds) to obscure the origin of the stolen assets.
Chain Hopping: Moving funds across multiple different blockchains to complicate tracing efforts.
Dispersing Funds: Spreading stolen assets across thousands of addresses to make tracking harder.
Conversion to Fiat: Eventually converting the "cleaned" crypto into traditional currencies through various brokers, often in countries with weaker anti-money laundering regulations.
3. Ransomware Attacks: Another Revenue Stream
Extortion and Disruption: Groups like Andariel, a Lazarus sub-group, have deployed ransomware (e.g., Maui ransomware) against a range of targets, including U.S. hospitals and healthcare providers.
Demanding Crypto Payments: Ransomware payments are typically demanded in cryptocurrency, providing another direct avenue for generating funds that are difficult to trace.
Double Extortion: Beyond just encrypting data, some groups engage in "double extortion," threatening to leak stolen sensitive data if the ransom isn't paid, increasing pressure on victims.
4. Illicit IT Worker Schemes:
While not strictly "cybercrime" in the hacking sense, this is a related and significant revenue stream that leverages North Korea's cyber talent.
Disguised Workers: North Korean IT workers, often highly skilled in programming and software development, fraudulently obtain remote freelance jobs globally, using false identities and documentation.
Funneling Wages: The wages earned from these legitimate-looking jobs are then funneled back to the North Korean regime, providing another source of foreign currency. Some reports indicate these workers also insert backdoors or malware into corporate systems they work on, potentially enabling future cybercrime or espionage.
In essence, North Korea has become an innovator in state-sponsored cybercrime out of necessity. Facing stringent sanctions, its regime has adapted by exploiting the nascent and less-regulated cryptocurrency ecosystem to generate a consistent and substantial stream of revenue, directly funding its strategic weapons programs and circumventing international efforts to curb its proliferation activities.
North Korea has allegedly leveraged cybercrime, particularly cryptocurrency theft and ransomware, as a crucial and increasingly preferred method to fund its regime and, specifically, its illicit weapons programs.
This strategy is a direct response to the crippling international sanctions imposed on the country.
Here's how they've allegedly done it:
1. Circumventing Sanctions for Hard Currency:
Financial Isolation: North Korea faces severe international sanctions that cut off its access to traditional global financial systems. This makes it extremely difficult for the regime to acquire the foreign currency (like U.S. dollars or Euros) needed to import goods, technology, and components for its military and luxury items for its elite.
Cryptocurrency as an Alternative: Cryptocurrencies operate largely outside traditional banking regulations and centralized financial institutions. This makes them an attractive alternative for a sanctioned state. By stealing crypto, North Korea effectively generates hard currency that is harder to trace and block.
Funding WMD Programs: UN reports, U.S. government assessments, and cybersecurity firm analyses consistently state that the proceeds from these cybercrimes directly fund North Korea's prohibited weapons of mass destruction (WMD) programs, including nuclear weapons and ballistic missiles. Some estimates suggest cybercrime accounts for a significant portion, potentially 40% to 50% or more, of the regime's foreign currency income.
2. Cryptocurrency Theft: The Primary Goldmine
Massive Scale: North Korean hacking groups, notably the Lazarus Group and its sub-units like BlueNoroff, have stolen billions of dollars in cryptocurrency. For example, UN experts reported investigating 58 suspected North Korean cyberattacks between 2017 and 2023, valued at approximately $3 billion. The FBI recently attributed a single $1.5 billion hack against Bybit in February 2025 to North Korean actors.
Targeting Crypto Exchanges and DeFi Platforms:
Direct Hacks: They target centralized cryptocurrency exchanges, exploiting vulnerabilities in their security systems to steal large amounts of various cryptocurrencies.
Decentralized Finance (DeFi) Exploits: As the crypto landscape evolved, North Korean hackers shifted to more vulnerable DeFi platforms and "bridges" (which facilitate asset transfer between different blockchains). Notorious examples include the Harmony Horizon Bridge ($100 million+) and the Sky Mavis Ronin Bridge ($600 million+). DeFi platforms often have less stringent security and regulatory oversight, making them "softer targets."
Sophisticated Social Engineering: They employ elaborate social engineering tactics to gain initial access:
Fake Job Offers: Creating fake companies, LinkedIn profiles, and seemingly legitimate job opportunities to trick employees of crypto firms into downloading malicious software or revealing credentials.
Impersonation: Impersonating venture capitalists, recruiters, or other legitimate business contacts.
Deepfake Technology: Increasingly, they use AI-enabled deepfake technologies in video calls to disguise their appearance and build trust with targets.
Laundering Stolen Funds: After stealing the cryptocurrency, they employ sophisticated laundering techniques to convert it into fiat currency (like USD). This involves:
Mixing Services: Using "crypto mixers" like Tornado Cash (which was sanctioned by the U.S. Treasury for its role in laundering North Korean funds) to obscure the origin of the stolen assets.
Chain Hopping: Moving funds across multiple different blockchains to complicate tracing efforts.
Dispersing Funds: Spreading stolen assets across thousands of addresses to make tracking harder.
Conversion to Fiat: Eventually converting the "cleaned" crypto into traditional currencies through various brokers, often in countries with weaker anti-money laundering regulations.
3. Ransomware Attacks: Another Revenue Stream
Extortion and Disruption: Groups like Andariel, a Lazarus sub-group, have deployed ransomware (e.g., Maui ransomware) against a range of targets, including U.S. hospitals and healthcare providers.
Demanding Crypto Payments: Ransomware payments are typically demanded in cryptocurrency, providing another direct avenue for generating funds that are difficult to trace.
Double Extortion: Beyond just encrypting data, some groups engage in "double extortion," threatening to leak stolen sensitive data if the ransom isn't paid, increasing pressure on victims.
4. Illicit IT Worker Schemes:
While not strictly "cybercrime" in the hacking sense, this is a related and significant revenue stream that leverages North Korea's cyber talent.
Disguised Workers: North Korean IT workers, often highly skilled in programming and software development, fraudulently obtain remote freelance jobs globally, using false identities and documentation.
Funneling Wages: The wages earned from these legitimate-looking jobs are then funneled back to the North Korean regime, providing another source of foreign currency. Some reports indicate these workers also insert backdoors or malware into corporate systems they work on, potentially enabling future cybercrime or espionage.
