1 hr. ago
Want to create a profitable online marketplace like OLX?
Use our OLX Clone Script to build your own buy-sell marketplace. Take advantage of secure payments, simple listings, advanced search, and complete customization. It facilitates the quick and simple launch of a profitable online classifieds platform with a variety of revenue options.
Black Friday just got more profitable! Grab up to 50% OFF on our OLX clone script and start your own revenue-generating marketplace today.
Free Demo: https://www.trioangle.com/...
Contact: salestrioangle.com
#OLX Clone Script #Buy and Sell Marketplace #Classified Script #online Classifieds Marketplace Script #Buy Sell Platform Clone App Development #online Marketplace
Use our OLX Clone Script to build your own buy-sell marketplace. Take advantage of secure payments, simple listings, advanced search, and complete customization. It facilitates the quick and simple launch of a profitable online classifieds platform with a variety of revenue options.
Black Friday just got more profitable! Grab up to 50% OFF on our OLX clone script and start your own revenue-generating marketplace today.
Free Demo: https://www.trioangle.com/...
Contact: salestrioangle.com
#OLX Clone Script #Buy and Sell Marketplace #Classified Script #online Classifieds Marketplace Script #Buy Sell Platform Clone App Development #online Marketplace
2 months ago
Launch Your Own TikTok Clone App — Classified Ad
Looking to ride the creator economy wave? Get your hands on Oyelabs’ TikTok clone solution — a white-label, fully customizable short video platform loaded with features like AI-driven feed, duet & remix tools, in-app monetization (ads, tips, coins), real-time engagement, and full source code control. Build your brand, scale fast, and dominate the short video market.
🔗 https://oyelabs.com/tiktok...
#tiktokclone #ShortVideoApp #VideoPlatform #CreatorEconomy #WhiteLabelApp #SocialVideo #oyelabs #CustomCloneScript
Looking to ride the creator economy wave? Get your hands on Oyelabs’ TikTok clone solution — a white-label, fully customizable short video platform loaded with features like AI-driven feed, duet & remix tools, in-app monetization (ads, tips, coins), real-time engagement, and full source code control. Build your brand, scale fast, and dominate the short video market.
🔗 https://oyelabs.com/tiktok...
#tiktokclone #ShortVideoApp #VideoPlatform #CreatorEconomy #WhiteLabelApp #SocialVideo #oyelabs #CustomCloneScript
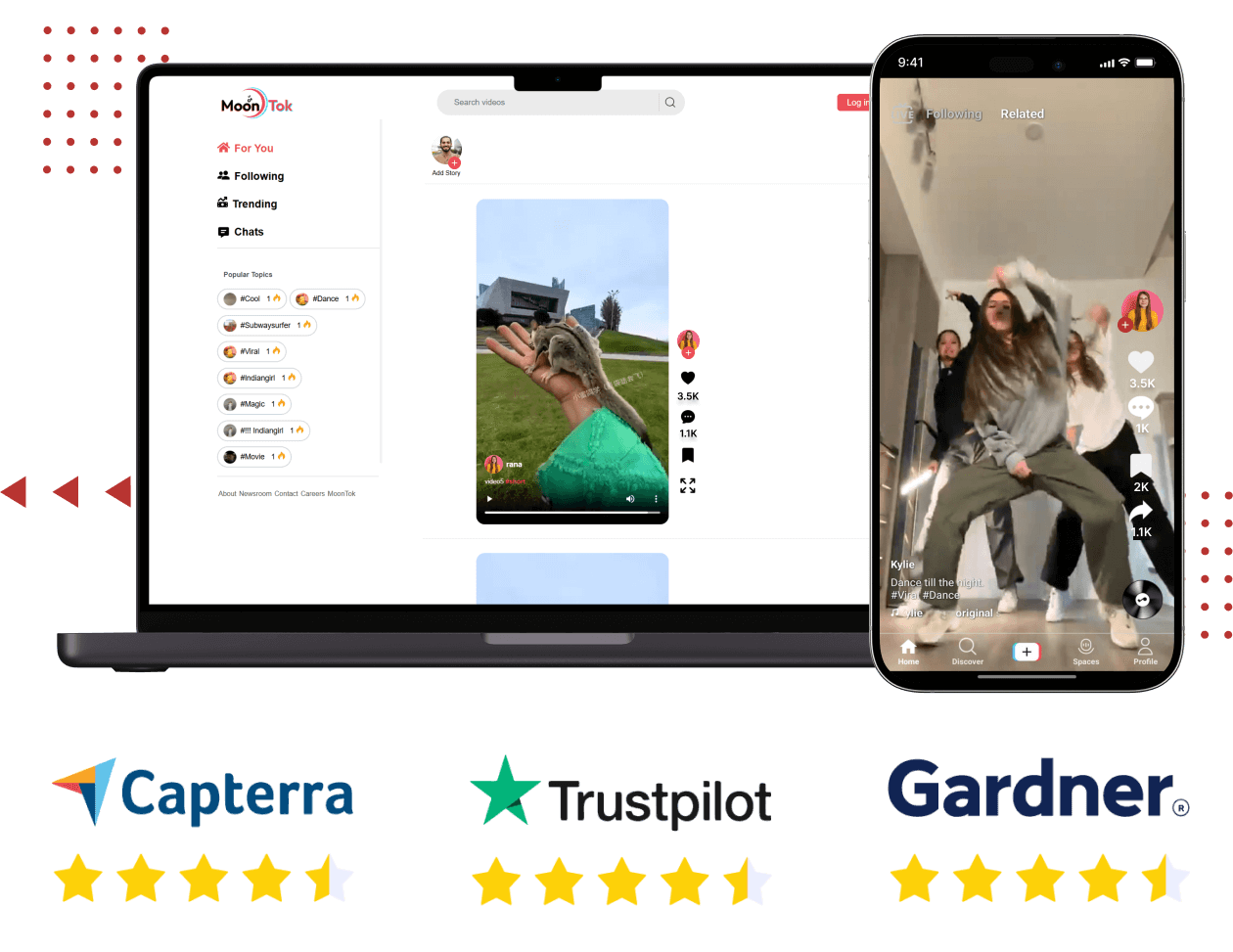
TikTok Clone - Launch Your Own TikTok Like App 2025
TikTok Clone is a 100% customizable, feature-rich solution to launch a video dubbing and video-sharing platform like TikTok, Dubsmash, Musical.ly in 7 days only.
https://oyelabs.com/tiktok-clone/
4 months ago
Focus on Cyber Warfare and Fraud-
How do multinational companies protect themselves from state-sponsored cyber espionage?
Multinational companies face a unique and elevated threat from state-sponsored cyber espionage due to their vast intellectual property, critical infrastructure dependencies, global reach, and often, involvement in strategic industries.
Protecting themselves requires a comprehensive, multi-layered, and continuously evolving cybersecurity strategy that goes beyond standard defenses.
Here are the key ways multinational companies protect themselves:
1. Robust Foundational Cybersecurity:
Before anything else, strong basic cybersecurity hygiene is paramount. State-sponsored actors often exploit common weaknesses.
Patch Management: Aggressive and immediate patching of all software, operating systems, and network devices, especially for known exploited vulnerabilities (N-day exploits). This includes out-of-band updates.
Strong Access Controls:
Multi-Factor Authentication (MFA): Mandatory MFA for all employees, especially for remote access, cloud services, and privileged accounts. Hardware tokens are often preferred for highly sensitive access.
Principle of Least Privilege (PoLP): Granting users and systems only the minimum access rights necessary to perform their functions.
Privileged Access Management (PAM): Solutions to secure, manage, and monitor privileged accounts.
Network Segmentation: Dividing the network into isolated zones to limit lateral movement if a part of the network is compromised. Critical data and operational technology (OT) networks should be completely segregated.
Endpoint Detection and Response (EDR) / Extended Detection and Response (XDR): Deploying advanced solutions to continuously monitor, detect, and respond to threats on endpoints (laptops, servers) and across the broader IT ecosystem.
Data Encryption: Encrypting data at rest and in transit, especially sensitive intellectual property and customer data.
2. Advanced Threat Detection and Intelligence:
State-sponsored groups are stealthy; proactive detection is crucial.
Behavioral Analytics & Anomaly Detection: Implementing tools that use AI and machine learning to establish baselines of "normal" user and network behavior, and then flag deviations that could indicate a compromise.
Threat Hunting Teams (Red Teaming/Blue Teaming): Employing internal or external teams to proactively search for hidden threats within the network, rather than just reacting to alerts. This includes simulating attacks (red teaming) to test defenses.
Comprehensive Logging and Monitoring: Centralized collection and analysis of logs from all systems, applications, and network devices to identify suspicious activity.
Threat Intelligence Integration: Subscribing to and actively consuming high-quality threat intelligence feeds from government agencies (like CISA, NCSC), cybersecurity vendors, and industry-specific ISACs (Information Sharing and Analysis Centers). This intelligence provides insights into the latest TTPs of state-sponsored actors, enabling proactive defense.
Dark Web Monitoring: Monitoring for mentions of the company, its employees, or stolen data on underground forums.
3. Supply Chain and Third-Party Risk Management:
State-sponsored actors often target weaker links in the supply chain.
Thorough Vendor Due Diligence: Rigorous cybersecurity assessments of all third-party vendors, suppliers, and partners, especially those with access to sensitive systems or data. This includes contractual security requirements.
Continuous Monitoring of Third-Parties: Not just a one-time assessment, but ongoing monitoring of third-party security postures and potential vulnerabilities in their products or services.
Supply Chain Visibility: Mapping the entire digital supply chain to understand dependencies and identify potential weak points.
Software Bill of Materials (SBOMs): Requiring SBOMs from software vendors to understand all components (including open-source) in their products and track potential vulnerabilities.
4. Human Element and Insider Threat Mitigation:
Employees are often the primary target for initial access.
Security Awareness Training: Regular, up-to-date, and engaging training for all employees on phishing, social engineering tactics, safe Browse, and reporting suspicious activity. Tailored training for executives and high-value targets (HVT) is essential.
Phishing Simulations: Conducting frequent and varied phishing simulations to test employee vigilance and reinforce training.
Insider Threat Programs: Establishing programs to detect and mitigate risks from malicious or unwitting insiders, including monitoring user behavior and data access patterns.
5. Incident Response and Resilience:
Assuming compromise is inevitable, preparation is key.
Well-Defined Incident Response Plan: A detailed, tested, and regularly updated plan for how to detect, contain, eradicate, and recover from a state-sponsored cyberattack. This includes clear roles, responsibilities, and communication protocols.
Secure Backups: Regular, encrypted, and offline backups of critical data and systems to ensure recovery from destructive attacks.
