17 days ago
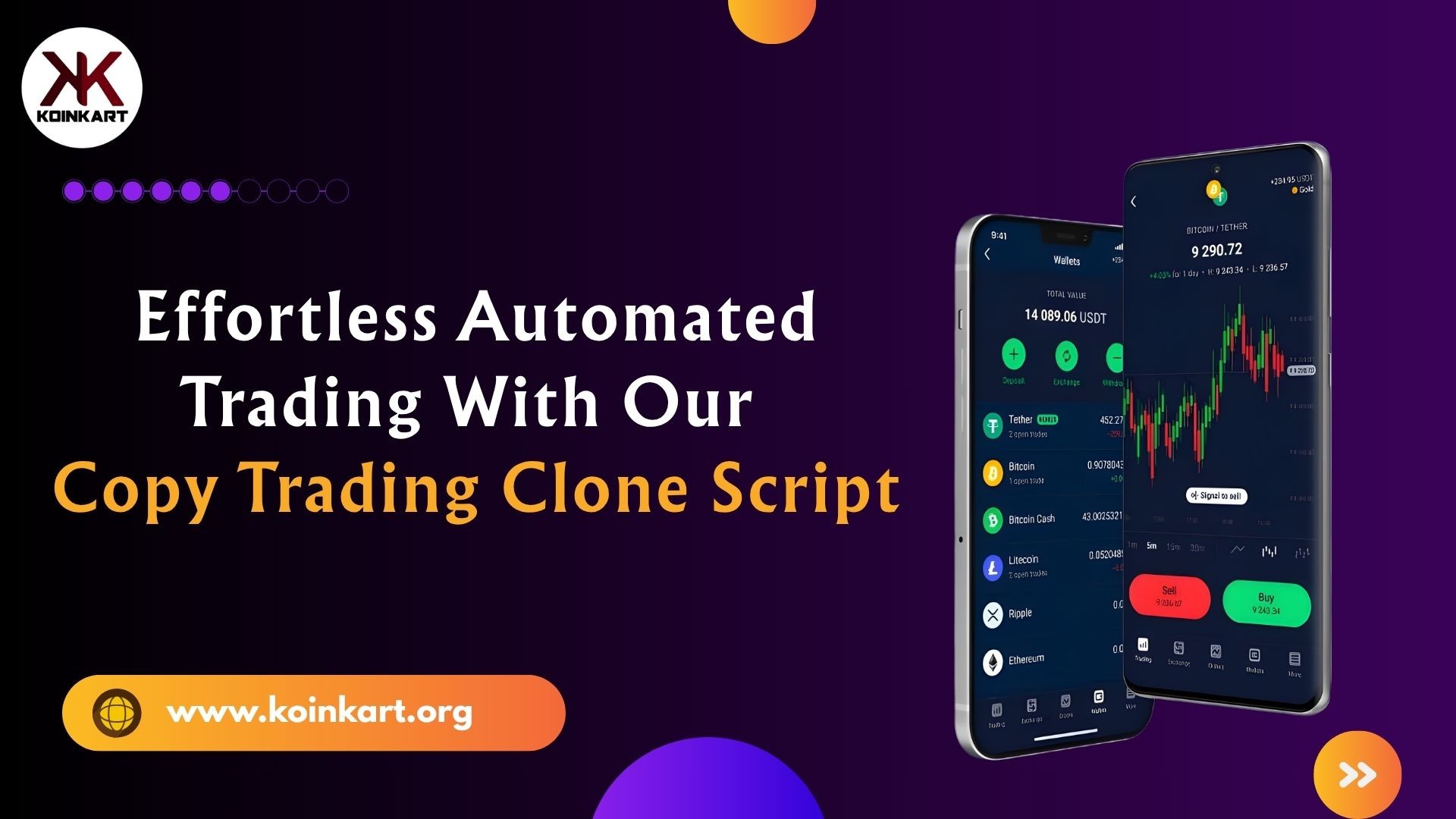
Effortless Automated Trading With Our Copy Trading Clone Script
Effortless automated trading is now possible with our advanced Copy Trading Clone Script. Koinkart is the premier Copy Trading Clone Script provider, trusted for high performance and smooth trading automation. Designed for business owners and crypto platforms, this ready-made solution helps your users copy expert trades in real time and grow faster.
Explore the features designed for our clients:
Auto-copy trades from top-performing traders
Secure architecture with high-level encryption
Real-time analytics and performance dashboards
Multi-asset support for flexible trading
Easy admin control with revenue-driven modules
Get Live Demo or Quote Now!
Website: https://www.koinkart.org/c...
WhatsApp: +91 93842 63771
Mail: businesskoinkart.org
Effortless automated trading is now possible with our advanced Copy Trading Clone Script. Koinkart is the premier Copy Trading Clone Script provider, trusted for high performance and smooth trading automation. Designed for business owners and crypto platforms, this ready-made solution helps your users copy expert trades in real time and grow faster.
Explore the features designed for our clients:
Auto-copy trades from top-performing traders
Secure architecture with high-level encryption
Real-time analytics and performance dashboards
Multi-asset support for flexible trading
Easy admin control with revenue-driven modules
Get Live Demo or Quote Now!
Website: https://www.koinkart.org/c...
WhatsApp: +91 93842 63771
Mail: businesskoinkart.org
20 days ago
Start a Profitable Crypto Exchange Business Using the Coinbase Clone Script
Koinkart is the leading provider of a Coinbase Clone Script, crafted to help entrepreneurs and enterprises build a highly profitable, ROI-focused crypto trading platform that drives growth and long-term financial success. Our script is developed with advanced technologies to ensure smooth performance, scalability, and continuous revenue flow.
We list out the features offered for our clients:
Multiple Revenue Streams
High-Performance Trading Engine
Advanced Liquidity & Market-Making Tools
Native Token Integration:
Comprehensive Admin Control:
WhatsApp: +91 93842 63771
Mail: businesskoinkart.org
Website: https://www.koinkart.org/c...
Koinkart is the leading provider of a Coinbase Clone Script, crafted to help entrepreneurs and enterprises build a highly profitable, ROI-focused crypto trading platform that drives growth and long-term financial success. Our script is developed with advanced technologies to ensure smooth performance, scalability, and continuous revenue flow.
We list out the features offered for our clients:
Multiple Revenue Streams
High-Performance Trading Engine
Advanced Liquidity & Market-Making Tools
Native Token Integration:
Comprehensive Admin Control:
WhatsApp: +91 93842 63771
Mail: businesskoinkart.org
Website: https://www.koinkart.org/c...
2 months ago
Advance your trading strategies with crypto trading bot development. Our expert team builds intelligent bots using algorithmic strategies, real-time analytics, and blockchain integration, delivering precise and efficient solutions for businesses and professional traders.
Explore More: https://www.addustechnolog...
#CryptoTradingBot #CryptoExchange #BlockchainDevelopment #tradingbot #bot #crypto #bitcoin #cryptocurrency #cryptotradingplatform #usa #dubi #uk
Explore More: https://www.addustechnolog...
#CryptoTradingBot #CryptoExchange #BlockchainDevelopment #tradingbot #bot #crypto #bitcoin #cryptocurrency #cryptotradingplatform #usa #dubi #uk
2 months ago
Expert Crypto Sniper Bot Development Services
Koinkart is the premier partner for Crypto Sniper bot development, focused on smart and reliable strategies. We design bots that follow proven signals and reduce noise so trades are more accurate and less stressful.
Check out the features here:
Focus on robust wallet encryption and secure API handling.
Multi-strategy engine
Built-in backtesting and live-paper trading options.
24/7 monitoring and incident alerts to keep bots live.
Ready to simplify trading and gain insights? Start with a free demo and setup guidance at Koinkart.org.
📲 Get Demo or Quote Now!
🌐 Website: https://www.koinkart.org/b...
📞 WhatsApp: +91 93842 63771
Koinkart is the premier partner for Crypto Sniper bot development, focused on smart and reliable strategies. We design bots that follow proven signals and reduce noise so trades are more accurate and less stressful.
Check out the features here:
Focus on robust wallet encryption and secure API handling.
Multi-strategy engine
Built-in backtesting and live-paper trading options.
24/7 monitoring and incident alerts to keep bots live.
Ready to simplify trading and gain insights? Start with a free demo and setup guidance at Koinkart.org.
📲 Get Demo or Quote Now!
🌐 Website: https://www.koinkart.org/b...
📞 WhatsApp: +91 93842 63771
2 months ago
We build user-friendly crypto exchange platforms for businesses. Our development services help companies simplify trading, attract global users, and grow revenue while staying competitive in the fast-changing digital finance world.
To More Information : https://www.addustechnolog...
#CryptoExchangeDevelopmentCompany #cryptoexchangesoftwaredevelopment #GlobalBusinessSolutions #Cryptocurrencyexchangedevelopmentcompany #BlockchainForBusiness
To More Information : https://www.addustechnolog...
#CryptoExchangeDevelopmentCompany #cryptoexchangesoftwaredevelopment #GlobalBusinessSolutions #Cryptocurrencyexchangedevelopmentcompany #BlockchainForBusiness
2 months ago
Koinkart Develop a Crypto Sniper Bot with high-speed solution
Expand your trading opportunities with Koinkart. Our Crypto Sniper Bot Development service delivers a high-speed solution that helps traders capture profits with split-second accuracy. Built for traders who want smarter entries and exits without missing opportunities.
We list out the features offered for our clients:
• Automated instant order execution
• Real-time market scanning and alerts
• Smart risk controls and take-profit settings
• User-friendly dashboard with performance tracking
• Secure architecture and regular updates
📲 Get Demo or Quote Now!