In essence, North Korea has become an innovator in state-sponsored cybercrime out of necessity. Facing stringent sanctions, its regime has adapted by exploiting the nascent and less-regulated cryptocurrency ecosystem to generate a consistent and substantial stream of revenue, directly funding its strategic weapons programs and circumventing international efforts to curb its proliferation activities.
3 months ago
How can Nigeria make quality education more accessible in rural areas?
Making quality education more accessible in rural areas of Nigeria is a complex undertaking that requires a holistic and sustained approach, addressing issues across infrastructure, human resources, technology, community engagement, and funding.
Here's how it can be achieved:
I. Infrastructure and Facilities Development:
Context-Specific School Construction and Renovation:
Durable & Local Materials: Build and renovate school buildings using durable, locally sourced, and climate-appropriate materials. Designs should consider natural lighting and ventilation.
Essential Amenities: Ensure all schools have basic facilities: clean and functional toilets (separate for boys and girls), access to clean water, reliable electricity (solar power is a viable option), and proper ventilation.
Flexible Learning Spaces: Create adaptable classrooms that can accommodate different learning styles and potentially multi-grade teaching, which is common in smaller rural schools.
Libraries and Labs: Equip schools with functional libraries and basic science/computer laboratories. These can be shared resources among clusters of schools.
Mobile and Satellite Learning Centers:
For extremely remote or sparsely populated areas, explore mobile classrooms or "learning hubs" that rotate among communities, or satellite learning centers that provide access to digital resources and connectivity.
II. Qualified and Motivated Teachers:
Incentives for Rural Deployment:
Improved Remuneration: Offer attractive salary packages, allowances, and hardship pay for teachers willing to serve in rural areas.
Housing and Utilities: Provide subsidized or free housing, access to reliable electricity, and potable water to make rural living more appealing.
Career Advancement Opportunities: Create clear pathways for career progression for rural teachers, linked to performance and continuous professional development.
Loan Forgiveness/Scholarships: Offer student loan forgiveness or scholarships to aspiring teachers who commit to serving in rural schools for a specified period.
Targeted Recruitment and Training:
Local Recruitment: Prioritize recruiting teachers from within or near rural communities, as they are often more likely to stay due to existing ties.
Specialized Training: Equip teachers with skills for multi-grade teaching, differentiated instruction, and managing large classes. Training should also cover culturally sensitive pedagogy and community engagement.
Continuous Professional Development (CPD): Implement regular, accessible, and relevant CPD programs, utilizing blended learning models (online modules, local workshops) to reduce travel burdens.
Mentorship Programs: Pair experienced urban teachers with rural counterparts for mentorship and support.
III. Leveraging Technology (Bridging the Digital Divide):
Sustainable Power and Connectivity:
Solar Power: Prioritize equipping rural schools with reliable solar power systems to run computers, projectors, and charging stations.
Affordable Internet: Work with telecom providers and government agencies (e.g., NCC, NITDA) to extend affordable, reliable internet connectivity to rural areas, perhaps through community Wi-Fi hotspots or satellite internet.
Digital Learning Resources:
Tablets/E-readers: Provide students and teachers with rugged, low-cost tablets preloaded with digital textbooks, educational apps, and interactive learning content (e.g., "Solar-Powered Tablets").
Learning Management Systems (LMS): Implement simple LMS platforms that can deliver content offline and sync when connectivity is available.
Educational TV/Radio: Utilize existing media (radio, TV) to deliver curriculum-aligned lessons, especially in areas with limited internet access.
Teacher Digital Literacy Training:
Train teachers not just on how to use technology, but how to integrate it effectively into their pedagogy to enhance learning outcomes.
IV. Community Engagement and Ownership:
School-Based Management Committees (SBMCs):
Strengthen and empower SBMCs with genuine decision-making authority and training in financial management, school development planning, and monitoring.
Encourage active participation of parents, traditional leaders, and community members in school governance, resource mobilization, and monitoring teacher attendance and performance.
Community Contributions:
Foster a sense of community ownership by encouraging local contributions (labor, materials, financial support) for school development projects.
Integrate schools into community life, making them centers for community development, adult literacy programs, and health awareness.
Sensitization and Advocacy:
Conduct targeted campaigns to raise awareness among rural parents about the value of education, especially for girls, and discourage child labor or early marriage.
V. Funding and Policy:
Increased and Targeted Funding:
Higher Education Allocation: Significantly increase the overall budget allocation to education, ensuring a substantial portion is dedicated to rural school development and teacher welfare.
Specific Rural Education Fund: Establish a dedicated fund for rural education, managed transparently, to address unique challenges.
Public-Private Partnerships (PPPs): Encourage and incentivize private sector involvement through CSR initiatives, grants, and direct investment in rural schools.
Innovative Financing: Explore mechanisms like education bonds, diaspora engagement, and philanthropic partnerships to supplement government funding.
Flexible and Context-Specific Policies:
Local Curriculum Adaptation: Allow for some flexibility in curriculum delivery to address local contexts, needs, and cultural nuances, while maintaining national standards.
Remote Learning Policies: Develop clear policies for remote and blended learning that can be effectively deployed during emergencies or to support continuous learning.
Data-Driven Planning: Establish robust data collection and analysis systems to identify out-of-school children, monitor learning outcomes in rural areas, and allocate resources effectively based on needs.
Making quality education accessible in rural Nigeria requires sustained political will, a commitment to transparent resource utilization, and genuine collaboration among all stakeholders to overcome the geographical, economic, and social barriers.
Making quality education more accessible in rural areas of Nigeria is a complex undertaking that requires a holistic and sustained approach, addressing issues across infrastructure, human resources, technology, community engagement, and funding.
Here's how it can be achieved:
I. Infrastructure and Facilities Development:
Context-Specific School Construction and Renovation:
Durable & Local Materials: Build and renovate school buildings using durable, locally sourced, and climate-appropriate materials. Designs should consider natural lighting and ventilation.
Essential Amenities: Ensure all schools have basic facilities: clean and functional toilets (separate for boys and girls), access to clean water, reliable electricity (solar power is a viable option), and proper ventilation.
Flexible Learning Spaces: Create adaptable classrooms that can accommodate different learning styles and potentially multi-grade teaching, which is common in smaller rural schools.
Libraries and Labs: Equip schools with functional libraries and basic science/computer laboratories. These can be shared resources among clusters of schools.