Business Continuity and Disaster Recovery (BCDR) Plans: Comprehensive plans to maintain essential business operations even during and after a significant cyber incident.
Post-Incident Analysis: Conducting thorough post-mortem analyses after any incident to learn lessons and improve defenses.
6. Collaboration with Government and Intelligence Agencies:
Governments often have unique insights into nation-state threats.
Information Sharing: Actively participating in information-sharing initiatives with government cybersecurity agencies (e.g., CISA in the US, NCSC in the UK), industry-specific ISACs, and threat intelligence alliances.
Trusted Relationships: Building direct, trusted relationships with relevant government cyber defense and intelligence agencies to facilitate rapid two-way sharing of classified or sensitive threat intelligence.
Reporting Incidents: Urgently reporting suspected state-sponsored cyberattacks to relevant government authorities to aid in national defense and enable coordinated responses.
By implementing these advanced and comprehensive measures, multinational companies can significantly enhance their resilience against state-sponsored cyber espionage, protect their valuable assets, and maintain their competitive edge in a contested digital landscape.
How do multinational companies protect themselves from state-sponsored cyber espionage?
Multinational companies face a unique and elevated threat from state-sponsored cyber espionage due to their vast intellectual property, critical infrastructure dependencies, global reach, and often, involvement in strategic industries.
Protecting themselves requires a comprehensive, multi-layered, and continuously evolving cybersecurity strategy that goes beyond standard defenses.
Here are the key ways multinational companies protect themselves:
1. Robust Foundational Cybersecurity:
Before anything else, strong basic cybersecurity hygiene is paramount. State-sponsored actors often exploit common weaknesses.
Patch Management: Aggressive and immediate patching of all software, operating systems, and network devices, especially for known exploited vulnerabilities (N-day exploits). This includes out-of-band updates.
Strong Access Controls:
Multi-Factor Authentication (MFA): Mandatory MFA for all employees, especially for remote access, cloud services, and privileged accounts. Hardware tokens are often preferred for highly sensitive access.
Principle of Least Privilege (PoLP): Granting users and systems only the minimum access rights necessary to perform their functions.
Privileged Access Management (PAM): Solutions to secure, manage, and monitor privileged accounts.
Network Segmentation: Dividing the network into isolated zones to limit lateral movement if a part of the network is compromised. Critical data and operational technology (OT) networks should be completely segregated.
Endpoint Detection and Response (EDR) / Extended Detection and Response (XDR): Deploying advanced solutions to continuously monitor, detect, and respond to threats on endpoints (laptops, servers) and across the broader IT ecosystem.
Data Encryption: Encrypting data at rest and in transit, especially sensitive intellectual property and customer data.
2. Advanced Threat Detection and Intelligence:
State-sponsored groups are stealthy; proactive detection is crucial.
Behavioral Analytics & Anomaly Detection: Implementing tools that use AI and machine learning to establish baselines of "normal" user and network behavior, and then flag deviations that could indicate a compromise.
Threat Hunting Teams (Red Teaming/Blue Teaming): Employing internal or external teams to proactively search for hidden threats within the network, rather than just reacting to alerts. This includes simulating attacks (red teaming) to test defenses.
Comprehensive Logging and Monitoring: Centralized collection and analysis of logs from all systems, applications, and network devices to identify suspicious activity.
Threat Intelligence Integration: Subscribing to and actively consuming high-quality threat intelligence feeds from government agencies (like CISA, NCSC), cybersecurity vendors, and industry-specific ISACs (Information Sharing and Analysis Centers). This intelligence provides insights into the latest TTPs of state-sponsored actors, enabling proactive defense.
Dark Web Monitoring: Monitoring for mentions of the company, its employees, or stolen data on underground forums.
3. Supply Chain and Third-Party Risk Management:
State-sponsored actors often target weaker links in the supply chain.
Thorough Vendor Due Diligence: Rigorous cybersecurity assessments of all third-party vendors, suppliers, and partners, especially those with access to sensitive systems or data. This includes contractual security requirements.
Continuous Monitoring of Third-Parties: Not just a one-time assessment, but ongoing monitoring of third-party security postures and potential vulnerabilities in their products or services.
Supply Chain Visibility: Mapping the entire digital supply chain to understand dependencies and identify potential weak points.
Software Bill of Materials (SBOMs): Requiring SBOMs from software vendors to understand all components (including open-source) in their products and track potential vulnerabilities.
4. Human Element and Insider Threat Mitigation:
Employees are often the primary target for initial access.
Security Awareness Training: Regular, up-to-date, and engaging training for all employees on phishing, social engineering tactics, safe Browse, and reporting suspicious activity. Tailored training for executives and high-value targets (HVT) is essential.
Phishing Simulations: Conducting frequent and varied phishing simulations to test employee vigilance and reinforce training.
Insider Threat Programs: Establishing programs to detect and mitigate risks from malicious or unwitting insiders, including monitoring user behavior and data access patterns.
5. Incident Response and Resilience:
Assuming compromise is inevitable, preparation is key.
Well-Defined Incident Response Plan: A detailed, tested, and regularly updated plan for how to detect, contain, eradicate, and recover from a state-sponsored cyberattack. This includes clear roles, responsibilities, and communication protocols.
Secure Backups: Regular, encrypted, and offline backups of critical data and systems to ensure recovery from destructive attacks.
Business Continuity and Disaster Recovery (BCDR) Plans: Comprehensive plans to maintain essential business operations even during and after a significant cyber incident.
Post-Incident Analysis: Conducting thorough post-mortem analyses after any incident to learn lessons and improve defenses.
6. Collaboration with Government and Intelligence Agencies:
Governments often have unique insights into nation-state threats.
Information Sharing: Actively participating in information-sharing initiatives with government cybersecurity agencies (e.g., CISA in the US, NCSC in the UK), industry-specific ISACs, and threat intelligence alliances.
Trusted Relationships: Building direct, trusted relationships with relevant government cyber defense and intelligence agencies to facilitate rapid two-way sharing of classified or sensitive threat intelligence.
Reporting Incidents: Urgently reporting suspected state-sponsored cyberattacks to relevant government authorities to aid in national defense and enable coordinated responses.
By implementing these advanced and comprehensive measures, multinational companies can significantly enhance their resilience against state-sponsored cyber espionage, protect their valuable assets, and maintain their competitive edge in a contested digital landscape.
6 months ago
Taiwan-Taipei prosecutors indicted four people on Tuesday suspected of spying for China in a case that reached Taiwan's presidential office, seeking jail terms of more than 18 years.
Democratically-governed Taiwan says it has faced heightened military and political pressure over the past five years or so from Beijing, which views the island as sovereign Chinese territory, a position Taipei's government rejects.
In a statement, Taipei prosecutors said the four, all previously members of the ruling Democratic Progressive Party, had been indicted on espionage and other charges.
One of them was a former assistant to then foreign minister Joseph Wu, now head of the National Security Council, while another was a former presidential office adviser, sources familiar with the matter have previously told Reuters.
The Taipei prosecutors said in a statement that their suspected crimes included divulging or delivering classified national security information to China.
Jail sentences of 18 years or more are being sought, the statement added.
China's Taiwan Affairs Office did not respond to a request for comment.
Last week, Taiwan's presidential office said it could not comment on the cases given the ongoing legal proceedings.
But it said that any person, regardless of party affiliation, who has "betrayed the country, collaborated with hostile external forces and committed crimes that hurt the whole nation" should be subject to the most severe punishment.
Democratically-governed Taiwan says it has faced heightened military and political pressure over the past five years or so from Beijing, which views the island as sovereign Chinese territory, a position Taipei's government rejects.
In a statement, Taipei prosecutors said the four, all previously members of the ruling Democratic Progressive Party, had been indicted on espionage and other charges.
One of them was a former assistant to then foreign minister Joseph Wu, now head of the National Security Council, while another was a former presidential office adviser, sources familiar with the matter have previously told Reuters.
The Taipei prosecutors said in a statement that their suspected crimes included divulging or delivering classified national security information to China.
Jail sentences of 18 years or more are being sought, the statement added.
China's Taiwan Affairs Office did not respond to a request for comment.
Last week, Taiwan's presidential office said it could not comment on the cases given the ongoing legal proceedings.
But it said that any person, regardless of party affiliation, who has "betrayed the country, collaborated with hostile external forces and committed crimes that hurt the whole nation" should be subject to the most severe punishment.
6 months ago
Serbia's populist President Aleksandar Vucic travelled to the Ukrainian city of Odesa for a regional summit on Wednesday, the first time the Moscow-friendly leader has visited the country during his 12 years in power.
Vucic travelled to Ukraine for one day to take part in the Ukraine-Southeastern Europe Summit in the Black Sea port of Odesa, which this week faced a major Russian drone and missile attack.
Senior politicians from 12 Southeastern European nations also took part in the summit, which was hosted by Ukrainian President Volodymyr Zelenskiy.
At the summit, Vucic, who has previously met Zelenskiy at least three times, said Serbia could help Kyiv in the renewal of Ukraine's war-torn regions.
Vucic who balances relations between Russia and the West, said he abstained from signing the joint declaration at the summit, reflecting Serbia's bid to maintain good ties with both Kyiv and Moscow.
"By protecting our (Serbia's) interests I am partially protecting both Russian and Ukrainian interests alike ... as we are protecting interests of international ... law," he said in remarks to Serbian journalists.
The joint declaration supports Ukraine’s efforts to find a diplomatic path to a just and lasting peace, and includes a call to the international community to intensify its support for Kyiv and refrain from offering material or other assistance to Russia’s war effort.
Serbia wants to join the European Union, but Russia, a traditional Slavic and Orthodox Christian ally, remains its biggest gas supplier, and the country's sole oil refinery is majority-owned by Gazprom and Gazprom Neft.
Although Belgrade has refused to join Western sanctions on Russia over its invasion of Ukraine, it has condemned Moscow's policies in the United Nations and expressed support for Ukraine's territorial integrity.
Belgrade recognises Ukraine in its entirety, including territories seized by Russia since 2014, while Kyiv refused to recognise the 2008 independence of Kosovo, Serbia's predominantly Albanian former southern province.
In late May, the SVR, the Russian foreign intelligence service, accused Belgrade of "a stab in the back", alleging Serbia's defence manufacturers were selling ammunition and weapons to Ukraine via intermediaries.
According to a classified Pentagon document leaked online, Serbia in 2023 agreed to supply arms to Kyiv, despite the country's professed military neutrality. Moscow has criticised Belgrade several times over the issue. Serbia has denied it ever supplied arms to Ukraine but has said it has sold to other buyers worldwide.
The only Serbian president to visit Ukraine since the Balkan country became independent in 2006 was Boris Tadic in 2011. Ukraine's previous president, Petro Poroshenko, visited Serbia in 2018.