🌐 Website: https://www.koinkart.org/b...
📞 WhatsApp: +91 93842 63771
Expand your trading opportunities with Koinkart. Our Crypto Sniper Bot Development service delivers a high-speed solution that helps traders capture profits with split-second accuracy. Built for traders who want smarter entries and exits without missing opportunities.
We list out the features offered for our clients:
• Automated instant order execution
• Real-time market scanning and alerts
• Smart risk controls and take-profit settings
• User-friendly dashboard with performance tracking
• Secure architecture and regular updates
📲 Get Demo or Quote Now!
🌐 Website: https://www.koinkart.org/b...
📞 WhatsApp: +91 93842 63771
3 months ago
Grow your crypto profits with our Triangular Arbitrage Bot Development solutions. Detect real-time price differences, minimize risks, and achieve steady returns through advanced automation designed for traders, startups, and global enterprises.
To More Information : https://www.addustechnolog...
#CryptoTrading #ArbitrageBot #CryptoProfits #BlockchainSolutions #TradingAutomation #CryptoInvestment #CryptoBusiness #FinTechSolutions #CryptoMarket
To More Information : https://www.addustechnolog...
#CryptoTrading #ArbitrageBot #CryptoProfits #BlockchainSolutions #TradingAutomation #CryptoInvestment #CryptoBusiness #FinTechSolutions #CryptoMarket
3 months ago
Get a Customizable Trust Wallet Clone Script with Advanced Security
Koinkart.org delivers a flexible Trust Wallet Clone Script for businesses ready to launch their own crypto wallet. Our script offers extensive customization and top-notch security measures.
Multi-layered encryption to safeguard assets
Biometric and 2FA authentication
Private key storage under user control
Phishing protection and scam alerts
With strong security, users gain confidence to trade, store, and manage assets without risk. Protecting transactions has never been easier.
📲 Get Demo or Quote Now!
🌐 Website: https://www.koinkart.org/b...
📞 WhatsApp: +91 93842 63771
Koinkart.org delivers a flexible Trust Wallet Clone Script for businesses ready to launch their own crypto wallet. Our script offers extensive customization and top-notch security measures.
Multi-layered encryption to safeguard assets
Biometric and 2FA authentication
Private key storage under user control
Phishing protection and scam alerts
With strong security, users gain confidence to trade, store, and manage assets without risk. Protecting transactions has never been easier.
📲 Get Demo or Quote Now!
🌐 Website: https://www.koinkart.org/b...
📞 WhatsApp: +91 93842 63771
3 months ago
Develop Secure & Unique with Our Trust Wallet Clone Script For Multi-Currency
Koinkart.org introduces the upgraded Trust Wallet Clone Script, designed with advanced security features to protect digital assets and build user confidence. This powerful solution ensures private key ownership, multi-factor authentication, and real-time protection for every transaction.
We list out the features offered for our clients:
End-to-end encryption for safe transfers
Biometric authentication support
User-controlled private keys
Multi-layered security protocols
📲 Get Demo or Quote Now!
🌐 Website: https://www.koinkart.org/b...
📞 WhatsApp: +91 93842 63771
Koinkart.org introduces the upgraded Trust Wallet Clone Script, designed with advanced security features to protect digital assets and build user confidence. This powerful solution ensures private key ownership, multi-factor authentication, and real-time protection for every transaction.
We list out the features offered for our clients:
End-to-end encryption for safe transfers
Biometric authentication support
User-controlled private keys
Multi-layered security protocols
📲 Get Demo or Quote Now!
🌐 Website: https://www.koinkart.org/b...
📞 WhatsApp: +91 93842 63771
3 months ago
Koinkart Upgraded Binance Clone Script Software with Superior Features
Koinkart introduces the upgraded Binance clone script, packed with superior features to launch a professional crypto exchange effortlessly. Our advanced solution ensures high performance, robust security, and a seamless trading experience for users of all levels.
Enhanced Security: Multi-layer authentication, encrypted wallets, and real-time fraud detection
Fast Deployment: Fully functional exchange ready in weeks
User-Friendly Interface: Intuitive design with multi-language and multi-currency support
Advanced Trading Tools: Spot, margin, and futures trading with real-time charts
Scalable Architecture: Grow your exchange without limits
📲 Get Demo or Quote Now!
🌐 Website: https://www.koinkart.org/b...
📞 WhatsApp: +91 93842 63771
Koinkart introduces the upgraded Binance clone script, packed with superior features to launch a professional crypto exchange effortlessly. Our advanced solution ensures high performance, robust security, and a seamless trading experience for users of all levels.
Enhanced Security: Multi-layer authentication, encrypted wallets, and real-time fraud detection
Fast Deployment: Fully functional exchange ready in weeks
User-Friendly Interface: Intuitive design with multi-language and multi-currency support
Advanced Trading Tools: Spot, margin, and futures trading with real-time charts
Scalable Architecture: Grow your exchange without limits
📲 Get Demo or Quote Now!
🌐 Website: https://www.koinkart.org/b...
📞 WhatsApp: +91 93842 63771
3 months ago
Koinkart Upgraded Binance Clone Script Software with Superior Features
Koinkart introduces the upgraded Binance clone script, packed with superior features to launch a professional crypto exchange effortlessly. Our advanced solution ensures high performance, robust security, and a seamless trading experience for users of all levels.
Enhanced Security: Multi-layer authentication, encrypted wallets, and real-time fraud detection
Fast Deployment: Fully functional exchange ready in weeks
User-Friendly Interface: Intuitive design with multi-language and multi-currency support
Advanced Trading Tools: Spot, margin, and futures trading with real-time charts
Scalable Architecture: Grow your exchange without limits
📲 Get Demo or Quote Now!
🌐 Website: https://www.koinkart.org/b...
📞 WhatsApp: +91 93842 63771
Koinkart introduces the upgraded Binance clone script, packed with superior features to launch a professional crypto exchange effortlessly. Our advanced solution ensures high performance, robust security, and a seamless trading experience for users of all levels.
Enhanced Security: Multi-layer authentication, encrypted wallets, and real-time fraud detection
Fast Deployment: Fully functional exchange ready in weeks
User-Friendly Interface: Intuitive design with multi-language and multi-currency support
Advanced Trading Tools: Spot, margin, and futures trading with real-time charts
Scalable Architecture: Grow your exchange without limits
📲 Get Demo or Quote Now!
🌐 Website: https://www.koinkart.org/b...
📞 WhatsApp: +91 93842 63771
4 months ago
Data, Dollars, and Drones: Who Controls Tomorrow’s Tools?
“He who controls the data, programs the future. He who owns the drones, defends—or dictates—it. And he who prints the dollars, plays God with the global economy.”
The 21st century won’t be ruled by empires of land—it will be ruled by empires of data, capital, and surveillance technology. In this new world, algorithms shape minds, money moves faster than people, and drones fly where diplomacy dares not go.
But who truly owns these tools? Who benefits? And who is being left behind—or watched from above?
Data: The New Oil or the New Chains?
4.6 billion people are now online—most on mobile phones
Africa contributes a massive stream of digital behavior—but stores little of it locally
American and Chinese tech giants own 90% of global data traffic and storage
While data is harvested from Africa, Latin America, and Southeast Asia, it’s analyzed in Silicon Valley, processed in Shenzhen, and monetized without consent.
“We are not just users—we are the unpaid labor feeding AI.”
Even worse: data colonialism is rising—where nations are reduced to mere sources of behavioral raw material.
Dollars: Still King of a Decaying Kingdom
Despite talk of "de-dollarization":
The US dollar dominates 88% of global trade
Countries like Ghana, Pakistan, and Sri Lanka still face currency collapse based on Fed decisions
Dollar scarcity creates austerity, debt dependency, and policy handcuffs for many Global South nations
The IMF and World Bank, still largely Western-controlled, act as gatekeepers to emergency funds—often in exchange for structural reforms that weaken local industries and sovereignty.
“When Washington sneezes, African currencies catch pneumonia.”
Meanwhile, crypto and fintechs try to provide escape routes—but they face crackdowns or co-option.
Drones: From Warfare to Watchdogs
Once a futuristic fantasy, drones are now:
Weapons in proxy wars (Libya, Ethiopia, Ukraine)
Surveillance tools for regimes monitoring protests
Delivery agents for aid and vaccines in hard-to-reach zones
Business tools for agriculture and logistics
But who owns the skies?
China’s DJI controls over 70% of the global commercial drone market
US and Israeli military drones dominate combat zones
African countries import rather than manufacture—despite strong use cases
Drones may save lives—or spy on them. Liberate farmers—or be used to suppress dissent.
Who’s Really in Control?
Let’s break it down:
Tool Controlled By Impact on Global South
Data Big Tech (US, China) Extracted, not owned
Dollars US Federal Reserve Externalized pain
Drones China, US, Israel Imported, rarely made
In all three, the Global South is a consumer, not a controller. And Africa, in particular, risks becoming the testing ground, resource mine, and data farm for tomorrow’s tech empires.
The Risks of Dependency
Surveillance authoritarianism (via foreign-built tech)
Digital dictatorships (where information flow is centralized)
Economic instability (due to external financial control)
Policy blackmail (based on foreign data or financial leverage)
If tomorrow’s tools are not domestically owned or ethically governed, Africa and other regions may end up technologically colonized—even as they go digital.
What Can Be Done?