Mobile and Satellite Learning Centers:
For extremely remote or sparsely populated areas, explore mobile classrooms or "learning hubs" that rotate among communities, or satellite learning centers that provide access to digital resources and connectivity.
II. Qualified and Motivated Teachers:
Incentives for Rural Deployment:
Improved Remuneration: Offer attractive salary packages, allowances, and hardship pay for teachers willing to serve in rural areas.
Housing and Utilities: Provide subsidized or free housing, access to reliable electricity, and potable water to make rural living more appealing.
Career Advancement Opportunities: Create clear pathways for career progression for rural teachers, linked to performance and continuous professional development.
Loan Forgiveness/Scholarships: Offer student loan forgiveness or scholarships to aspiring teachers who commit to serving in rural schools for a specified period.
Targeted Recruitment and Training:
Local Recruitment: Prioritize recruiting teachers from within or near rural communities, as they are often more likely to stay due to existing ties.
Specialized Training: Equip teachers with skills for multi-grade teaching, differentiated instruction, and managing large classes. Training should also cover culturally sensitive pedagogy and community engagement.
Continuous Professional Development (CPD): Implement regular, accessible, and relevant CPD programs, utilizing blended learning models (online modules, local workshops) to reduce travel burdens.
Mentorship Programs: Pair experienced urban teachers with rural counterparts for mentorship and support.
III. Leveraging Technology (Bridging the Digital Divide):
Sustainable Power and Connectivity:
Solar Power: Prioritize equipping rural schools with reliable solar power systems to run computers, projectors, and charging stations.
Affordable Internet: Work with telecom providers and government agencies (e.g., NCC, NITDA) to extend affordable, reliable internet connectivity to rural areas, perhaps through community Wi-Fi hotspots or satellite internet.
Digital Learning Resources:
Tablets/E-readers: Provide students and teachers with rugged, low-cost tablets preloaded with digital textbooks, educational apps, and interactive learning content (e.g., "Solar-Powered Tablets").
Learning Management Systems (LMS): Implement simple LMS platforms that can deliver content offline and sync when connectivity is available.
Educational TV/Radio: Utilize existing media (radio, TV) to deliver curriculum-aligned lessons, especially in areas with limited internet access.
Teacher Digital Literacy Training:
Train teachers not just on how to use technology, but how to integrate it effectively into their pedagogy to enhance learning outcomes.
IV. Community Engagement and Ownership:
School-Based Management Committees (SBMCs):
Strengthen and empower SBMCs with genuine decision-making authority and training in financial management, school development planning, and monitoring.
Encourage active participation of parents, traditional leaders, and community members in school governance, resource mobilization, and monitoring teacher attendance and performance.
Community Contributions:
Foster a sense of community ownership by encouraging local contributions (labor, materials, financial support) for school development projects.
Integrate schools into community life, making them centers for community development, adult literacy programs, and health awareness.
Sensitization and Advocacy:
Conduct targeted campaigns to raise awareness among rural parents about the value of education, especially for girls, and discourage child labor or early marriage.
V. Funding and Policy:
Increased and Targeted Funding:
Higher Education Allocation: Significantly increase the overall budget allocation to education, ensuring a substantial portion is dedicated to rural school development and teacher welfare.
Specific Rural Education Fund: Establish a dedicated fund for rural education, managed transparently, to address unique challenges.
Public-Private Partnerships (PPPs): Encourage and incentivize private sector involvement through CSR initiatives, grants, and direct investment in rural schools.
Innovative Financing: Explore mechanisms like education bonds, diaspora engagement, and philanthropic partnerships to supplement government funding.
Flexible and Context-Specific Policies:
Local Curriculum Adaptation: Allow for some flexibility in curriculum delivery to address local contexts, needs, and cultural nuances, while maintaining national standards.
Remote Learning Policies: Develop clear policies for remote and blended learning that can be effectively deployed during emergencies or to support continuous learning.
Data-Driven Planning: Establish robust data collection and analysis systems to identify out-of-school children, monitor learning outcomes in rural areas, and allocate resources effectively based on needs.
Making quality education accessible in rural Nigeria requires sustained political will, a commitment to transparent resource utilization, and genuine collaboration among all stakeholders to overcome the geographical, economic, and social barriers.
3 months ago
How can Nigeria bridge the gap between education and employable skills?
Bridging the gap between education and employable skills in Nigeria is a critical challenge that requires a holistic and multi-pronged approach involving government, educational institutions, the private sector, and civil society.
The current system often produces graduates ill-equipped for the demands of the modern job market, leading to high youth unemployment.
Here's how Nigeria can effectively bridge this gap:
I. Curriculum Reform & Relevance:
Industry-Driven Curriculum Development:
Regular Review & Updates: Curricula at all levels (primary, secondary, tertiary, and TVET) must be regularly reviewed and updated in close collaboration with industry experts, employers, and professional bodies. This ensures that what is taught aligns directly with the skills demanded by the job market.
Competency-Based Learning: Shift the focus from rote memorization and theoretical knowledge to competency-based education. This means assessing students on their ability to apply knowledge and skills to real-world problems.
Inclusion of 21st-Century Skills: Integrate critical thinking, problem-solving, creativity, communication, collaboration, digital literacy, and data analysis across all disciplines. These "soft skills" are highly valued by employers.
Emphasis on STEM and Digital Skills:
Strengthen Science, Technology, Engineering, and Mathematics (STEM) Education: Invest heavily in STEM education from an early age, ensuring adequate laboratories, equipment, and qualified teachers.
Digital Literacy: Make digital literacy a foundational skill across all levels of education. Introduce coding, data analytics, cybersecurity, and AI/Machine Learning at appropriate stages. Initiatives like NITDA's 3MTT (Three Million Technical Talent) are good starts but need massive scaling.
Mandatory Entrepreneurship Education:
Integrate practical entrepreneurship education into all tertiary curricula. This should go beyond theoretical concepts to include business plan development, mentorship, access to seed funding (even if small), and incubation support. The goal is to produce job creators, not just job seekers.
II. Strengthen Technical and Vocational Education and Training (TVET):
Rebranding and Destigmatization:
Launch nationwide campaigns to change the societal perception of TVET. Highlight successful TVET graduates, showcase the lucrative nature of skilled trades (e.g., plumbing, welding, carpentry, ICT repairs), and emphasize their vital role in economic development. Combat the notion that TVET is for "school dropouts."
Increased Investment and Modernization:
Adequately fund TVET institutions with modern tools, equipment, workshops, and technology that reflect current industry standards.