Vucic travelled to Ukraine for one day to take part in the Ukraine-Southeastern Europe Summit in the Black Sea port of Odesa, which this week faced a major Russian drone and missile attack.
Senior politicians from 12 Southeastern European nations also took part in the summit, which was hosted by Ukrainian President Volodymyr Zelenskiy.
At the summit, Vucic, who has previously met Zelenskiy at least three times, said Serbia could help Kyiv in the renewal of Ukraine's war-torn regions.
Vucic who balances relations between Russia and the West, said he abstained from signing the joint declaration at the summit, reflecting Serbia's bid to maintain good ties with both Kyiv and Moscow.
"By protecting our (Serbia's) interests I am partially protecting both Russian and Ukrainian interests alike ... as we are protecting interests of international ... law," he said in remarks to Serbian journalists.
The joint declaration supports Ukraine’s efforts to find a diplomatic path to a just and lasting peace, and includes a call to the international community to intensify its support for Kyiv and refrain from offering material or other assistance to Russia’s war effort.
Serbia wants to join the European Union, but Russia, a traditional Slavic and Orthodox Christian ally, remains its biggest gas supplier, and the country's sole oil refinery is majority-owned by Gazprom and Gazprom Neft.
Although Belgrade has refused to join Western sanctions on Russia over its invasion of Ukraine, it has condemned Moscow's policies in the United Nations and expressed support for Ukraine's territorial integrity.
Belgrade recognises Ukraine in its entirety, including territories seized by Russia since 2014, while Kyiv refused to recognise the 2008 independence of Kosovo, Serbia's predominantly Albanian former southern province.
In late May, the SVR, the Russian foreign intelligence service, accused Belgrade of "a stab in the back", alleging Serbia's defence manufacturers were selling ammunition and weapons to Ukraine via intermediaries.
According to a classified Pentagon document leaked online, Serbia in 2023 agreed to supply arms to Kyiv, despite the country's professed military neutrality. Moscow has criticised Belgrade several times over the issue. Serbia has denied it ever supplied arms to Ukraine but has said it has sold to other buyers worldwide.
The only Serbian president to visit Ukraine since the Balkan country became independent in 2006 was Boris Tadic in 2011. Ukraine's previous president, Petro Poroshenko, visited Serbia in 2018.
6 months ago
Elon Musk escalates feud with Trump: 'Time to drop the really big bomb'
Elon Musk alleged that President Donald Trump's name is mentioned in undisclosed classified files related to the financier and sex offender Jeffrey Epstein as a feud between Trump and the world's richest man devolved into deeply personal attacks.
"Time to drop the really big bomb," Musk said in a June 5 post on X. "realDonaldTrump is in the Epstein files. That is the real reason they have not been made public. Have a nice day, DJT!"
Trump did not respond to shouted questions from reporters about Musk’s Esptein claim following a White House event with Attorney General Pam Bondi and members of the National Fraternal Order of Police.
The White House sent USA TODAY a statement from Trump press secretary Karoline Leavitt in response to the Epstein allegations. "This is an unfortunate episode from Elon, who is unhappy with the One Big Beautiful Bill because it does not include the policies he wanted. The President is focused on passing this historic piece of legislation and making our country great again," Leavitt said.
Musk provided no evidence for his allegation but wrote: "Mark this post for the future. The truth will come out."
His attack came after Trump, in posts on Truth Social, threatened to end government contracts with Musk's companies and said Musk left the White House's Department of Government Efficiency because Trump asked him to leave.
After hyping up the release of declassified government files on Epstein, Bondi on Feb. 27 disclosed about 200 pages of documents that implicated no one else in Epstein's orbit other than Epstein, who died in a federal prison in 2019.
The “Epstein list,” and the scandal surrounding the multimillionaire’s exploitation of teenage girls offers plenty of red meat for partisans on the right and left. Trump and Epstein were filmed and photographed together at parties, and in 2002 he praised the wealthy businessman as a "terrific guy.”
Elon Musk alleged that President Donald Trump's name is mentioned in undisclosed classified files related to the financier and sex offender Jeffrey Epstein as a feud between Trump and the world's richest man devolved into deeply personal attacks.
"Time to drop the really big bomb," Musk said in a June 5 post on X. "realDonaldTrump is in the Epstein files. That is the real reason they have not been made public. Have a nice day, DJT!"
Trump did not respond to shouted questions from reporters about Musk’s Esptein claim following a White House event with Attorney General Pam Bondi and members of the National Fraternal Order of Police.
The White House sent USA TODAY a statement from Trump press secretary Karoline Leavitt in response to the Epstein allegations. "This is an unfortunate episode from Elon, who is unhappy with the One Big Beautiful Bill because it does not include the policies he wanted. The President is focused on passing this historic piece of legislation and making our country great again," Leavitt said.
Musk provided no evidence for his allegation but wrote: "Mark this post for the future. The truth will come out."
His attack came after Trump, in posts on Truth Social, threatened to end government contracts with Musk's companies and said Musk left the White House's Department of Government Efficiency because Trump asked him to leave.
After hyping up the release of declassified government files on Epstein, Bondi on Feb. 27 disclosed about 200 pages of documents that implicated no one else in Epstein's orbit other than Epstein, who died in a federal prison in 2019.
The “Epstein list,” and the scandal surrounding the multimillionaire’s exploitation of teenage girls offers plenty of red meat for partisans on the right and left. Trump and Epstein were filmed and photographed together at parties, and in 2002 he praised the wealthy businessman as a "terrific guy.”
6 months ago
Chinese Web Around U.S. Military Bases Worries Americans; Is Ukraine’s ‘Shock’ Attack On Russia A Wake-Up Call For Trump?
The surprise Ukrainian drone attack on Russia, facilitated by the smuggling of drones inside trucks, has rattled the world at large. American analysts and lawmakers are now concerned that Chinese cargo ships that dock at U.S. ports could potentially carry out a similar stunt against the United States.
The Security Service of Ukraine, or SBU, launched the drone attacks on multiple Russian military bases on June 1 under ‘Operation Spiderweb.’ The operation involved 117 First Person View (FPV) drones that were smuggled into Russia, concealed in wooden containers with remotely operated roofs mounted on trucks.
These trucks, driven by individuals reportedly unaware of the cargo they were carrying, were positioned near the target air bases to ensure precision strikes.
Russia couldn’t have fathomed that an infiltration like that was taking place right under its nose. The strikes, meticulously planned over 18 months, humiliated Russia’s military by exposing the gaps in its intelligence architecture and the vulnerabilities in its air defenses.
Caught unaware, the Russian military sustained losses of billions of dollars. In the aftermath of the incident, several pro-Russian military bloggers said it was Russia’s Pearl Harbor, a reference to the surprise Japanese attack on the US Pearl Harbor port during World War II, that destroyed multiple US warships and aircraft.
The attack, perhaps the most significant demonstration of asymmetric warfare in recent times, will have far-reaching global repercussions. US analysts are concerned that China could replicate a similar move against America, utilizing its cargo ships that have unrestricted access to US ports, as highlighted by Newsweek in a recent report.
The report noted that lawmakers and security experts have expressed concerns over China’s state-owned shipping behemoth, COSCO Shipping, operating across US ports, despite being classified as a Chinese military enterprise by the Pentagon in January 2025.
US analysts have voiced concern that these cargo ships could be used to deploy drones, possibly hidden inside ships, to launch a preemptive strike on US ports in the event of a conflict.
COSCO is the largest state-owned shipping firm in China and a significant force in international marine logistics, with a considerable presence in important US ports, including Oakland, Long Beach, and Los Angeles, among others.
In January 2025, the House Committee on Homeland Security expressed concern about COSCO’s access to major US ports and the alleged presence of suspected Chinese Communist Party (CCP) political officers on board its ships, suggesting direct CCP influence. It warned of threats like espionage, cyber intrusion, or even sabotage by the Chinese.
The Trump administration has imposed port fees on COSCO to challenge China’s hegemony in the world’s shipbuilding industry. Additionally, the recently imposed US tariffs, including a 145% tariff on Chinese goods, have led to a sharp decline in COSCO’s shipments to American ports.
For example, the Port of Los Angeles saw a 35% plunge in cargo volume in May 2025, with COSCO and other carriers canceling transits.
Notably, a temporary US-China tariff truce last month spurred a surge in bookings, but COSCO continues to face operational challenges due to fees and reduced demand.
Despite COSCO’s reduced presence in the US, US analysts remain suspicious. Retired Navy Commander Thomas Shugart and a fellow at the Center for a New American Security said: “It is becoming borderline-insane that we routinely allow ships owned and operated by DoD-designated Chinese military companies to sit in our ports with thousands of containers onboard and under their control.”
While a Chinese attack is unlikely without an existing state of war, the presence of COSCO vessels near critical infrastructure, like the Norfolk Naval Station, raises concerns about espionage or sabotage.
It is pertinent to note that even the Ukrainian operation took 18 months of planning and intelligence gathering to achieve the desired result.
Moreover, there have been suggestive reports about China spying on US military facilities by purchasing land nearby and even infiltrating the US port infrastructure in the past, which makes the threat of a Ukraine drone-like attack more plausible to some in the US.
Chinese Spying Concerns Loom Large
Chinese ships docking at US ports have been a matter of discourse in the US for quite some time. Last year, a US Congressional investigation discovered that a Chinese business installed intelligence-gathering equipment on cranes used at US seaports, potentially enabling Beijing to spy on Americans or damage vital infrastructure.
ZPMC, a state-owned engineering company based in Shanghai, exerted pressure on American port authorities to grant remote access to its cranes, specifically those situated on the West Coast, i.e., the contiguous states of California, Oregon, and Washington.
The report, produced after a year-long research, warned that “This access could potentially be extended to other [People’s Republic of China] government entities, posing a significant risk due to the PRC’s national security laws that mandate cooperation with state intelligence agencies.”
Citing contract paperwork and testimonies from port operators, the investigation stated that “these unknown modems were believed to have been installed under the auspices of collecting usage data for the equipment.” These modems allegedly employed a covert approach to gathering data and circumventing firewalls, which could potentially disrupt port operations, even though they were unnecessary for the cranes to operate.
At the time, these findings caused alarm because about 80% of the cargo cranes in American ports are owned by ZPMC.
Transporting goods through US marine ports, which generate trillions of dollars in economic activity every year, requires ship-to-shore cranes. However, because these cranes can often be controlled remotely, anyone with access to the networks may be able to collect intelligence from ports or damage equipment.
In a hypothetical scenario, the intelligence collected through the cranes could be used to launch an ‘Operation Spiderweb’ type of operation where Chinese cargos double up as carriers of drones that go off by flicking a button on a remote.