-Data Sovereignty
-Build local data centers
-Enact data protection laws
Push for digital commons and open-source alternatives
Financial Autonomy
Explore pan-African payment systems and stable coins
Create sovereign wealth tech funds
Reduce dependency on external aid tied to conditionalities
Drone & Tech Manufacturing
Invest in STEM education and hardware innovation
Support tech hubs and partnerships with ethical manufacturers
Use drones for development, not just surveillance
Conclusion: Tools Are Not Neutral
Data, dollars, and drones will define this century. But they are not just neutral instruments—they are extensions of power, control, and ideology.
Africa and the rest of the Global South must ask:
Will we own the tools of tomorrow—or be owned by them?
This is not just a tech question.
It’s a question of sovereignty, freedom, and the shape of the future.
“He who controls the data, programs the future. He who owns the drones, defends—or dictates—it. And he who prints the dollars, plays God with the global economy.”
The 21st century won’t be ruled by empires of land—it will be ruled by empires of data, capital, and surveillance technology. In this new world, algorithms shape minds, money moves faster than people, and drones fly where diplomacy dares not go.
But who truly owns these tools? Who benefits? And who is being left behind—or watched from above?
Data: The New Oil or the New Chains?
4.6 billion people are now online—most on mobile phones
Africa contributes a massive stream of digital behavior—but stores little of it locally
American and Chinese tech giants own 90% of global data traffic and storage
While data is harvested from Africa, Latin America, and Southeast Asia, it’s analyzed in Silicon Valley, processed in Shenzhen, and monetized without consent.
“We are not just users—we are the unpaid labor feeding AI.”
Even worse: data colonialism is rising—where nations are reduced to mere sources of behavioral raw material.
Dollars: Still King of a Decaying Kingdom
Despite talk of "de-dollarization":
The US dollar dominates 88% of global trade
Countries like Ghana, Pakistan, and Sri Lanka still face currency collapse based on Fed decisions
Dollar scarcity creates austerity, debt dependency, and policy handcuffs for many Global South nations
The IMF and World Bank, still largely Western-controlled, act as gatekeepers to emergency funds—often in exchange for structural reforms that weaken local industries and sovereignty.
“When Washington sneezes, African currencies catch pneumonia.”
Meanwhile, crypto and fintechs try to provide escape routes—but they face crackdowns or co-option.
Drones: From Warfare to Watchdogs
Once a futuristic fantasy, drones are now:
Weapons in proxy wars (Libya, Ethiopia, Ukraine)
Surveillance tools for regimes monitoring protests
Delivery agents for aid and vaccines in hard-to-reach zones
Business tools for agriculture and logistics
But who owns the skies?
China’s DJI controls over 70% of the global commercial drone market
US and Israeli military drones dominate combat zones
African countries import rather than manufacture—despite strong use cases
Drones may save lives—or spy on them. Liberate farmers—or be used to suppress dissent.
Who’s Really in Control?
Let’s break it down:
Tool Controlled By Impact on Global South
Data Big Tech (US, China) Extracted, not owned
Dollars US Federal Reserve Externalized pain
Drones China, US, Israel Imported, rarely made
In all three, the Global South is a consumer, not a controller. And Africa, in particular, risks becoming the testing ground, resource mine, and data farm for tomorrow’s tech empires.
The Risks of Dependency
Surveillance authoritarianism (via foreign-built tech)
Digital dictatorships (where information flow is centralized)
Economic instability (due to external financial control)
Policy blackmail (based on foreign data or financial leverage)
If tomorrow’s tools are not domestically owned or ethically governed, Africa and other regions may end up technologically colonized—even as they go digital.
What Can Be Done?
-Data Sovereignty
-Build local data centers
-Enact data protection laws
Push for digital commons and open-source alternatives
Financial Autonomy
Explore pan-African payment systems and stable coins
Create sovereign wealth tech funds
Reduce dependency on external aid tied to conditionalities
Drone & Tech Manufacturing
Invest in STEM education and hardware innovation
Support tech hubs and partnerships with ethical manufacturers
Use drones for development, not just surveillance
Conclusion: Tools Are Not Neutral
Data, dollars, and drones will define this century. But they are not just neutral instruments—they are extensions of power, control, and ideology.
Africa and the rest of the Global South must ask:
Will we own the tools of tomorrow—or be owned by them?
This is not just a tech question.
It’s a question of sovereignty, freedom, and the shape of the future.
4 months ago
How has North Korea allegedly used cybercrime (crypto theft, ransomware) to fund its regime?
North Korea has allegedly leveraged cybercrime, particularly cryptocurrency theft and ransomware, as a crucial and increasingly preferred method to fund its regime and, specifically, its illicit weapons programs.
This strategy is a direct response to the crippling international sanctions imposed on the country.
Here's how they've allegedly done it:
1. Circumventing Sanctions for Hard Currency:
Financial Isolation: North Korea faces severe international sanctions that cut off its access to traditional global financial systems. This makes it extremely difficult for the regime to acquire the foreign currency (like U.S. dollars or Euros) needed to import goods, technology, and components for its military and luxury items for its elite.
Cryptocurrency as an Alternative: Cryptocurrencies operate largely outside traditional banking regulations and centralized financial institutions. This makes them an attractive alternative for a sanctioned state. By stealing crypto, North Korea effectively generates hard currency that is harder to trace and block.
Funding WMD Programs: UN reports, U.S. government assessments, and cybersecurity firm analyses consistently state that the proceeds from these cybercrimes directly fund North Korea's prohibited weapons of mass destruction (WMD) programs, including nuclear weapons and ballistic missiles. Some estimates suggest cybercrime accounts for a significant portion, potentially 40% to 50% or more, of the regime's foreign currency income.
2. Cryptocurrency Theft: The Primary Goldmine
Massive Scale: North Korean hacking groups, notably the Lazarus Group and its sub-units like BlueNoroff, have stolen billions of dollars in cryptocurrency. For example, UN experts reported investigating 58 suspected North Korean cyberattacks between 2017 and 2023, valued at approximately $3 billion. The FBI recently attributed a single $1.5 billion hack against Bybit in February 2025 to North Korean actors.
Targeting Crypto Exchanges and DeFi Platforms:
Direct Hacks: They target centralized cryptocurrency exchanges, exploiting vulnerabilities in their security systems to steal large amounts of various cryptocurrencies.
Decentralized Finance (DeFi) Exploits: As the crypto landscape evolved, North Korean hackers shifted to more vulnerable DeFi platforms and "bridges" (which facilitate asset transfer between different blockchains). Notorious examples include the Harmony Horizon Bridge ($100 million+) and the Sky Mavis Ronin Bridge ($600 million+). DeFi platforms often have less stringent security and regulatory oversight, making them "softer targets."
Sophisticated Social Engineering: They employ elaborate social engineering tactics to gain initial access:
Fake Job Offers: Creating fake companies, LinkedIn profiles, and seemingly legitimate job opportunities to trick employees of crypto firms into downloading malicious software or revealing credentials.
Impersonation: Impersonating venture capitalists, recruiters, or other legitimate business contacts.
Deepfake Technology: Increasingly, they use AI-enabled deepfake technologies in video calls to disguise their appearance and build trust with targets.
Laundering Stolen Funds: After stealing the cryptocurrency, they employ sophisticated laundering techniques to convert it into fiat currency (like USD). This involves:
Mixing Services: Using "crypto mixers" like Tornado Cash (which was sanctioned by the U.S. Treasury for its role in laundering North Korean funds) to obscure the origin of the stolen assets.
Chain Hopping: Moving funds across multiple different blockchains to complicate tracing efforts.
Dispersing Funds: Spreading stolen assets across thousands of addresses to make tracking harder.
Conversion to Fiat: Eventually converting the "cleaned" crypto into traditional currencies through various brokers, often in countries with weaker anti-money laundering regulations.
3. Ransomware Attacks: Another Revenue Stream
Extortion and Disruption: Groups like Andariel, a Lazarus sub-group, have deployed ransomware (e.g., Maui ransomware) against a range of targets, including U.S. hospitals and healthcare providers.
Demanding Crypto Payments: Ransomware payments are typically demanded in cryptocurrency, providing another direct avenue for generating funds that are difficult to trace.
Double Extortion: Beyond just encrypting data, some groups engage in "double extortion," threatening to leak stolen sensitive data if the ransom isn't paid, increasing pressure on victims.
4. Illicit IT Worker Schemes:
While not strictly "cybercrime" in the hacking sense, this is a related and significant revenue stream that leverages North Korea's cyber talent.
Disguised Workers: North Korean IT workers, often highly skilled in programming and software development, fraudulently obtain remote freelance jobs globally, using false identities and documentation.
Funneling Wages: The wages earned from these legitimate-looking jobs are then funneled back to the North Korean regime, providing another source of foreign currency. Some reports indicate these workers also insert backdoors or malware into corporate systems they work on, potentially enabling future cybercrime or espionage.
In essence, North Korea has become an innovator in state-sponsored cybercrime out of necessity. Facing stringent sanctions, its regime has adapted by exploiting the nascent and less-regulated cryptocurrency ecosystem to generate a consistent and substantial stream of revenue, directly funding its strategic weapons programs and circumventing international efforts to curb its proliferation activities.
North Korea has allegedly leveraged cybercrime, particularly cryptocurrency theft and ransomware, as a crucial and increasingly preferred method to fund its regime and, specifically, its illicit weapons programs.
This strategy is a direct response to the crippling international sanctions imposed on the country.
Here's how they've allegedly done it:
1. Circumventing Sanctions for Hard Currency:
Financial Isolation: North Korea faces severe international sanctions that cut off its access to traditional global financial systems. This makes it extremely difficult for the regime to acquire the foreign currency (like U.S. dollars or Euros) needed to import goods, technology, and components for its military and luxury items for its elite.