Upgrade and maintain existing polytechnics, technical colleges, and vocational centers.
Industry-Led TVET:
Ensure that TVET programs are directly developed and run in partnership with industries. Companies should be involved in curriculum design, practical training, and certification.
Promote apprenticeships and on-the-job training programs, where students learn practical skills directly in a workplace setting.
III. Enhance Industry-Academia Collaboration:
Structured Partnerships:
MOU and Joint Projects: Facilitate Memoranda of Understanding (MOUs) between universities/polytechnics and industries for joint research projects, curriculum development, and student internships.
Research & Development (R&D): Encourage industries to fund university research that addresses their specific needs and challenges, creating a symbiotic relationship.
Advisory Boards: Establish industry advisory boards for academic departments to provide direct input on curriculum, necessary skills, and emerging trends.
Internship and Apprenticeship Programs:
Make internships (Industrial Attachment) mandatory, well-structured, and adequately supervised. Ensure students gain relevant, hands-on experience that aligns with their studies.
Incentivize companies (e.g., through tax breaks) to offer quality internships and apprenticeships.
Guest Lecturers and Adjunct Faculty:
Invite industry professionals to serve as guest lecturers, adjunct faculty, or mentors, bringing real-world experience into the classroom.
IV. Teacher Training and Professional Development:-
Skills-Focused Pedagogy:
Train educators at all levels to adopt practical, problem-solving, and project-based teaching methodologies that foster skill development rather than rote learning.
Equip teachers with the skills to integrate technology effectively into their teaching.
Continuous Professional Development:
Provide ongoing training for teachers and lecturers to keep them updated on industry trends, new technologies, and modern pedagogical approaches.
Encourage lecturers to undertake sabbaticals in relevant industries to gain practical experience.
Industry Experience for Educators:
Implement programs that allow academic staff to spend time in relevant industries, gaining practical experience that they can then bring back to the classroom.
V. Leverage Technology and Digital Learning:
E-Learning Platforms:
Invest in robust e-learning platforms and digital resources to complement traditional classroom learning, making education more accessible and flexible.
Promote blended learning models that combine online and in-person instruction.
Access to ICT Infrastructure:
Address the challenges of internet connectivity and reliable power supply, especially in rural areas, to ensure equitable access to digital learning tools.
Provide affordable digital devices to students and educators.
Virtual Labs and Simulations:
Utilize virtual laboratories and simulation software to provide practical experience where physical equipment is limited or too expensive.
VI. Government Policies & Funding:
Increased and Targeted Funding:
Significantly increase the budget allocation to education, specifically earmarking funds for curriculum reform, TVET modernization, industry collaboration initiatives, and teacher training.
Ensure transparent and accountable use of these funds.
Policy Cohesion:
Develop a coherent national education policy that links educational outcomes directly to labor market needs, with clear implementation strategies and monitoring mechanisms.
Avoid frequent policy changes that disrupt progress.
Incentives for Private Sector Engagement:
Offer tax incentives, grants, or subsidies to private companies that invest in skills development, apprenticeships, or collaborate with educational institutions.
Strengthen Career Guidance & Counseling:
Implement effective career guidance and counseling services in schools and universities to help students make informed choices about their academic and career paths, aligning their interests with market demands.
By addressing these areas comprehensively, Nigeria can transform its educational system into a powerful engine for skill development, producing a workforce that is not only educated but also highly employable and capable of driving economic growth and innovation.
Bridging the gap between education and employable skills in Nigeria is a critical challenge that requires a holistic and multi-pronged approach involving government, educational institutions, the private sector, and civil society.
The current system often produces graduates ill-equipped for the demands of the modern job market, leading to high youth unemployment.
Here's how Nigeria can effectively bridge this gap:
I. Curriculum Reform & Relevance:
Industry-Driven Curriculum Development:
Regular Review & Updates: Curricula at all levels (primary, secondary, tertiary, and TVET) must be regularly reviewed and updated in close collaboration with industry experts, employers, and professional bodies. This ensures that what is taught aligns directly with the skills demanded by the job market.
Competency-Based Learning: Shift the focus from rote memorization and theoretical knowledge to competency-based education. This means assessing students on their ability to apply knowledge and skills to real-world problems.
Inclusion of 21st-Century Skills: Integrate critical thinking, problem-solving, creativity, communication, collaboration, digital literacy, and data analysis across all disciplines. These "soft skills" are highly valued by employers.
Emphasis on STEM and Digital Skills:
Strengthen Science, Technology, Engineering, and Mathematics (STEM) Education: Invest heavily in STEM education from an early age, ensuring adequate laboratories, equipment, and qualified teachers.
Digital Literacy: Make digital literacy a foundational skill across all levels of education. Introduce coding, data analytics, cybersecurity, and AI/Machine Learning at appropriate stages. Initiatives like NITDA's 3MTT (Three Million Technical Talent) are good starts but need massive scaling.
Mandatory Entrepreneurship Education:
Integrate practical entrepreneurship education into all tertiary curricula. This should go beyond theoretical concepts to include business plan development, mentorship, access to seed funding (even if small), and incubation support. The goal is to produce job creators, not just job seekers.
II. Strengthen Technical and Vocational Education and Training (TVET):
Rebranding and Destigmatization:
Launch nationwide campaigns to change the societal perception of TVET. Highlight successful TVET graduates, showcase the lucrative nature of skilled trades (e.g., plumbing, welding, carpentry, ICT repairs), and emphasize their vital role in economic development. Combat the notion that TVET is for "school dropouts."
Increased Investment and Modernization:
Adequately fund TVET institutions with modern tools, equipment, workshops, and technology that reflect current industry standards.
Upgrade and maintain existing polytechnics, technical colleges, and vocational centers.
Industry-Led TVET:
Ensure that TVET programs are directly developed and run in partnership with industries. Companies should be involved in curriculum design, practical training, and certification.
Promote apprenticeships and on-the-job training programs, where students learn practical skills directly in a workplace setting.
III. Enhance Industry-Academia Collaboration:
Structured Partnerships:
MOU and Joint Projects: Facilitate Memoranda of Understanding (MOUs) between universities/polytechnics and industries for joint research projects, curriculum development, and student internships.
Research & Development (R&D): Encourage industries to fund university research that addresses their specific needs and challenges, creating a symbiotic relationship.