Earlier, the White House disclosed plans to “phase out Chinese-made port equipment and fully return crane making to the United States to deal with 200 Chinese-made cranes at U.S. ports and facilities”. However, the progress of that effort under the Trump administration remains unknown.
Another prevailing concern in the United States has been the ownership of farm and commercial land near US military facilities by Chinese people and corporations.
A previous report revealed that Chinese companies purchased several farmlands close to strategic US military installations, including some of the most strategically important military installations, such as MacDill Air Force Base in Tampa, Florida; Marine Corps Base Camp Pendleton in San Diego, California; Fort Liberty (formerly Fort Bragg) in Fayetteville, North Carolina; and Fort Cavazos (formerly Fort Hood) in Killeen, Texas.
Sources suggest that under the guise of farming, Chinese landowners could potentially set up surveillance equipment or use drones to monitor military sites. According to the January 2024 data from the US Department of Agriculture, China claims 349,442 acres out of roughly 40 million acres of foreign-owned farmland, or 0.87 percent.
It does not help that Chinese nationals have sneaked into military bases and other sensitive US sites more than 100 times in recent years, as the Wall Street Journal reported in 2023. This raises a very alarming issue regarding Chinese ownership of land near military sites.
Additionally, the US National Association of Realtors (NAR) stated in a report last year that the Chinese have remained the top foreign buyers of US residential property for the 11th consecutive year.
Experts caution that, just as Ukraine’s drones targeted Russian airfields, Chinese-owned property may be used for tracking devices, reconnaissance sites, or drones to observe US military activities.
The strategic placement of these lands near bases like Fort Liberty, which hosts critical airborne and special operations units, amplifies concerns about a surprise threat akin to Pearl Harbor’s unexpected attack.
Although no US federal law mandates a ban, individual states have been passing laws to curtail Chinese ownership of land near US military bases.
The surprise Ukrainian drone attack on Russia, facilitated by the smuggling of drones inside trucks, has rattled the world at large. American analysts and lawmakers are now concerned that Chinese cargo ships that dock at U.S. ports could potentially carry out a similar stunt against the United States.
The Security Service of Ukraine, or SBU, launched the drone attacks on multiple Russian military bases on June 1 under ‘Operation Spiderweb.’ The operation involved 117 First Person View (FPV) drones that were smuggled into Russia, concealed in wooden containers with remotely operated roofs mounted on trucks.
These trucks, driven by individuals reportedly unaware of the cargo they were carrying, were positioned near the target air bases to ensure precision strikes.
Russia couldn’t have fathomed that an infiltration like that was taking place right under its nose. The strikes, meticulously planned over 18 months, humiliated Russia’s military by exposing the gaps in its intelligence architecture and the vulnerabilities in its air defenses.
Caught unaware, the Russian military sustained losses of billions of dollars. In the aftermath of the incident, several pro-Russian military bloggers said it was Russia’s Pearl Harbor, a reference to the surprise Japanese attack on the US Pearl Harbor port during World War II, that destroyed multiple US warships and aircraft.
The attack, perhaps the most significant demonstration of asymmetric warfare in recent times, will have far-reaching global repercussions. US analysts are concerned that China could replicate a similar move against America, utilizing its cargo ships that have unrestricted access to US ports, as highlighted by Newsweek in a recent report.
The report noted that lawmakers and security experts have expressed concerns over China’s state-owned shipping behemoth, COSCO Shipping, operating across US ports, despite being classified as a Chinese military enterprise by the Pentagon in January 2025.
US analysts have voiced concern that these cargo ships could be used to deploy drones, possibly hidden inside ships, to launch a preemptive strike on US ports in the event of a conflict.
COSCO is the largest state-owned shipping firm in China and a significant force in international marine logistics, with a considerable presence in important US ports, including Oakland, Long Beach, and Los Angeles, among others.
In January 2025, the House Committee on Homeland Security expressed concern about COSCO’s access to major US ports and the alleged presence of suspected Chinese Communist Party (CCP) political officers on board its ships, suggesting direct CCP influence. It warned of threats like espionage, cyber intrusion, or even sabotage by the Chinese.
The Trump administration has imposed port fees on COSCO to challenge China’s hegemony in the world’s shipbuilding industry. Additionally, the recently imposed US tariffs, including a 145% tariff on Chinese goods, have led to a sharp decline in COSCO’s shipments to American ports.
For example, the Port of Los Angeles saw a 35% plunge in cargo volume in May 2025, with COSCO and other carriers canceling transits.
Notably, a temporary US-China tariff truce last month spurred a surge in bookings, but COSCO continues to face operational challenges due to fees and reduced demand.
Despite COSCO’s reduced presence in the US, US analysts remain suspicious. Retired Navy Commander Thomas Shugart and a fellow at the Center for a New American Security said: “It is becoming borderline-insane that we routinely allow ships owned and operated by DoD-designated Chinese military companies to sit in our ports with thousands of containers onboard and under their control.”
While a Chinese attack is unlikely without an existing state of war, the presence of COSCO vessels near critical infrastructure, like the Norfolk Naval Station, raises concerns about espionage or sabotage.
It is pertinent to note that even the Ukrainian operation took 18 months of planning and intelligence gathering to achieve the desired result.
Moreover, there have been suggestive reports about China spying on US military facilities by purchasing land nearby and even infiltrating the US port infrastructure in the past, which makes the threat of a Ukraine drone-like attack more plausible to some in the US.
Chinese Spying Concerns Loom Large
Chinese ships docking at US ports have been a matter of discourse in the US for quite some time. Last year, a US Congressional investigation discovered that a Chinese business installed intelligence-gathering equipment on cranes used at US seaports, potentially enabling Beijing to spy on Americans or damage vital infrastructure.
ZPMC, a state-owned engineering company based in Shanghai, exerted pressure on American port authorities to grant remote access to its cranes, specifically those situated on the West Coast, i.e., the contiguous states of California, Oregon, and Washington.
The report, produced after a year-long research, warned that “This access could potentially be extended to other [People’s Republic of China] government entities, posing a significant risk due to the PRC’s national security laws that mandate cooperation with state intelligence agencies.”
Citing contract paperwork and testimonies from port operators, the investigation stated that “these unknown modems were believed to have been installed under the auspices of collecting usage data for the equipment.” These modems allegedly employed a covert approach to gathering data and circumventing firewalls, which could potentially disrupt port operations, even though they were unnecessary for the cranes to operate.
At the time, these findings caused alarm because about 80% of the cargo cranes in American ports are owned by ZPMC.
Transporting goods through US marine ports, which generate trillions of dollars in economic activity every year, requires ship-to-shore cranes. However, because these cranes can often be controlled remotely, anyone with access to the networks may be able to collect intelligence from ports or damage equipment.
In a hypothetical scenario, the intelligence collected through the cranes could be used to launch an ‘Operation Spiderweb’ type of operation where Chinese cargos double up as carriers of drones that go off by flicking a button on a remote.
Earlier, the White House disclosed plans to “phase out Chinese-made port equipment and fully return crane making to the United States to deal with 200 Chinese-made cranes at U.S. ports and facilities”. However, the progress of that effort under the Trump administration remains unknown.
Another prevailing concern in the United States has been the ownership of farm and commercial land near US military facilities by Chinese people and corporations.
A previous report revealed that Chinese companies purchased several farmlands close to strategic US military installations, including some of the most strategically important military installations, such as MacDill Air Force Base in Tampa, Florida; Marine Corps Base Camp Pendleton in San Diego, California; Fort Liberty (formerly Fort Bragg) in Fayetteville, North Carolina; and Fort Cavazos (formerly Fort Hood) in Killeen, Texas.
Sources suggest that under the guise of farming, Chinese landowners could potentially set up surveillance equipment or use drones to monitor military sites. According to the January 2024 data from the US Department of Agriculture, China claims 349,442 acres out of roughly 40 million acres of foreign-owned farmland, or 0.87 percent.
It does not help that Chinese nationals have sneaked into military bases and other sensitive US sites more than 100 times in recent years, as the Wall Street Journal reported in 2023. This raises a very alarming issue regarding Chinese ownership of land near military sites.
Additionally, the US National Association of Realtors (NAR) stated in a report last year that the Chinese have remained the top foreign buyers of US residential property for the 11th consecutive year.
Experts caution that, just as Ukraine’s drones targeted Russian airfields, Chinese-owned property may be used for tracking devices, reconnaissance sites, or drones to observe US military activities.
The strategic placement of these lands near bases like Fort Liberty, which hosts critical airborne and special operations units, amplifies concerns about a surprise threat akin to Pearl Harbor’s unexpected attack.
Although no US federal law mandates a ban, individual states have been passing laws to curtail Chinese ownership of land near US military bases.
6 months ago
Israeli strikes on Gaza schools used as civilian shelters are part of deliberate strategy, say sources
A series of recent deadly airstrikes on school buildings sheltering displaced people in Gaza were part of a deliberate Israeli military bombing strategy, with further schools identified as targets, the Guardian has learned.
At least six school buildings have been struck, reportedly killing more than 120 people, in recent months as part of a targeting effort by the Israeli military.
This followed a loosening of controls on actions targeting Hamas operatives at sites with large numbers of civilians present, according to sources familiar with the strategy.
On Monday, four people were reportedly killed in the latest Israeli airstrike on a school turned shelter, in Deir al-Balah in the centre of Gaza. Videos on social media appeared to show the aftermath of what was said to be the location of al-Aishiya school.
Announcing the strike, the Israel Defense Forces (IDF) said, without providing evidence or naming the school, it had bombed a site “used by terrorists” in the area, claiming it had taken steps to reduce civilian harm.
Al-Aishiya school was among a series of school buildings used as shelters identified by the IDF as targets in recent weeks, according to military sources.
Four further school buildings have been marked as potential targets to be bombed, according to the sources.
The locations identified as potential targets include four schools: Halawa, al-Rafaa’i, Nusiba and Halima Sa’dia. All four are in or near Jabaliya in the north of Gaza.
It was not immediately clear whether these buildings were also being used as shelters. Two of the schools appear to have been damaged by airstrikes at earlier stages in the offensive.
According to latest UN assessments, 95% of Gaza’s schools have sustained some level of damage to their buildings. Approximately 400 schools were classified as having suffered a “direct hit”.
On 25 May, an Israeli strike killed at least 54 people sleeping at the Fahmi al-Jarjawi school, according to local officials, who told the BBC that severely burnt bodies, including those of children, were recovered from classrooms that had been set ablaze.
The IDF claimed it had “struck key terrorists who were operating within a Hamas and Islamic Jihad command and control centre embedded in an area that previously served” as the school.
Over the past two months, school buildings, hospitals and municipal buildings have been categorised by the IDF as “heavy centres”, which it believes are being used by Hamas militants alongside civilians, according to three military sources.