Cryptocurrency as an Alternative: Cryptocurrencies operate largely outside traditional banking regulations and centralized financial institutions. This makes them an attractive alternative for a sanctioned state. By stealing crypto, North Korea effectively generates hard currency that is harder to trace and block.
Funding WMD Programs: UN reports, U.S. government assessments, and cybersecurity firm analyses consistently state that the proceeds from these cybercrimes directly fund North Korea's prohibited weapons of mass destruction (WMD) programs, including nuclear weapons and ballistic missiles. Some estimates suggest cybercrime accounts for a significant portion, potentially 40% to 50% or more, of the regime's foreign currency income.
2. Cryptocurrency Theft: The Primary Goldmine
Massive Scale: North Korean hacking groups, notably the Lazarus Group and its sub-units like BlueNoroff, have stolen billions of dollars in cryptocurrency. For example, UN experts reported investigating 58 suspected North Korean cyberattacks between 2017 and 2023, valued at approximately $3 billion. The FBI recently attributed a single $1.5 billion hack against Bybit in February 2025 to North Korean actors.
Targeting Crypto Exchanges and DeFi Platforms:
Direct Hacks: They target centralized cryptocurrency exchanges, exploiting vulnerabilities in their security systems to steal large amounts of various cryptocurrencies.
Decentralized Finance (DeFi) Exploits: As the crypto landscape evolved, North Korean hackers shifted to more vulnerable DeFi platforms and "bridges" (which facilitate asset transfer between different blockchains). Notorious examples include the Harmony Horizon Bridge ($100 million+) and the Sky Mavis Ronin Bridge ($600 million+). DeFi platforms often have less stringent security and regulatory oversight, making them "softer targets."
Sophisticated Social Engineering: They employ elaborate social engineering tactics to gain initial access:
Fake Job Offers: Creating fake companies, LinkedIn profiles, and seemingly legitimate job opportunities to trick employees of crypto firms into downloading malicious software or revealing credentials.
Impersonation: Impersonating venture capitalists, recruiters, or other legitimate business contacts.
Deepfake Technology: Increasingly, they use AI-enabled deepfake technologies in video calls to disguise their appearance and build trust with targets.
Laundering Stolen Funds: After stealing the cryptocurrency, they employ sophisticated laundering techniques to convert it into fiat currency (like USD). This involves:
Mixing Services: Using "crypto mixers" like Tornado Cash (which was sanctioned by the U.S. Treasury for its role in laundering North Korean funds) to obscure the origin of the stolen assets.
Chain Hopping: Moving funds across multiple different blockchains to complicate tracing efforts.
Dispersing Funds: Spreading stolen assets across thousands of addresses to make tracking harder.
Conversion to Fiat: Eventually converting the "cleaned" crypto into traditional currencies through various brokers, often in countries with weaker anti-money laundering regulations.
3. Ransomware Attacks: Another Revenue Stream
Extortion and Disruption: Groups like Andariel, a Lazarus sub-group, have deployed ransomware (e.g., Maui ransomware) against a range of targets, including U.S. hospitals and healthcare providers.
Demanding Crypto Payments: Ransomware payments are typically demanded in cryptocurrency, providing another direct avenue for generating funds that are difficult to trace.
Double Extortion: Beyond just encrypting data, some groups engage in "double extortion," threatening to leak stolen sensitive data if the ransom isn't paid, increasing pressure on victims.
4. Illicit IT Worker Schemes:
While not strictly "cybercrime" in the hacking sense, this is a related and significant revenue stream that leverages North Korea's cyber talent.
Disguised Workers: North Korean IT workers, often highly skilled in programming and software development, fraudulently obtain remote freelance jobs globally, using false identities and documentation.
Funneling Wages: The wages earned from these legitimate-looking jobs are then funneled back to the North Korean regime, providing another source of foreign currency. Some reports indicate these workers also insert backdoors or malware into corporate systems they work on, potentially enabling future cybercrime or espionage.
In essence, North Korea has become an innovator in state-sponsored cybercrime out of necessity. Facing stringent sanctions, its regime has adapted by exploiting the nascent and less-regulated cryptocurrency ecosystem to generate a consistent and substantial stream of revenue, directly funding its strategic weapons programs and circumventing international efforts to curb its proliferation activities.
4 months ago
What are some known North Korean hacking groups (e.g., Lazarus Group) and their main motives?
North Korea's hacking groups are distinct from those of many other nations due to their overwhelming primary motivation: generating revenue for the regime and funding its illicit weapons programs, particularly nuclear and ballistic missile development, in circumvention of severe international sanctions.
While they also engage in espionage, the financial imperative is paramount.
Here are some of the most well-known North Korean hacking groups (often considered sub-groups or operations under the broader "Lazarus Group" umbrella) and their main motives and alleged activities:
Lazarus Group (Aliases: APT38, Hidden Cobra, Guardians of Peace, ZINC, Diamond Sleet)
The Lazarus Group is the overarching umbrella term for North Korea's state-sponsored cyber operations. It's a highly sophisticated and prolific entity with various subdivisions specializing in different types of attacks.
Main Motives of Lazarus Group as a Whole:
Financial Gain (Primary): To generate illicit revenue for the Kim Jong Un regime, circumventing international sanctions that heavily restrict North Korea's access to traditional financial systems. This funding directly supports their weapons of mass destruction (WMD) and ballistic missile programs.
Cyber Espionage: To gather strategic intelligence on foreign governments, military capabilities, advanced technologies, and internal political dynamics, particularly concerning South Korea, the U.S., and Japan.
Destruction/Disruption: To cause disruption, sow fear, or retaliate against perceived adversaries.
Influence Operations: To shape public opinion or undermine trust in institutions, especially in South Korea.
Accusations and Notable Activities:
Sony Pictures Entertainment Hack (2014): One of their most infamous early operations, involving the theft of massive amounts of data (unreleased films, emails, personal employee info) and destructive wiper attacks on Sony's network, seemingly in retaliation for the film "The Interview."
Bangladesh Bank Heist (2016): A sophisticated operation that attempted to steal nearly $1 billion from Bangladesh Bank's account at the New York Federal Reserve via SWIFT messages, with $81 million successfully stolen and laundered.
WannaCry Ransomware Attack (2017): Widely attributed to Lazarus, this global ransomware worm exploited a Windows vulnerability (EternalBlue) to encrypt data and demand ransom payments, causing massive disruption to critical services worldwide.
Extensive Cryptocurrency Thefts: This has become their most consistent and lucrative line of effort. They have stolen billions of dollars in cryptocurrencies from exchanges, DeFi platforms, and individual wallets globally through phishing, social engineering, and exploiting vulnerabilities. Examples include the hacks of Harmony's Horizon Bridge ($100M+), Sky Mavis' Ronin Bridge ($600M+), and Bybit ($1.5B+ in 2025).
Sub-Groups of Lazarus:
North Korea often operates through specialized sub-groups that share resources and coordinate under the broader Lazarus umbrella.
1. BlueNoroff (Aliases: APT38, Sapphire Sleet, Alluring Pisces, TraderTraitor, UNC4899, CryptoCore)
Main Motive: Exclusively focused on large-scale financial theft, particularly targeting banks, financial institutions, and more recently, cryptocurrency exchanges and Web3 companies. They aim to steal vast sums of money for the regime.
Accusations and Notable Activities:
Bank Heists: Known for sophisticated attacks on traditional financial institutions, often involving deep reconnaissance of bank systems and SWIFT networks (e.g., the Bangladesh Bank Heist, attacks on banks in Poland, Mexico, Taiwan, etc.).
Cryptocurrency Theft: Currently one of the most active in this domain, using highly sophisticated social engineering tactics (e.g., fake job offers, deepfake Zoom calls) to trick employees of crypto firms into installing malware that facilitates the theft of digital assets. They often create elaborate fake companies and profiles.
2. Kimsuky (Aliases: Emerald Sleet, Velvet Chollima, TEMP.Firework)
Main Motive: Primarily focused on cyber espionage and intelligence gathering, specifically targeting South Korean government entities, think tanks, academic institutions, defense companies, and individuals involved in foreign policy and national security related to the Korean Peninsula, nuclear policy, and sanctions. They also target individuals in the US and Japan.
Accusations and Notable Activities:
Spear-Phishing Campaigns: Known for highly targeted spear-phishing emails, often impersonating legitimate contacts or organizations (e.g., South Korean government officials, journalists, academics) to deliver malware for intelligence collection. They use clever social engineering to trick victims into running malicious PowerShell scripts or installing backdoors.
Theft of Sensitive Data: Accused of stealing information related to inter-Korean affairs, nuclear negotiations, and sanctions enforcement.
Use of Illicit IT Worker Schemes: Some reporting links Kimsuky to the broader scheme of North Korean IT workers fraudulently gaining remote jobs globally, with the salaries funneled back to the regime. (While this scheme also funds the regime, Kimsuky's primary cyber mission remains espionage).
3. Andariel (Aliases: APT45, Silent Chollima, Onyx Fleet)
Main Motive: A mix of financial gain (often through ransomware) and cyber espionage, with a particular focus on military and defense information, especially targeting South Korea. They are also linked to direct revenue generation for the regime.
Accusations and Notable Activities:
Ransomware Deployments: Known for deploying ransomware, including Maui ransomware, against healthcare and critical infrastructure organizations to extort funds.
Stealing Defense Information: Accused of stealing technical information related to anti-aircraft weapon systems from South Korean defense companies.