Advisory Boards: Establish industry advisory boards for academic departments to provide direct input on curriculum, necessary skills, and emerging trends.
Internship and Apprenticeship Programs:
Make internships (Industrial Attachment) mandatory, well-structured, and adequately supervised. Ensure students gain relevant, hands-on experience that aligns with their studies.
Incentivize companies (e.g., through tax breaks) to offer quality internships and apprenticeships.
Guest Lecturers and Adjunct Faculty:
Invite industry professionals to serve as guest lecturers, adjunct faculty, or mentors, bringing real-world experience into the classroom.
IV. Teacher Training and Professional Development:-
Skills-Focused Pedagogy:
Train educators at all levels to adopt practical, problem-solving, and project-based teaching methodologies that foster skill development rather than rote learning.
Equip teachers with the skills to integrate technology effectively into their teaching.
Continuous Professional Development:
Provide ongoing training for teachers and lecturers to keep them updated on industry trends, new technologies, and modern pedagogical approaches.
Encourage lecturers to undertake sabbaticals in relevant industries to gain practical experience.
Industry Experience for Educators:
Implement programs that allow academic staff to spend time in relevant industries, gaining practical experience that they can then bring back to the classroom.
V. Leverage Technology and Digital Learning:
E-Learning Platforms:
Invest in robust e-learning platforms and digital resources to complement traditional classroom learning, making education more accessible and flexible.
Promote blended learning models that combine online and in-person instruction.
Access to ICT Infrastructure:
Address the challenges of internet connectivity and reliable power supply, especially in rural areas, to ensure equitable access to digital learning tools.
Provide affordable digital devices to students and educators.
Virtual Labs and Simulations:
Utilize virtual laboratories and simulation software to provide practical experience where physical equipment is limited or too expensive.
VI. Government Policies & Funding:
Increased and Targeted Funding:
Significantly increase the budget allocation to education, specifically earmarking funds for curriculum reform, TVET modernization, industry collaboration initiatives, and teacher training.
Ensure transparent and accountable use of these funds.
Policy Cohesion:
Develop a coherent national education policy that links educational outcomes directly to labor market needs, with clear implementation strategies and monitoring mechanisms.
Avoid frequent policy changes that disrupt progress.
Incentives for Private Sector Engagement:
Offer tax incentives, grants, or subsidies to private companies that invest in skills development, apprenticeships, or collaborate with educational institutions.
Strengthen Career Guidance & Counseling:
Implement effective career guidance and counseling services in schools and universities to help students make informed choices about their academic and career paths, aligning their interests with market demands.
By addressing these areas comprehensively, Nigeria can transform its educational system into a powerful engine for skill development, producing a workforce that is not only educated but also highly employable and capable of driving economic growth and innovation.
3 months ago
Is it possible to build quality local alternatives, and if so, what’s stopping us?
lt's absolutely possible to build quality local alternatives to cheap imports. What's stopping us is a combination of systemic barriers, policy gaps, and economic disadvantages that make it incredibly difficult for local industries to compete. The challenge isn't a lack of ability or ideas, but rather a lack of a strong enabling environment.
Key Barriers to Local Manufacturing
The primary reasons local industries struggle to take root and thrive can be grouped into several key areas:
Infrastructure Deficiencies: A fundamental issue is the lack of reliable and affordable infrastructure. In many places, manufacturers face frequent power outages, poor road and rail networks, and high logistics costs. These challenges make it more expensive and less efficient to produce and transport goods locally compared to importing finished products from countries with superior infrastructure.
Lack of Capital and Finance: Local businesses, especially small and medium-sized enterprises (SMEs), often have limited access to the large amounts of capital needed to build modern factories, purchase machinery, and invest in technology. Financial institutions may be hesitant to lend to new or smaller businesses, making it difficult to scale operations and achieve the economies of scale needed to compete on price with mass-produced imports.
Skills Gaps and Technology: African manufacturers often lag behind in technology adoption and have a shortage of skilled labor, particularly in technical and managerial roles. Without access to modern technology and a well-trained workforce, productivity remains low, and it's difficult to produce goods that meet international quality standards.
Policy and Regulatory Hurdles: While governments have a role to play, inconsistent or poorly implemented industrial policies can create a hostile environment for local businesses. This includes bureaucratic red tape, high taxes on raw materials, and a lack of harmonized trade regulations, which make it difficult for businesses to operate and trade across borders.
Competition from a Single Market: The fragmented nature of many local markets makes it hard for businesses to grow. The African Continental Free Trade Area (AfCFTA) is a step toward creating a larger, integrated market, but its full implementation is a work in progress. This fragmentation means local firms often don't have a large enough consumer base to justify the investment in mass production.
lt's absolutely possible to build quality local alternatives to cheap imports. What's stopping us is a combination of systemic barriers, policy gaps, and economic disadvantages that make it incredibly difficult for local industries to compete. The challenge isn't a lack of ability or ideas, but rather a lack of a strong enabling environment.
Key Barriers to Local Manufacturing
The primary reasons local industries struggle to take root and thrive can be grouped into several key areas:
Infrastructure Deficiencies: A fundamental issue is the lack of reliable and affordable infrastructure. In many places, manufacturers face frequent power outages, poor road and rail networks, and high logistics costs. These challenges make it more expensive and less efficient to produce and transport goods locally compared to importing finished products from countries with superior infrastructure.
Lack of Capital and Finance: Local businesses, especially small and medium-sized enterprises (SMEs), often have limited access to the large amounts of capital needed to build modern factories, purchase machinery, and invest in technology. Financial institutions may be hesitant to lend to new or smaller businesses, making it difficult to scale operations and achieve the economies of scale needed to compete on price with mass-produced imports.
Skills Gaps and Technology: African manufacturers often lag behind in technology adoption and have a shortage of skilled labor, particularly in technical and managerial roles. Without access to modern technology and a well-trained workforce, productivity remains low, and it's difficult to produce goods that meet international quality standards.
Policy and Regulatory Hurdles: While governments have a role to play, inconsistent or poorly implemented industrial policies can create a hostile environment for local businesses. This includes bureaucratic red tape, high taxes on raw materials, and a lack of harmonized trade regulations, which make it difficult for businesses to operate and trade across borders.
Competition from a Single Market: The fragmented nature of many local markets makes it hard for businesses to grow. The African Continental Free Trade Area (AfCFTA) is a step toward creating a larger, integrated market, but its full implementation is a work in progress. This fragmentation means local firms often don't have a large enough consumer base to justify the investment in mass production.