The sources said airstrikes had been authorised against such sites in circumstances in which only low-ranking militants were present despite knowing that civilians could be killed.
Juliette Touma, the director of communications at Unrwa, the UN agency for Palestine refugees, said schools “must always be protected and must never be hit or used for military or fighting purposes”.
“Very sadly, schools have been struck over and over for the past 20 months. It’s a grave violation of international law and of children’s rights,” she said.
Asked about its planned operations against school buildings, a spokesperson said the IDF “operates exclusively on the grounds of military necessity and in strict accordance with international law”.
The spokesperson claimed that Hamas unlawfully “exploits schools” for military activities by “building military networks beneath and within schools … launching attacks towards IDF forces from them, and imprisoning hostages in them”.
A series of recent deadly airstrikes on school buildings sheltering displaced people in Gaza were part of a deliberate Israeli military bombing strategy, with further schools identified as targets, the Guardian has learned.
At least six school buildings have been struck, reportedly killing more than 120 people, in recent months as part of a targeting effort by the Israeli military.
This followed a loosening of controls on actions targeting Hamas operatives at sites with large numbers of civilians present, according to sources familiar with the strategy.
On Monday, four people were reportedly killed in the latest Israeli airstrike on a school turned shelter, in Deir al-Balah in the centre of Gaza. Videos on social media appeared to show the aftermath of what was said to be the location of al-Aishiya school.
Announcing the strike, the Israel Defense Forces (IDF) said, without providing evidence or naming the school, it had bombed a site “used by terrorists” in the area, claiming it had taken steps to reduce civilian harm.
Al-Aishiya school was among a series of school buildings used as shelters identified by the IDF as targets in recent weeks, according to military sources.
Four further school buildings have been marked as potential targets to be bombed, according to the sources.
The locations identified as potential targets include four schools: Halawa, al-Rafaa’i, Nusiba and Halima Sa’dia. All four are in or near Jabaliya in the north of Gaza.
It was not immediately clear whether these buildings were also being used as shelters. Two of the schools appear to have been damaged by airstrikes at earlier stages in the offensive.
According to latest UN assessments, 95% of Gaza’s schools have sustained some level of damage to their buildings. Approximately 400 schools were classified as having suffered a “direct hit”.
On 25 May, an Israeli strike killed at least 54 people sleeping at the Fahmi al-Jarjawi school, according to local officials, who told the BBC that severely burnt bodies, including those of children, were recovered from classrooms that had been set ablaze.
The IDF claimed it had “struck key terrorists who were operating within a Hamas and Islamic Jihad command and control centre embedded in an area that previously served” as the school.
Over the past two months, school buildings, hospitals and municipal buildings have been categorised by the IDF as “heavy centres”, which it believes are being used by Hamas militants alongside civilians, according to three military sources.
The sources said airstrikes had been authorised against such sites in circumstances in which only low-ranking militants were present despite knowing that civilians could be killed.
Juliette Touma, the director of communications at Unrwa, the UN agency for Palestine refugees, said schools “must always be protected and must never be hit or used for military or fighting purposes”.
“Very sadly, schools have been struck over and over for the past 20 months. It’s a grave violation of international law and of children’s rights,” she said.
Asked about its planned operations against school buildings, a spokesperson said the IDF “operates exclusively on the grounds of military necessity and in strict accordance with international law”.
The spokesperson claimed that Hamas unlawfully “exploits schools” for military activities by “building military networks beneath and within schools … launching attacks towards IDF forces from them, and imprisoning hostages in them”.
6 months ago
Alleged Chinese spy ‘plotted’ to make Xi critic ‘bang bang and gone’
A British father accused of spying for the Chinese Communist Party plotted to kidnap and kneecap a critic of Xi Jinping, according to an indictment.
John Miller, a businessman who owns a £1.5 million home in Tunbridge Wells that is flanked by two Chinese Terracotta warriors, is alleged to have tried to smuggle missiles and drones into China.
The 63-year-old, whose wife is a churchwarden in Kent, was described by neighbours as “funny, nice and perfectly normal”.
However, he is accused of attempting to traffic “sensitive American military technology” to China, including missiles, air defence radar and drones.
It is also alleged that he referred to Mr Xi, the Chinese president, as “the boss” in intercepted phone calls.
Court documents in the US state that Mr Miller wanted to have a Los Angeles artist who was a critic of Mr Xi “f---ed up”. He allegedly said his Chinese handlers were “bang up” for launching an attack on him with “bullets” instead of baseball bats.
In April, Mr Miller was arrested along with Cui Guanghai, a 43-year-old Chinese national, on the orders of the FBI in Serbia, where he is awaiting extradition to the US.
The pair were charged after approaching two individuals who, unbeknown to them, were working for the FBI.
Mr Miller is a permanent resident of the US but was born in the UK. He has held roles in at least five UK companies, including a firm that appeared to facilitate English language teaching jobs in China but is now dissolved.
On Sunday, neighbours described the Millers as a “perfect family”, and told of their surprise at his arrest.
One said: “He was a nice guy. Over and above that I didn’t know what he did for work. He was funny, nice and perfectly normal. He wasn’t cagey... I am astounded.
“It’s awful for him, and if he has done it he’s a bloody idiot, but it’s innocent until proven guilty. It’s slightly surreal.”
‘A kind man and good neighbour’
At the Parish Church of King Charles the Martyr, where Mr Miller’s wife Bea is a warden, Rev Laurence Powell said: “It is shocking to hear this about John. He is a very kind man and a good neighbour. I feel so sorry for Beatrice. She must be going through hell right now.”
Mr Miller is accused of employing a wide range of tactics over two and a half years to harass, intimidate, stalk and threaten the Xi critic in LA.
According to a 27-page indictment at the US District Court for the Central District of California, Mr Miller told a confidential FBI source that “the real f---ing pay... the real payday is going to be putting the siding up on that guy” and “there will be extra cash to play with when that happens”.
A special agent said “siding” meant an assault and that there had been an earlier conversation where Mr Miller “had discussed possibly kidnapping the victim”.
“They want it bang bang and gone,” Miller is quoted as saying in a recorded phone call. “No talking to, no nothing to, like a mugging or something. Take his f---ing watch. Take his phone.”
He is then asked if he cares if he preferred “bullets versus baseball bat”, before replying: “Um, not necessarily. But I think you’d get paid more for bullets. And the guys I spoke to said that’s way f---ing easier. Apparently, they’re not so much baseball bat, or like an ice pick is the best way of doing it.
“On the knees and ankles. Doesn’t necessarily have to be bullets. Have him f---ed up and have his picture taken. F---ed up. But the guys I’ve spoken to, the easiest thing is just bam bam bang bang and just walk away. But listen it doesn’t have to be that... knees and ankles.”
‘Chinese Christmas wish list’
Another phone call appears to show Mr Miller had arranged a payment with a “minimum” of $100,000 for the source to carry out the assault, and, when questioned if there was a problem from the female handler Mr Guanghai was reporting to, he replied: “Oh no no no no.
“She’s second in command. And her boss is bang up for it. There’s another guy who needs to approve it. But they’re all bang up for it. As long as it’s reasonable. The numbers we talked about I’m pretty sure it’s 100 per cent.”
The documents show that the pair also enlisted undercover agents to stop the victim from protesting against Mr Xi’s appearance at a summit and installed tracking devices on the victim’s car, and paid the undercover agents to slash their tyres.
They also devised a complex plan to destroy a set of statues created by the artist which depicted Mr Xi and his wife bare-chested, kneeling with their hands tied behind their backs.
Initially, Mr Miller had allegedly wanted to steal the statues and “remove the heads” as evidence but later decided to pay the undercover FBI agents to “smash up” them up.
In 2025, Mr Miller paid the agents $36,500 (£27,100) to convince the victim to desist from showcasing the new statues at an upcoming protest.
He also allegedly tried to purchase millions of pounds worth of military equipment on behalf of the Chinese military as part of a “Christmas wish list”. He is quoted as saying his buyers were “interested in the Western stuff” including armour plates for “tanks that the Yanks have”.
He reportedly tried to buy a £37,000 Stinger portable missile launcher, two military drones valued at £148,000, a £668,000 AGM-88E anti-radiation missile system and a £1.5 million air-defence radar system.
Mr Miller also allegedly tried to procure a cryptographic device, which is used for secure communication of classified and sensitive information.
At one point, the Briton allegedly suggested that the device be smuggled from the US to China by hiding it inside a food blender or a motor starter, having shipped it first via DHL or FedEx to Hong Kong.
‘Big boss’
Several times in Mr Miller’s conversations, he is said to have mentioned a “boss” or at times a “big boss” that seems to be the one giving orders.
According to the special FBI agent who submitted the affidavit, Mr Miller’s use of the phrase “boss” “refer[s] to President Xi” and “demonstrates [Miller’s] awareness that he was acting at the direction and control of the [Chinese] government.”
Todd Blanche, the US deputy attorney general, said: “This is a blatant assault on both our national security and our democratic values. This Justice Department will not tolerate foreign repression on US soil, nor will we allow hostile nations to infiltrate or exploit our defence systems.
“We will act decisively to expose and dismantle these threats wherever they emerge.”
If convicted, Mr Miller could also face the maximum penalties of five years in prison for conspiracy, five years in prison for interstate stalking, and 10 years in prison for smuggling.
A British father accused of spying for the Chinese Communist Party plotted to kidnap and kneecap a critic of Xi Jinping, according to an indictment.
John Miller, a businessman who owns a £1.5 million home in Tunbridge Wells that is flanked by two Chinese Terracotta warriors, is alleged to have tried to smuggle missiles and drones into China.
The 63-year-old, whose wife is a churchwarden in Kent, was described by neighbours as “funny, nice and perfectly normal”.
However, he is accused of attempting to traffic “sensitive American military technology” to China, including missiles, air defence radar and drones.
It is also alleged that he referred to Mr Xi, the Chinese president, as “the boss” in intercepted phone calls.
Court documents in the US state that Mr Miller wanted to have a Los Angeles artist who was a critic of Mr Xi “f---ed up”. He allegedly said his Chinese handlers were “bang up” for launching an attack on him with “bullets” instead of baseball bats.
In April, Mr Miller was arrested along with Cui Guanghai, a 43-year-old Chinese national, on the orders of the FBI in Serbia, where he is awaiting extradition to the US.
The pair were charged after approaching two individuals who, unbeknown to them, were working for the FBI.
Mr Miller is a permanent resident of the US but was born in the UK. He has held roles in at least five UK companies, including a firm that appeared to facilitate English language teaching jobs in China but is now dissolved.
On Sunday, neighbours described the Millers as a “perfect family”, and told of their surprise at his arrest.
One said: “He was a nice guy. Over and above that I didn’t know what he did for work. He was funny, nice and perfectly normal. He wasn’t cagey... I am astounded.