ATM Cash-outs and Fraud: Engaging in activities like hacking into ATMs to withdraw cash or stealing bank card information for sale on the black market.
Illicit IT Worker Schemes: Recent U.S. sanctions (July 2025) have directly linked an individual associated with Andariel (Song Kum Hyok) to the fraudulent IT worker scheme that funnels money back to North Korea's weapons programs. This indicates a more direct role in generating revenue through non-cyber-attack means, complementing their cyber-enabled activities.
In summary, North Korean hacking groups are unique in their pervasive focus on generating illicit funds, primarily through large-scale cryptocurrency theft and financial fraud, to sustain the isolated regime and its nuclear ambitions. This financial imperative often goes hand-in-hand with strategic cyber espionage and, at times, disruptive operations designed to achieve Pyongyang's geopolitical goals.
North Korea's hacking groups are distinct from those of many other nations due to their overwhelming primary motivation: generating revenue for the regime and funding its illicit weapons programs, particularly nuclear and ballistic missile development, in circumvention of severe international sanctions.
While they also engage in espionage, the financial imperative is paramount.
Here are some of the most well-known North Korean hacking groups (often considered sub-groups or operations under the broader "Lazarus Group" umbrella) and their main motives and alleged activities:
Lazarus Group (Aliases: APT38, Hidden Cobra, Guardians of Peace, ZINC, Diamond Sleet)
The Lazarus Group is the overarching umbrella term for North Korea's state-sponsored cyber operations. It's a highly sophisticated and prolific entity with various subdivisions specializing in different types of attacks.
Main Motives of Lazarus Group as a Whole:
Financial Gain (Primary): To generate illicit revenue for the Kim Jong Un regime, circumventing international sanctions that heavily restrict North Korea's access to traditional financial systems. This funding directly supports their weapons of mass destruction (WMD) and ballistic missile programs.
Cyber Espionage: To gather strategic intelligence on foreign governments, military capabilities, advanced technologies, and internal political dynamics, particularly concerning South Korea, the U.S., and Japan.
Destruction/Disruption: To cause disruption, sow fear, or retaliate against perceived adversaries.
Influence Operations: To shape public opinion or undermine trust in institutions, especially in South Korea.
Accusations and Notable Activities:
Sony Pictures Entertainment Hack (2014): One of their most infamous early operations, involving the theft of massive amounts of data (unreleased films, emails, personal employee info) and destructive wiper attacks on Sony's network, seemingly in retaliation for the film "The Interview."
Bangladesh Bank Heist (2016): A sophisticated operation that attempted to steal nearly $1 billion from Bangladesh Bank's account at the New York Federal Reserve via SWIFT messages, with $81 million successfully stolen and laundered.
WannaCry Ransomware Attack (2017): Widely attributed to Lazarus, this global ransomware worm exploited a Windows vulnerability (EternalBlue) to encrypt data and demand ransom payments, causing massive disruption to critical services worldwide.
Extensive Cryptocurrency Thefts: This has become their most consistent and lucrative line of effort. They have stolen billions of dollars in cryptocurrencies from exchanges, DeFi platforms, and individual wallets globally through phishing, social engineering, and exploiting vulnerabilities. Examples include the hacks of Harmony's Horizon Bridge ($100M+), Sky Mavis' Ronin Bridge ($600M+), and Bybit ($1.5B+ in 2025).
Sub-Groups of Lazarus:
North Korea often operates through specialized sub-groups that share resources and coordinate under the broader Lazarus umbrella.
1. BlueNoroff (Aliases: APT38, Sapphire Sleet, Alluring Pisces, TraderTraitor, UNC4899, CryptoCore)
Main Motive: Exclusively focused on large-scale financial theft, particularly targeting banks, financial institutions, and more recently, cryptocurrency exchanges and Web3 companies. They aim to steal vast sums of money for the regime.
Accusations and Notable Activities:
Bank Heists: Known for sophisticated attacks on traditional financial institutions, often involving deep reconnaissance of bank systems and SWIFT networks (e.g., the Bangladesh Bank Heist, attacks on banks in Poland, Mexico, Taiwan, etc.).
Cryptocurrency Theft: Currently one of the most active in this domain, using highly sophisticated social engineering tactics (e.g., fake job offers, deepfake Zoom calls) to trick employees of crypto firms into installing malware that facilitates the theft of digital assets. They often create elaborate fake companies and profiles.
2. Kimsuky (Aliases: Emerald Sleet, Velvet Chollima, TEMP.Firework)
Main Motive: Primarily focused on cyber espionage and intelligence gathering, specifically targeting South Korean government entities, think tanks, academic institutions, defense companies, and individuals involved in foreign policy and national security related to the Korean Peninsula, nuclear policy, and sanctions. They also target individuals in the US and Japan.
Accusations and Notable Activities:
Spear-Phishing Campaigns: Known for highly targeted spear-phishing emails, often impersonating legitimate contacts or organizations (e.g., South Korean government officials, journalists, academics) to deliver malware for intelligence collection. They use clever social engineering to trick victims into running malicious PowerShell scripts or installing backdoors.
Theft of Sensitive Data: Accused of stealing information related to inter-Korean affairs, nuclear negotiations, and sanctions enforcement.
Use of Illicit IT Worker Schemes: Some reporting links Kimsuky to the broader scheme of North Korean IT workers fraudulently gaining remote jobs globally, with the salaries funneled back to the regime. (While this scheme also funds the regime, Kimsuky's primary cyber mission remains espionage).
3. Andariel (Aliases: APT45, Silent Chollima, Onyx Fleet)
Main Motive: A mix of financial gain (often through ransomware) and cyber espionage, with a particular focus on military and defense information, especially targeting South Korea. They are also linked to direct revenue generation for the regime.
Accusations and Notable Activities:
Ransomware Deployments: Known for deploying ransomware, including Maui ransomware, against healthcare and critical infrastructure organizations to extort funds.
Stealing Defense Information: Accused of stealing technical information related to anti-aircraft weapon systems from South Korean defense companies.
ATM Cash-outs and Fraud: Engaging in activities like hacking into ATMs to withdraw cash or stealing bank card information for sale on the black market.
Illicit IT Worker Schemes: Recent U.S. sanctions (July 2025) have directly linked an individual associated with Andariel (Song Kum Hyok) to the fraudulent IT worker scheme that funnels money back to North Korea's weapons programs. This indicates a more direct role in generating revenue through non-cyber-attack means, complementing their cyber-enabled activities.
In summary, North Korean hacking groups are unique in their pervasive focus on generating illicit funds, primarily through large-scale cryptocurrency theft and financial fraud, to sustain the isolated regime and its nuclear ambitions. This financial imperative often goes hand-in-hand with strategic cyber espionage and, at times, disruptive operations designed to achieve Pyongyang's geopolitical goals.
4 months ago
The crypto market is growing fast. People are buying, selling, and trading digital coins every day, and platforms like Coinbase have become a go-to for millions.
But if you’ve ever thought about starting your own exchange, you’ll know it’s not simple. Building one from the ground up takes months of coding, large budgets, and a skilled tech team.
A Coinbase Clone Script changes all that. It’s a ready-made solution with the features you need to run a crypto exchange. You can customise it to suit your brand, launch it quickly, and start earning sooner.
Website:https://www.thecryptoape.c...
Email : infothecryptoape.com
But if you’ve ever thought about starting your own exchange, you’ll know it’s not simple. Building one from the ground up takes months of coding, large budgets, and a skilled tech team.
A Coinbase Clone Script changes all that. It’s a ready-made solution with the features you need to run a crypto exchange. You can customise it to suit your brand, launch it quickly, and start earning sooner.
Website:https://www.thecryptoape.c...
Email : infothecryptoape.com
4 months ago
(E)
Still unsure how to integrate crypto payments into your business? You don’t need to start from zero.
With our CoinPayments Clone Script, you get a plug-and-play crypto payment gateway that’s secure, scalable, and ready to launch.
No technical stress. No delays.
✅ Accept 100+ cryptocurrencies
✅ Built-in merchant dashboard
✅ Instant global payments
✅ Full branding and API support
Whether you're a startup or scaling brand, we provide the tools to launch quickly, look professional, and stay competitive in the crypto space.
Go live in days, not months.
Let us handle the backend while you focus on growth.
Book your free Consultation !
Got Questions? Let’s Talk.
https://www.beleaftechnolo...
Whatsapp: +91 7904323274
Telegram: BeleafSoftTech
Mail to: businessbeleaftechnologies.com
With our CoinPayments Clone Script, you get a plug-and-play crypto payment gateway that’s secure, scalable, and ready to launch.
No technical stress. No delays.
✅ Accept 100+ cryptocurrencies
✅ Built-in merchant dashboard
✅ Instant global payments
✅ Full branding and API support
Whether you're a startup or scaling brand, we provide the tools to launch quickly, look professional, and stay competitive in the crypto space.
Go live in days, not months.
Let us handle the backend while you focus on growth.
Book your free Consultation !
Got Questions? Let’s Talk.
https://www.beleaftechnolo...
Whatsapp: +91 7904323274
Telegram: BeleafSoftTech
Mail to: businessbeleaftechnologies.com
4 months ago
Skip the Struggles, Go Live Faster with White Label Crypto Exchange Development - Beleaf Technologies
Stuck with a big crypto vision but no clue how to turn it into a working exchange?
It’s a common struggle—but the solution is simpler than you think.
With White Label Crypto Exchange Development , you get a fully customizable, ready-to-go platform built by experts who understand the tech, the security, and the speed the market demands.