3 months ago
What incentives or policies could protect and grow local manufacturing in the face of cheap imports?
To protect and grow local manufacturing against cheap imports, governments can implement a mix of protectionist policies and incentives for domestic industries. These strategies aim to either make imports less competitive or boost the capabilities and competitiveness of local businesses.
Protectionist Policies
These policies directly address the challenge of low-priced imports by raising their cost or limiting their quantity.
Tariffs: A tariff is a tax on imported goods. By increasing the price of imports, tariffs make locally produced goods more attractive to consumers. Governments can use specific tariffs (a fixed fee per unit) or ad valorem tariffs (a percentage of the item's value).
Import Quotas: This is a non-tax barrier that sets a strict limit on the volume of a specific good that can be imported over a given period. Quotas reduce the supply of foreign goods, which drives up their price and creates a market for domestic producers to fill the gap.
Anti-Dumping Duties: "Dumping" occurs when a foreign company sells its products in an export market at a price below its production cost to gain market share. Governments can impose special tariffs, known as anti-dumping duties, on these goods to level the playing field and prevent predatory pricing that could destroy local industries.
Local Content Requirements: This policy mandates that a certain percentage of a product's components or labor must be sourced locally. This measure is often used in sectors like automotive manufacturing or electronics to build a domestic supply chain and foster related industries.
Incentives and Support for Local Industry
Beyond restricting imports, governments can also take proactive steps to make local businesses more competitive.
Subsidies and Financial Support: Governments can provide financial assistance to local manufacturers through cash grants, low-interest loans, or tax breaks. These subsidies help reduce the cost of production, making local products more affordable and competitive without directly raising consumer prices.
Investment in Infrastructure and Technology: Improving a nation's infrastructure, such as power grids, transportation networks, and ports, can significantly lower the operational costs for local businesses. Governments can also fund research and development or offer tax credits for businesses that invest in new technology to improve efficiency and productivity.
Export Promotion: Policies that support local firms in selling their products abroad can help them achieve economies of scale. This includes government-sponsored trade missions, export subsidies, and assistance with marketing and logistics. A larger market allows companies to grow, become more efficient, and better withstand foreign competition at home.
"Buy Local" Campaigns: These are public awareness campaigns that encourage consumers and government agencies to prioritize purchasing locally made goods. For example, a "Buy Local" program for government procurement can guarantee a steady market for domestic producers, providing a stable foundation for growth.
To protect and grow local manufacturing against cheap imports, governments can implement a mix of protectionist policies and incentives for domestic industries. These strategies aim to either make imports less competitive or boost the capabilities and competitiveness of local businesses.
Protectionist Policies
These policies directly address the challenge of low-priced imports by raising their cost or limiting their quantity.
Tariffs: A tariff is a tax on imported goods. By increasing the price of imports, tariffs make locally produced goods more attractive to consumers. Governments can use specific tariffs (a fixed fee per unit) or ad valorem tariffs (a percentage of the item's value).
Import Quotas: This is a non-tax barrier that sets a strict limit on the volume of a specific good that can be imported over a given period. Quotas reduce the supply of foreign goods, which drives up their price and creates a market for domestic producers to fill the gap.
Anti-Dumping Duties: "Dumping" occurs when a foreign company sells its products in an export market at a price below its production cost to gain market share. Governments can impose special tariffs, known as anti-dumping duties, on these goods to level the playing field and prevent predatory pricing that could destroy local industries.
Local Content Requirements: This policy mandates that a certain percentage of a product's components or labor must be sourced locally. This measure is often used in sectors like automotive manufacturing or electronics to build a domestic supply chain and foster related industries.
Incentives and Support for Local Industry
Beyond restricting imports, governments can also take proactive steps to make local businesses more competitive.
Subsidies and Financial Support: Governments can provide financial assistance to local manufacturers through cash grants, low-interest loans, or tax breaks. These subsidies help reduce the cost of production, making local products more affordable and competitive without directly raising consumer prices.
Investment in Infrastructure and Technology: Improving a nation's infrastructure, such as power grids, transportation networks, and ports, can significantly lower the operational costs for local businesses. Governments can also fund research and development or offer tax credits for businesses that invest in new technology to improve efficiency and productivity.
Export Promotion: Policies that support local firms in selling their products abroad can help them achieve economies of scale. This includes government-sponsored trade missions, export subsidies, and assistance with marketing and logistics. A larger market allows companies to grow, become more efficient, and better withstand foreign competition at home.
"Buy Local" Campaigns: These are public awareness campaigns that encourage consumers and government agencies to prioritize purchasing locally made goods. For example, a "Buy Local" program for government procurement can guarantee a steady market for domestic producers, providing a stable foundation for growth.
3 months ago
“Sky Is NOT The Limit”: Su-57, S-500, R-37M In Spotlight As IAF Thrilled By Super Success Of S-400 & BrahMos (Part2)
Let us look at the two Russia-origin systems.
S-400 Missile System “Sudarshan Chakra”
The S-400 is a Russian mobile SAM system developed in the 1990s by Russia’s NPO Almaz as an upgrade to the S-300 family of missiles.
The S-400 joined the Russian armed forces in 2007. The system is complemented by its successor, the S-500. The S-400 system has four radars and four sets of missiles covering different ranges and vertical bubbles.
The maximum target detection range is 600 kilometres, and targets can be engaged as far as 400 kilometres. The five S-400 batteries contracted by India in 2018 cost $5.43 billion, including reserve missiles.
All the sub-units are data-linked and controlled by a central command and control system with sufficient redundancy. The system is capable of layered defence and integrates with other Indian air defences.
One system can control 72 launchers, with a maximum of 384 missiles. All missiles are equipped with directed explosion warheads, which increases the probability of complete destruction of aerial targets.
The system is designed to destroy aircraft, cruise, and ballistic missiles, and can also be used against ground targets. It can engage targets up to 17,000 km/h or Mach 14. It can intercept low-flying cruise missiles at a range of about 40 km due to the line-of-sight requirement. The anti-ballistic missile (ABM) capabilities of the S-400 system are near the maximum allowed under the (now void) Anti-Ballistic Missile Treaty. The number of simultaneously engaged targets by the full system is 36.