“It’s awful for him, and if he has done it he’s a bloody idiot, but it’s innocent until proven guilty. It’s slightly surreal.”
‘A kind man and good neighbour’
At the Parish Church of King Charles the Martyr, where Mr Miller’s wife Bea is a warden, Rev Laurence Powell said: “It is shocking to hear this about John. He is a very kind man and a good neighbour. I feel so sorry for Beatrice. She must be going through hell right now.”
Mr Miller is accused of employing a wide range of tactics over two and a half years to harass, intimidate, stalk and threaten the Xi critic in LA.
According to a 27-page indictment at the US District Court for the Central District of California, Mr Miller told a confidential FBI source that “the real f---ing pay... the real payday is going to be putting the siding up on that guy” and “there will be extra cash to play with when that happens”.
A special agent said “siding” meant an assault and that there had been an earlier conversation where Mr Miller “had discussed possibly kidnapping the victim”.
“They want it bang bang and gone,” Miller is quoted as saying in a recorded phone call. “No talking to, no nothing to, like a mugging or something. Take his f---ing watch. Take his phone.”
He is then asked if he cares if he preferred “bullets versus baseball bat”, before replying: “Um, not necessarily. But I think you’d get paid more for bullets. And the guys I spoke to said that’s way f---ing easier. Apparently, they’re not so much baseball bat, or like an ice pick is the best way of doing it.
“On the knees and ankles. Doesn’t necessarily have to be bullets. Have him f---ed up and have his picture taken. F---ed up. But the guys I’ve spoken to, the easiest thing is just bam bam bang bang and just walk away. But listen it doesn’t have to be that... knees and ankles.”
‘Chinese Christmas wish list’
Another phone call appears to show Mr Miller had arranged a payment with a “minimum” of $100,000 for the source to carry out the assault, and, when questioned if there was a problem from the female handler Mr Guanghai was reporting to, he replied: “Oh no no no no.
“She’s second in command. And her boss is bang up for it. There’s another guy who needs to approve it. But they’re all bang up for it. As long as it’s reasonable. The numbers we talked about I’m pretty sure it’s 100 per cent.”
The documents show that the pair also enlisted undercover agents to stop the victim from protesting against Mr Xi’s appearance at a summit and installed tracking devices on the victim’s car, and paid the undercover agents to slash their tyres.
They also devised a complex plan to destroy a set of statues created by the artist which depicted Mr Xi and his wife bare-chested, kneeling with their hands tied behind their backs.
Initially, Mr Miller had allegedly wanted to steal the statues and “remove the heads” as evidence but later decided to pay the undercover FBI agents to “smash up” them up.
In 2025, Mr Miller paid the agents $36,500 (£27,100) to convince the victim to desist from showcasing the new statues at an upcoming protest.
He also allegedly tried to purchase millions of pounds worth of military equipment on behalf of the Chinese military as part of a “Christmas wish list”. He is quoted as saying his buyers were “interested in the Western stuff” including armour plates for “tanks that the Yanks have”.
He reportedly tried to buy a £37,000 Stinger portable missile launcher, two military drones valued at £148,000, a £668,000 AGM-88E anti-radiation missile system and a £1.5 million air-defence radar system.
Mr Miller also allegedly tried to procure a cryptographic device, which is used for secure communication of classified and sensitive information.
At one point, the Briton allegedly suggested that the device be smuggled from the US to China by hiding it inside a food blender or a motor starter, having shipped it first via DHL or FedEx to Hong Kong.
‘Big boss’
Several times in Mr Miller’s conversations, he is said to have mentioned a “boss” or at times a “big boss” that seems to be the one giving orders.
According to the special FBI agent who submitted the affidavit, Mr Miller’s use of the phrase “boss” “refer[s] to President Xi” and “demonstrates [Miller’s] awareness that he was acting at the direction and control of the [Chinese] government.”
Todd Blanche, the US deputy attorney general, said: “This is a blatant assault on both our national security and our democratic values. This Justice Department will not tolerate foreign repression on US soil, nor will we allow hostile nations to infiltrate or exploit our defence systems.
“We will act decisively to expose and dismantle these threats wherever they emerge.”
If convicted, Mr Miller could also face the maximum penalties of five years in prison for conspiracy, five years in prison for interstate stalking, and 10 years in prison for smuggling.
6 months ago
NATO will ask Germany to provide seven more brigades, or some 40,000 troops, for the alliance's defence, three sources told Reuters, under new targets for weapons and troop numbers that its members' defence ministers are set to agree on next week.
The alliance is dramatically increasing its military capability targets as it views Russia as a much greater threat since its 2022 full-scale invasion of Ukraine.
Exact figures for NATO's targets - either overall or country by country - are hard to verify as the information is highly classified.
One senior military official who, like the other sources spoke on condition of anonymity, said the target for the total number of brigades that NATO allies would have to provide in future will be raised to between 120 and 130.
This would mean a hike of some 50% from the current target of around 80 brigades, the source said. A government source put the target at 130 brigades for all of NATO.
The alliance is dramatically increasing its military capability targets as it views Russia as a much greater threat since its 2022 full-scale invasion of Ukraine.
Exact figures for NATO's targets - either overall or country by country - are hard to verify as the information is highly classified.
One senior military official who, like the other sources spoke on condition of anonymity, said the target for the total number of brigades that NATO allies would have to provide in future will be raised to between 120 and 130.
This would mean a hike of some 50% from the current target of around 80 brigades, the source said. A government source put the target at 130 brigades for all of NATO.
6 months ago
The Czech Republic said on Wednesday China was responsible for a "malicious cyber campaign" targeting a network used for unclassified communication at the Foreign Affairs ministry, and summoned the Chinese ambassador to condemn the incident.
The attacks have been ongoing since 2022 and were perpetrated by the cyber espionage actor APT31, which the Czech Republic, an EU state and NATO member, said was publicly associated with the Chinese Ministry of State Security.
The Chinese embassy in Prague did not immediately respond to a request for comment. NATO and the European Union said they stood in solidarity with the Czech Republic.
Foreign Minister Jan Lipavsky said on X that after the attack was detected, the ministry implemented a new communications system with enhanced security.
The attacks have been ongoing since 2022 and were perpetrated by the cyber espionage actor APT31, which the Czech Republic, an EU state and NATO member, said was publicly associated with the Chinese Ministry of State Security.
The Chinese embassy in Prague did not immediately respond to a request for comment. NATO and the European Union said they stood in solidarity with the Czech Republic.
Foreign Minister Jan Lipavsky said on X that after the attack was detected, the ministry implemented a new communications system with enhanced security.
6 months ago
A new COVID-19 variant sweeping through China has yet to make a sizable footprint in the U.S., the Centers for Disease Control and Prevention (CDC) says.
In January, a new COVID-19 variant known as NB.1.8.1 was first detected in China. On May 23, the World Health Organization (WHO) classified NB.1.8.1 as a variant that public health officials "may require prioritized attention and monitoring."
As of Tuesday, May 27, less than 20 cases of NB.1.8.1 had been reported in the U.S., a CDC spokesperson told USA TODAY. This figure is too low to be added to the CDC's COVID Data Tracker dashboard, the spokesperson added, though they did not clarify what the threshold for adding new variants to the dashboard is.
In January, a new COVID-19 variant known as NB.1.8.1 was first detected in China. On May 23, the World Health Organization (WHO) classified NB.1.8.1 as a variant that public health officials "may require prioritized attention and monitoring."
As of Tuesday, May 27, less than 20 cases of NB.1.8.1 had been reported in the U.S., a CDC spokesperson told USA TODAY. This figure is too low to be added to the CDC's COVID Data Tracker dashboard, the spokesperson added, though they did not clarify what the threshold for adding new variants to the dashboard is.
7 months ago
China struck a defiant stance on Tuesday in response to American concerns about Beijing's efforts to expand its influence in the resource-rich South American nation of Chile, escalating tensions over a Chinese astronomical venture in Chile’s arid north.
At a press conference Tuesday in Chile's capital of Santiago, China's ambassador to Chile, Niu Qingbao, lambasted the United States for “interfering in Chile’s sovereign right to independently choose its partners” and spreading "disinformation about the project.”
The astronomy project stems from a 2023 agreement between China's state-run National Astronomical Observatory and Chile's Catholic University of the North to work on a powerful space observatory in the country's vast northern Atacama Desert. The proposed high-resolution telescope would be able to observe near-Earth objects, which are classified as asteroids or comets.
But the project quickly became entangled in China's spiraling rivalry with the Trump administration.
At a press conference Tuesday in Chile's capital of Santiago, China's ambassador to Chile, Niu Qingbao, lambasted the United States for “interfering in Chile’s sovereign right to independently choose its partners” and spreading "disinformation about the project.”
The astronomy project stems from a 2023 agreement between China's state-run National Astronomical Observatory and Chile's Catholic University of the North to work on a powerful space observatory in the country's vast northern Atacama Desert. The proposed high-resolution telescope would be able to observe near-Earth objects, which are classified as asteroids or comets.
But the project quickly became entangled in China's spiraling rivalry with the Trump administration.
7 months ago
The infighting and backstabbing that plagued President Donald Trump’s first term have returned as a threat to his second, with deepening fissures over trade, national security and questions of personal loyalty.
The latest turmoil threatens to engulf the Pentagon, where Defense Secretary Pete Hegseth has pushed out top advisers and faces fresh controversy over sharing sensitive information about airstrikes in Yemen outside of classified channels. A former Pentagon spokesperson who was ousted last week wrote in Politico that Trump should fire Hegseth for presiding over a “full-blown meltdown."
Hegseth lashed out on Tuesday on Fox News Channel, where he was a weekend host before joining Trump's administration, by faulting the people who used to work for him.
“Those folks who were leaking, who have been pushed out of the building, are now attempting to leak and sabotage the president’s agenda," he said.
The latest turmoil threatens to engulf the Pentagon, where Defense Secretary Pete Hegseth has pushed out top advisers and faces fresh controversy over sharing sensitive information about airstrikes in Yemen outside of classified channels. A former Pentagon spokesperson who was ousted last week wrote in Politico that Trump should fire Hegseth for presiding over a “full-blown meltdown."
Hegseth lashed out on Tuesday on Fox News Channel, where he was a weekend host before joining Trump's administration, by faulting the people who used to work for him.
“Those folks who were leaking, who have been pushed out of the building, are now attempting to leak and sabotage the president’s agenda," he said.
8 months ago
Tech billionaire Elon Musk was slated to visit the Pentagon on Friday and attend a meeting of the Joint Chiefs of Staff that would touch on China, among other things, two United States officials confirmed to ABC News -- but that plan changed after The New York Times reported Musk would be briefed on potential China war plans.