✅ No coding headaches
✅ Bank-level security features
✅ Faster time to market
✅ Scalable to your business goals
We help you skip the complicated backend development and go live with a sleek, high-performing exchange that your users will trust.
Whether it’s spot trading, wallets, or admin dashboards . you get it all, built-in and branded as your own.
Don’t spend months or money building everything from scratch.
Let our proven solutions handle the heavy tech, while you focus on growing your brand and dominating the crypto space.
Stuck with a big crypto vision but no clue how to turn it into a working exchange?
It’s a common struggle—but the solution is simpler than you think.
With White Label Crypto Exchange Development , you get a fully customizable, ready-to-go platform built by experts who understand the tech, the security, and the speed the market demands.
✅ No coding headaches
✅ Bank-level security features
✅ Faster time to market
✅ Scalable to your business goals
We help you skip the complicated backend development and go live with a sleek, high-performing exchange that your users will trust.
Whether it’s spot trading, wallets, or admin dashboards . you get it all, built-in and branded as your own.
Don’t spend months or money building everything from scratch.
Let our proven solutions handle the heavy tech, while you focus on growing your brand and dominating the crypto space.
6 months ago
Trump Is Bleeding Hundreds of Millions Thanks to Musk’s War.
The explosion of Donald Trump’s once-cozy friendship with Elon Musk is hitting them hard where it hurts most—in the pocketbook.
As reported Thursday, Musk’s personal fortune was cut by $26.6 billion after Tesla shares slumped by more than 14 percent, wiping a mind-boggling $150 billion off the EV giant’s market value.
But Trump isn’t escaping unscathed. According to Axios, Trump Media & Technology Group stock declined 8 percent, while his MAGA-fueled $TRUMP cryptocurrency tumbled 12 percent—bleeding him of more than a billion dollars.
The website reported that the 8 percent dip in Trump Media & Technology Group cost the president around $202 million.
The explosion of Donald Trump’s once-cozy friendship with Elon Musk is hitting them hard where it hurts most—in the pocketbook.
As reported Thursday, Musk’s personal fortune was cut by $26.6 billion after Tesla shares slumped by more than 14 percent, wiping a mind-boggling $150 billion off the EV giant’s market value.
But Trump isn’t escaping unscathed. According to Axios, Trump Media & Technology Group stock declined 8 percent, while his MAGA-fueled $TRUMP cryptocurrency tumbled 12 percent—bleeding him of more than a billion dollars.
The website reported that the 8 percent dip in Trump Media & Technology Group cost the president around $202 million.
6 months ago
Alleged Chinese spy ‘plotted’ to make Xi critic ‘bang bang and gone’
A British father accused of spying for the Chinese Communist Party plotted to kidnap and kneecap a critic of Xi Jinping, according to an indictment.
John Miller, a businessman who owns a £1.5 million home in Tunbridge Wells that is flanked by two Chinese Terracotta warriors, is alleged to have tried to smuggle missiles and drones into China.
The 63-year-old, whose wife is a churchwarden in Kent, was described by neighbours as “funny, nice and perfectly normal”.
However, he is accused of attempting to traffic “sensitive American military technology” to China, including missiles, air defence radar and drones.
It is also alleged that he referred to Mr Xi, the Chinese president, as “the boss” in intercepted phone calls.
Court documents in the US state that Mr Miller wanted to have a Los Angeles artist who was a critic of Mr Xi “f---ed up”. He allegedly said his Chinese handlers were “bang up” for launching an attack on him with “bullets” instead of baseball bats.
In April, Mr Miller was arrested along with Cui Guanghai, a 43-year-old Chinese national, on the orders of the FBI in Serbia, where he is awaiting extradition to the US.
The pair were charged after approaching two individuals who, unbeknown to them, were working for the FBI.
Mr Miller is a permanent resident of the US but was born in the UK. He has held roles in at least five UK companies, including a firm that appeared to facilitate English language teaching jobs in China but is now dissolved.
On Sunday, neighbours described the Millers as a “perfect family”, and told of their surprise at his arrest.
One said: “He was a nice guy. Over and above that I didn’t know what he did for work. He was funny, nice and perfectly normal. He wasn’t cagey... I am astounded.
“It’s awful for him, and if he has done it he’s a bloody idiot, but it’s innocent until proven guilty. It’s slightly surreal.”
‘A kind man and good neighbour’
At the Parish Church of King Charles the Martyr, where Mr Miller’s wife Bea is a warden, Rev Laurence Powell said: “It is shocking to hear this about John. He is a very kind man and a good neighbour. I feel so sorry for Beatrice. She must be going through hell right now.”
Mr Miller is accused of employing a wide range of tactics over two and a half years to harass, intimidate, stalk and threaten the Xi critic in LA.
According to a 27-page indictment at the US District Court for the Central District of California, Mr Miller told a confidential FBI source that “the real f---ing pay... the real payday is going to be putting the siding up on that guy” and “there will be extra cash to play with when that happens”.
A special agent said “siding” meant an assault and that there had been an earlier conversation where Mr Miller “had discussed possibly kidnapping the victim”.
“They want it bang bang and gone,” Miller is quoted as saying in a recorded phone call. “No talking to, no nothing to, like a mugging or something. Take his f---ing watch. Take his phone.”
He is then asked if he cares if he preferred “bullets versus baseball bat”, before replying: “Um, not necessarily. But I think you’d get paid more for bullets. And the guys I spoke to said that’s way f---ing easier. Apparently, they’re not so much baseball bat, or like an ice pick is the best way of doing it.
“On the knees and ankles. Doesn’t necessarily have to be bullets. Have him f---ed up and have his picture taken. F---ed up. But the guys I’ve spoken to, the easiest thing is just bam bam bang bang and just walk away. But listen it doesn’t have to be that... knees and ankles.”
‘Chinese Christmas wish list’
Another phone call appears to show Mr Miller had arranged a payment with a “minimum” of $100,000 for the source to carry out the assault, and, when questioned if there was a problem from the female handler Mr Guanghai was reporting to, he replied: “Oh no no no no.
“She’s second in command. And her boss is bang up for it. There’s another guy who needs to approve it. But they’re all bang up for it. As long as it’s reasonable. The numbers we talked about I’m pretty sure it’s 100 per cent.”
The documents show that the pair also enlisted undercover agents to stop the victim from protesting against Mr Xi’s appearance at a summit and installed tracking devices on the victim’s car, and paid the undercover agents to slash their tyres.
They also devised a complex plan to destroy a set of statues created by the artist which depicted Mr Xi and his wife bare-chested, kneeling with their hands tied behind their backs.
Initially, Mr Miller had allegedly wanted to steal the statues and “remove the heads” as evidence but later decided to pay the undercover FBI agents to “smash up” them up.
In 2025, Mr Miller paid the agents $36,500 (£27,100) to convince the victim to desist from showcasing the new statues at an upcoming protest.
He also allegedly tried to purchase millions of pounds worth of military equipment on behalf of the Chinese military as part of a “Christmas wish list”. He is quoted as saying his buyers were “interested in the Western stuff” including armour plates for “tanks that the Yanks have”.
He reportedly tried to buy a £37,000 Stinger portable missile launcher, two military drones valued at £148,000, a £668,000 AGM-88E anti-radiation missile system and a £1.5 million air-defence radar system.
Mr Miller also allegedly tried to procure a cryptographic device, which is used for secure communication of classified and sensitive information.
At one point, the Briton allegedly suggested that the device be smuggled from the US to China by hiding it inside a food blender or a motor starter, having shipped it first via DHL or FedEx to Hong Kong.
‘Big boss’
Several times in Mr Miller’s conversations, he is said to have mentioned a “boss” or at times a “big boss” that seems to be the one giving orders.
According to the special FBI agent who submitted the affidavit, Mr Miller’s use of the phrase “boss” “refer[s] to President Xi” and “demonstrates [Miller’s] awareness that he was acting at the direction and control of the [Chinese] government.”
Todd Blanche, the US deputy attorney general, said: “This is a blatant assault on both our national security and our democratic values. This Justice Department will not tolerate foreign repression on US soil, nor will we allow hostile nations to infiltrate or exploit our defence systems.
“We will act decisively to expose and dismantle these threats wherever they emerge.”
If convicted, Mr Miller could also face the maximum penalties of five years in prison for conspiracy, five years in prison for interstate stalking, and 10 years in prison for smuggling.
A British father accused of spying for the Chinese Communist Party plotted to kidnap and kneecap a critic of Xi Jinping, according to an indictment.
John Miller, a businessman who owns a £1.5 million home in Tunbridge Wells that is flanked by two Chinese Terracotta warriors, is alleged to have tried to smuggle missiles and drones into China.
The 63-year-old, whose wife is a churchwarden in Kent, was described by neighbours as “funny, nice and perfectly normal”.
However, he is accused of attempting to traffic “sensitive American military technology” to China, including missiles, air defence radar and drones.
It is also alleged that he referred to Mr Xi, the Chinese president, as “the boss” in intercepted phone calls.
Court documents in the US state that Mr Miller wanted to have a Los Angeles artist who was a critic of Mr Xi “f---ed up”. He allegedly said his Chinese handlers were “bang up” for launching an attack on him with “bullets” instead of baseball bats.
In April, Mr Miller was arrested along with Cui Guanghai, a 43-year-old Chinese national, on the orders of the FBI in Serbia, where he is awaiting extradition to the US.
The pair were charged after approaching two individuals who, unbeknown to them, were working for the FBI.
Mr Miller is a permanent resident of the US but was born in the UK. He has held roles in at least five UK companies, including a firm that appeared to facilitate English language teaching jobs in China but is now dissolved.