The system ground mobility speed is close to 60 km/h on roads and 25 km/h cross-country. It takes 5 minutes to be operational and fire when ordered while driving. Otherwise, the system response time is just 10 seconds. The time between major overhauls is 10,000 hours. The Service life is at least 20 years.
In Russia, the system was made operational around Moscow in 2007. Russia reportedly deployed S-400 in Syria. The system has been widely used in the ongoing conflict in Ukraine, and it is claimed to have shot down many aircraft.
Meanwhile, Ukraine has reportedly used Western weapons, mainly U.S.-made ATACMS missiles, to hit S-400 units on the ground.
Belarus has unspecified numbers of S-400 units. Deliveries to China, of the six batteries ordered, began in January 2018. Four batteries consisting of 36 fire units and 192 or more missiles were delivered to Turkey.
Algeria is another operator. Some other countries, like Iran, Egypt, Iraq, and Serbia, have also shown interest. South Korea is developing the KM-SAM, a medium-range SAM system based on technology from S-400 missiles, with assistance from NPO Almaz.
Three of the five batteries have arrived in India. India took deliveries despite the American threat of CAATSA (Countering America’s Adversaries Through Sanctions Act).
The remaining two are expected in 2025/26. The recent conflict has revealed the rough location of two systems, one each in Punjab and Gujarat. As per open sources, the third is somewhere in the east. The systems have been tested in various Indian military exercises.
BrahMos
The BrahMos is a long-range ramjet supersonic cruise missile that can be launched from land, submarines, ships, and fighter aircraft. It is a joint venture between the Indian Defence Research and Development Organisation (DRDO) and the Russian Federation’s NPO Mashinostroyeniya, which together have formed BrahMos Aerospace.
The missile is based on Russian P-800 Oniks. The name BrahMos is a portmanteau formed from the names of two rivers, the Brahmaputra of India and the Moskva of Russia. India holds 50.5 percent share of the joint venture. 75 percent of the missile is manufactured in India and there are plans to increase this to 85 percent.
Large numbers of land-launched, ship-launched as well as air-launched versions have been inducted and are in service with the Indian armed forces.
The missile guidance has been developed by BrahMos Aerospace. In 2016, after India became a member of the Missile Technology Control Regime (MTCR), India and Russia gradually increased the range of the missile to 800 km. The latest deliveries to the Indian Navy are of this type.
The cruise missile has anti-ship and land-attack roles, and has been in service since June 2007. The other operator is the Philippine Marine Corps. The unit cost is around $ 3.5 million.
The extended range variant costs around $4.85 million. Many futuristic variants are evolving. The BrahMos-A is a modified air-launched variant of the missile with a reduced size and weight (2.55 tons). It has a range of 500 km when launched from Su-30 MKI, and it can carry only one BrahMos missile.
50 IAF SU-30MKI were modified to carry the BrahMos-A missile. Smaller-sized variants like BrahMos-NG could be carried on more types of aircraft, even on LCA. Additionally, the BrahMos-NG will have an AESA radar rather than the current mechanically scanned one.
The Sukhoi Su-30MKI will carry three NG missiles, while other IAF fighters will carry one. The BrahMos-NG will be ready by the end of 2025. BrahMos-II will be a hypersonic cruise missile. A UCAV variant is planned.
This solid propellant missile can carry a 200–300 kg warhead that could be nuclear or conventional semi-armour-piercing. Max operational ranges are up to 8-900 kilometres. Export variants are currently restricted to 290 kilometres.
The BrahMos is generally considered the world’s fastest supersonic cruise missile. Currently, the missile speed is Mach 3. Later variants will be hypersonic (M 5+). The missile is very accurate with a CEP of less than one metre.
BrahMos was first test-fired on 12 June 2001 from the Integrated Test Range (ITR), Chandipur, in a vertical launch configuration. The September 2010 test of BrahMos created a world record for being the first cruise missile to be tested at supersonic speeds in a steep-dive mode.
BrahMos was tested with an Indian seeker for the first time in March 2018, and was tested with an India-developed propulsion system, airframe, and power supply in September 2019. On 30 September 2020, India successfully test-fired an extended-range BrahMos, offering a range of around 350 km, at speeds up to Mach 2.8.
The submarine-launched variant of BrahMos was test-fired successfully for the first time from a submerged pontoon on 20 March 2013. Even BrahMos Block III land-attack variants are operational. There are plans to have missiles with a range of 1500 km or more.
BrahMos is operationally deployed in large numbers by the three services. Additional missile orders have been recently placed for extended-range variants.
The Philippines has placed a substantial order for their services, and deliveries began in 2024. Russia, too, has plans to buy many missiles. Brazil has shown interest in the missile system. Vietnam and Indonesia have already signed deals.
Sky Is Not The Limit
Resolute political will, choice of targets, weapon matching and accuracy, actionable intelligence, strong Indian air defences, and great IAF professionals. and hitting strategic targets in depth were the clear clinchers.
Aerospace has become the primary means of prosecuting war. India-Russia relations are time-tested. Nearly 60 percent of IAF aircraft are of Russian origin.
Russian platforms and weapons with the Indian armed forces have performed exceedingly well for many decades, since the MiG-21s of the 1960s. The S-400 and Su-30MKI-BrahMos combination have excelled in Op Sindoor.
Could S-500 (600 km) be the next acquisition? Will India select the Su-57 fifth-generation aircraft and Make in India? Can Russia help accelerate the Indian nuclear submarine program? Should India acquire the “AWACS Killer” Russian R-37M AAM and collaborate on developing futuristic long-range aerial missiles?
Should there be more work together on the Su-30MKI upgrade? Can the two enter into a joint venture for Kamikaze drones required by both sides in large numbers, and India can help scale up production?
The Sky is NO more the limit!
Let us look at the two Russia-origin systems.
S-400 Missile System “Sudarshan Chakra”
The S-400 is a Russian mobile SAM system developed in the 1990s by Russia’s NPO Almaz as an upgrade to the S-300 family of missiles.
The S-400 joined the Russian armed forces in 2007. The system is complemented by its successor, the S-500. The S-400 system has four radars and four sets of missiles covering different ranges and vertical bubbles.
The maximum target detection range is 600 kilometres, and targets can be engaged as far as 400 kilometres. The five S-400 batteries contracted by India in 2018 cost $5.43 billion, including reserve missiles.
All the sub-units are data-linked and controlled by a central command and control system with sufficient redundancy. The system is capable of layered defence and integrates with other Indian air defences.