Musk visited the Pentagon on Friday -- but instead of meeting with the Joint Chiefs, Musk met with Defense Secretary Pete Hegseth and staffers, a U.S. official said.
The meeting between Musk and the Joint Chiefs was to be at the unclassified level and attended virtually by Adm. Sam Paparo, the commander of U.S. Indo-Pacific Command, one official said. But some time between the publication of The New York Times story on Thursday and Musk's visit to the Pentagon Friday morning, the visit turned into just a meeting with Hegseth.
Musk visited the Pentagon on Friday -- but instead of meeting with the Joint Chiefs, Musk met with Defense Secretary Pete Hegseth and staffers, a U.S. official said.
The meeting between Musk and the Joint Chiefs was to be at the unclassified level and attended virtually by Adm. Sam Paparo, the commander of U.S. Indo-Pacific Command, one official said. But some time between the publication of The New York Times story on Thursday and Musk's visit to the Pentagon Friday morning, the visit turned into just a meeting with Hegseth.
8 months ago
President Donald Trump said Friday that Elon Musk should not be allowed to see top secret US plans for any war with China, in a rare admission that his billionaire ally's business links raised potential conflicts of interest.
Trump strongly denied media reports that the world's richest man, who is now leading the cost-cutting Department of Government Efficiency (DOGE), would receive a classified Pentagon briefing on its war strategy.
Tesla and Space X boss Musk has major business interests in China but also has huge US defense contracts, while his status as an unelected advisor to Trump has raised concerns about his influence.
"I don’t want to show it to anybody. You’re talking about a potential war with China," Trump told reporters in the Oval Office.
"Certainly you wouldn’t show it to a businessman who is helping us so much... Elon has businesses in China and he would be susceptible perhaps to that."
Trump strongly denied media reports that the world's richest man, who is now leading the cost-cutting Department of Government Efficiency (DOGE), would receive a classified Pentagon briefing on its war strategy.
Tesla and Space X boss Musk has major business interests in China but also has huge US defense contracts, while his status as an unelected advisor to Trump has raised concerns about his influence.
"I don’t want to show it to anybody. You’re talking about a potential war with China," Trump told reporters in the Oval Office.
"Certainly you wouldn’t show it to a businessman who is helping us so much... Elon has businesses in China and he would be susceptible perhaps to that."
8 months ago
President Donald Trump revoked security clearances for Joe Biden, Kamala Harris and a string of top Democrats and political foes in a presidential memo late Friday.
“I have determined that it is no longer in the national interest for the following individuals to access classified information,” Trump wrote.
He went on to name a list of 15 opponents and Biden-era officials, including Hillary Clinton, former Secretary of State Antony Blinken, former Wyoming Rep. Liz Cheney, former Illinois Rep. Adam Kinzinger and New York Attorney General Letitia James, who prosecuted Trump for fraud, as well as former president Biden’s entire family.
It is unclear what formal security clearance was possessed by some of the figures named in the memo. Trump had already announced his intention to rescind security clearance for Biden in February, and National Intelligence Director Tulsi Gabbard said on March 10 that she had revoked access for Blinken, James and others per Trump’s directive.
“I have determined that it is no longer in the national interest for the following individuals to access classified information,” Trump wrote.
He went on to name a list of 15 opponents and Biden-era officials, including Hillary Clinton, former Secretary of State Antony Blinken, former Wyoming Rep. Liz Cheney, former Illinois Rep. Adam Kinzinger and New York Attorney General Letitia James, who prosecuted Trump for fraud, as well as former president Biden’s entire family.
It is unclear what formal security clearance was possessed by some of the figures named in the memo. Trump had already announced his intention to rescind security clearance for Biden in February, and National Intelligence Director Tulsi Gabbard said on March 10 that she had revoked access for Blinken, James and others per Trump’s directive.
10 months ago
U.S. President Donald Trump says he expects Elon Musk to find billions of dollars of fraud and abuse at the Pentagon during an audit that the billionaire will lead.
"I'm going to tell him very soon, like maybe in 24 hours, to go check the Department of Education. ... Then I'm going to go, go to the military. Let's check the military," Trump said in a Super Bowl interview with Fox News' Brett Baier.
"We're going to find billions, hundreds of millions of dollars of fraud and abuse," Trump said of the largest federal department.
The Pentagon's budget is approaching $1 trillion per year. In December, then-President Joe Biden signed a bill authorizing $895 billion in defense spending for the fiscal year ending Sept. 30.
Critics say the efforts are likely illegal, risk exposing classified information and in practice are gutting entire agencies without congressional approval.
"I'm going to tell him very soon, like maybe in 24 hours, to go check the Department of Education. ... Then I'm going to go, go to the military. Let's check the military," Trump said in a Super Bowl interview with Fox News' Brett Baier.
"We're going to find billions, hundreds of millions of dollars of fraud and abuse," Trump said of the largest federal department.
The Pentagon's budget is approaching $1 trillion per year. In December, then-President Joe Biden signed a bill authorizing $895 billion in defense spending for the fiscal year ending Sept. 30.
Critics say the efforts are likely illegal, risk exposing classified information and in practice are gutting entire agencies without congressional approval.
10 months ago
Guatemalan President Bernardo Arévalo says that his country will accept migrants from other countries during a meeting with Secretary of State Marco Rubio.
Secretary of State Marco Rubio, who was tapped as the acting director of the United States Agency for International Development (USAID) just days ago, is taking on another new role in President Donald Trump's new administration.
Rubio is now also serving as the acting director of the U.S. Archives, ABC News reported, citing a high-level official. Fox News Digital reached out to the State Department for comment, but they did not immediately respond.
Trump signaled last month his intention of replacing the now-former national archivist Colleen Shogan, who was appointed by former President Joe Biden. The National Archives notified the Justice Department in early 2022 over classified documents Trump allegedly took with him to his Mar-a-Lago estate in Florida after leaving office.
Secretary of State Marco Rubio, who was tapped as the acting director of the United States Agency for International Development (USAID) just days ago, is taking on another new role in President Donald Trump's new administration.
Rubio is now also serving as the acting director of the U.S. Archives, ABC News reported, citing a high-level official. Fox News Digital reached out to the State Department for comment, but they did not immediately respond.
Trump signaled last month his intention of replacing the now-former national archivist Colleen Shogan, who was appointed by former President Joe Biden. The National Archives notified the Justice Department in early 2022 over classified documents Trump allegedly took with him to his Mar-a-Lago estate in Florida after leaving office.
10 months ago
The seeming alliance between the Lebanese Armed Forces (LAF) and the Hezbollah terrorist movement is adding greater urgency to calls for the Trump administration to pull the plug on its generous aid to the LAF.
"Hezbollah and the Lebanese army are the same," Edy Cohen, a Lebanese-born Israeli scholar of Hezbollah. Cohen, a researcher at the Eitan Center, added, "Trump must not fund the Lebanese" He noted the Lebanese army gave Hezbollah intelligence information about Israel.
Times newspaper said that an LAF chief sent a classified document to Hezbollah. The LAF‘s Suhil Bahij Gharb, who oversees military intelligence for southern Lebanon, secured the confidential material from a military facility run by the U.S., France and the U.N. interim force in Lebanon (UNIFIL)
On the day of President Donald Trump’s inauguration, the U.S. State Department posted a fact sheet about USA-LAF cooperation. "Since 2006, U.S. investments of more than $3 billion to the LAF enabled the Lebanese milit
"Hezbollah and the Lebanese army are the same," Edy Cohen, a Lebanese-born Israeli scholar of Hezbollah. Cohen, a researcher at the Eitan Center, added, "Trump must not fund the Lebanese" He noted the Lebanese army gave Hezbollah intelligence information about Israel.
Times newspaper said that an LAF chief sent a classified document to Hezbollah. The LAF‘s Suhil Bahij Gharb, who oversees military intelligence for southern Lebanon, secured the confidential material from a military facility run by the U.S., France and the U.N. interim force in Lebanon (UNIFIL)
On the day of President Donald Trump’s inauguration, the U.S. State Department posted a fact sheet about USA-LAF cooperation. "Since 2006, U.S. investments of more than $3 billion to the LAF enabled the Lebanese milit
10 months ago
https://afriprime.net/post...
Trump's release of assassination docs opens window into nation's most debated mysteries
A trove of long-classified government documents concerning some of the most politically charged killings in modern American history — including the assassination of former President John F. Kennedy — will finally be made available to the public. But that's just the start of the latest saga surrounding the killings, which have sparked fascination, conspiracy theories,
Trump's release of assassination docs opens window into nation's most debated mysteries
A trove of long-classified government documents concerning some of the most politically charged killings in modern American history — including the assassination of former President John F. Kennedy — will finally be made available to the public. But that's just the start of the latest saga surrounding the killings, which have sparked fascination, conspiracy theories,

Sign in
Share your memories, connect with others, make new friends
https://afriprime.net/posts/90454
10 months ago
President-elect Donald Trump said on Sunday he would release classified documents in the coming days related to the assassinations of U.S. President John F. Kennedy, Senator Robert Kennedy and civil rights leader Martin Luther King Jr.
Trump, who returns to the White House on Monday, promised on the campaign trail to release classified intelligence and law enforcement files on the 1963 assassination of JFK, as America's 35th president is widely known.
He had made a similar promise during his 2017 to 2021 term, but he ultimately bowed to pressure from the Central Intelligence Agency and Federal Bureau of Investigation, and kept a significant chunk of documents under wraps, citing national security concerns.
"In the coming days, we are going to make public remaining records related to the assassinations of President John F. Kennedy, his brother Robert Kennedy, as well as Dr. Martin Luther King Jr. and other topics of great public interest,"
Trump, who returns to the White House on Monday, promised on the campaign trail to release classified intelligence and law enforcement files on the 1963 assassination of JFK, as America's 35th president is widely known.
He had made a similar promise during his 2017 to 2021 term, but he ultimately bowed to pressure from the Central Intelligence Agency and Federal Bureau of Investigation, and kept a significant chunk of documents under wraps, citing national security concerns.
"In the coming days, we are going to make public remaining records related to the assassinations of President John F. Kennedy, his brother Robert Kennedy, as well as Dr. Martin Luther King Jr. and other topics of great public interest,"
12 months ago
The U.S. voiced concern about potential foreign interference in Romania's presidential election after the declassification of documents showing the country was a target of "aggressive hybrid Russian attacks" during a period of three consecutive ballots.
Having previously polled in single digits, pro-Russia ultranationalist Calin Georgescu surged to victory in the first presidential election round on Nov. 24, causing widespread surprise in the European Union and NATO member state.
Documents declassified by Romania's top security council on Wednesday showed Georgescu was massively promoted on social media platform TikTok through coordinated accounts, recommendation algorithms and paid promotion. Georgescu has declared zero funds spent in the campaign.