On Sunday, neighbours described the Millers as a “perfect family”, and told of their surprise at his arrest.
One said: “He was a nice guy. Over and above that I didn’t know what he did for work. He was funny, nice and perfectly normal. He wasn’t cagey... I am astounded.
“It’s awful for him, and if he has done it he’s a bloody idiot, but it’s innocent until proven guilty. It’s slightly surreal.”
‘A kind man and good neighbour’
At the Parish Church of King Charles the Martyr, where Mr Miller’s wife Bea is a warden, Rev Laurence Powell said: “It is shocking to hear this about John. He is a very kind man and a good neighbour. I feel so sorry for Beatrice. She must be going through hell right now.”
Mr Miller is accused of employing a wide range of tactics over two and a half years to harass, intimidate, stalk and threaten the Xi critic in LA.
According to a 27-page indictment at the US District Court for the Central District of California, Mr Miller told a confidential FBI source that “the real f---ing pay... the real payday is going to be putting the siding up on that guy” and “there will be extra cash to play with when that happens”.
A special agent said “siding” meant an assault and that there had been an earlier conversation where Mr Miller “had discussed possibly kidnapping the victim”.
“They want it bang bang and gone,” Miller is quoted as saying in a recorded phone call. “No talking to, no nothing to, like a mugging or something. Take his f---ing watch. Take his phone.”
He is then asked if he cares if he preferred “bullets versus baseball bat”, before replying: “Um, not necessarily. But I think you’d get paid more for bullets. And the guys I spoke to said that’s way f---ing easier. Apparently, they’re not so much baseball bat, or like an ice pick is the best way of doing it.
“On the knees and ankles. Doesn’t necessarily have to be bullets. Have him f---ed up and have his picture taken. F---ed up. But the guys I’ve spoken to, the easiest thing is just bam bam bang bang and just walk away. But listen it doesn’t have to be that... knees and ankles.”
‘Chinese Christmas wish list’
Another phone call appears to show Mr Miller had arranged a payment with a “minimum” of $100,000 for the source to carry out the assault, and, when questioned if there was a problem from the female handler Mr Guanghai was reporting to, he replied: “Oh no no no no.
“She’s second in command. And her boss is bang up for it. There’s another guy who needs to approve it. But they’re all bang up for it. As long as it’s reasonable. The numbers we talked about I’m pretty sure it’s 100 per cent.”
The documents show that the pair also enlisted undercover agents to stop the victim from protesting against Mr Xi’s appearance at a summit and installed tracking devices on the victim’s car, and paid the undercover agents to slash their tyres.
They also devised a complex plan to destroy a set of statues created by the artist which depicted Mr Xi and his wife bare-chested, kneeling with their hands tied behind their backs.
Initially, Mr Miller had allegedly wanted to steal the statues and “remove the heads” as evidence but later decided to pay the undercover FBI agents to “smash up” them up.
In 2025, Mr Miller paid the agents $36,500 (£27,100) to convince the victim to desist from showcasing the new statues at an upcoming protest.
He also allegedly tried to purchase millions of pounds worth of military equipment on behalf of the Chinese military as part of a “Christmas wish list”. He is quoted as saying his buyers were “interested in the Western stuff” including armour plates for “tanks that the Yanks have”.
He reportedly tried to buy a £37,000 Stinger portable missile launcher, two military drones valued at £148,000, a £668,000 AGM-88E anti-radiation missile system and a £1.5 million air-defence radar system.
Mr Miller also allegedly tried to procure a cryptographic device, which is used for secure communication of classified and sensitive information.
At one point, the Briton allegedly suggested that the device be smuggled from the US to China by hiding it inside a food blender or a motor starter, having shipped it first via DHL or FedEx to Hong Kong.
‘Big boss’
Several times in Mr Miller’s conversations, he is said to have mentioned a “boss” or at times a “big boss” that seems to be the one giving orders.
According to the special FBI agent who submitted the affidavit, Mr Miller’s use of the phrase “boss” “refer[s] to President Xi” and “demonstrates [Miller’s] awareness that he was acting at the direction and control of the [Chinese] government.”
Todd Blanche, the US deputy attorney general, said: “This is a blatant assault on both our national security and our democratic values. This Justice Department will not tolerate foreign repression on US soil, nor will we allow hostile nations to infiltrate or exploit our defence systems.
“We will act decisively to expose and dismantle these threats wherever they emerge.”
If convicted, Mr Miller could also face the maximum penalties of five years in prison for conspiracy, five years in prison for interstate stalking, and 10 years in prison for smuggling.
6 months ago
Turns Out, Trump’s Qatar Private Jet Wasn’t Even a Gift.
There’s no such thing as a free plane.
Donald Trump’s administration specifically sought out the luxury Boeing 747-8 jumbo jet from Qatar’s government to replace Air Force One, despite the president’s insistence that the plane was a gift.
A senior White House official said Trump tasked Steve Witkoff, the president’s special envoy to the Middle East (and shady crypto partner), with tracking down a replacement for Air Force One, after Trump learned that Boeing would not have new jets ready for another two years. Witkoff ended up leading initial conversations with the Qatari government.
Boeing provided the Pentagon with a list of other clients who might be able to help with America’s search for a new plane. One of those sources said that Qatar was included on that list of clients and that the U.S. reached out about purchasing the luxury plane from the Qatari Defense Ministry, which indicated it was willing to sell.
There’s no such thing as a free plane.
Donald Trump’s administration specifically sought out the luxury Boeing 747-8 jumbo jet from Qatar’s government to replace Air Force One, despite the president’s insistence that the plane was a gift.
A senior White House official said Trump tasked Steve Witkoff, the president’s special envoy to the Middle East (and shady crypto partner), with tracking down a replacement for Air Force One, after Trump learned that Boeing would not have new jets ready for another two years. Witkoff ended up leading initial conversations with the Qatari government.
Boeing provided the Pentagon with a list of other clients who might be able to help with America’s search for a new plane. One of those sources said that Qatar was included on that list of clients and that the U.S. reached out about purchasing the luxury plane from the Qatari Defense Ministry, which indicated it was willing to sell.
7 months ago
Why High-Net-Worth Investors Prefer OTC Crypto Trading?
High-net-worth investors prefer OTC crypto trading platform for its privacy, reduced market impact, and ability to handle large-volume transactions discreetly. OTC desks offer personalized service, deep liquidity, and better pricing for bulk trades. They also provide faster settlements and regulatory compliance support.
visit: https://www.troniextechnol...
High-net-worth investors prefer OTC crypto trading platform for its privacy, reduced market impact, and ability to handle large-volume transactions discreetly. OTC desks offer personalized service, deep liquidity, and better pricing for bulk trades. They also provide faster settlements and regulatory compliance support.
visit: https://www.troniextechnol...
8 months ago
Fortune 500 companies have unwittingly hired thousands of software engineers who claim to be American developers but are actually North Korean citizens using stolen or fake identities. Through legitimate employment, the IT workers are illegally funneling their salaries to Kim Jong Un’s regime to fund prohibited weapons of mass destruction and ballistic missile programs. The U.S. Treasury, State Department, and FBI collectively estimate the IT workers scam has generated hundreds of millions each year since 2018.
About 95% of the résumés Harrison Leggio gets in response to job postings for his crypto startup g8keep are from North Korean engineers pretending to be American, the founder estimates. He even once interviewed a job seeker who claimed to have worked at the same Manhattan-based cryptocurrency exchange as he did, during the time he worked there.
About 95% of the résumés Harrison Leggio gets in response to job postings for his crypto startup g8keep are from North Korean engineers pretending to be American, the founder estimates. He even once interviewed a job seeker who claimed to have worked at the same Manhattan-based cryptocurrency exchange as he did, during the time he worked there.
8 months ago
Senior officers from Iran’s Revolutionary Guard have been accused of pilfering approximately $21 million in cryptocurrency while investigating a corruption case.
What Happened: The alleged theft took place during a probe into Cryptoland, a digital exchange that was shuttered following the arrest of its CEO, Sina Estavi, in May 2021.
Blockchain records showed that six billion BRG tokens, created by Estavi, were transferred from his cryptocurrency wallet a day after his arrest, the report said. These tokens were allegedly sold off by officers of the Revolutionary Guard, generating millions for themselves.
Two key figures, Mehdi Hajipour and Mehdi Badi, senior interrogators in the Revolutionary Guard’s economic branch, were identified by a court-appointed expert. The expert’s report confirmed that wallets controlled by Hajipour sold over $21 million worth of BRG tokens.
What Happened: The alleged theft took place during a probe into Cryptoland, a digital exchange that was shuttered following the arrest of its CEO, Sina Estavi, in May 2021.
Blockchain records showed that six billion BRG tokens, created by Estavi, were transferred from his cryptocurrency wallet a day after his arrest, the report said. These tokens were allegedly sold off by officers of the Revolutionary Guard, generating millions for themselves.
Two key figures, Mehdi Hajipour and Mehdi Badi, senior interrogators in the Revolutionary Guard’s economic branch, were identified by a court-appointed expert. The expert’s report confirmed that wallets controlled by Hajipour sold over $21 million worth of BRG tokens.
11 months ago
China's foreign exchange regulator released new rules that require banks to flag risky trades, including those involving cryptocurrencies, which would make it more difficult for mainland investors to buy and sell bitcoin and other digital assets.
Banks are expected to monitor and report "risky foreign exchange trading behaviours", including underground banks, cross-border gambling and illegal cross-border financial activities involving cryptocurrencies, according to last week's announcement by the State Administration of Foreign Exchange.