One system can control 72 launchers, with a maximum of 384 missiles. All missiles are equipped with directed explosion warheads, which increases the probability of complete destruction of aerial targets.
The system is designed to destroy aircraft, cruise, and ballistic missiles, and can also be used against ground targets. It can engage targets up to 17,000 km/h or Mach 14. It can intercept low-flying cruise missiles at a range of about 40 km due to the line-of-sight requirement. The anti-ballistic missile (ABM) capabilities of the S-400 system are near the maximum allowed under the (now void) Anti-Ballistic Missile Treaty. The number of simultaneously engaged targets by the full system is 36.
The system ground mobility speed is close to 60 km/h on roads and 25 km/h cross-country. It takes 5 minutes to be operational and fire when ordered while driving. Otherwise, the system response time is just 10 seconds. The time between major overhauls is 10,000 hours. The Service life is at least 20 years.
In Russia, the system was made operational around Moscow in 2007. Russia reportedly deployed S-400 in Syria. The system has been widely used in the ongoing conflict in Ukraine, and it is claimed to have shot down many aircraft.
Meanwhile, Ukraine has reportedly used Western weapons, mainly U.S.-made ATACMS missiles, to hit S-400 units on the ground.
Belarus has unspecified numbers of S-400 units. Deliveries to China, of the six batteries ordered, began in January 2018. Four batteries consisting of 36 fire units and 192 or more missiles were delivered to Turkey.
Algeria is another operator. Some other countries, like Iran, Egypt, Iraq, and Serbia, have also shown interest. South Korea is developing the KM-SAM, a medium-range SAM system based on technology from S-400 missiles, with assistance from NPO Almaz.
Three of the five batteries have arrived in India. India took deliveries despite the American threat of CAATSA (Countering America’s Adversaries Through Sanctions Act).
The remaining two are expected in 2025/26. The recent conflict has revealed the rough location of two systems, one each in Punjab and Gujarat. As per open sources, the third is somewhere in the east. The systems have been tested in various Indian military exercises.
BrahMos
The BrahMos is a long-range ramjet supersonic cruise missile that can be launched from land, submarines, ships, and fighter aircraft. It is a joint venture between the Indian Defence Research and Development Organisation (DRDO) and the Russian Federation’s NPO Mashinostroyeniya, which together have formed BrahMos Aerospace.
The missile is based on Russian P-800 Oniks. The name BrahMos is a portmanteau formed from the names of two rivers, the Brahmaputra of India and the Moskva of Russia. India holds 50.5 percent share of the joint venture. 75 percent of the missile is manufactured in India and there are plans to increase this to 85 percent.
Large numbers of land-launched, ship-launched as well as air-launched versions have been inducted and are in service with the Indian armed forces.
The missile guidance has been developed by BrahMos Aerospace. In 2016, after India became a member of the Missile Technology Control Regime (MTCR), India and Russia gradually increased the range of the missile to 800 km. The latest deliveries to the Indian Navy are of this type.
The cruise missile has anti-ship and land-attack roles, and has been in service since June 2007. The other operator is the Philippine Marine Corps. The unit cost is around $ 3.5 million.
The extended range variant costs around $4.85 million. Many futuristic variants are evolving. The BrahMos-A is a modified air-launched variant of the missile with a reduced size and weight (2.55 tons). It has a range of 500 km when launched from Su-30 MKI, and it can carry only one BrahMos missile.
50 IAF SU-30MKI were modified to carry the BrahMos-A missile. Smaller-sized variants like BrahMos-NG could be carried on more types of aircraft, even on LCA. Additionally, the BrahMos-NG will have an AESA radar rather than the current mechanically scanned one.
The Sukhoi Su-30MKI will carry three NG missiles, while other IAF fighters will carry one. The BrahMos-NG will be ready by the end of 2025. BrahMos-II will be a hypersonic cruise missile. A UCAV variant is planned.
This solid propellant missile can carry a 200–300 kg warhead that could be nuclear or conventional semi-armour-piercing. Max operational ranges are up to 8-900 kilometres. Export variants are currently restricted to 290 kilometres.
The BrahMos is generally considered the world’s fastest supersonic cruise missile. Currently, the missile speed is Mach 3. Later variants will be hypersonic (M 5+). The missile is very accurate with a CEP of less than one metre.
BrahMos was first test-fired on 12 June 2001 from the Integrated Test Range (ITR), Chandipur, in a vertical launch configuration. The September 2010 test of BrahMos created a world record for being the first cruise missile to be tested at supersonic speeds in a steep-dive mode.
BrahMos was tested with an Indian seeker for the first time in March 2018, and was tested with an India-developed propulsion system, airframe, and power supply in September 2019. On 30 September 2020, India successfully test-fired an extended-range BrahMos, offering a range of around 350 km, at speeds up to Mach 2.8.
The submarine-launched variant of BrahMos was test-fired successfully for the first time from a submerged pontoon on 20 March 2013. Even BrahMos Block III land-attack variants are operational. There are plans to have missiles with a range of 1500 km or more.
BrahMos is operationally deployed in large numbers by the three services. Additional missile orders have been recently placed for extended-range variants.
The Philippines has placed a substantial order for their services, and deliveries began in 2024. Russia, too, has plans to buy many missiles. Brazil has shown interest in the missile system. Vietnam and Indonesia have already signed deals.
Sky Is Not The Limit
Resolute political will, choice of targets, weapon matching and accuracy, actionable intelligence, strong Indian air defences, and great IAF professionals. and hitting strategic targets in depth were the clear clinchers.
Aerospace has become the primary means of prosecuting war. India-Russia relations are time-tested. Nearly 60 percent of IAF aircraft are of Russian origin.
Russian platforms and weapons with the Indian armed forces have performed exceedingly well for many decades, since the MiG-21s of the 1960s. The S-400 and Su-30MKI-BrahMos combination have excelled in Op Sindoor.
Could S-500 (600 km) be the next acquisition? Will India select the Su-57 fifth-generation aircraft and Make in India? Can Russia help accelerate the Indian nuclear submarine program? Should India acquire the “AWACS Killer” Russian R-37M AAM and collaborate on developing futuristic long-range aerial missiles?
Should there be more work together on the Su-30MKI upgrade? Can the two enter into a joint venture for Kamikaze drones required by both sides in large numbers, and India can help scale up production?
The Sky is NO more the limit!