They also showed compromised login data to Romanian election websites and over 85,000 cyber attacks during the election. Romania's intelligence agency said the campaign's size, methods and coordination pointed to a foreign state.
Having previously polled in single digits, pro-Russia ultranationalist Calin Georgescu surged to victory in the first presidential election round on Nov. 24, causing widespread surprise in the European Union and NATO member state.
Documents declassified by Romania's top security council on Wednesday showed Georgescu was massively promoted on social media platform TikTok through coordinated accounts, recommendation algorithms and paid promotion. Georgescu has declared zero funds spent in the campaign.
They also showed compromised login data to Romanian election websites and over 85,000 cyber attacks during the election. Romania's intelligence agency said the campaign's size, methods and coordination pointed to a foreign state.
12 months ago
A former British soldier whose audacious escape from a London prison spurred a dayslong search was convicted on Thursday of spying for Iran.
Daniel Khalife, 23, was found guilty by a jury in Woolwich Crown Court on violations of Britain's Official Secrets Act and Terrorism Act by collecting information useful to an enemy — Iran. He was cleared of a charge of planting fake bombs in his military barracks.
Prosecutors said Khalife played a “cynical game” by claiming he wanted to be a spy after he had delivered a large amount of restricted and classified material to the Iranian intelligence service, including the names of special forces officers.
Khalife testified that he had been in touch with people in the Iranian government but that it was all part of a ploy to ultimately work as a double agent for Britain, a scheme he developed from watching the TV show “Homeland.”
Daniel Khalife, 23, was found guilty by a jury in Woolwich Crown Court on violations of Britain's Official Secrets Act and Terrorism Act by collecting information useful to an enemy — Iran. He was cleared of a charge of planting fake bombs in his military barracks.
Prosecutors said Khalife played a “cynical game” by claiming he wanted to be a spy after he had delivered a large amount of restricted and classified material to the Iranian intelligence service, including the names of special forces officers.
Khalife testified that he had been in touch with people in the Iranian government but that it was all part of a ploy to ultimately work as a double agent for Britain, a scheme he developed from watching the TV show “Homeland.”
1 yr. ago
A pair of Democratic senators called for a federal investigation into Elon Musk’s involvement in SpaceX’s federal contracts following reports the tech billionaire has been in regular contact with Russian President Vladimir Putin.
In a letter sent Friday, Senate Armed Services Committee Chair Jack Reed (D-R.I.) and Sen. Jeanne Shaheen (D-N.H.) said Musk’s reported relations with a U.S. adversary “pose serious questions” about his “reliability as a government contract and a clearance holder.”
Musk’s aerospace company, SpaceX, holds contracts with the Department of Defense and Intelligence Community worth billions of dollars. He is also a “prime contractor” for the Space Force’s National Security Space program and holds a $1.8 billion classified contract with the National Reconnaissance Office, the lawmakers noted.
The tech entrepreneur has reportedly claimed he holds a U.S. security clearance as part of these federal agreements.
In a letter sent Friday, Senate Armed Services Committee Chair Jack Reed (D-R.I.) and Sen. Jeanne Shaheen (D-N.H.) said Musk’s reported relations with a U.S. adversary “pose serious questions” about his “reliability as a government contract and a clearance holder.”
Musk’s aerospace company, SpaceX, holds contracts with the Department of Defense and Intelligence Community worth billions of dollars. He is also a “prime contractor” for the Space Force’s National Security Space program and holds a $1.8 billion classified contract with the National Reconnaissance Office, the lawmakers noted.
The tech entrepreneur has reportedly claimed he holds a U.S. security clearance as part of these federal agreements.
1 yr. ago
In one form or another, all of America’s major enemies — China, Russia, North Korea and Iran — are intervening in and taking advantage of our election.
North Korea just had its say by directly joining Russia’s invasion of Ukraine; South Korean and Ukrainian officials reported last week that some North Korean personnel, probably military engineers, were killed in Ukraine.
U.S. intelligence then declassified a report that said at least 3,000 North Korean soldiers are undergoing combat training in Russia, a development that U.S officials say could have global implications. Ukrainian intelligence places the number at 12,000.
“It’s effectively the participation of a second state in the war against Ukraine on the side of Russia,” President Volodymyr Zelensky announced to Ukraine’s Parliament.
Though Western intelligence and political leaders were clearly surprised by the deployments, they logically operationalize the Russia-North Korea strategic partnership announced in June.
North Korea just had its say by directly joining Russia’s invasion of Ukraine; South Korean and Ukrainian officials reported last week that some North Korean personnel, probably military engineers, were killed in Ukraine.
U.S. intelligence then declassified a report that said at least 3,000 North Korean soldiers are undergoing combat training in Russia, a development that U.S officials say could have global implications. Ukrainian intelligence places the number at 12,000.
“It’s effectively the participation of a second state in the war against Ukraine on the side of Russia,” President Volodymyr Zelensky announced to Ukraine’s Parliament.
Though Western intelligence and political leaders were clearly surprised by the deployments, they logically operationalize the Russia-North Korea strategic partnership announced in June.
1 yr. ago
Documents purported to show classified U.S. intelligence gathering on Israel's preparations for a potential retaliatory strike on Iran appeared on social media platforms this week. It is unclear what impact the potential leak may have on any Israeli military planning for a possible strike on Iran, or Israeli-American relations.
U.S. officials declined to provide comment when contacted.
Nobody has independently verify the authenticity of the documents, which appear to show specific details about the types and number of munitions that Israel may be readying for a potentially large-scale strike on Iran in retaliation for the regime's late September barrage of almost 200 ballistic missiles aimed at Israel.
The documents posted on social media have markings that would indicate that they originated from the National Geospatial-Intelligence Agency (NGA), the U.S. agency that collects, analyzes and distributes intelligence gleaned from satellite and aerial imagery.
U.S. officials declined to provide comment when contacted.
Nobody has independently verify the authenticity of the documents, which appear to show specific details about the types and number of munitions that Israel may be readying for a potentially large-scale strike on Iran in retaliation for the regime's late September barrage of almost 200 ballistic missiles aimed at Israel.
The documents posted on social media have markings that would indicate that they originated from the National Geospatial-Intelligence Agency (NGA), the U.S. agency that collects, analyzes and distributes intelligence gleaned from satellite and aerial imagery.
1 yr. ago
Israeli officials, including Prime Minister Benjamin Netanyahu, have assured the United States that a counterstrike on Iran will be limited to military targets rather than oil or nuclear facilities.
President Biden, who has conveyed in public his opposition to striking Tehran’s nuclear and oil facilities, discussed Israel’s plans with Netanyahu during a classified phone call last week. In that conversation, Netanyahu relayed to Biden his plan to hit military targets.
Netanyahu had reassured Biden of his plans to avoid nuclear and oil targets.
Netanyahu’s office said it will consider US opinions but ultimately decide its response to Iran’s October 1 attack based on its own national interests. And American officials said they were still closely coordinating with Israel as it decides how to respond.
“We listen to the opinions of the United States, but we will make our final decisions based on our national interests,” Netanyahu’s office.
President Biden, who has conveyed in public his opposition to striking Tehran’s nuclear and oil facilities, discussed Israel’s plans with Netanyahu during a classified phone call last week. In that conversation, Netanyahu relayed to Biden his plan to hit military targets.
Netanyahu had reassured Biden of his plans to avoid nuclear and oil targets.
Netanyahu’s office said it will consider US opinions but ultimately decide its response to Iran’s October 1 attack based on its own national interests. And American officials said they were still closely coordinating with Israel as it decides how to respond.
“We listen to the opinions of the United States, but we will make our final decisions based on our national interests,” Netanyahu’s office.
1 yr. ago
China is menacing Taiwan with a drone swarm attack — and the US is playing catch-up
China is menacing Taiwan with the threat of invasion
A military strike on the US ally could involve a vast drone attack.
Taiwan and the US must boost the island's capacity to fight
The narrow strait separating the island from the mainland would likely be transformed into a ferocious battlefield
Vast fleets of unmanned aerial and naval drones will likely darken the skies and hide beneath waves, bringing with them a deadly threat that Taiwan and its allies are ill-prepared to counter.
Drones could be deployed by China to swarm over Taiwan and guide high-precision missile strikes
One way to counter China's assumed strategy is a US plan called "Hellscape"
"I want to turn the Taiwan Strait into an unmanned hellscape using a number of classified capabilities" Adm. Paparo told the publication. "So that I can make their lives utterly miserable for a month, which buys me the time for the rest of
China is menacing Taiwan with the threat of invasion
A military strike on the US ally could involve a vast drone attack.
Taiwan and the US must boost the island's capacity to fight
The narrow strait separating the island from the mainland would likely be transformed into a ferocious battlefield
Vast fleets of unmanned aerial and naval drones will likely darken the skies and hide beneath waves, bringing with them a deadly threat that Taiwan and its allies are ill-prepared to counter.
Drones could be deployed by China to swarm over Taiwan and guide high-precision missile strikes
One way to counter China's assumed strategy is a US plan called "Hellscape"
"I want to turn the Taiwan Strait into an unmanned hellscape using a number of classified capabilities" Adm. Paparo told the publication. "So that I can make their lives utterly miserable for a month, which buys me the time for the rest of
1 yr. ago
Donald Trump is clearly not happy about the release of a bombshell 165-page motion Wednesday filed by Special Counsel Jack Smith which lays out a sprawling timeline of how the former president attempted to claw his way back into power after losing the 2020 election.
He then repeated many of those claims in an almost-two-minute rant with NewsNation Wednesday night, in which Trump bragged about winning the classified documents case in Florida, described Democratic opponent Kamala Harris as “more incompetent than Biden,” and claimed the accusations within the document are “nothing new.”
“The release of this falsehood-ridden, Unconstitutional, J6 brief immediately following Tim Walz’s disastrous Debate performance, and 33 days before the Most Important Election in the History of our Country, is another obvious attempt by the Harris-Biden regime to undermine and Weaponize American Democracy, and INTERFERE IN THE 2024 PRESIDENTIAL ELECTION.”
He then repeated many of those claims in an almost-two-minute rant with NewsNation Wednesday night, in which Trump bragged about winning the classified documents case in Florida, described Democratic opponent Kamala Harris as “more incompetent than Biden,” and claimed the accusations within the document are “nothing new.”
“The release of this falsehood-ridden, Unconstitutional, J6 brief immediately following Tim Walz’s disastrous Debate performance, and 33 days before the Most Important Election in the History of our Country, is another obvious attempt by the Harris-Biden regime to undermine and Weaponize American Democracy, and INTERFERE IN THE 2024 PRESIDENTIAL ELECTION.”