The rules, applicable to local banks across mainland China, also require them to track such activities based on the identity of the institutions and individuals involved, source of funds and trading frequency, among other factors.
In addition, banks are required to put in place risk-control measures that cover those entities and restrict provision of certain services to them, the regulator said.
Banks are expected to monitor and report "risky foreign exchange trading behaviours", including underground banks, cross-border gambling and illegal cross-border financial activities involving cryptocurrencies, according to last week's announcement by the State Administration of Foreign Exchange.
The rules, applicable to local banks across mainland China, also require them to track such activities based on the identity of the institutions and individuals involved, source of funds and trading frequency, among other factors.
In addition, banks are required to put in place risk-control measures that cover those entities and restrict provision of certain services to them, the regulator said.
11 months ago
Russian companies have begun using bitcoin and other digital currencies in international payments following legislative changes that allowed such use in order to counter Western sanctions, Finance Minister Anton Siluanov said on Wednesday.
Sanctions have complicated Russia's trade with its major partners such as China or Turkey, as local banks are extremely cautious with Russia-related transactions to avoid scrutiny from Western regulators.
This year, Russia permitted the use of cryptocurrencies in foreign trade and has taken steps to make it legal to mine cryptocurrencies, including bitcoin. Russia is one of the global leaders in bitcoin mining.
"As part of the experimental regime, it is possible to use bitcoins, which we had mined here in Russia (in foreign trade transactions)," Siluanov told Russia 24 television channel.
"Such transactions are already occurring. We believe they should be expanded and developed further. I am confident this will happen next year," he said.
Sanctions have complicated Russia's trade with its major partners such as China or Turkey, as local banks are extremely cautious with Russia-related transactions to avoid scrutiny from Western regulators.
This year, Russia permitted the use of cryptocurrencies in foreign trade and has taken steps to make it legal to mine cryptocurrencies, including bitcoin. Russia is one of the global leaders in bitcoin mining.
"As part of the experimental regime, it is possible to use bitcoins, which we had mined here in Russia (in foreign trade transactions)," Siluanov told Russia 24 television channel.
"Such transactions are already occurring. We believe they should be expanded and developed further. I am confident this will happen next year," he said.
12 months ago
The Iranian currency extended its fall on Saturday, hitting a new all-time low against the U.S. dollar amid uncertainties about Donald Trump's imminent arrival in the White House and tensions with the West over Tehran's nuclear programme.
The rial plunged to 756,000 to the dollar on the unofficial market on Saturday, compared to 741,500 rials on Friday, according to Bonbast.com, which reports exchange rates. The bazar360.com website said the dollar was being sold for about 755,000 rials.
Facing an official inflation rate of about 35%, Iranians seeking safe havens for their savings have been buying dollars, other hard currencies, gold or cryptocurrencies, suggesting further headwinds for the rial.
The dollar has been gaining against the rial since trading around 690,000 rials in early November amid concerns that once inaugurated in January, Trump would re-impose his "maximum pressure" policy against Iran with tougher sanctions and empower Israel to strike Iranian nuclear sites.
The rial plunged to 756,000 to the dollar on the unofficial market on Saturday, compared to 741,500 rials on Friday, according to Bonbast.com, which reports exchange rates. The bazar360.com website said the dollar was being sold for about 755,000 rials.
Facing an official inflation rate of about 35%, Iranians seeking safe havens for their savings have been buying dollars, other hard currencies, gold or cryptocurrencies, suggesting further headwinds for the rial.
The dollar has been gaining against the rial since trading around 690,000 rials in early November amid concerns that once inaugurated in January, Trump would re-impose his "maximum pressure" policy against Iran with tougher sanctions and empower Israel to strike Iranian nuclear sites.
1 yr. ago
For your safety deactivate your telegram account and delete the app.
Powerful criminal networks in Southeast Asia extensively use the messaging app Telegram which has enabled a fundamental change in the way organised crime can conduct large-scale illicit activity, the United Nations said in a report on Monday.
Hacked data including credit card details, passwords and browser history are openly traded on a vast scale on the app which has sprawling channels with little moderation, the report by the United Nations Office for Drugs and Crime (UNODC) said.
Tools used for cybercrime, including so-called deepfake software designed for fraud, and data-stealing malware are also widely sold, while unlicensed cryptocurrency exchanges offer money laundering services.
There is "strong evidence of underground data markets moving to Telegram and vendors actively looking to target transnational organized crime groups based in Southeast Asia," the report said.
Powerful criminal networks in Southeast Asia extensively use the messaging app Telegram which has enabled a fundamental change in the way organised crime can conduct large-scale illicit activity, the United Nations said in a report on Monday.
Hacked data including credit card details, passwords and browser history are openly traded on a vast scale on the app which has sprawling channels with little moderation, the report by the United Nations Office for Drugs and Crime (UNODC) said.
Tools used for cybercrime, including so-called deepfake software designed for fraud, and data-stealing malware are also widely sold, while unlicensed cryptocurrency exchanges offer money laundering services.
There is "strong evidence of underground data markets moving to Telegram and vendors actively looking to target transnational organized crime groups based in Southeast Asia," the report said.
1 yr. ago
How Telegram Became a Playground for Criminals, Extremists and Terrorists.
For millions of people, Telegram is like any other social media or messaging app.
In Brazil, 167,000 people subscribe to a Telegram channel for news about reality shows and entertainment. More than 1 million users in India prepare for government exams in another channel. One called Whale with more than 3 million followers, crypto trading tips are swapped in Arabic.
Look deeper, and a dark underbelly emerges.
Uncut lumps of cocaine and shards of crystal meth are on sale. Handguns and stolen checks are widely available. White nationalists use the platform to coordinate fight clubs and plan rallies. Hamas broadcast its Oct. 7 attack on Israel on the site.
The degree to which Telegram has been inundated by such content has not been previously reported. Investigation found 1,500 channels operated by white supremacists who coordinate activities among almost 1 million people around the world.
For millions of people, Telegram is like any other social media or messaging app.
In Brazil, 167,000 people subscribe to a Telegram channel for news about reality shows and entertainment. More than 1 million users in India prepare for government exams in another channel. One called Whale with more than 3 million followers, crypto trading tips are swapped in Arabic.
Look deeper, and a dark underbelly emerges.
Uncut lumps of cocaine and shards of crystal meth are on sale. Handguns and stolen checks are widely available. White nationalists use the platform to coordinate fight clubs and plan rallies. Hamas broadcast its Oct. 7 attack on Israel on the site.
The degree to which Telegram has been inundated by such content has not been previously reported. Investigation found 1,500 channels operated by white supremacists who coordinate activities among almost 1 million people around the world.
1 yr. ago
Countries from Russia to China are building payments systems that could threaten the dollar's global dominance.
The West's sanctions are pushing Russia to develop alternative payment systems with its trade partners.
Russia's SPFS and Mir systems, China's CIPS, and India's UPI help aim to challenge SWIFT's dominance.
Central bank digital currencies and cryptocurrencies are also being explored to facilitate trade.
The West's tightening sanctions are driving Russia nearly up against the wall — but Moscow keeps finding ways to keep the country's economy going.
Russia's trade partners, too, are looking for ways to continue doing business with the country via alternative systems to rival the Western-led, US dollar-dominated global financial order.
There's been some success, with trade between Russia and China, as well as Russia and India, chugging along until recently.
Russia and its partners have been looking at other ways to do business.
The West's sanctions are pushing Russia to develop alternative payment systems with its trade partners.
Russia's SPFS and Mir systems, China's CIPS, and India's UPI help aim to challenge SWIFT's dominance.
Central bank digital currencies and cryptocurrencies are also being explored to facilitate trade.
The West's tightening sanctions are driving Russia nearly up against the wall — but Moscow keeps finding ways to keep the country's economy going.
Russia's trade partners, too, are looking for ways to continue doing business with the country via alternative systems to rival the Western-led, US dollar-dominated global financial order.
There's been some success, with trade between Russia and China, as well as Russia and India, chugging along until recently.
Russia and its partners have been looking at other ways to do business.
1 yr. ago
French authorities charged Telegram CEO Pavel Durov with multiple crimes this week.
Telegram's finances reveal a $108 million loss on $342 million of revenue last year, the FT reports.
Telegram's apparent reliance on crypto services raises questions about its $30 billion valuation.
This week French authorities charged Telegram CEO Pavel Durov with multiple crimes. But in the months before that, he was telling people he might take his company public, and floated a $30 billion valuation for his messaging/social media company, which boasts more than 900 million users.
Now the Financial Times says it has gotten a look at Telegram's 2023 finances, and those numbers make it very hard to imagine the company could convince people it's worth anything like $30 billion — even if its founder and CEO wasn't looking at jail time.
It's not uncommon for fast-growing consumer tech companies to be money losers when they go public. Twitter did that in 2012, and Reddit did it this year.
Telegram's finances reveal a $108 million loss on $342 million of revenue last year, the FT reports.
Telegram's apparent reliance on crypto services raises questions about its $30 billion valuation.
This week French authorities charged Telegram CEO Pavel Durov with multiple crimes. But in the months before that, he was telling people he might take his company public, and floated a $30 billion valuation for his messaging/social media company, which boasts more than 900 million users.
Now the Financial Times says it has gotten a look at Telegram's 2023 finances, and those numbers make it very hard to imagine the company could convince people it's worth anything like $30 billion — even if its founder and CEO wasn't looking at jail time.
It's not uncommon for fast-growing consumer tech companies to be money losers when they go public. Twitter did that in 2012, and Reddit did it this year.